Cannot get to shared folders
-
Let me try the images again. Maybe this will work in Chrome.
-
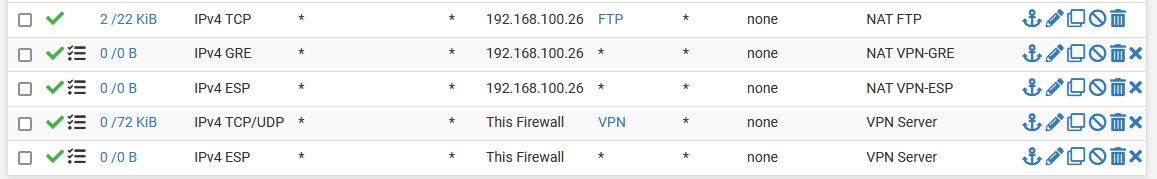
@dalicollins The IPsec rule is matching traffic (1 KiB). Did you look at the Windows Server Firewall?
-
@dalicollins
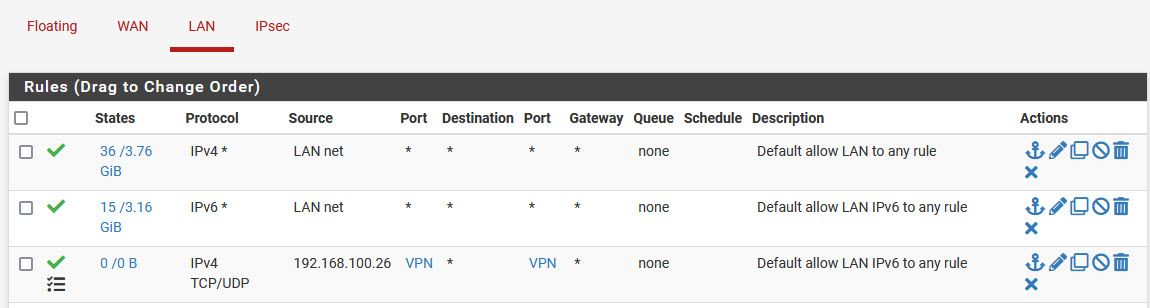
There is no need to pass GRE or ESP packets to the server if you run the IPSec server on pfSense itself.Also the rule on LAN might be useless as I don't think, that your server need to access something included in the VPN port alias.
And stating a source port is wrong in most cases. -
@viragomann
I disabled the ESP, GRE, and LAN rule. I can still connect, but not sure how to get access to the shares on IP 192.168.100.26. On another computer on the same subnet within Pfsense, if I use \192.168.100.26, I have full access to the shared folders. What URL would I use on the remote computer? If I use \10.3.3.1, which is the IP of the remote VPN, It opens, but nothing is there. -
@dalicollins
There are no WAN rules necessary for accessing the server. You only need to allow IPSec to pfSense WAN address there. But this is obviously working already.For passing traffic from the vpn client to the server the rules on the IPSec tab are relevant.
Use \\<IP>\<share> for access it. Same as from local devices.
Did you state the local subnet or at least the servers IP in the IPSec settings?
Did you already configure the servers firewall? Or disable it for testing.
-
@dalicollins I see the forum is escaping the double slash but to be clear it is
slash-slash-servername_or_ip
(as I noted above ;) )
If you've allowed IPv4 * you should also be able to ping the server, if you've allowed ICMP from the remote IP on the server's firewall
-
@viragomann
The Windows server firewall is disabled. You can see in the above pic the IPsec Rules. Is that correct? Using \192.168.100.26 returns 'Windows cannot access \192.168.100.26'
Pinging that IP shows 'Request timed out
I greatly appreciate the help. Thank you. -
@steveits
Nice. Need to double each backslash. -
@viragomann
I do double the backslash. The forum removes one in the post -
@dalicollins
I meant, I need to write them double to get one. -
@dalicollins
I forgot to ask one essential question: is pfSense the default gateway on the file server? -
@viragomann
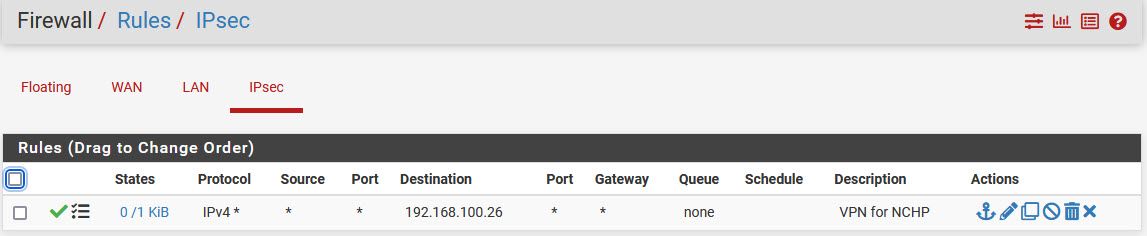
lol. I think I am really close. probably just missing a rule. Is the IPsec rule I show above correct? -
@dalicollins said in Cannot get to shared folders:
@viragomann
lol. I think I am really close. probably just missing a rule. Is the IPsec rule I show above correct?Yes, it allows any protocol to the server. So access to the file share should be allowed.
