Unable to check for updates (SOLVED)
-
Is it too much to ask for, to just release the installer for the latest version of pfsense plus. Here I am trying to resolve an issue with PFSense Plus 22.5 resulting in me having to do a fresh install. As other recovery methods aren't working, And in normal circumstances with my situation, The easiest method would be to just do a fresh install, and use my backup config to recover and go on with my day. But I cant simply install PFSense Plus, restore my backup. and get back to where I was and what I was working on. Instead I have to install an out outdated version of CE, upgrade that, Then upgrade that to PFSense Plus, 22.1 Then upgrade that again to 22.5. But for whatever reason, CE is having issues unable to check for updates. So, 5 fresh installs failed attempts later, multiple issues during one required update process or the next. An hour+ of my time wasted dealing with update issues trying to get an outdated version of CE to update Just so I can get to the point where I get PFSense Plus to install, so I can update that and Finally get to the current Non BETA version.
-
It should be possible to go from 2.6 to 23.01 directly once it's released. It will probably be possible to go from 2.7 but that is a moving target.
Other options are in development. -
@stephenw10 im in the same boat where i have remote sites, and to backdate firmware, i have to travel to site, backup, and install firmware from USB. I think it should be as easy to roll back firmware as it is to update. PS Sense is constantly informing you that there is an update, only to update and them find out there are issues.
-
If you're running a ZFS install and update from 22.05 to 23.01 it will automatically create a snapshot before the update and you can roll back it simply by selecting it.
-
@techpro2004 This just worked for me also. Was on 22.01-RELEASE and getting the "unable to check" error, 22.05 now shows as available.
-
I am having a similar issue on 5100. The difference being, I can see my installed packages, but the Available Packages is empty, nor is it able to check for system updates.
I have checked the pfSense.conf file. It looks to be correct (from what others have posted).
I have also tried switching to the development branch, then back.
pkg -d updateDBG(1)[96943]> pkg initialized
Updating pfSense-core repository catalogue...
DBG(1)[96943]> PkgRepo: verifying update for pfSense-core
DBG(1)[96943]> PkgRepo: need forced update of pfSense-core
DBG(1)[96943]> Pkgrepo, begin update of '/var/db/pkg/repo-pfSense-core.sqlite'
DBG(1)[96943]> Request to fetch pkg+https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-core/meta.conf
DBG(1)[96943]> opening libfetch fetcher
DBG(1)[96943]> Fetch > libfetch: connecting
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-core/meta.conf with opts "i"
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-core/meta.conf with opts "i"
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-core/meta.conf with opts "i"
DBG(1)[96943]> Request to fetch pkg+https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-core/meta.txz
DBG(1)[96943]> opening libfetch fetcher
DBG(1)[96943]> Fetch > libfetch: connecting
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-core/meta.txz with opts "i"
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-core/meta.txz with opts "i"
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-core/meta.txz with opts "i"
pkg: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-core/meta.txz: No address record
repository pfSense-core has no meta file, using default settings
DBG(1)[96943]> Request to fetch pkg+https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-core/packagesite.pkg
DBG(1)[96943]> opening libfetch fetcher
DBG(1)[96943]> Fetch > libfetch: connecting
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-core/packagesite.pkg with opts "i"
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-core/packagesite.pkg with opts "i"
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-core/packagesite.pkg with opts "i"
pkg: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-core/packagesite.pkg: No address record
DBG(1)[96943]> Request to fetch pkg+https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-core/packagesite.txz
DBG(1)[96943]> opening libfetch fetcher
DBG(1)[96943]> Fetch > libfetch: connecting
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-core/packagesite.txz with opts "i"
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-core/packagesite.txz with opts "i"
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-core/packagesite.txz with opts "i"
pkg: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-core/packagesite.txz: No address record
Unable to update repository pfSense-core
Updating pfSense repository catalogue...
