Routing Traffic From VPN To WAN
-
@aiden21c Interesting case...
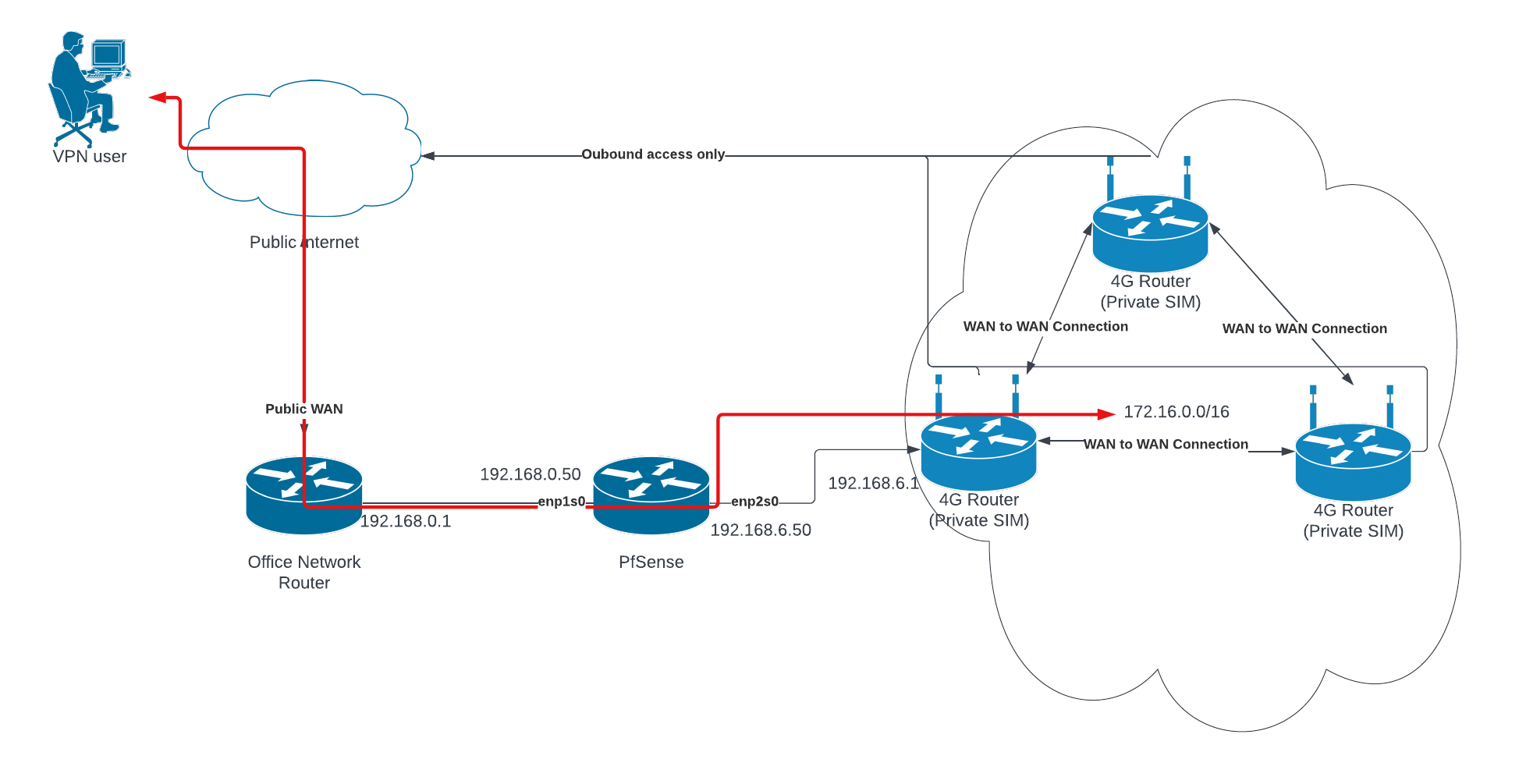
I'm thinking that the VPN user, when terminating inside the Office Network, needs to have pfsense as it's "gateway" somehow. I might be wrong but I think any attempts to reach the 172 network will simply hit the Office router and be lost.So perhaps a first step would be to set up the office router so that any traffic going to 172.16.0.0/16 will be routed towards 192.128.0.50. Unless that is possible to define in the VPN setup itself?
