Get internet on one LAN interface
-
@stoneedge if you have a vlan X, lets say its network is 10.0.20.0/24 with pfsense IP being 10.0.20.1
All devices on this vlan would use 10.0.20.1 as their gateway..
if you had another vlan 10.0.30.0/24 with pfsense IP in this interface 10.0.30.1, then all devices on this 10.0.30.0/24 network would use 10.0.30.1 as their gateway.
-
@stoneedge said in Get internet on one LAN interface:
Hello,
First time using pfsense and still struggling with some configurations.
First I am using pfsense on my Neste VMware environment
I have:
1 WAN: using an IP from my Internet router
1 LAN internal IP 10.0.10.2, both defaultWhat does "both default" mean?
This Management LAN is 10.0.10.1/24 same subnet has the LAN(default). Dont know if is a problem, if yes I can change the LAN IP.
Are you saying you have 2 vlans with the same subnet?
If so, yes, that's a problem and I can't believe pfSense would let you do it. Is that why you used .2 for your LAN address?I read that when we try to have a gateway on a LAN it will treat as a WAN. Not really what I want, but as long it works, I don't mind.
Are you referring to the IPv4 Upstream gateway setting in the interface config?
If so you don't use that. As John said .1 in each vlan would normally be the interface address and used as the gateway for that vlan. -
@stoneedge also as @Jarhead asks - your not setting a gateway on the interfaces in pfsense are you??
-
@johnpoz first thanks all for the replies. Will try to answer all the questions.
Full configuration:
Have vmxo - WAN with: 192.168.1.x (with IP from the internet router) with the gateway pointing to my internet router
vmx1 - LAN with:10.0.10.2/32 - no VLAN added
Then I have 7 VLANs
1 - 10.0.10.1/24
2 - 10.0.20.1/24
3 - 10.0.30.1/24
4 - 10.0.40.1/24
5 - 10.0.50.1/24
6 - 10.0.60.1/24
7 - 10.0.70.1/24All VLANs are assigned to the vmx1 LAN as parent interface. So I have vmx1.10, vmx1.20, vmx1.30, etc.
@Jarhead, there is no gateway on any of the LAN, only WAN as a gateway and is the IP of my internet router.
As I said, the internal local network is working ok. All VMs can reach each other(using the network 10.0.10.1/24, which also has DHCP from 10.0.10.10 to 10.0.10.150), and the gateway on those VMs is always the VLAN IP, in this case, 10.0.10.1.
So if VMS has an IP eq: 10.0.10.100 and has the gateway 10.0.10.1 cannot reach the internet. That is my problem here.
Is the problem because I am using the vmx1 LAN with no VLAN and IP 10.0.10.2?
Thanks again for the anwers.
SE
-
Just another update that could also be important. Inside of all my network(and switch), only the 192.168.1.x(local network) and 192.168.10.x(storage network) subnets is available and works.
In the Switch, I only use two ports where I added/trunk all the VLANs used on the pfsense, which are the ports connected to the pfsense LANs.Don't know if this is important or not.
But I added all the VLANs IP subnets to my switch.
-
@stoneedge So you aren't using the untagged traffic on vmx1, so don't assign it an address at all. Still don't see how pfSense would have let you assign it that address since it's part of vlan1. It should have told you that is overlapping.
So delete that address, then show your rules on the vlan interface for vlan1. Once that one works you can apply the fix to all. -
@stoneedge said in Get internet on one LAN interface:
Just another update that could also be important. Inside of all my network(and switch), only the 192.168.1.x(local network) and 192.168.10.x(storage network) subnets is available and works.
In the Switch, I only use two ports where I added/trunk all the VLANs used on the pfsense, which are the ports connected to the pfsense LANs.Don't know if this is important or not.
But I added all the VLANs IP subnets to my switch.
What does this mean? If you only have 2 ports assigned to the vlans, assuming one is the trunk, how would you ever access them?