You can restrict it later if you want.
-
@viragomann
Yes there is only one default gateway and everything on pfsense uses it. All other functions of pfsense work great. But you brought up an interesting question. The server has two NIC's each connected to a different pfsense firewall. But the other computers on the same firewall can get to the shared folders. -
@dalicollins Your IPsec rule allows all traffic and is matching packets so should be fine.
[slash-slash-slash-text seems to work fine. It shows in the preview to the right while typing. ]
-
@dalicollins said in Cannot get to shared folders:
Yes there is only one default gateway and everything on pfsense uses it.
The question was if the server uses the pfSense running the IPSec server as default gateway.
Run
route printon the command line to show the default route.
-
@viragomann
On the server
IPv4 Route TableActive Routes:
Network Destination Netmask Gateway Interface Metric
0.0.0.0 0.0.0.0 192.168.100.1 192.168.100.26 1255
0.0.0.0 0.0.0.0 192.168.1.1 192.168.1.100 266
10.10.10.100 255.255.255.255 On-link 10.10.10.100 315
10.10.10.102 255.255.255.255 10.10.10.102 10.10.10.100 60
10.10.10.105 255.255.255.255 10.10.10.105 10.10.10.100 60
10.10.10.107 255.255.255.255 10.10.10.107 10.10.10.100 60
10.10.10.109 255.255.255.255 10.10.10.109 10.10.10.100 60
127.0.0.0 255.0.0.0 On-link 127.0.0.1 331
127.0.0.1 255.255.255.255 On-link 127.0.0.1 331
127.255.255.255 255.255.255.255 On-link 127.0.0.1 331
192.168.1.0 255.255.255.0 On-link 192.168.1.100 266
192.168.1.100 255.255.255.255 On-link 192.168.1.100 266
192.168.1.101 255.255.255.255 On-link 192.168.1.100 266
192.168.1.255 255.255.255.255 On-link 192.168.1.100 266
192.168.100.0 255.255.255.0 On-link 192.168.100.26 1255
192.168.100.26 255.255.255.255 On-link 192.168.100.26 1255
192.168.100.255 255.255.255.255 On-link 192.168.100.26 1255
224.0.0.0 240.0.0.0 On-link 127.0.0.1 331
224.0.0.0 240.0.0.0 On-link 192.168.100.26 1255
224.0.0.0 240.0.0.0 On-link 192.168.1.100 266
224.0.0.0 240.0.0.0 On-link 10.10.10.100 315
255.255.255.255 255.255.255.255 On-link 127.0.0.1 331
255.255.255.255 255.255.255.255 On-link 192.168.100.26 1255
255.255.255.255 255.255.255.255 On-link 192.168.1.100 266
255.255.255.255 255.255.255.255 On-link 10.10.10.100 315Persistent Routes:
Network Address Netmask Gateway Address Metric
0.0.0.0 0.0.0.0 192.168.1.1 Default
0.0.0.0 0.0.0.0 26.0.0.1 9256
0.0.0.0 0.0.0.0 192.168.100.1 Default
0.0.0.0 0.0.0.0 192.168.1.1 Default192.168.1.1 is the IP going to the other pfsense firewall.
10.10.10.100 is the servers internal Windows VPN which is what I want to switch the uses from. -
@dalicollins said in Cannot get to shared folders:
192.168.1.1 is the IP going to the other pfsense firewall.
So access from the VPN cannot work.
This would be worth to mention at first of all.To get access you have to either add a static route to the server for the VPN tunnel pool and point it to the IPSec pfSense or you can masquerade the outgoing traffic on pfSense.
However, if the other router is a pfSense as well, I'm wondering why you fire up an additional to run a VPN on it.
-
@viragomann
Not sure how to do that. I also tried changing the IPsec rule to an IP of a local computer with only one connection and I can ping that IP. So how do I masquerade the outgoing traffic? -
@dalicollins
Masquerading is only recommended if you know, what it does and if you have restrict firewall rules. It's a workaround for different issues.
But since this VPN is obviously for your own purposes only, you can do this to get a step beyond.It's done by Firewall > NAT > Outbound
Select hybride mode and save this first.
Add a new rule:
interface: LAN
source: IPSec tunnel pool (or maybe any, since there is no other passing this pfSense)
destination: any
translation: interface addressShould work then.