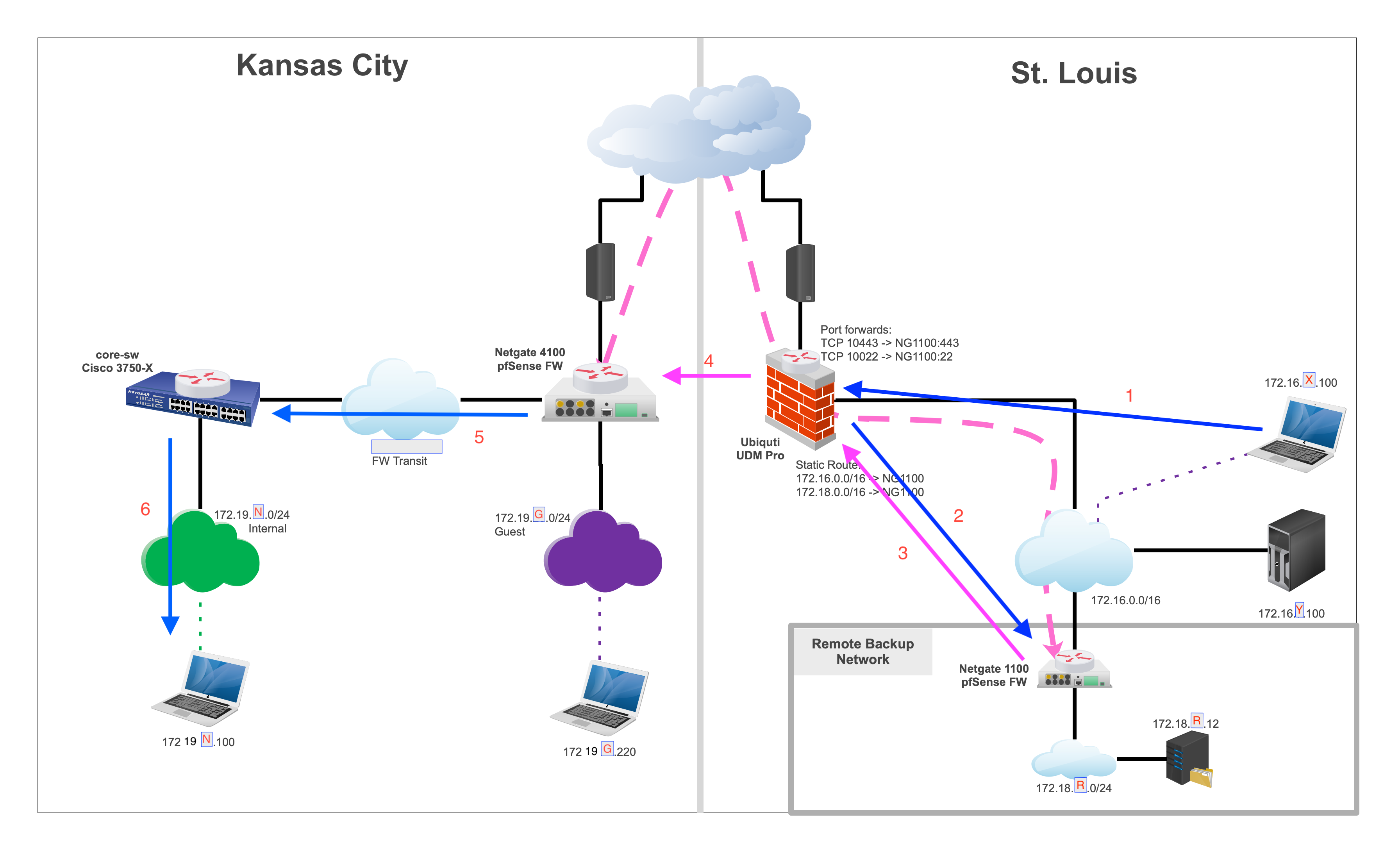
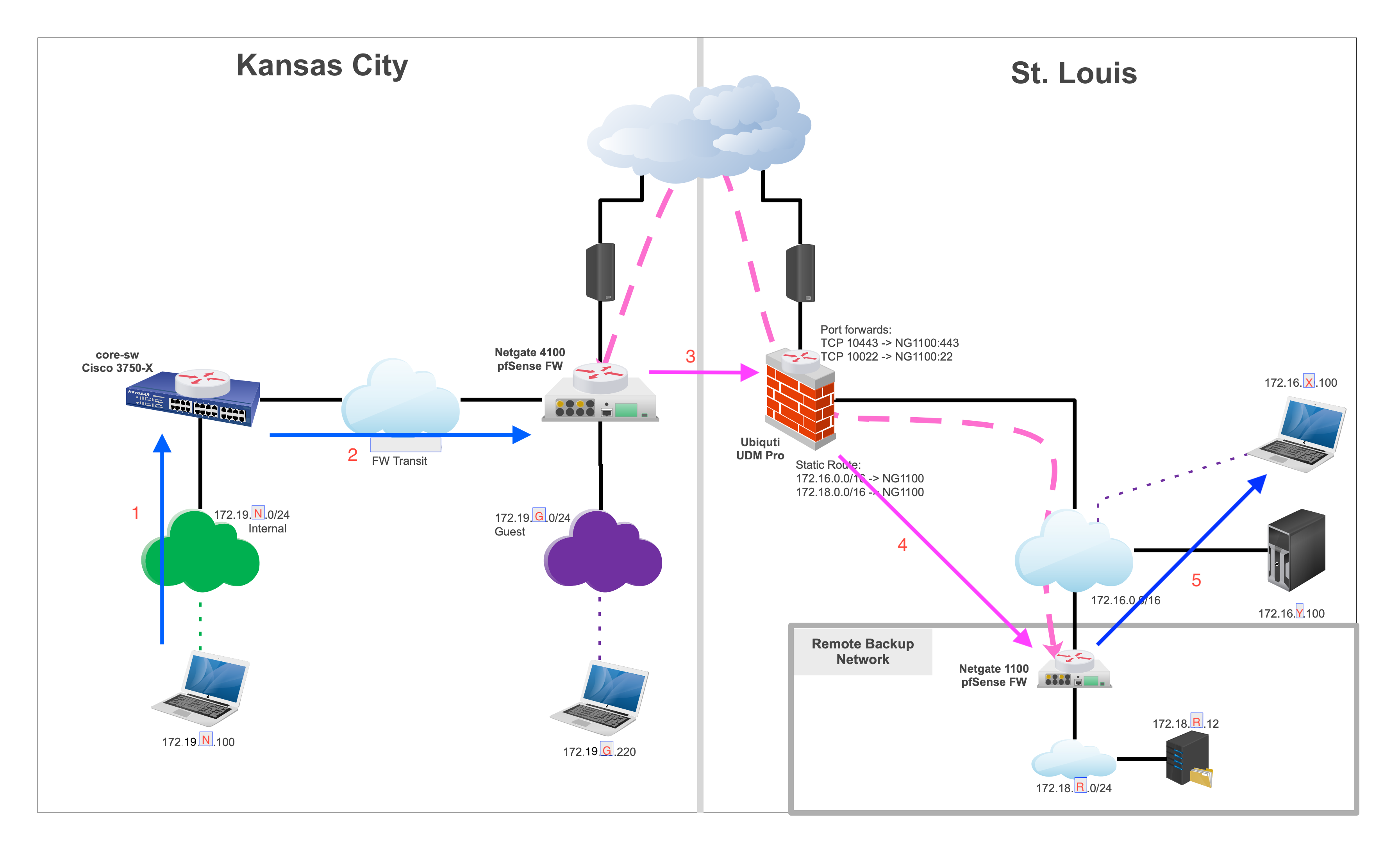
Site to Site and Hair-Pin
-
@photomankc Would he need to access anything on the backup network?
If not, you're better off just setting up a separate VPN for each.
One for lan access and one for backup. -
@jarhead said in Site to Site and Hair-Pin:
@photomankc Would he need to access anything on the backup network?
If not, you're better off just setting up a separate VPN for each.
One for lan access and one for backup.No. There would not really be any cause for him (while on his side) to need to ride the VPN to get to the backup network. That would be just done via the normal firewall if it all.
So create one IPSEC VPN that carries only 172.18.R.0/24 -> 172.19.0.0/16
Then create another one that carries only 172.16.0.0/16 -> 172.19.0.0/16
That's cool so long as the hair-pin for 172.16 to 172.19 is not going to be a problem.
-
@photomankc
No need for the hairpin.
Create the vpn to his network for the lan access.
Create the backup vpn to your stuff.Would be a lot better if you just use the pfSense as the gateway for both networks but he may not like that.
