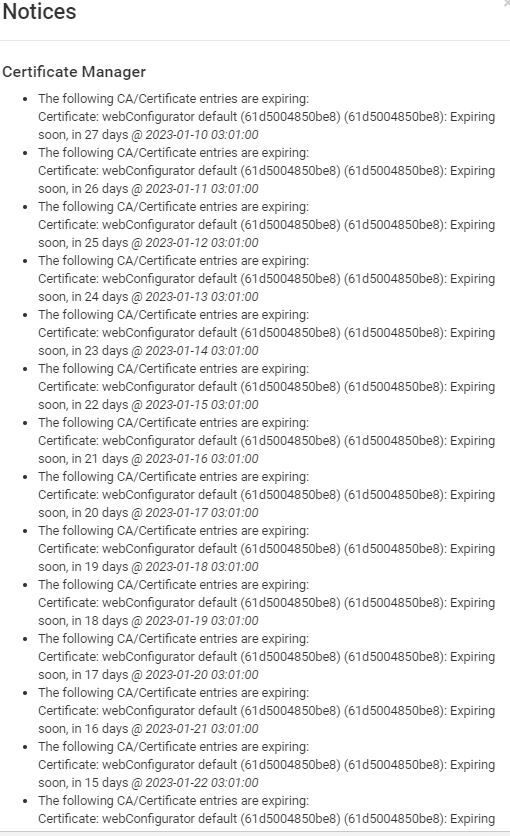
Certification issue?
-
@travelmore I think you need to understand some basic things about certificates in general.
If you go to:
and look at:
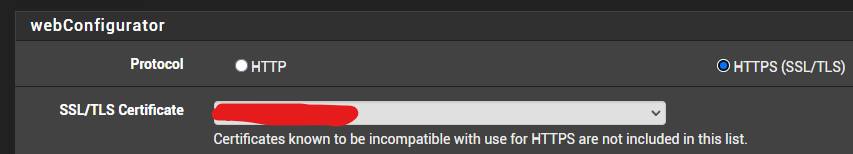
(I erased the name of my cert for security reasons)you will probably see "webConfiguratorDefault-xxxxxxxxxxx..." selected.
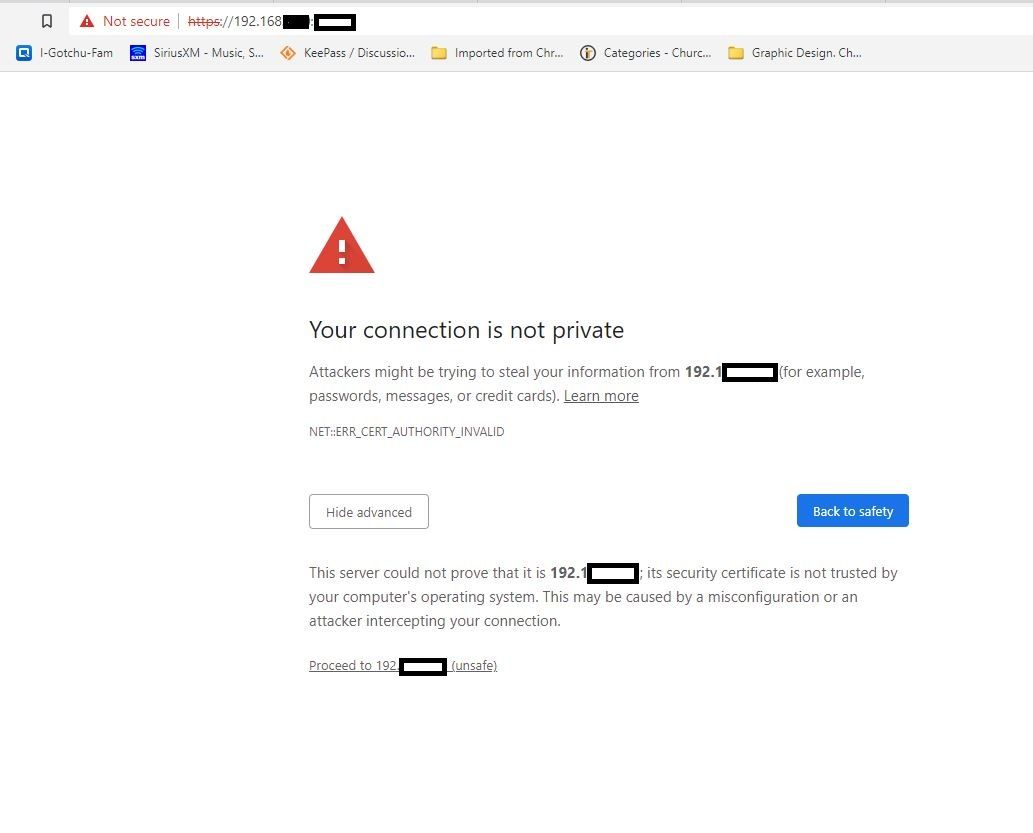
That certificate is created by pfsense during install. That means that nobody knows the creator of the certificate. Meaning, while it may be a valid cert, the Certificate Authority that signs it (ie, your PfSense default_CA) is not a Certification Authority that Firefox or Chrome or Safari or ... hmmm ... Edge (yes, some people use it) knows it can trust out-of-the-box.
