NAT Translation Breaks DNS
-
I am trying to send my DNS requests out via an interface that has NAT translation set up on it and it fails.
In DNS resolver the Outgoing Network Interfaces is set to only use the interface with the translated NAT. DNS Access List are in place to allow my LAN (192.168.163.1/24), 127.0.0/8, interface address (10.2.0.3) and translated address (10.2.0.2) to access the DNS Resolver (not in forwarding mode).
The interface is a wireguard tunnel interface to a VPN provider. The interface address is 10.2.0.3 that has it's outbound NAT translated to 10.2.0.2. Internet traffic across this tunnel works perfectly. But all DNS requests fail....regardless if I'm using Resolver in resolving or forwarding mode.
However, if I set the interface to use the 10.2.0.2 IP address all (resolving or forwarding) DNS queries work perfectly....they are not being blocked by the VPN provider and it has been confirmed by their tech support that they do not block anything on port 53.
I did a pcap on the interface and I can see that the outbound NAT rule is not being applied. Here's a picture of the pcap:

In the red circle you can see that the DNS query was sent out but with the actual interface address (10.2.0.3) and not the translated NAT of 10.2.0.2. I can't figure out why the outbound NAT rule is not being applied to the DNS request sent by Resolver. Here are some pictures of the outbound NAT setup:
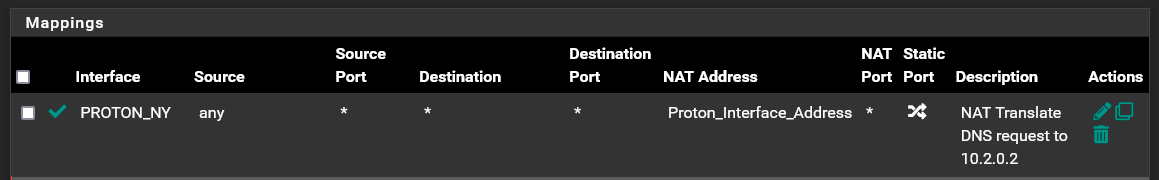
Outbound NAT Translation Rule At Top Of Outbound Nat Rules.
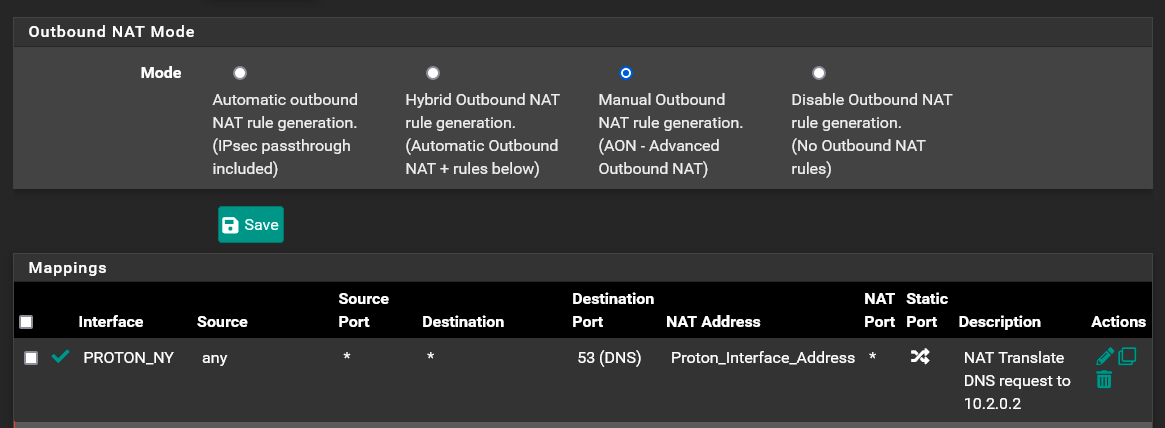
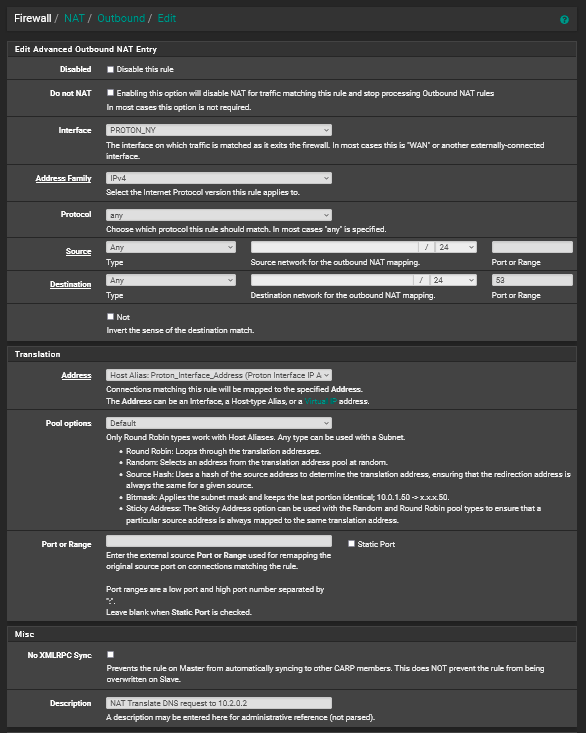
Detail Of Outbound NAT Rule (Alias in Translation is 1 IP - 10.2.0.2)
Thanks in advance for any help in figuring out what I have incorrectly setup.
