IPSec tunnel stopped working post upgrade
-
Netgate please may I have some help? This whole upgrade thing is totally unreliable nowadays
-
@orangehand lets start with the basics.
What does your logs show?
a. Status > System Logs, Firewall tabIs the service running?
a. Status > Services.What have you done to tshoot?
What pf version are you on?Both ends show as fine.
- what does this mean?
-
@michmoor The Firewall logs show a load of blocks via the WAN from my WANip to theirs for UDP traffic on seemingly random ports. Is there any risk in posting the actual entries here?
Service is running
I've rebooted the remote router and restarted the IPSec service
The status in the dashboard and the IPsec status page both show as up and connected. I have another ipsec from my pfSense to another customer and that is fine, so the issue is at the other end post upgrade to 22.05 (prior to which I had removed all packages and then reinstalled post upgrade as seems to be recommended)
Does that help any? (and thanks!)
-
@orangehand also just added in a new tunnel at other end with same results. P1 shows as up, but P2 is down at my end.remote end shows P1 up and P2 down
-
NETGATE: your update has killed VPNs. Please help.
New IPSec won't connect P2, IPSec that WAS working shows as fine/connected but traffic doesn't pass. I uninstalled all the packages, upgraded then reinstalled them. My openVPN client connection from my Mac doesn't pass traffic either, despite showing as up and working. -
@orangehand
You havent provided any system logs. That will be the clearest place to see what is not being negotiated between your peers.Status/ System Logs / IPsec
Search for the peer IP. Something should come up. For example this is what i find in my syslog.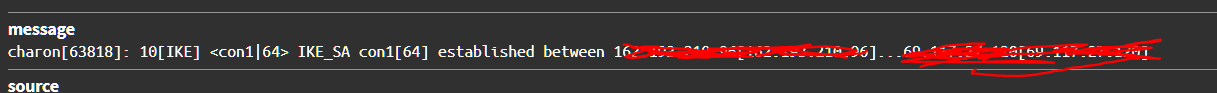
-
@michmoor Thank you. I am embarrassed to admit it was a config at my end. However this was a replacement tunnel I had made (wrongly) as the upgrade DID break the original IPSec tunnel.
Humble apologies if I have wasted anyone's time
-
@orangehand I’m confused. You blamed Netgate then you blamed the upgrade and then you said the tunnels worked fine for years until you upgraded. Then you made a replacement tunnel that didn’t work.
But you actually made a config change this whole time?!?
And the original IPsec tunnel is still down? -
@michmoor No. The update to 22.05 broke the existing IPSec tunnel, and I couldn't fix it. Nothing had changed other than the upgrade. So I made a new one, but screwed it up. For which I apologised. The original tunnel was deleted. I thought I had just disabled it, but I was again wrong!
-
@orangehand ok no problem. Glad it all worked out