A second problem is that SSL certificates have to mention the host.domain.tld of the machine they claim to be (not the IP address) to be trusted by a browser, even if the certificate is signed by a trusted authority (although, no certification authority would ever sign a cert without verifying the domain name).
You can resolve all that by:
- Getting a free domain name (Freenom? That one you should search for yourself, you need to have control over the DNS records or to be able to direct the domain to PfSense)
- Following this guide, in order to setup the ACME package on PfSense and setup your trusted cert.
- Setting up DNS overrides on your LAN that connect PfSense (192.168.x.x) to the name of you cert, ie your.domain.com. That would let you visit pfsense using that name instead of the local IP (192.168.x.x).
- Selecting the trusted ACME cert in the Admin Access menu of PfSense.
If you have other servers that you are tired of remembering the IPs of, and/or are tired of clicking "I understand the risks", you should look into the HAProxy package. Here is a handy guide to play around with.
Also, the errors you are getting can be because of two things:
- Either your PfSense is set up for a really long time and your CA or cert expired (meaning, you have to create a new one and select it in the menu I showed you above)
- Or (and this happens) the clock of your PfSense machine is way off (because of a bad CMOS battery, lack of NTP config and/or connectivity, hypervisor not cooperating in a VM...) and while the expiration date of your cert seemed to be two years away, after clock corruption or correction, the machine sees the expiration date getting close.
Either way, check datetime and renew both you CA and Cert.
-
@nightlyshark said in Certification issue?:
You can resolve all that by:
You forgot a method
Setup your own CA in pfsense and have your browser trust it.. Now you can use this CA to sign certs for all your local stuff that might want to use certs your browser trusts.
One advantage of this is you can use any domain name you want, home.arpa for example the new standard domain to use for local stuff. You can add rfc1918 IPs as SAN, so those are trusted as well, etc. You do not have to mess with owning a domain, or using some free domain. You don't have to worry about acme renewing a cert every 90 days, you don't need to setup any nat reflection or host overrides or haproxy to access your local stuff because you can just access via your whatever.home.arpa fqdn for example that pfsense points to your local IP of your thing.
here is an old quick walk through I did back in 2019
-
@johnpoz (Tried to like twice
 ) Didn't forget it, just... It is tiresome! (Excuse the exclamation). Especially with Windows clients. And Chrome-Firefox using QUICK-DoT... Everyone their own trust store... I also think it would lead to more questions down the proverbial road...
) Didn't forget it, just... It is tiresome! (Excuse the exclamation). Especially with Windows clients. And Chrome-Firefox using QUICK-DoT... Everyone their own trust store... I also think it would lead to more questions down the proverbial road... -
@johnpoz Also, the ACME package is great because it renews all certs by itself! I almost had a stroke when I found out about it (in the middle of trying to manually configure CloudFlare DNS and letsencrypt!).
-
@nightlyshark yeah the acme package is great I use it for some domains I host locally, and use ssl offload haproxy with them.
Your mention of browser using doh is sure valid point I guess.. None of my clients use that nor will they ever.. I run my own local dns thank you very much.. ;)
There are many ways to skin a cat, I prefer running my own ca and the ability to use my own domain names and rfc1918 as well for a SAN..