-
@jarhead said in Get internet on one LAN interface:
@stoneedge said in Get internet on one LAN interface:
Just another update that could also be important. Inside of all my network(and switch), only the 192.168.1.x(local network) and 192.168.10.x(storage network) subnets is available and works.
In the Switch, I only use two ports where I added/trunk all the VLANs used on the pfsense, which are the ports connected to the pfsense LANs.Don't know if this is important or not.
But I added all the VLANs IP subnets to my switch.
What does this mean? If you only have 2 ports assigned to the vlans, assuming one is the trunk, how would you ever access them?
Sorry I did not understand that question.
2 Ports(one for each interface in the pysical ESXI) with the VLANs trunked.
How to access them? Creating a virtual Switch on ESXi and add the VLAN that I want(one or all, depeding what network I want to create for the VMs).If I have 2 VMs on VLAN 10 I add them to that Virtual Portroup, trunk also VLAN 10 inside the VM and that is it, they will use the VLAN 10
-
@stoneedge Ok, start over.
Do you have internet on the pfSense WAN? -
@stoneedge said in Get internet on one LAN interface:
So if VMS has an IP eq: 10.0.10.100 and has the gateway 10.0.10.1 cannot reach the internet. That is my problem here.
So can the vm ping the 10.0.10.1 IP? What rules do you have on this interface in pfsense. Pfsense only creates the default rule for the lan, when you fire up either a new interface or a vlan there are no rules. You have to add rule(s) to allow the traffic you want, ie say internet.
Also keep in mind with esxi - where are you doing the tags, is the vswitch/port group passing them to pfsense? Unless you set 4095 on the vswitch/port group pretty sure the tags are stripped.
-
@johnpoz you can set for all VLANs 4095 or set for Trunking for the VLANs you want. In this case, I add all the VLANs that I created in the pfsense.
Example:
Distributed Virtual Switch have pfsense VLANs
Port group have only specific VLAN (let's say, management and other Storage). You can do both ways.Yes VMs can ping each other and also the 10.0.10.1.
If pfsense has internet. Honestly never tested, the only thing I try was the update and it says that pfsense is up to date. I think that means it has internet. But I can double check.
-
@stoneedge said in Get internet on one LAN interface:
Yes VMs can ping each other and also the 10.0.10.1.
well what are the rules on this interface then... Did you mess with outbound nat on pfsense. If client can talk to the pfsense interface, and the rules allow it - it would have internet, if pfsense has internet. Unless outbound nat was wrong.
Or your rules on the interface are not allowing for dns that the client is using? So when you do a traceroute to say 8.8.8.8 what happens? you hit 10.0.10.1 as your first hop and then nothing?
-
@johnpoz I dont any have rules created. Then that is the problem :)
-
@stoneedge said in Get internet on one LAN interface:
I dont any have rules created. Then that is the problem :)
Yes VMs can ping each other and also the 10.0.10.1.
If you had "no" rules then you wouldn't be able to ping the interface even..
-
@johnpoz inside of the same isolated network, with the same VLAN, I think we can.
Is VMs running in the same ESXi host, so packages never go outside
-
@stoneedge if you have no rules on pfsense interface you wouldn't be able to ping it from that network.. If pfsense IP is 10.0.10.1 and you have no rules on the interface.. Then no you wouldn't be even able to ping it from 10.0.10.x - either you have rules on that interface allowing ping. Or you pinging something else and not pfsense.. If there are no rules on the interface to allow ping, you wouldn't be able to ping it..