-
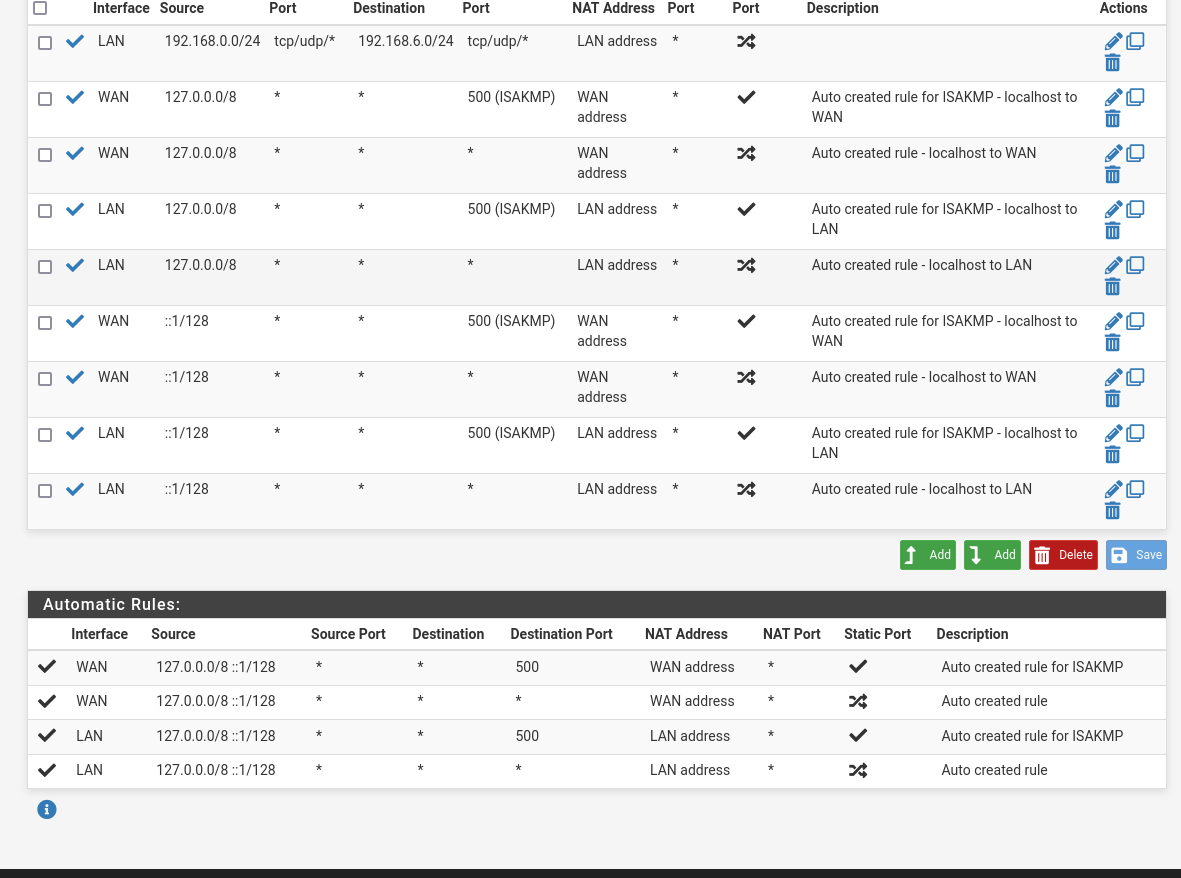
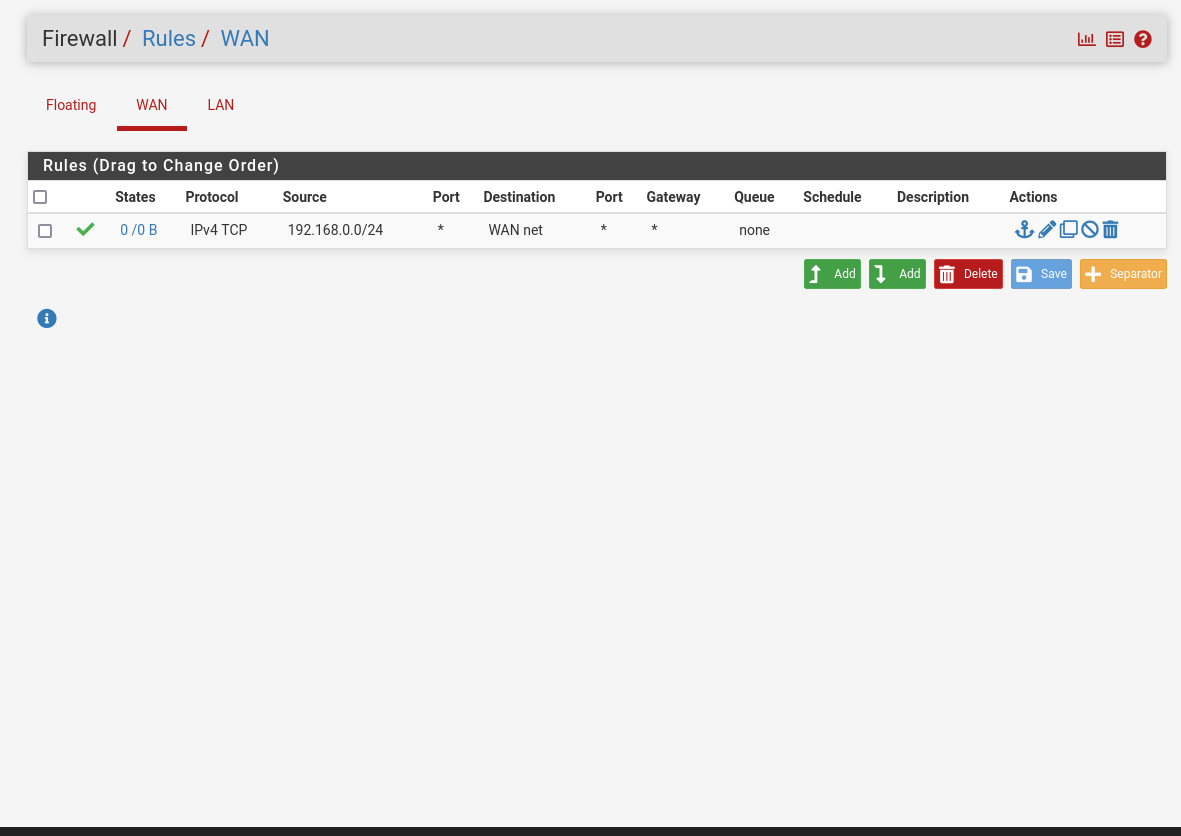
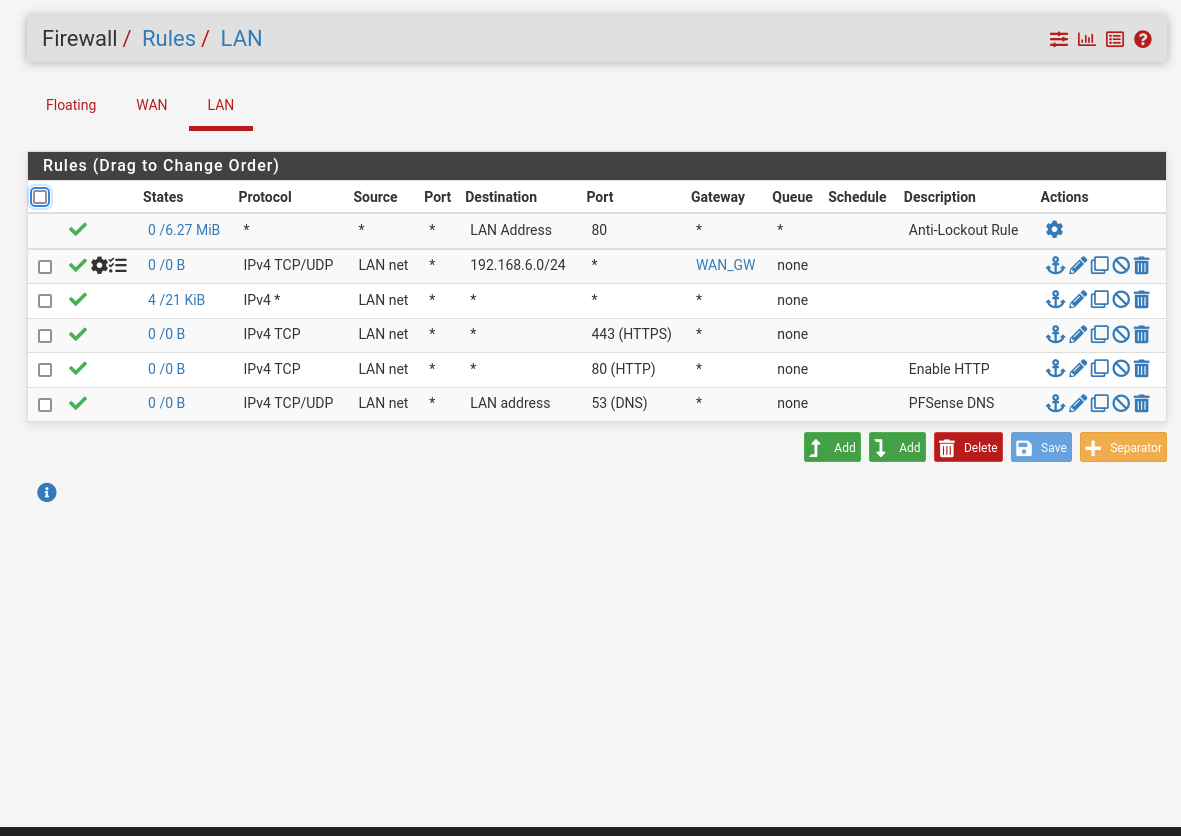
@gblenn this would definitely be my guess of what to do, but I'm struggling with even routing traffic from 192.168.0.50 to the network in 192.168.6.50 and then using this WAN. Would you be able to have a quick look at my firewall rules and maybe help me out in figuring out why I cannot ping 192.168.6.1 from the LAN?
-
@gblenn Perhaps this could work...??
Change the interface settings so that pfsense has two WAN ports. Essentially a failover scenario where WAN1 (default=PRI1) is the office network and WAN2 (PRI2) is the mobile router network.
You obviously need to access the UI so either use a third interface for that (LAN) or configure the office Eth-port with VLAN.The VPN tunnel needs to be set up in pfsense, not inside the office network. Then you can policy route any traffic in pfsense so that 172 goes out via WAN2 towards the mobile network.
Of course now you have a double NAT scenario from a VPN-tunnel perspective, which may present some challenges of course. -
@aiden21c said in Routing Traffic From VPN To WAN:
@gblenn this would definitely be my guess of what to do, but I'm struggling with even routing traffic from 192.168.0.50 to the network in 192.168.6.50 and then using this WAN. Would you be able to have a quick look at my firewall rules and maybe help me out in figuring out why I cannot ping 192.168.6.1 from the LAN?
You should really read up on how rules are evaluated. Your rules aren't doing what you think they are.
Chances are you can't ping 6.1 because you have the gateway of the device your pinging from as the office router.
-
@jarhead just wondering if you could elaborate on this? I am simply trying to ping from the LAN interface using the ping diagnostic tool inside the PFsense. I'm not sure exactly how to route the traffic between the interfaces because I'm pretty sure it has to do with firewall rules that are incorrect. The gateway of the LAN interface is in fact the office router as you suspected, however I had the same issues when I set the gateway to "none".