-
@johnpoz If only I could Group Policy my whole house... But no, because if my relatives call me for assistance now ("why has netflix stopped working? Are you playing around again?" - Me sleeping like a rock, after work) imagine if they had to configure anything or their games on android stopped working (because no ads)...
-
@nightlyshark said in Certification issue?:
imagine if they had to configure anything or their games on android stopped working
Not understanding what any of that has to do with using your own CA for creating certs for stuff you will access.. Nowhere did I say you should use that for stuff that public might use ;)
Nobody access pfsense web gui but me, nobody access the web gui of my unifi controller but me.. Nobody ever access the web interfaces of my switches or printer, etc.
And even if they did - they would get the same stupid error about cert not trusted like they would with self signed, and they could still access it.
A local CA and your browser trusting this CA is not for sites that will be consumed by public.. But it is a valid solution for for stuff that would be access by you, or limited users access that can trust the ca.
-
@johnpoz I meant to say, because I also have other services running on LAN:
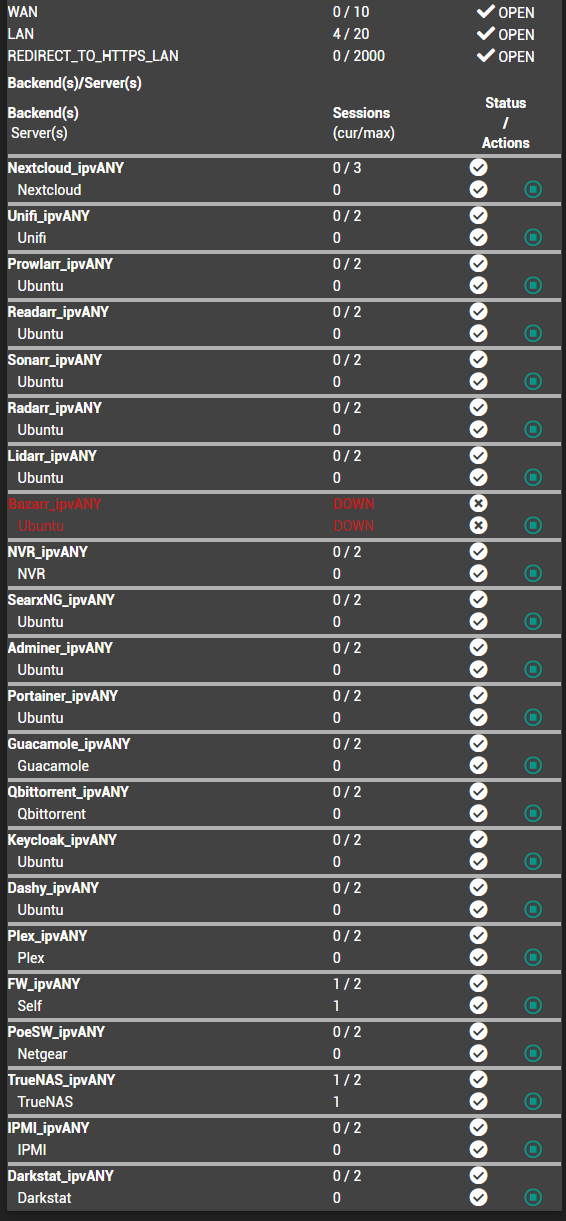
(can't change photo size)
I found it easier to just ACME and HAProxy it, seeing as everything not in Docker here has its own IP, everything Docker has a custom port (not HTTPS) and making a cert for everything...Even if Windows trusts the CA, what if I want to connect from a laptop? Or from IPsec? I would have to do two whole clicks more per service visited. That is unacceptable!
 (just joking)
(just joking)Anyway, just as you said, it comes down to personal preference and routine. I am just an enthusiast and not used to professional setups. Also, at first, before ACMEing it, everyone here distrusted the servers because of the warnings and I got tired of it.
Not to mention the DNS nightmare (even though this has only to do with HAProxy and not certs, it is still an extra point).
-
@johnpoz Thank you for the link w/the setup I will take a look at it. I also appreciate the knowledge and information shared. @NightlyShark Thank you for the information as well, it is appreciated. I skimmed the link but will go back and do a more thorough reading of it. It's really informative and explains it well.
To both of you, I read through everything you guys shared before replying and after reading, had this question. **I have not made any changes yet because I had this question I wanted to ask before I made any changes..