-
@johnpoz these are the settings
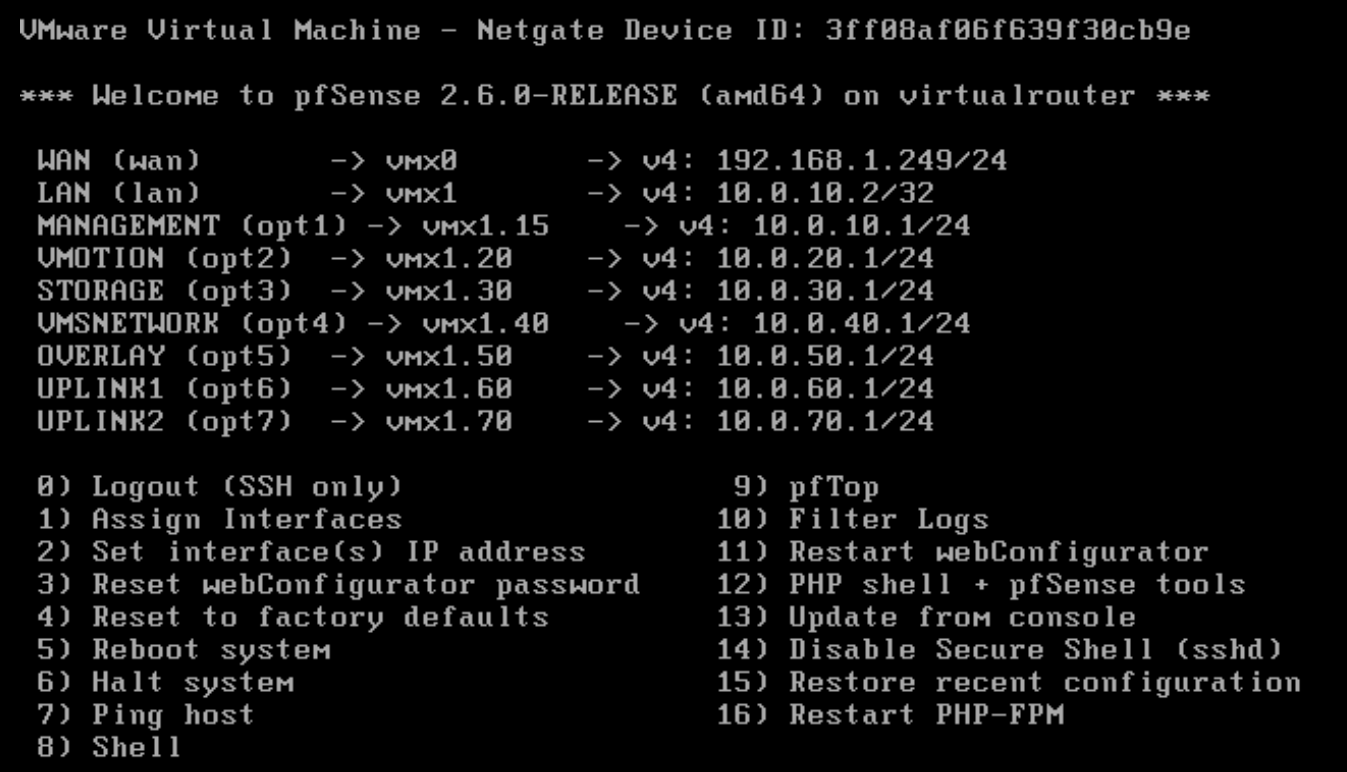
I have 3 VMs.
One with IP 10.0.10.3 (a DNS and DC)
Another is with DHCP 10.0.10.100 (DHCP is enabled on the LAN vmx1.15)
Another as a jump host 10.0.10.11All VMs are windows and all have in windows interface (VMware vmxnet3 virtual network) set trunk the VLAN 15.
And again, I can ping all IPs on the subnet 10.0.10.x(except the 10.0.10.2) from any of those VMs.Regarding the rules, sorry my previous statement was wrong. I have the default rules.