-
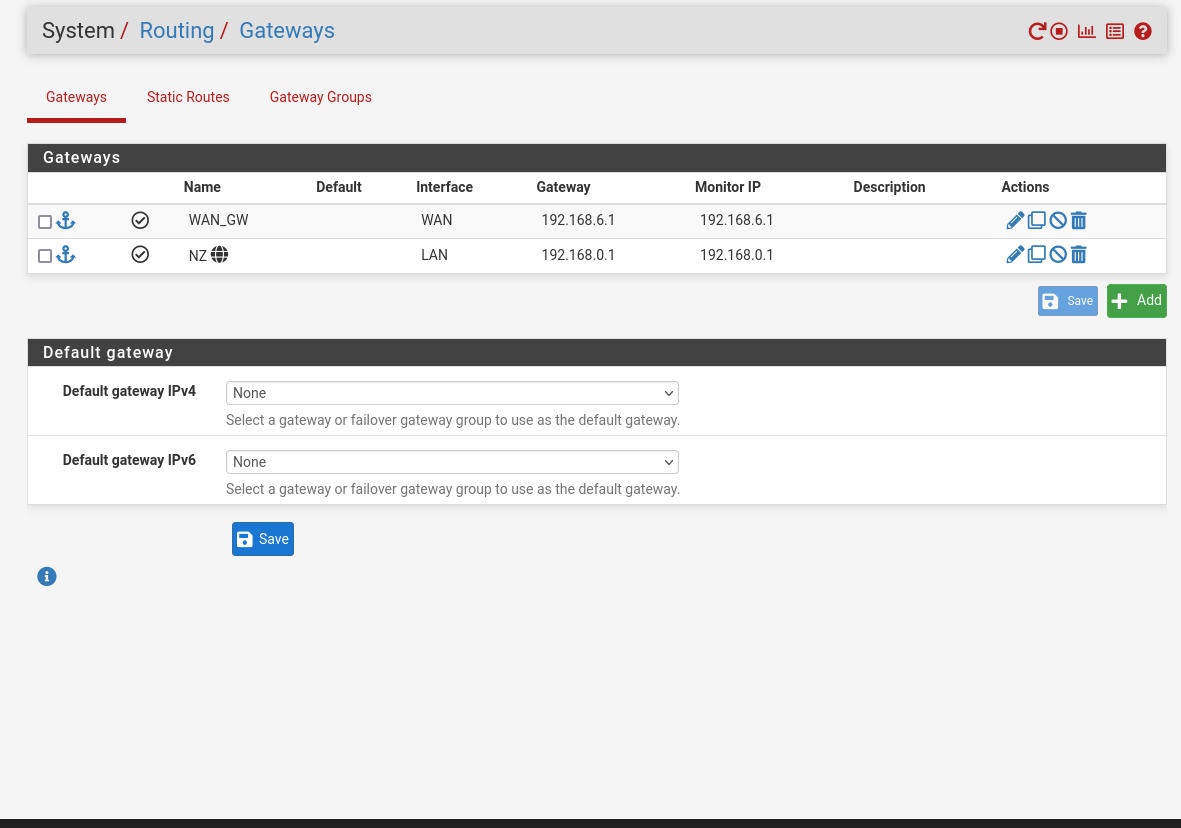
@aiden21c Perhaps I was wrong in talking about "policy route to 172". In the setup with dual WAN I guess you would rather set up a static route. System > Routing > Static routes
Destination network 172.16.0.0/16
Gateway WAN2. -
@aiden21c said in Routing Traffic From VPN To WAN:
@jarhead just wondering if you could elaborate on this? I am simply trying to ping from the LAN interface using the ping diagnostic tool inside the PFsense. I'm not sure exactly how to route the traffic between the interfaces because I'm pretty sure it has to do with firewall rules that are incorrect. The gateway of the LAN interface is in fact the office router as you suspected, however I had the same issues when I set the gateway to "none".
