Can't talk back from remote host over VPN
-
To start off, thank you for taking your time to read this.
Big Picture Goal:
I would like to use my Netgate 1100 to VPN (OpenVPN) to a lab environment (https://academy.hackthebox.com/) and be able to have full communication both ways.Setup:
Interface 1: WAN
Interface 2: Home LAN
Interface 3: Home Lab
Interface 4: OpenVPN to HTBA
Firewall allows all traffic on interface 3 and 4 (any any any....)
VLAN was automatically set up on interfaces 1/2/3
I am on the latest version of pfSense +
When I started having problems I put it back to factory settings so assume defaults for anything not above.Working:
I can WinRM/Ping/RDP into the remote host from Home Lab over OpenVPN.
OpenVPN reports connected and good for both server and client.
Home LAN and Home Lab has full access to WAN going out.Problem:
I am unable to WinRM into a Windows host in the remote lab and ping back to any host on my Home Lab. I am able to ping the Interface 4's IP but that is as deep as it gets.My Thoughts so far:
First thought of routes but dismissed because i can ping the Interface 4's IP from the remote lab.
Second, firewall, I added full open rules to interface 3 and 4 so I don't think that is the problem.
I am currently thinking it is a VLAN problem, the Home Lab is on a VLAN but I see no way to have the OpenVPN on the same VLAN.Any thoughts or suggests anyone has would be awesome.
-John
-
It probably is a missing route. The routers at both sides have an interface in the VPN tunnel subnet so the ping from the remote host is correctly routed over the VPN. pfSense has a route to the remote subnet since you are able to ping it so it can reply to those incoming pings.
However the remote side probably doesn't have a route to your local Home Lan subnet.Pings from there to the remote host probably work because pfSense is NATing the outbound traffic to the OpenVPN address.
Is the 1100 the OpenVPN client in this setup?
Do you have access to the OpenVPN server?
If so you need an iroute to your HomeLab subnet via your OpenVPN client.
Steve
-
Sounds like I should have dug deeper in my first path.
Yes, the 1100 is the OpenVPN client.
No, I don't have access to the server.After some reading I have an idea of what I need to do but I am missing some understanding.
Idea:
Make a gateway for my internal LAN (interface 3 Home Lab).
Make a static route pointing any 10.1.1.1/24 traffic to it.
(Idea source: https://www.youtube.com/watch?v=oIN9wMC80rA)I am getting conflict errors and after changing a few things I still have no luck.
Home Lab 10.1.1.1/24
Remote Lab 10.10.14.0/23 & 10.129.0.0/16Picture = 1000 words:
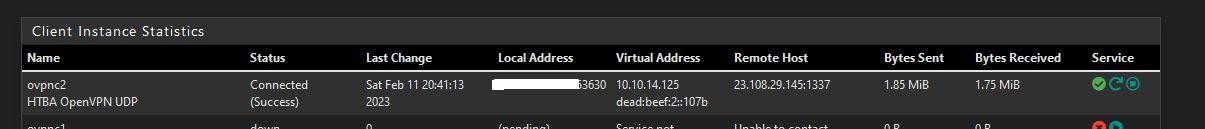
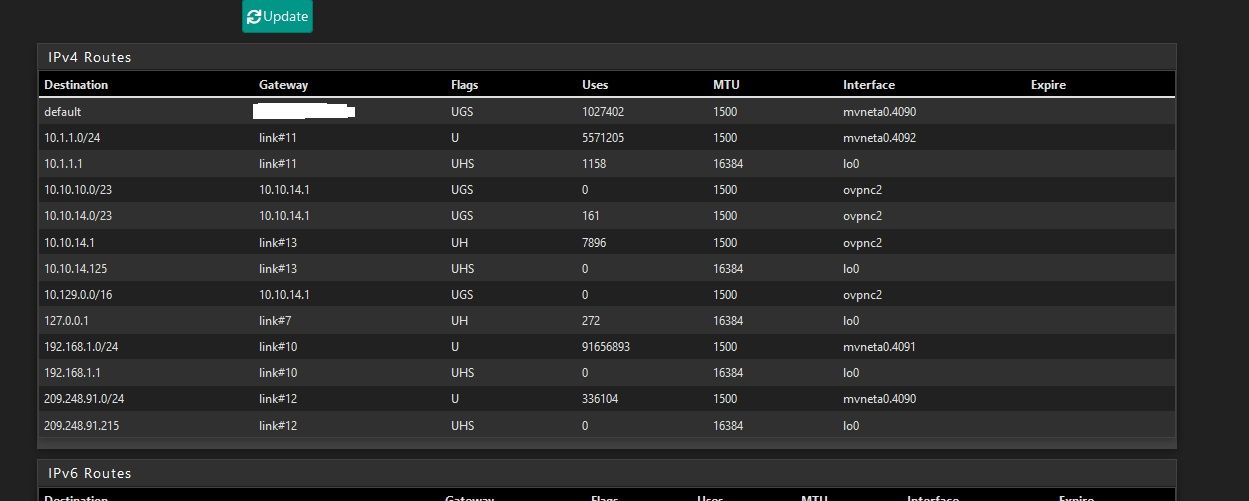
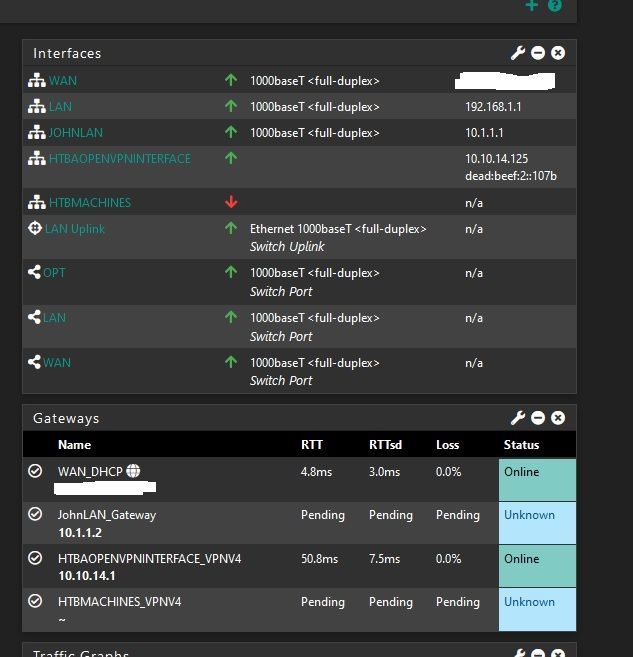
-
You will need a route at the server end to be able to open connections from there back your home lab subnet directly. Otherwise the router there has no idea where 10.1.1.0/24 is.
If it's for specific things you can port forwards on the OpenVPN interface in the 1100 to forward traffic to targets on your home lab subnet. Then open connections to them using the OpenVPN interface address, 10.10.14.125. If that's not static it becomes more complex.
Steve
-
@stephenw10 Perfect, that worked. Unfortunately the IP changes from time to time but it is for lab work so it is easy to edit the forward entry when needed.
-John
-
Depending on how the remote router is configured you might be able to use the hostname to access the 1100 OpenVPN interface. it would need to be setup to resolve OpenVPN clients.
You can always setup multiple port forwards with different incoming ports if you need to access several hosts behind the 1100.
Steve