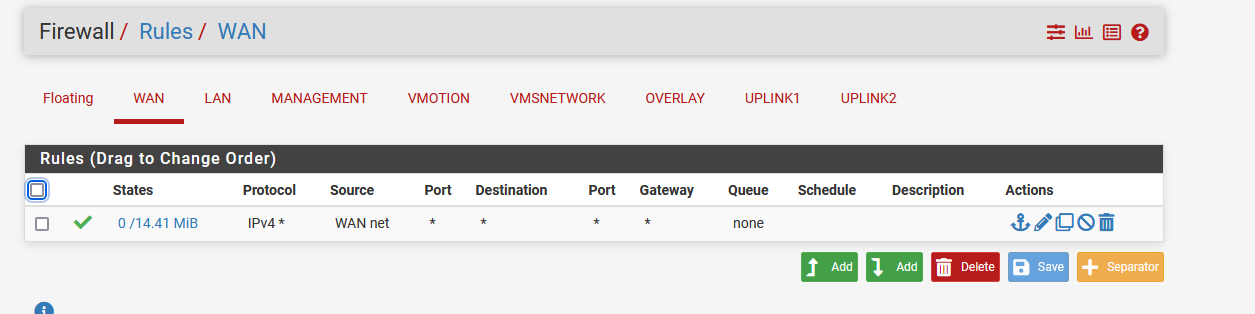
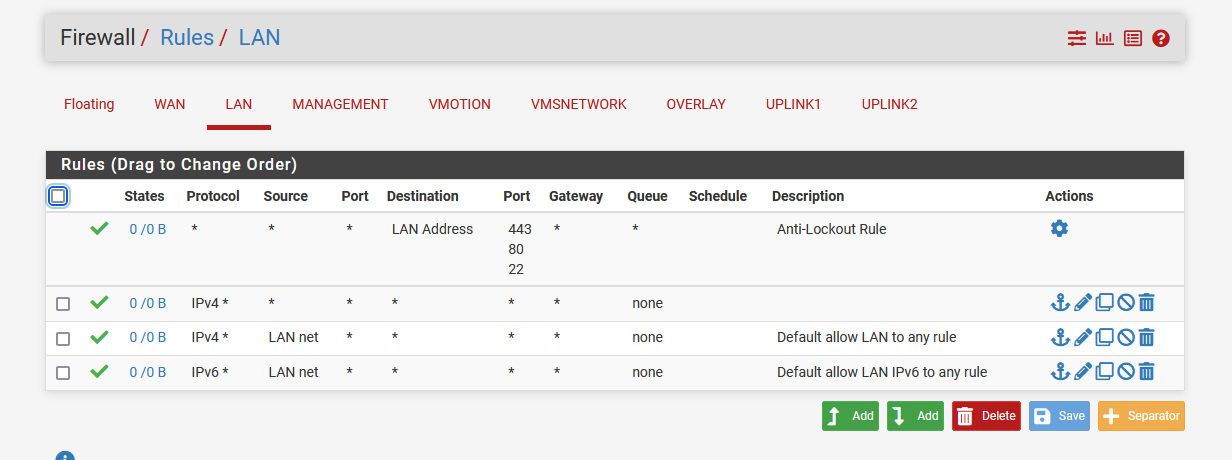
-
@stoneedge what rules do you have on the vlan interfaces? When you create a new interface/vlan there will be no rules. Are you saying you have a any any rule with the vlan as the source net for ipv4 any?
Also generally speaking a any rule on your wan like that is a really bad idea!!
Is anything even talking to pfsense? your rules on your lan all show zero evaluations - those 0/0 under the states table mean none of those rules have ever triggered.
-
@johnpoz honestly do not know what is impacting the configuration here.
But one thing is for sure, I am pinging this 10.0.10.1. Because if I disable it, ping doesn't work anymore.
Regarding the WAN, that is no problem here. This is my homelab, so firewall rules and security is not something that is to worry about much :)
So let us start over.
I need these 7 VLANs for my testing. What do you propose the configuration should be?
What should I change, and what rules should I create?
I think it is easier to start from scratch than try to do this.
And thanks again for the support.
-
@stoneedge First thing to do is get that /32 off your LAN interface.