pfSense 2nd WAN behind LTE modem DMZ
-
@siwyboy said in pfSense 2nd WAN behind LTE modem DMZ:
Right now I'm trying to find a USB LTE modem that is compatible with pfSense based on this article:
https://docs.netgate.com/pfsense/en/latest/cellular/hardware.htmlGood luck.
The LTE modem you're using has to assign the public IP to the pf. If it is assigning it to something else that is plugged in you can tell the interface to ignore IPs from a specific DHCP server but that is only going to work if the upstream is giving it one.
If your LTE has the public IP then you just need to DMZ the pfSense IP in the LTE device.
Comparing the EdgeRouter to pfSense in this regard is like saying you don't like that your scooter isn't a coupe.
So why isn't DDNS working? Dunno, the logs would tell you.
-
@siwyboy Are you sure DDNS doesn't work, have you tested? I have a similar setup although I have it set up towards my WAN Group. It works because it doesn't bother with the WAN IP, rather it goes to what you have defined under Services > Dynamic DNS under Check IP tab.
Mine reads http://checkip.dyndns.org which I think is default.
-
@gblenn I think there is something wrong with the TP-Link DMZ.
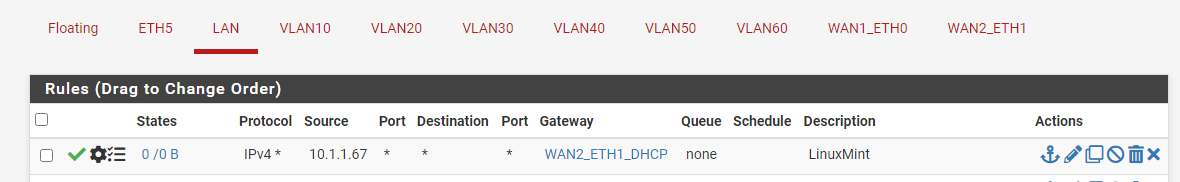
I connected a device to pfsense and gave it an IP: 10.1.1.67
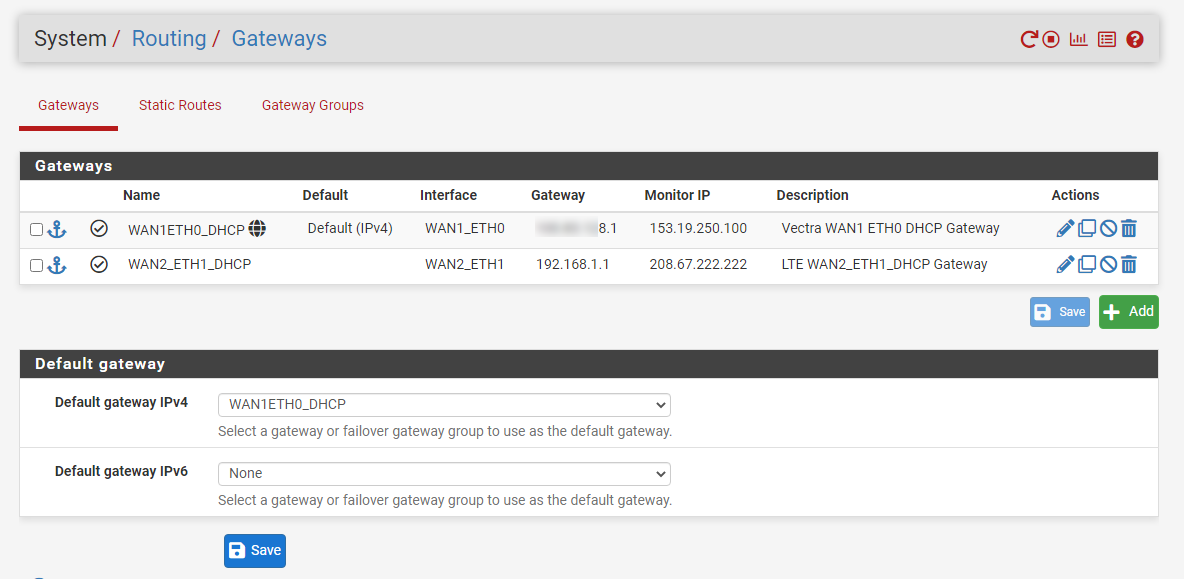
Used the http://checkip.dyndns.org service to check the default WAN 1 IP and it's correct.Then I created a rule to route the device through WAN 2:
Again used the http://checkip.dyndns.org service and I can see the public IP:
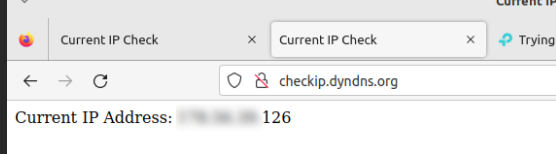
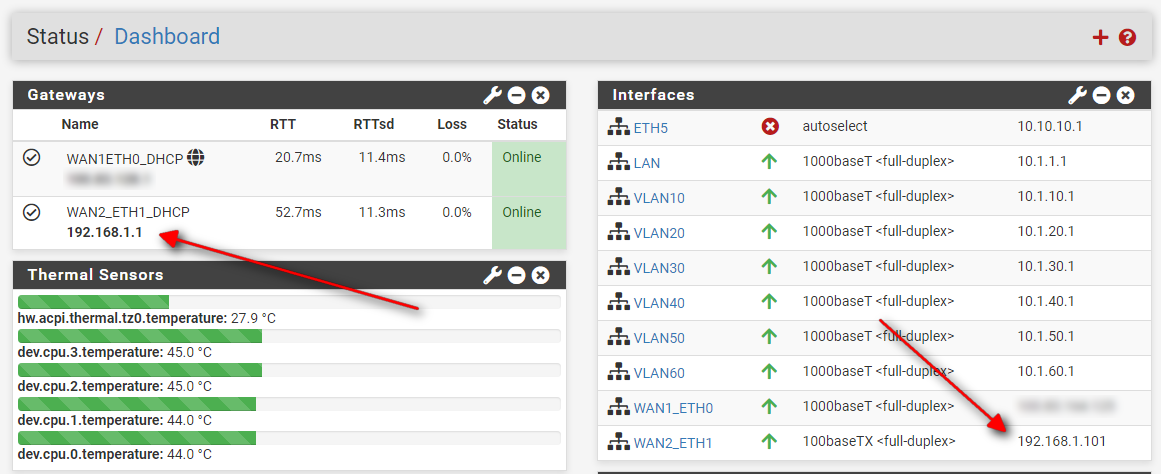
but I'm also able to open the TP-Link admin panel from this device. Probably it's because pfsense sees the router gateway 192.168.1.1
I checked the DMZ and it looks to be correct:
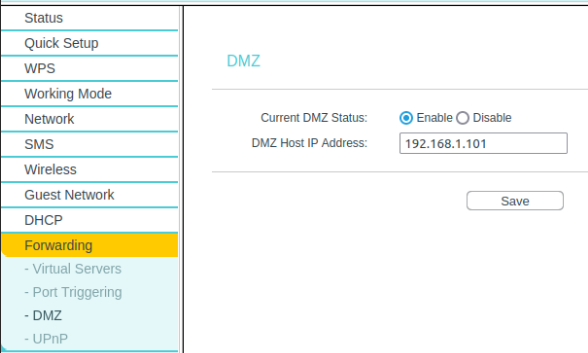
I can't see the linux machine on the DHCP list, so it's bypassing the tp-link router:
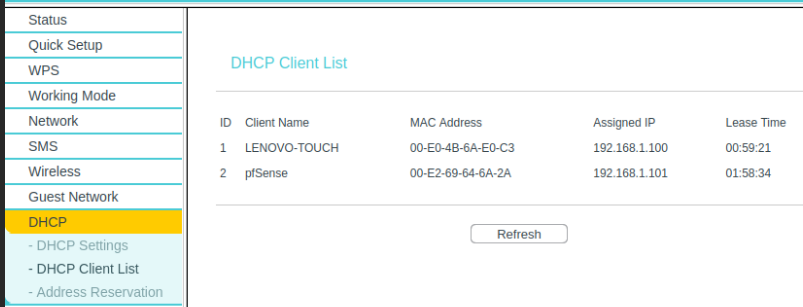
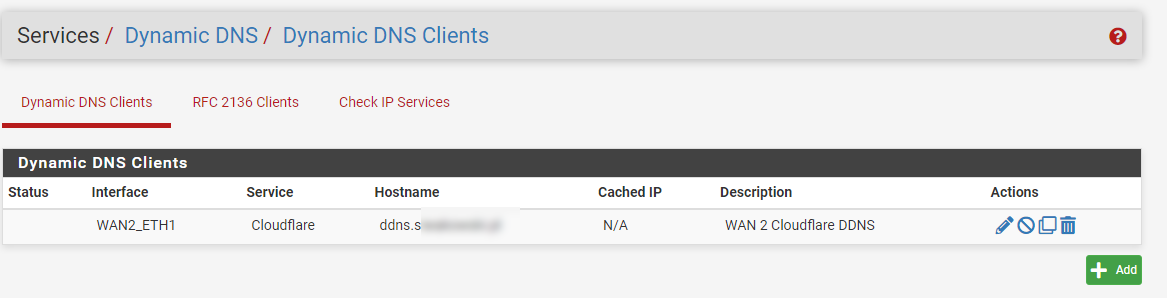
I also have the paid DynDNS Pro service so I created a dummy entry:
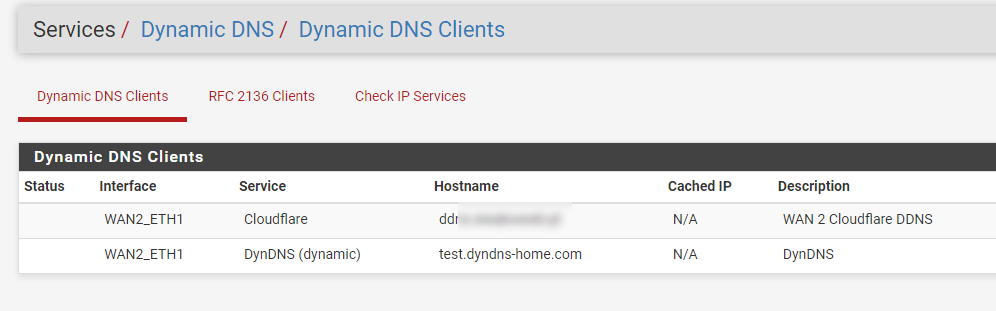
but still nothing.I'm still trying to figure this out :/
-
@siwyboy pfsense should pick up the right IP with or without DMZ. Provided it detects a private IP on WAN, it will accesses the web site just like you did and read the IP from that row.
And yes you should be able to reach the TP-Link from inside your pfsense, since pfsense is aware of it (the IP settings for pfsense WAN includes the gateway IP).
When you say
I also have the paid DynDNS Pro service so I created a dummy entry:
but still nothing.
Did you click Save and Force Update??
I think you need to check the settings for that DDNS entry, like type, user/pw or token and Update URL. It should update regardless of which IP pfsense thinks it should set (192.168.1.101) or your public IP from http://checkip.dyndns.org...
