QoS / Traffic Shaping / Limiters / FQ_CODEL on 22.05
-
@keylimesoda said in QoS / Traffic Shaping / Limiters / FQ_CODEL on 22.05:
I'm still seeing this issue in 22.05-REL?
That's why @luckman212 said :
@luckman212 said in QoS / Traffic Shaping / Limiters / FQ_CODEL on 22.05:
All working great on 22.05.r.20220604.1403.
Go from stock 22.05 to 22.05..r.20220604.1403 and re test ;)
-
@gertjan Are you sure?
Stock 22.05 was 22.05-RELEASE (amd64)
built on Wed Jun 22 18:56:13 UTC 2022
FreeBSD 12.3-STABLE20220604 is older.
And as far as redmine says.
https://redmine.pfsense.org/issues/13026?tab=history
It has been resolved in 22.05 -
@netblues said in QoS / Traffic Shaping / Limiters / FQ_CODEL on 22.05:
It has been resolved in 22.05
I stand corrected I guess.

-
@keylimesoda said in QoS / Traffic Shaping / Limiters / FQ_CODEL on 22.05:
@luckman212 I'm still seeing this issue in 22.05-REL?
No matter what limiter I'm putting on the WANDown it's still going full-bandwidth and bufferbloat is suffering.
Which brings us back to the original question regarding wandown
I just checked it on 22.05 and it DOES work.
Do a speedtest and see what speed are you getting and if it is consistent.
(eg. wan links from wisp's tend to fluctuate in speed)
And do keep in mind that wan down can only be controlled indirectly, by dropping tcp packets and hoping that ack-window will take care the rest.
If your incoming traffic is e.g. udp and there is no mechanism in the app that utilises udp traffic to request fewer data, there is no way to stop flooding your download. -
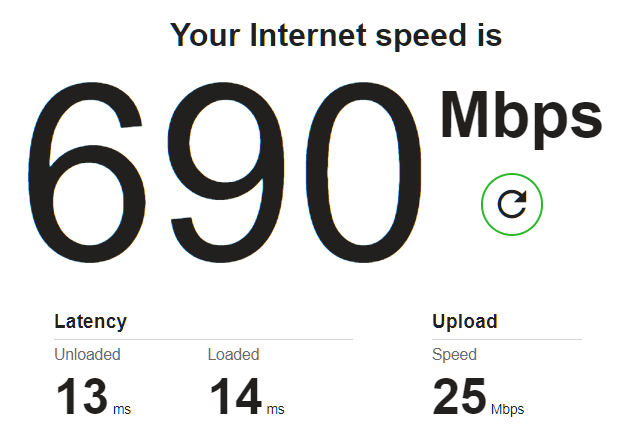
@netblues I'm getting different behavior on different speedtests which is odd. Could be the UDP issue?
On Ookla and FAST, the WAN down shows as scaling correctly. And in fact on FAST it shows almost no bufferbloat.
On Waveform test, it seems to ignore the download limiter, and shows all kinds of wonky behavior around buffer bloat on download (ranging from 20ms to 120ms). Upload is steadier.
In an informal test (watching ping times to google.com while running Ookla), I am seeing significant ping impact (from 16ms to 40-70ms) under load, which suggests that something is still off.
-
@keylimesoda said in QoS / Traffic Shaping / Limiters / FQ_CODEL on 22.05:
@netblues I'm getting different behavior on different speedtests which is odd. Could be the UDP issue?
On Ookla and FAST, the WAN down shows as scaling correctly. And in fact on FAST it shows almost no bufferbloat.
On Waveform test, it seems to ignore the download limiter, and shows all kinds of wonky behavior around buffer bloat on download (ranging from 20ms to 120ms). Upload is steadier.
In an informal test (watching ping times to google.com while running Ookla), I am seeing significant ping impact (from 16ms to 40-70ms) under load, which suggests that something is still off.

I have been seeing really weird results on the Waveform test. It seems broken. I have a 1Gbps connection and it will show over 1200Mbps and then go all over the place showing increased latency. I have my limiter set at 940Mbps. Speedtest (Ookla) seems to respect the limiters.
-
@keylimesoda Try liming to a ridiculous slow rate, something like 10Mbit down., 10Mbit up and see what happens there
If the line suffers from great speed spikes limiters don't work well.
I see this on a install that has a stable ftth line, and a 5g
on the same box.
5g leaves a lot to be desired at C, while ftth is a+ on bufferbloat tests -
I just went ahead and bought a TAC Pro sub. Order SO22-30515. Hope I can get some assistance next week.
-
@luckman212 said in QoS / Traffic Shaping / Limiters / FQ_CODEL on 22.05:
Firewall > Rules > Floating:
Action: Pass
Quick: checked
Interface: WAN1
Direction: out
Family: IPv4
Protocol: any #[Change this to TCP & UDP by ctrl + click each in drop-down menu]
Source: WAN1 address
Dest: Any
Gateway: WAN1
In/Out Pipe: WAN1UpQ / WAN1DownQNow traceroute and icmp will operate correctly without adding extra rules.
-
@mindwolf said in QoS / Traffic Shaping / Limiters / FQ_CODEL on 22.05:
Now traceroute and icmp will operate correctly without adding extra rules.
You may still find value in the general approach. It's a personal preference, but I prefer to exclude ping request/reply from the limiters because I don't want them delayed or dropped under load. I have a separate floating rule for ICMP request/reply just before the limiter assignment rule(s) to achieve this.
-
There are many ways to approach this but my suggestion does take icmp and other protocols out of the equation. The firewall floating rule ONLY includes tcp and udp. I just installed pfsense the other night and curiously ran into the same issues running ping and traceroute with my windows laptop having the “repeating” issue along with dropped pings. This change resolved my issue and still controls bloat. Cake has this feature aimed towards a 11:1 or higher rate.
Finding a way to drop duplicate acks is another avenue worth exploring for extending the ingress bandwidth at the expense of more cpu usage. I started with openwrt and the sqm folks learning much over the years.
-
I inferno480 referenced this topic on