Traffic through another wan, 2WAN 1LAN 1VLAN
-
-
@gdsf
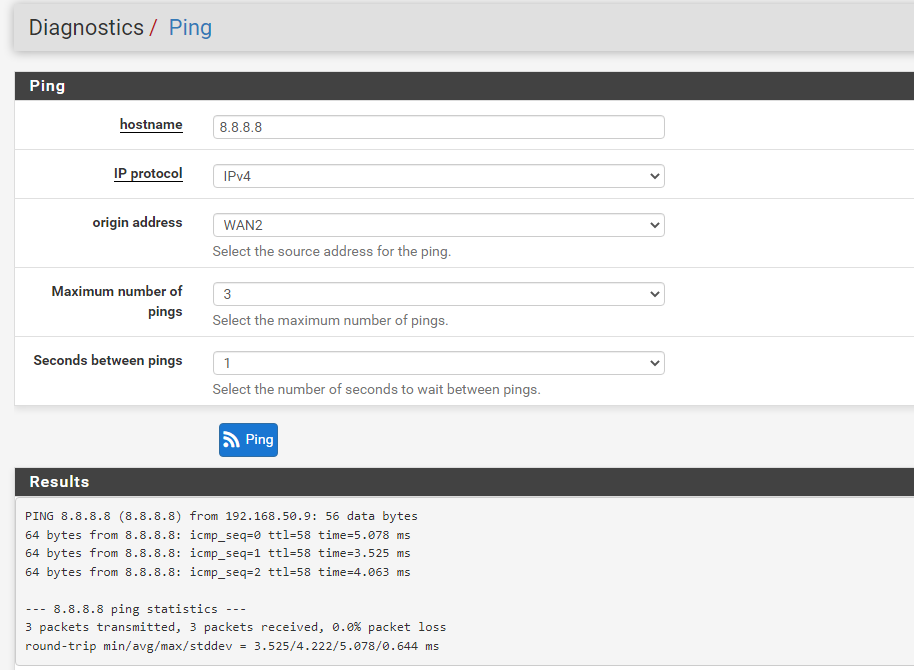
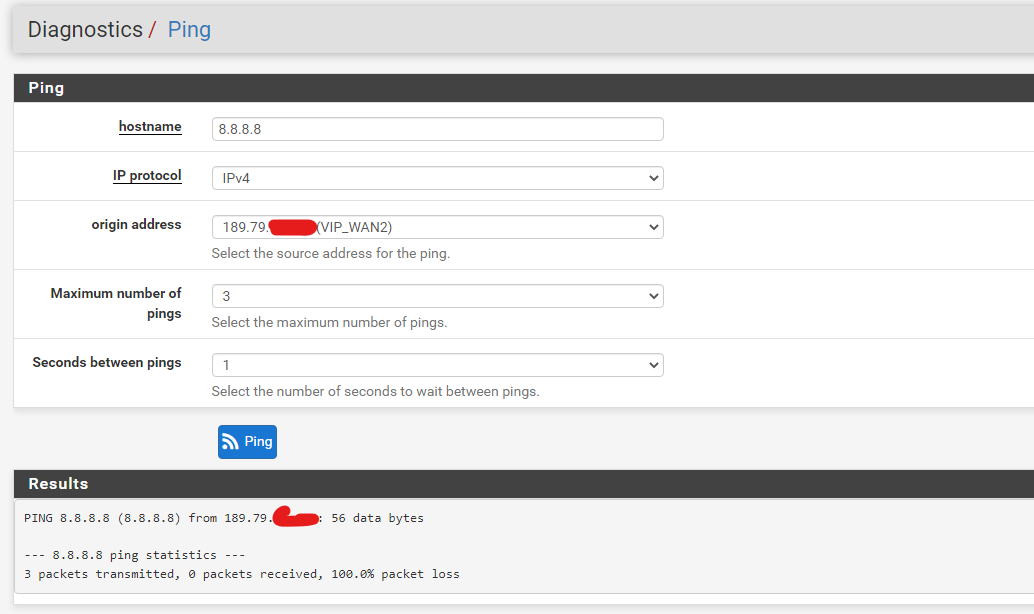
No, not this way. You have to state the VIP at source.
Your WAN IP is a private one as shown above. -
-
@gdsf
I got the idea, that the ping tool is not an appropriate way to test this. The ping requests might go out to the default gateway.You have to ping from a VLAN10 device. The policy routing rule should direct it out to WAN2 and it should get the VIP as source.
So sniff the traffic with packet capture while pinging to investigate if all these work. -
@viragomann that's the problem, if I could make VLAN10 travel over WAN2 it would already solve the problem
-
@gdsf
The policy routing rule forces all traffic, which the rule is applied to the WAN2 gateway. There is no way around this.
The screenshot ot the rule above shows, that it treated already some traffic. But maybe not all from VLAN10.If you suspect that the rule is circumvented by some packets for whatever reason, check if there are other rules with higher priority applied to VLAN10 traffic. Consider that floating rules and rules on interface group are probed before ones on the interface tab. So check if you have any.
-
@viragomann I just have an interface group configured in routing for failover, otherwise my firewall rules are any for all
-
@viragomann SQUID Proxy intervene in this matter?
-
@gdsf
Yes. See here: Troubleshooting Multi-WANI've read somewhere that there is an option to do the policy routing within squid, but I don't use it, so cannot help here.
-
@viragomann Bruh, I disabled squid and the firewall rules worked normally.
Thank you very much friend you helped me. have a great day !