DNS was mentioned in both of your responses I believe, that being said, I do have a pihole that is my DNS server, so does that change anything about needing the certificate?
Once I create my own like you mentioned in your step by step link, will that fix the issue or will i eventually come up against the 'not safe' message?
Does getting that 'not safe' message really matter when Im accessing my pfsense box?
Like is it a security risk or something?Yes I know, I need to do more research, Im not well-versed in cyber security so I always want to make sure I do the best I can and not accidentally, or unintentionally leave myself open for intruders/attacks when it can be prevented w/simple stuff.
I know I need to add pfblocker instead of pihole and I will when I have time to do it (its more do it on a day when i know if errors occur i wont be screwed come Monday, so do it on a fri night or sat. type thing to give myself time to fix any errors that might come up).
-
@travelmore said in Certification issue?:
Like is it a security risk or something?
no a self signed cert uses the same encryption as a signed one - the only reason to use something your browser trusts is you don't have the hassle of bitching to you about the cert not being trusted, etc. ;)
And if you installed a cert you signed and you trust, you know its your cert - if that for some reason changes you would know something is up..
As to dns - where you get that from has zero to do if you trust the cert, and if the you accessed the cert via a fqdn that is in the cert, or for that matter a IP address directly that is in the san..
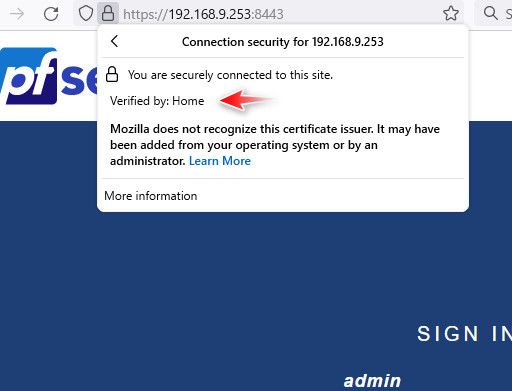
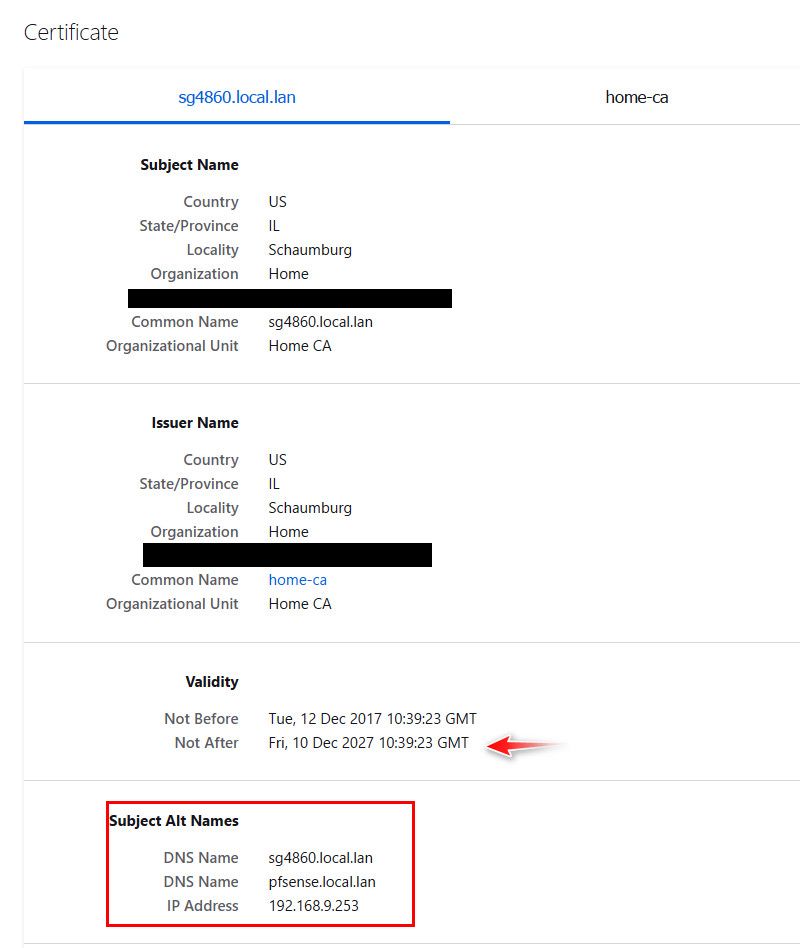
You can't really do this any more - unless maybe you set the clock back on your CA.. I keep meaning to test that.. But browsers no longer trust certs if they were created after a specific date for more than I believe like 398 days or something. But that didn't use to be the case.. Notice my cert is valid until 2027. 10 years from when I first created it.
