Using the wrong outgoing interface with the good origin IP
-
Hello,
I have the following configuration:TUNNEL IPSEC /WAN1 (IP1) ===================|---------| PFSENSE1/ |CISCO ASA| \ IPSEC TRANSPORT |__(IP3)__| \WAN2 (IP2) ===================One Netgate/pfSense whith HA with two WAN interfaces. I've configured one tunnel ipsec like this:
IP1 <--> IP3And our internet outgoing traffic is round-robin balanced using both interfaces. So far so good.
But I also want to connect to the same cisco asa from my laptop via VPN. To achieve this I want to use the following path:
IP2 <--> IP3The problem is I'm not able to achieve it. What is happening to me is when I connect from my laptop if I capture the traffic to the Netgate, I can see trafic outgoing from the WAN1 with the IP2. But I wan to use the WAN2 with the IP2 to reach the CISCO ASA.
Do you know what I could be doing wrong?
Thanks!
-
@galcorlo said in Using the wrong outgoing interface with the good origin IP:
But I also want to connect to the same cisco asa from my laptop via VPN.
You're running the second IPSec on the laptop?
-
@viragomann exactly. I want to have the vpn IPsec tunnel mode established and having the possibility to establish the VPN IPsec transport mode but with the other WAN interface.
With the traffic captures I can see the NAT working properly but I don't know how to override the route that force the traffic to use WAN1 instead of WAN2 -
@galcorlo
You can policy route the traffic to the WAN2 gateway.
Either route the whole upstream traffic out to WAN2 by the source IP of the laptop or only IPSec.
IPSec might use UDP on port 4500.However, what I don't understand is this statement:
if I capture the traffic to the Netgate, I can see trafic outgoing from the WAN1 with the IP2.
Outgoing packets on WAN2 should have the IP of WAN2, otherwise the communication might not work at all.
-
Thank you for your help @viragomann !
I needed more time to do more testing without causing affectation and for this reason until today I didn't answer you.
The point is I already did a policy route only for my laptop IP
192.168.11.64forcing the outgoing interface to be WAN2 but it seems to be ignored.
After debugging I think I have omitted some important information. Both WAN arepppoenegotiated with the same provider. My default route is:netstat -rn -f inet Routing tables Internet: Destination Gateway Flags Netif Expire default 192.168.144.1 UGS pppoe2So, a more accurate network scheme is:
TUNNEL IPSEC /WAN1 (pppoe2) (IP1) ===================___________ PFSENSE1/ |CISCO ASA| \ IPSEC TRANSPORT |__(IP3)__| \WAN2 (pppoe0) (IP2) ===================I am able to load balance traffic using both WAN interfaces but when I want to force the traffic to use the interface not configured as default gw (WAN2) it does not work. The traffic is routed through the WAN1 with the IP2. I know this was the part you did not understand. Neither did I, until I thought about
pppoeand the default gateway192.168.144.1that is a negotiatedpppoeaddress, not from my used range. Here my firewall rules:192.168.11.64my laptop IP
USUARIS netthe network where I am in
WAN2_FIBER_PPPOEoutgoing WAN2 interface
ALL_INTERNET_CONNa group that allows me to balance the traffic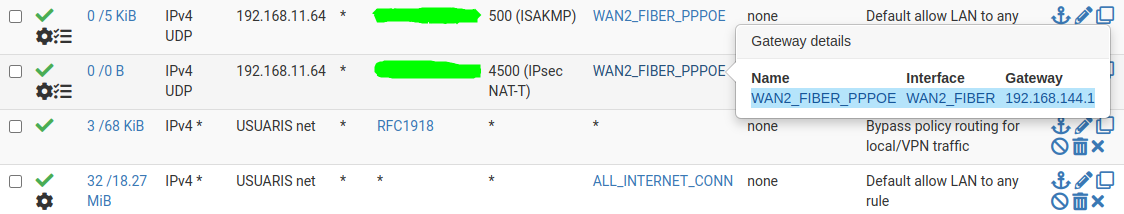
I hope with all the information you could give me some help to reach the vpn endpoint through the WAN2 instead of WAN1.
Thanks a lot!
-
@galcorlo
You have two WANs from the same ISP?
What's the WANs connected to? To an ISP modem, cable, DSL?What do the WAN settings show in Status > interfaces?
Apart from the PPPoE are there additional IPs assigned to the WAN interfaces?