DBG(1)[96943]> PkgRepo: verifying update for pfSense
DBG(1)[96943]> PkgRepo: need forced update of pfSense
DBG(1)[96943]> Pkgrepo, begin update of '/var/db/pkg/repo-pfSense.sqlite'
DBG(1)[96943]> Request to fetch pkg+https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-pfSense_plus_v22_05/meta.conf
DBG(1)[96943]> opening libfetch fetcher
DBG(1)[96943]> Fetch > libfetch: connecting
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-pfSense_plus_v22_05/meta.conf with opts "i"
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-pfSense_plus_v22_05/meta.conf with opts "i"
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-pfSense_plus_v22_05/meta.conf with opts "i"
DBG(1)[96943]> Request to fetch pkg+https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-pfSense_plus_v22_05/meta.txz
DBG(1)[96943]> opening libfetch fetcher
DBG(1)[96943]> Fetch > libfetch: connecting
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-pfSense_plus_v22_05/meta.txz with opts "i"
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-pfSense_plus_v22_05/meta.txz with opts "i"
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-pfSense_plus_v22_05/meta.txz with opts "i"
pkg: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-pfSense_plus_v22_05/meta.txz: No address record
repository pfSense has no meta file, using default settings
DBG(1)[96943]> Request to fetch pkg+https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-pfSense_plus_v22_05/packagesite.pkg
DBG(1)[96943]> opening libfetch fetcher
DBG(1)[96943]> Fetch > libfetch: connecting
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-pfSense_plus_v22_05/packagesite.pkg with opts "i"
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-pfSense_plus_v22_05/packagesite.pkg with opts "i"
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-pfSense_plus_v22_05/packagesite.pkg with opts "i"
pkg: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-pfSense_plus_v22_05/packagesite.pkg: No address record
DBG(1)[96943]> Request to fetch pkg+https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-pfSense_plus_v22_05/packagesite.txz
DBG(1)[96943]> opening libfetch fetcher
DBG(1)[96943]> Fetch > libfetch: connecting
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-pfSense_plus_v22_05/packagesite.txz with opts "i"
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-pfSense_plus_v22_05/packagesite.txz with opts "i"
DBG(1)[96943]> Fetch: fetching from: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-pfSense_plus_v22_05/packagesite.txz with opts "i"
pkg: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-pfSense_plus_v22_05/packagesite.txz: No address record
Unable to update repository pfSense
Error updating repositories!I also made sure ".pfsense.org" & ".netgate.com" were in the DNSBL whitelist.
Any ideas for me to try?
Thanks
-
@jossk said in Unable to check for updates (SOLVED):
pkg: https://firmware.netgate.com/pkg/pfSense_plus-v22_05_amd64-pfSense_plus_v22_05/packagesite.txz: No address record
Unable to update repository pfSense
Error updating repositories!No address record means it cannot resolve the repo server so you have a DNS issue on the firewall. Go to Diag > DNS Lookup and resolving
firmware.netgate.com. Make sure you are seeing results from the configures servers.Steve
-
Host "firmware.netgate.com" could not be resolved.
Name Servers:
127.0.0.1 ----> No ResponseSystem > Gen. Setup set to "Use Local DNS, ignore remote DNS Servers".
So I guess I have a misconfiguration in the DNS Resolver, then?
-
Yes, I would think so. And you have no other servers configured or being passed? They won't be used with that setting in general setup though.
-
I added all of my interfaces as DNS servers in General Setup. Only 2 interfaces are having issues, the loopback (127.0.0.1), and one other network.
With any of those added, pfS can check for system updates, and the Package Manager can load the Available Packages.
Knowing that, I'm more inclined to think that the more likely cause is a firewall config.
Cursory glance at my firewall rules doesn't show anything that should block these 2 interfaces.
I'll have to keep investigating.
Thank you for the idea. Now I have a direction and a stop-gap solution until I get it working properly.
-
@jossk said in Unable to check for updates (SOLVED):
I added all of my interfaces as DNS servers in General Setup.
Not sure exactly what you did but that's probably not what you want. The list there should contain other remote DNS servers that pfSense itself can use. It doesn't need to contain localhost, that is used anyway. The behaviour it uses those in can be set there but by default it will try localhost (Unbound on the firewall) and fall back to others in the list or servers passed by dhcp.
But since making any change there allowed it to work it's definitely a DNS problem.
Steve
-
Sorry, I should have clarified. I did that just to test all of my interfaces to see if my other interfaces were working or not. After verifying they worked, I deleted those from the list.
Also, changing to "Use local DNS (127.0.0.1), fall back to remote DNS", it tests localhost without me having to add it manually.
If that's the case, here is screenshots of my DNS Resolver config. Is there anything that stands out that could be the cause?