-
@dma_pf said in NAT Translation Breaks DNS:
DNS Access List are in place to allow my LAN (192.168.163.1/24), 127.0.0/8, interface address (10.2.0.3) and translated address (10.2.0.2) to access the DNS Resolver
Huh - you lost me... If your saying normal traffic works out of your vpn connection, then all traffic going out that interface would already be natted, there is no special need to create a special nat for dns? And there would be no need to nat anything anyway if you set unbound to use that interface address when talking out the tunnel..
You would nat say traffic from your lan 192.168.x.x whatever going down the vpn tunnel network of 10.something.. If your talking from the vpn interface for unbound there is no reason to nat anything..
-
@johnpoz said in NAT Translation Breaks DNS:
Huh - you lost me... If your saying normal traffic works out of your vpn connection, then all traffic going out that interface would already be natted, there is no special need to create a special nat for dns? And there would be no need to nat anything anyway if you set unbound to use that interface address when talking out the tunnel..
You would nat say traffic from your lan 192.168.x.x whatever going down the vpn tunnel network of 10.something.. If your talking from the vpn interface for unbound there is no reason to nat anything..Hi John, thanks for your help. With regard to the Access List I created the list for the various addresses as a trouble shooting measure. I did that based on a prior issue (https://forum.netgate.com/topic/165818/dns-not-working-with-phone-as-peer?_=1673805533998) we worked on which was only resolved by creating an access list for DNS requests to be routed out of wireguard. In that issue without the Access List I was not able to route DNS requests via a remote peer on a wireguard tunnel. Since I could not get DNS to work in my current issue I created the Access List as a troubleshooting item to see if it would work.
As to why I have to NAT translate the Interface IP it is because I'm trying to set up 3 VPN connections to my provider for redundancy purposes. ProtonVPN requires all connections to all of their servers to be on IP 10.2.0.2. Therefore I could not set up 3 different vpn connections as the interfaces would all require the same IP address.
However, I've gotten the 3 connections to their servers to work by creating 3 different interfaces, 10.2.0.3, 10.2.0.4 and 10.2.0.5 with each of them having an outbound NAT rule translating traffic on the interfaces to 10.2.0.2 that the provider wants. A lot more detail of how this was set up is here: https://forum.netgate.com/topic/176579/different-interfaces-gateways-using-same-ip-address.
This setup has been working perfectly for all traffic except DNS. For some reason when Resolver sends the DNS requests out any of those interfaces (resolving or forwarding) the NAT translation is ignored and the packets are sent with the original interface IP address.
I attempted to create the NAT rule in my post above to try to be more specific to any traffic from on my router to port 53 to be translated. If I set the NAT rule as shown in the picture below I get the exact same results.....everything but DNS packets are routed correctly. It's like Resolver is not seeing/using the NAT rule or is completely ignoring it.
-
@dma_pf if you want to nat dns, then you wouldn't use the vpn interface as the unbound interface. Use the loopback, then when it goes out, it would use your nat rule.
-
@johnpoz So I set the Outgoing Network Interfaces in Resolver to Localhost. Saved the settings, cleared all states and did a pcap on the VPN interface while doing a dig in the command prompt on pfsense.
This time dig resolved the domain. However, there was no traffic at all on the VPN interface. And when I checked https://www.dnsleaktest.com it shows that my DNS is being asked for from the IP address assigned by my ISP which is on my WAN. Doing a pcap on WAN shows the DNS requests.
How to route the Localhost DNS request out the VPN interface?
-
@dma_pf said in NAT Translation Breaks DNS:
How to route the Localhost DNS request out the VPN interface?
localhost would use the routing on your box.. Why would it use your isp dns? Thought you said you were resolving? And not forwarding.. There is no scenario where unbound would ask your isp dns unless you allowed those to be set via dhcp, and you were set to forward. Pfsense itself might ask them, if loopback didn't answer? Ie unbound was down/not working..
If you want to use your vpn dns, then set your default route to go out vpn. Or forward to your vpn dns..
I really don't get what you think having multiple connections to your vpn gets you? Do you actually have multiple wan connections?