-
@johnpoz Thanks! The information and screenshots are helpful. I didn't think DNS had zero to do w/the trust of the cert or not but wanted to ask because I saw DNS mentioned throughout and wanted to try to give information about my dns if ended up being of importance.
I am creating a new cert like you suggested...in this screenshot below from your steps...
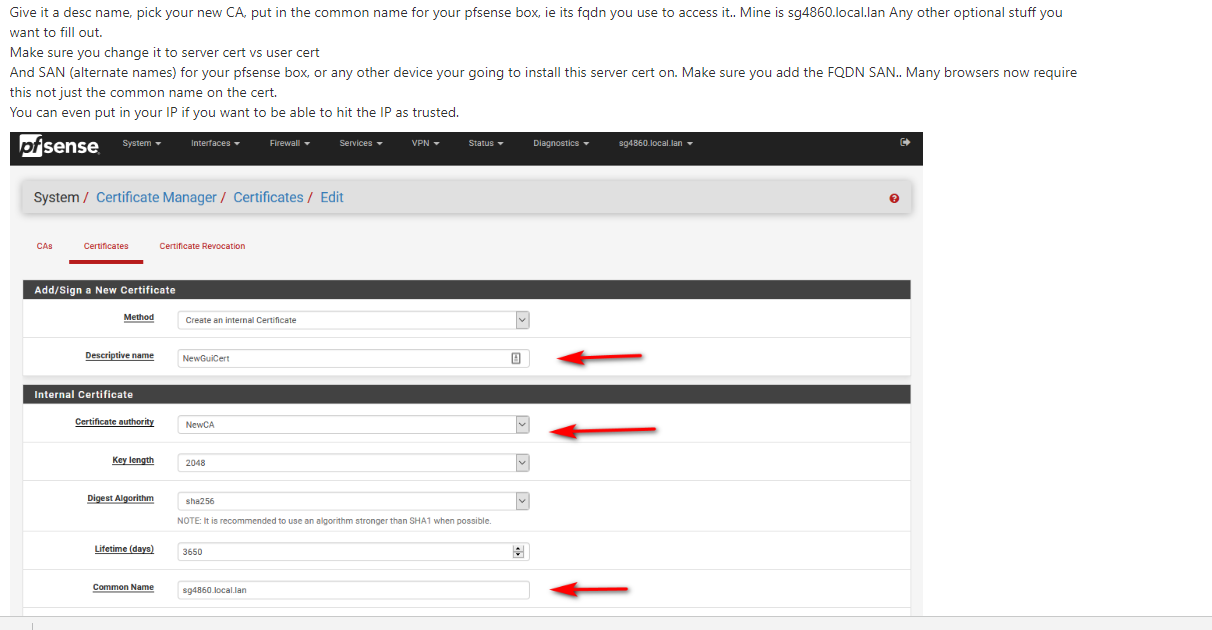
.....where you say put in the common name of your pfsense box, its fqdn you use to access it, that is this:
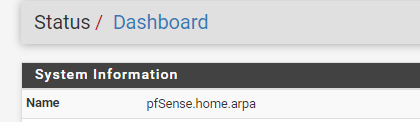 correct or is that not correct?
correct or is that not correct?
I access it just using the IP address, that is why I ask because im not sure what to put. -
@travelmore yeah that would be the new default fqdn.
If you access via IP, just make sure you add IP you use as a SAN. But you can start accessing it via the fqdn if you want as well.
I had created mine way before home.arpa was a thing.. And I use local.lan as my domain, kind of in the process of changing over.. I access my nas with home.arpa
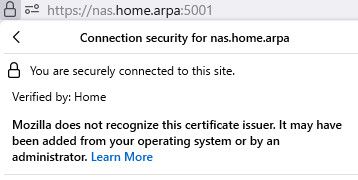
See my browser trusts it, and using different domain... Once you trust the ca, you can create certs it trust for any fqdn, any IP, etc.