Note: I have a firewall rule to block external DNS servers. Mostly so IoT devices with hard coded DNS will be forced to use mine.
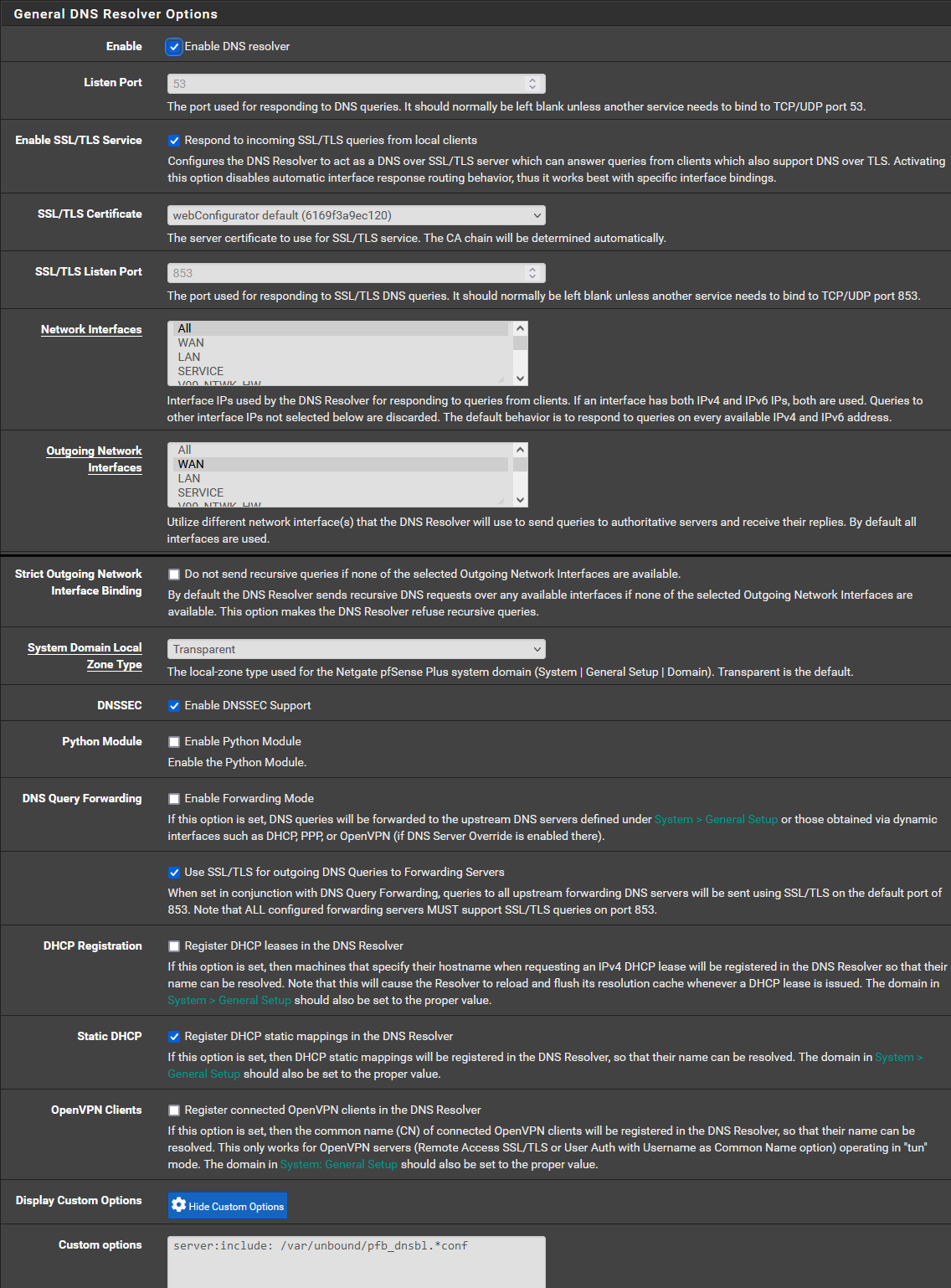
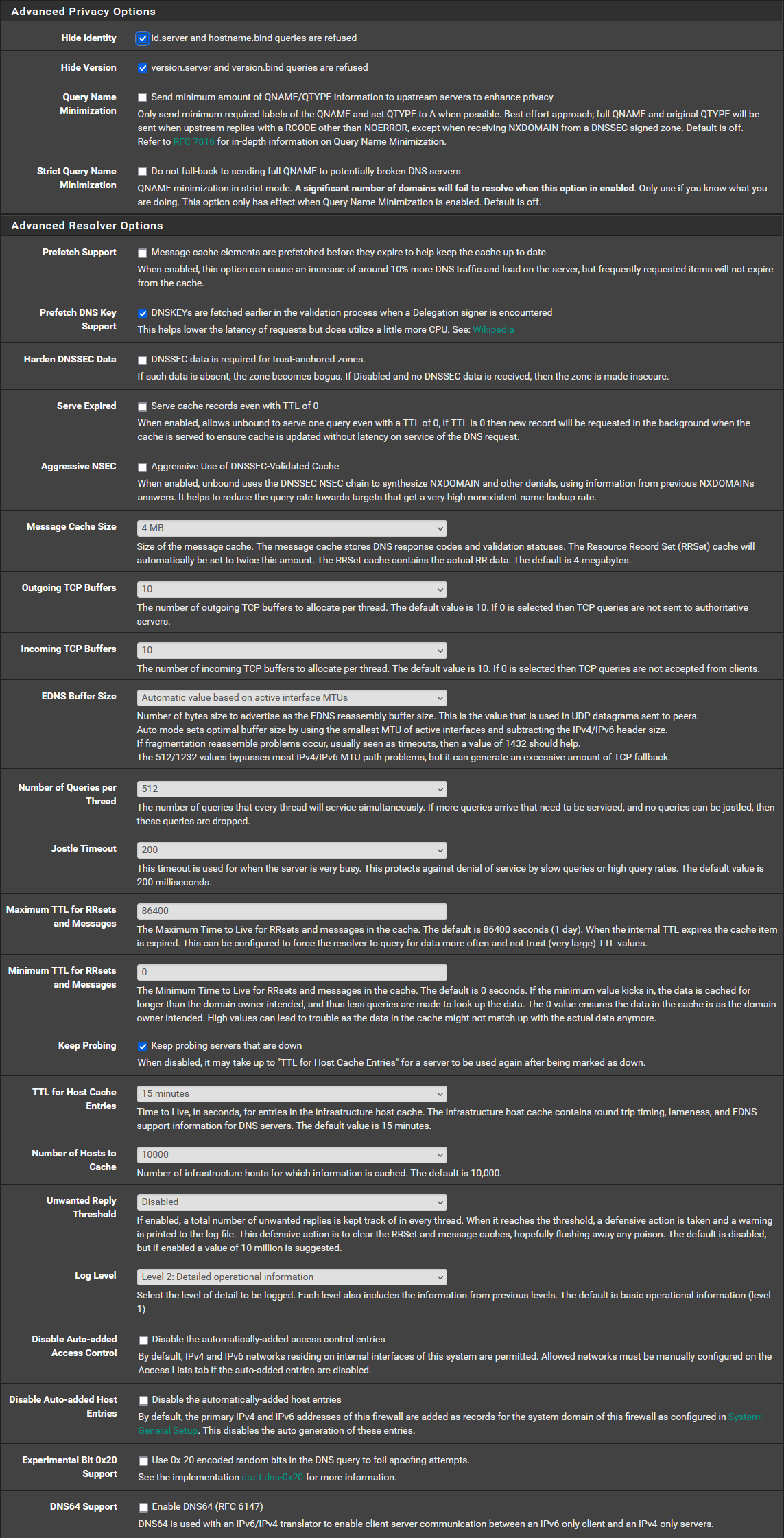
-
Try disabling SSL/TLS for outgoing queries. That should only ever be set in conjunction with forwarding mode.
Also you are filtering responses there using pfBlocker/DNSBL. Check the pfBlocker alerts. -
Disabled SSL/TLS for outgoing. No change in DNS Lookup (will leave off).
To be honest, I don't know what I should be looking for in the alerts.
I did try disabling pfBlocker. No change in DNS Lookup.
I can try turning off "Keep Settings", and uninstalling the pfBlocker package.
I'm still confused as to why DNS resolution works on my VLAN interfaces work, while not working on my LAN and loopback.