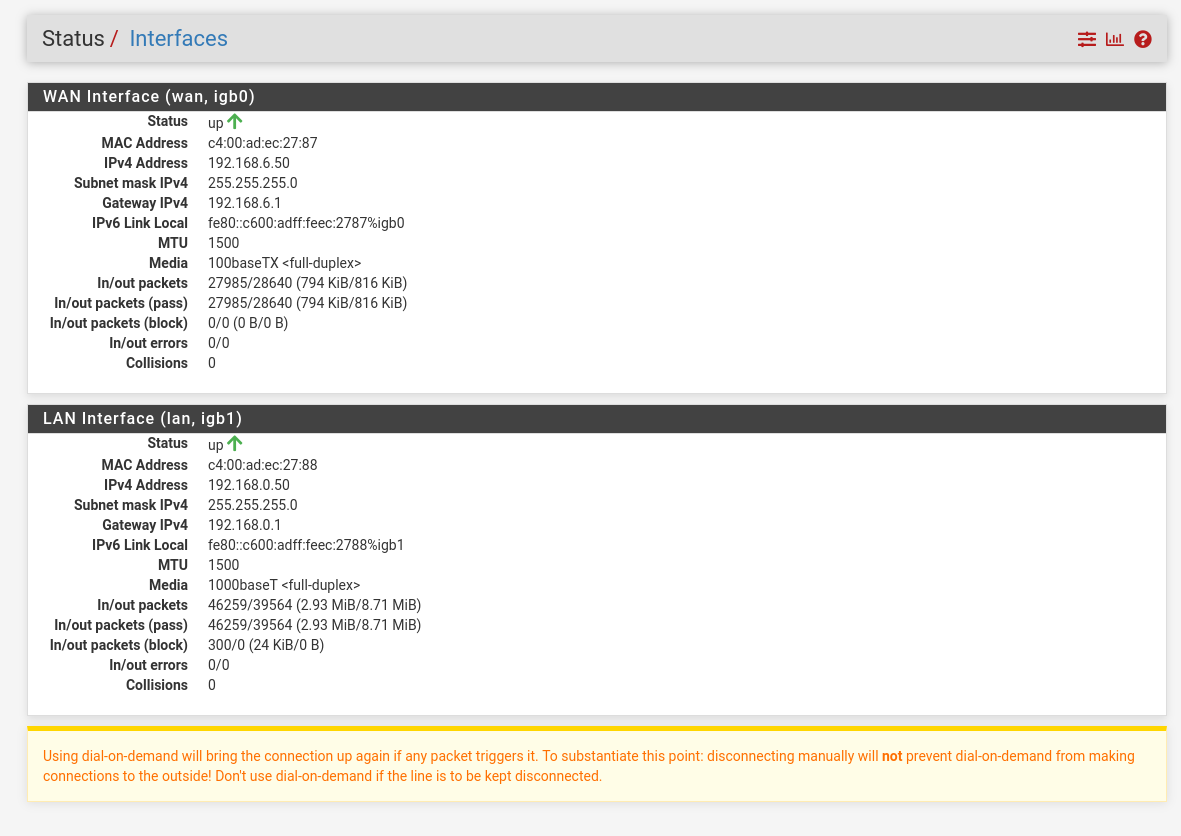
Without any special firewall rules, you should be able to ping anything that is on the WAN side of pfsense. But if you are pinging from a PC in the office network, you need to change the IP settings on it so that it's gateway is 192.168.0.50 (not 0.1 which is the office router).
-
@gblenn does this mean that I need to change the gateway on the LAN interface of the pfsense iteself to have a gateway of its own IP (192.168.0.50)? You can see in a few of my images above my failed traceroute and my current gateway settings. Does this have to do with setting up a dual wan setup?
-
@aiden21c said in Routing Traffic From VPN To WAN:
@gblenn does this mean that I need to change the gateway on the LAN interface of the pfsense iteself to have a gateway of its own IP (192.168.0.50)? You can see in a few of my images above my failed traceroute and my current gateway settings. Does this have to do with setting up a dual wan setup?
I mean that you need to create a hierarchy and "move" pfsense down one level below the office router. Right now they both have their LAN sides connected. And only one can be the "master" = gateway and DHCP server, which is the office router.
If you change the LAN port on pfsense to be a second WAN port (or first rather). PfSense drops down to sit at the same level as all the clients in the office network.
Then you need to have the VPN tunnel go all the way down on to the LAN side of pfsense, where it now can be routed as you want. Where in this case you want all the 172 traffic to go out the second WAN port = the 6.1 network. After that it's up to the mobile router to handle things and get it to the destination.
-
If the VPN user needs to access the office network as well as the 172 network, the tunnel needs to have both 172.16.0.0 /24 and 192.168.0.0 /24 as allowed IP's.
And under System > Routing > Static Routes in pfsense, you need to have both these IP's. The difference will be that 172 will use WAN2 as the Gateway and the 192 IP will have WAN1 as Gateway.I actually have a somewhat similar setup at our cottage. I have a site to site wireguard tunnel set up and we use an LTE-router for failover in the cottage. So the pfsense router there has two WAN ports, one with a public IP, and one with a private IP from the LTE router.
To be able to access the LTE routers management interface, I have set a static route for 192.168.2.0 /24 towards WAN2 (the LTE router).
The only difference here would be that where I have a public IP, you have the office router in between. And having double NAT may present a problem in itself. You obviously need to do a port forward for the VPN tunnel towards pfsense...