I made a test just now and it worked perfectly fine...
-
@gblenn I'm trying to figure this out for the last 4 hours hehehe
I checked, changed, reconfigured all possible settings that I'm aware of and still nothing...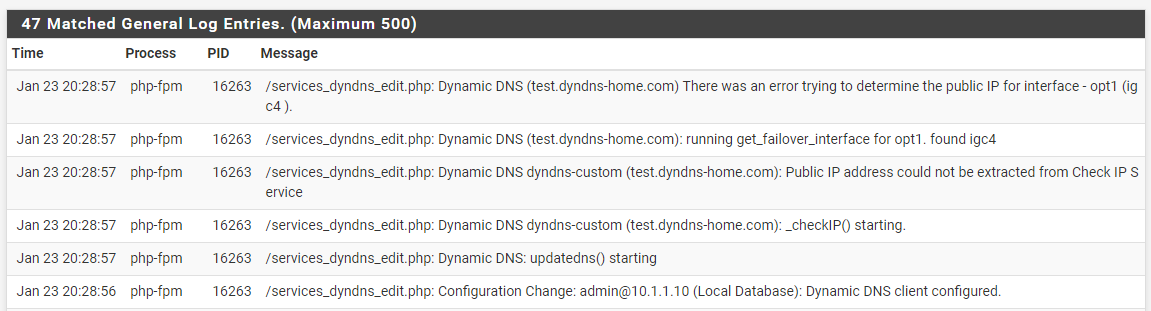
It must be something with the second router
-
@gblenn I performed the final test.
On tplink I disabled DMZ, configured dyndns and opened port 80
I was able to access the router without any issues.
I will try to get a different router this week and maybe a USB LTE modem. Will update this post once I find a solution or workaround.
-
Wierd that pfsense can't get the IP address when you can do it from inside pfsense, via that exact same service. Why would pfsense be any different?
Have you rebooted the TP-Link? Restarted the WAN2 interface? Restarted the DDNS service on pfsense?
One way of fooling pfsense into picking up the IP is to set the network (and pfsense IP) on your TP-Link to a public IP instead. That way pfsense will accept it as ok and directly try to reach out and update dyndns... Doesn't solve your problem but at least you can test that pfsense can get through to the service.
Also, wrt to DMZ, have you tried setting the pfsense IP as static in the TP-link router instead?? If I read things correctly you set that in pfsense WAN2 interface settings??