-
@photomankc
TCP traffic doesn't work this way with the static route on the UDM. You would run into asymmetric routing issues.To go around this, set up a transit network between the UDM and the NG1100.
If it's not possible to connect the 1100 directly to the UDM configure a separate VLAN, where you put both into.
Then point the static routes to the new IP of the 1100. -
Are you saying create the VPN to his firewall (UDM Pro) for our LAN to LAN traffic? Otherwise I can't see any way to avoid the hairpin.
Correct, it would be easier, but as I mention he's not really interested in messing around much in his gateway and certainly won't want me to replace his with mine. He's got a remote-office setup and a passing knowledge of networking but when issues crop up it's far too much bother to have to sit on the phone with us each working on our gateway to fix the tunnel.
I want to deploy hardware that's pretty transparent to him. I configure it all from the 1100 and have access to troubleshoot and work both sides without much risk of messing anything up that he needs for work. I'm just wondering if it's feasible to hairpin the VPN traffic knowing it's not really completely ideal.
-
@viragomann said in Site to Site and Hair-Pin:
To go around this, set up a transit network between the UDM and the NG1100.
Yeah, that's an idea I was tossing around a bit. As long as he has a spare interface to get that done without a lot of headache. I think the IN / OUT VPN traffic to HIS LAN would still hairpin but that would keep the routing cleaner.
-
@photomankc said in Site to Site and Hair-Pin:
As long as he has a spare interface to get that done without a lot of headache.
This also requires that all involved devices are on the same place. If not create a VLAN on his LAN, as said. Normally VLAN tags passes non-VLAN switches without any issue.
I think the IN / OUT VPN traffic to HIS LAN would still hairpin but that would keep the routing cleaner.
No, if you have a transit network the traffic goes LAN > transite > NG 1100 > your site and the same route back.
-
@photomankc said in Site to Site and Hair-Pin:
Are you saying create the VPN to his firewall (UDM Pro) for our LAN to LAN traffic? Otherwise I can't see any way to avoid the hairpin.
Yes, that would be the easiest solution.
-
Okay, I believe he's using his UDM Pro as a router-on-a-stick and that it does ALL the routing in his network. If we setup two interfaces on the UDM Pro with a small point-to-point network /29 or /30 then I can have all the internet bound traffic and VPN tunnel go out the WAN. All remote backup network gear traffic goes to the LAN. All traffic to friend's internal home networks goes to OPT to his UDM Pro and gets routed as appropriate. No hair-pins. Could even do it with a single port with VLAN tagging and VIPs. Not as dead simple as I hoped but would mean that I have full admin control of both ends of the tunnel since I'm the one most likely to ever try and fix it if it breaks.
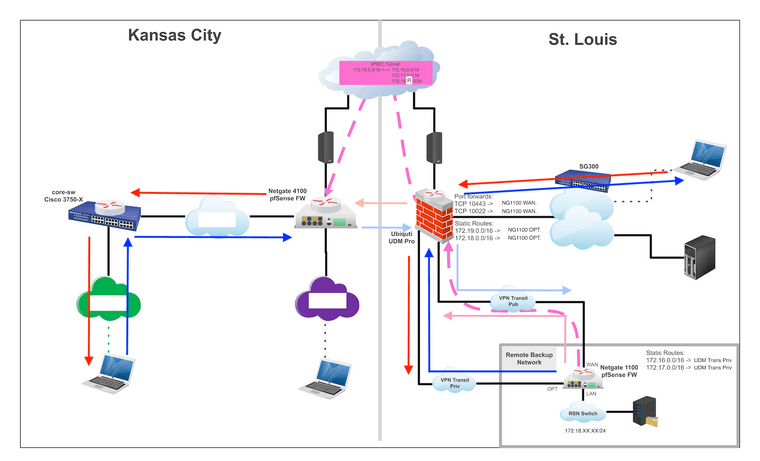
-
@photomankc
Isn't the UDM capable of managing multiple subnets or VLANs?
If so, what's the real benefit of the VPN? A VPN for transit within a transit network? -
I'll just continue on from here. I'm not following your comments really. His UDM is managing VLANs and networks for his clients. I need a connection to his UDM to get my VPN and network routed to and from his UDM. The VPN is to get to discrete networks in two geographically dispersed locations to communicate directly. I have no idea how else it would be done.
Appreciate everyone's input. Although I'd still be interested to know if pfSense can handle a hair-pin situation with VPN or if it really needs to cross interfaces to operate at all.