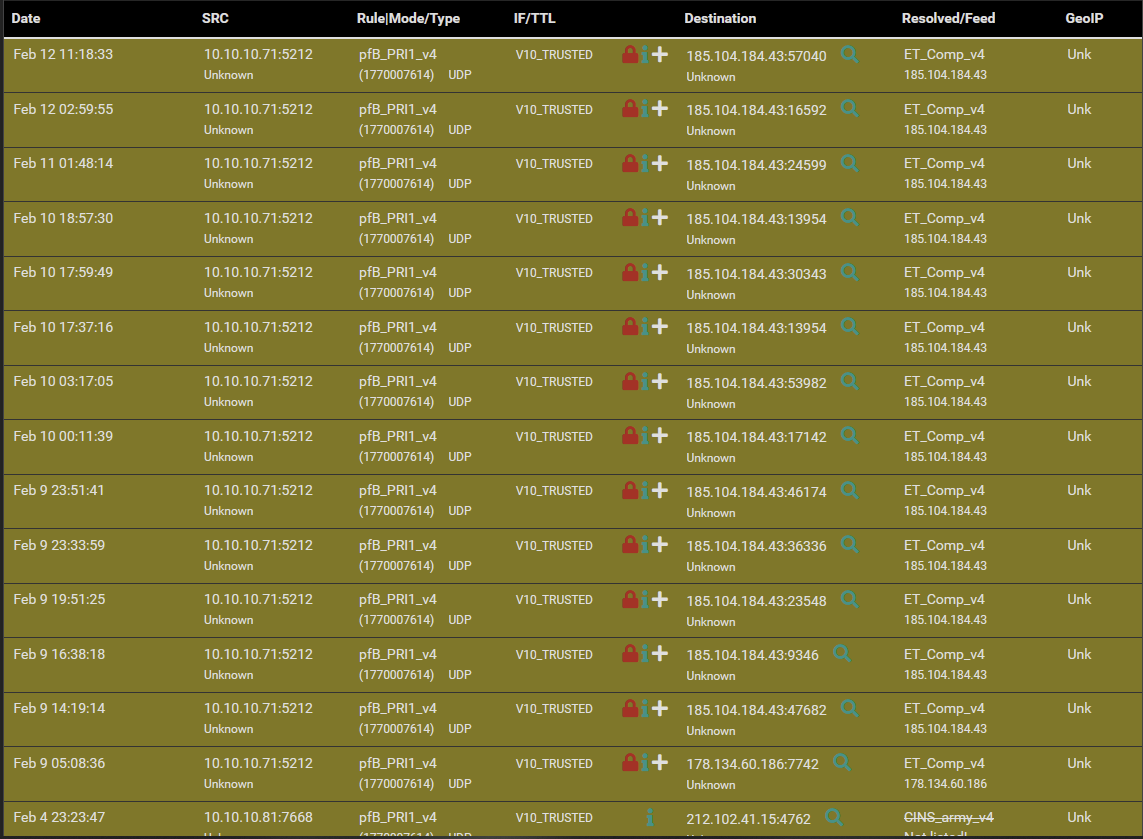
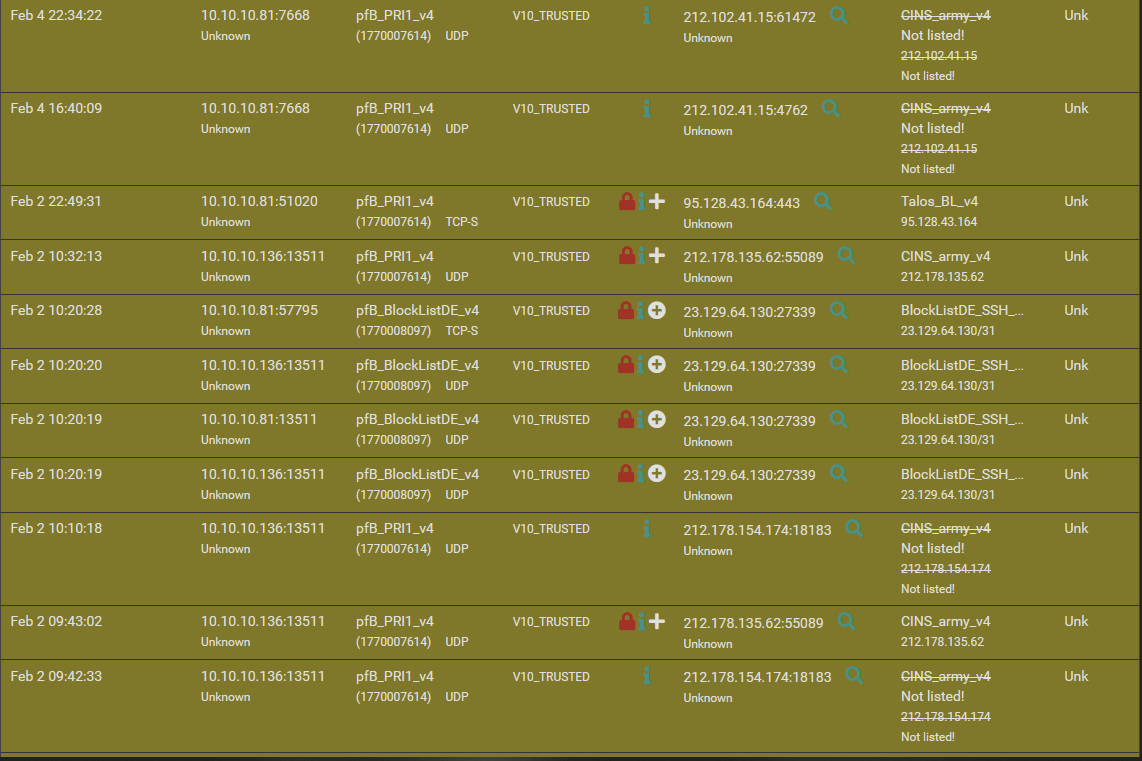
-
Check Status > DNS Resolver after you try to look it up. You should see entries for netgate.com.
Otherwise you can try turning up the logging in Unbound to see the individual queries and failures.
Steve
-
I see 2 entries for netgate.com.
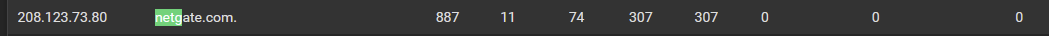

I also turned up logging to
Level 3: Query level informationin DNS Resolver > Advanced Settings.(Keep in mind I still have one of my (working) VLANs in my DNS servers list)
-
@jossk said in Unable to check for updates (SOLVED):
I also turned up logging to Level 3: Query level information in DNS Resolver > Advanced Settings.
Do you see failures in the DNS logs?
-
I think I found the issue. It was this floating firewall rule.
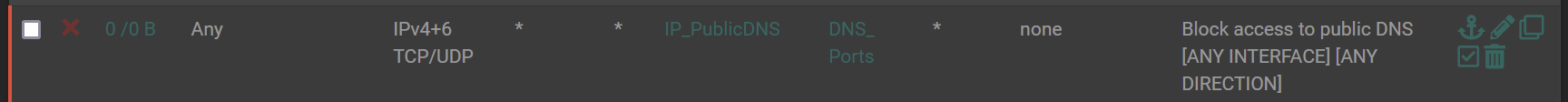
I disabled it (as shown), then tested via DNS Lookup (I also added Quad9 DNS as external DNS to test). All interfaces, including the loopback and the LAN interface are now connecting.
the IP_PublicDNS Alias (link contains list of public IPs). Unfortunately, it also appears to contain a number of private IPs, including 192.168.0.1, & loopback (127.0.0.1).
Now that I think of it, I know of a better way that doesn't use an arbitrary list.
I feel like an idiot for blindly using the list and not properly vetting before using.
Thank you. I appreciate your assistance and patients.
-
Yeah, that could easily block outbound requests. Setting direction In would prevent that.
But you probably want to use something that redirects anyway:
https://docs.netgate.com/pfsense/en/latest/recipes/dns-redirect.html -
I have that for my IoT subnet. That is the better method to transparently redirect traffic.
I think what happened was I found that list first, then learned how to do that traffic redirection, but neglected to scrap the list & associated rules.
I am perplexed as to why they put private IP addresses, including the reserved loopback on the list.
I just emailed the maintainers of the list to ask them why.
-
J jonathan.johnson referenced this topic on
-
J jonathan.johnson referenced this topic on