I always set static IP's in the router and never in a device. But sometimes when testing... I can't say for sure but I have a vague memory of something being off when doing it that way with the TP-Link.
-
@gblenn I found a very old Huawei E169 (3G) and a newer one ZTE MF833U1 (LTE).
The first one is on the supported list, but the ZTE is marked as:
Modems reported to work as Ethernet devices - whatever that means...I will test them today evening.
On Friday, my colleague will lend me a couple of his LTE routers and modems. I will update this post once I connect and test them.
@gblenn said in pfSense 2nd WAN behind LTE modem DMZ:
Have you rebooted the TP-Link? Restarted the WAN2 interface? Restarted the DDNS service on pfsense?
One way of fooling pfsense into picking up the IP is to set the network (and pfsense IP) on your TP-Link to a public IP instead. That way pfsense will accept it as ok and directly try to reach out and update dyndns... Doesn't solve your problem but at least you can test that pfsense can get through to the service.
Also, wrt to DMZ, have you tried setting the pfsense IP as static in the TP-link router instead?? If I read things correctly you set that in pfsense WAN2 interface settings??
I always set static IP's in the router and never in a device. But sometimes when testing... I can't say for sure but I have a vague memory of something being off when doing it that way with the TP-Link.
Thanks for the hints! I will test them today evening.
-
@siwyboy said in pfSense 2nd WAN behind LTE modem DMZ:
I found a very old Huawei E169 (3G) and a newer one ZTE MF833U1 (LTE).
The first one is on the supported list, but the ZTE is marked as:
Modems reported to work as Ethernet devices - whatever that means...
I will test them today evening.
On Friday, my colleague will lend me a couple of his LTE routers and modems. I will update this post once I connect and test them.I guess modems like that could work. But they are more of a temporary solution for mobile use, often with quite limited functionality. Might not even support DMZ or port forwarding...
But I still don't understand why pfsense can't access http://checkip.dyndns.org when you can do it from a device inside your network. It should not matter one bit if pfsense is actually in the DMZ or not! It's just simple web access through port 80, which clearly is working for devices inside the network.
BTW, do you have any firewall rules or tools (like suricata, pfBlocker) which may be interfering here?
-
@gblenn Kill me now...
Yesterday a new update pop up so I decided to install it.
2.7.0-DEVELOPMENT (amd64)
built on Tue Jan 24 06:07:01 UTC 2023
FreeBSD 14.0-CURRENTAfter the install, DDNS started to work and is now showing the correct public IP...
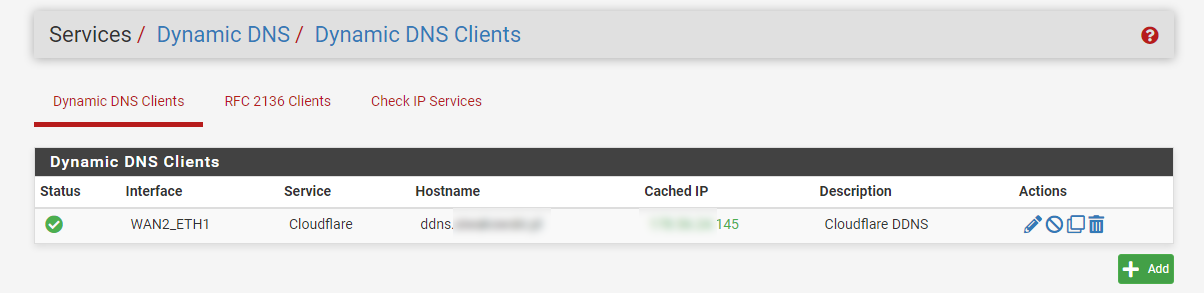
Right now, I need to figure out why it's still showing the TP-Link router login page even though I set up DMZ, changed the management port and management IP.
I think it might have something to do with the way how TP-Link is handling DMZ.PS
I don't use any tools like suricata, pfBlocker. I have very basic setup when it comes to packages.
I decided to use pfSense because it's much easier to setup vlans and firewall rules than on UI Edgemax routers.
-
First of all, great that it started working!!
Right now, I need to figure out why it's still showing the TP-Link router login page even though I set up DMZ, changed the management port and management IP.
I think it might have something to do with the way how TP-Link is handling DMZ.I don't see why it shouldn't... DMZ means all ports are open, not that the TP-Link "dissapears". It is still the gateway that pfSense "sees" and it's still doing NAT.
-
R rcoleman-netgate moved this topic from Routing and Multi WAN on