MacOS Ventura and IPSec Mobile Clients
-
@rcoleman-netgate I have no issues with Monterey or iOS either. I do with Ventura though. No error on the Mac side, it just switches back to disconnected right after to try to connect.
-
Use a profile, don't rely on the defaults. If you have plus, use the Apple IPsec Export function to make a profile (VPN > IPsec Export: Apple Profile). If you are on CE, then download the utility from Apple to create a profile manually.
That's going to be the most reliable way to make sure it uses the appropriate configuration.
Also it's helpful to review the profile reference to make sure you're using what Apple considers a valid combination of options:
https://developer.apple.com/business/documentation/Configuration-Profile-Reference.pdf
Using a profile, I have no problem getting macOS 13.1 to connect and pass traffic.
-
@jimp I tried ages back with the profiles and it would only seem to export my self signed CA and not the certificate used in phase 1, maybe I'm just doing it wrong.
-
@nogbadthebad said in MacOS Ventura and IPSec Mobile Clients:
@jimp I tried ages back with the profiles and it would only seem to export my self signed CA and not the certificate used in phase 1, maybe I'm just doing it wrong
The CA is what gets imported to the client (so it can validate the server cert), the server certificate never gets copied to the client.
Client certificates would get copied to the client as well if it's using EAP-TLS.
-
@jimp Ah I'm using EAP-RADIUS.
-
@nogbadthebad said in MacOS Ventura and IPSec Mobile Clients:
@jimp Ah I'm using EAP-RADIUS.
Then all you'd need is the CA that signed the server cert so the client can validate it as needed.
-
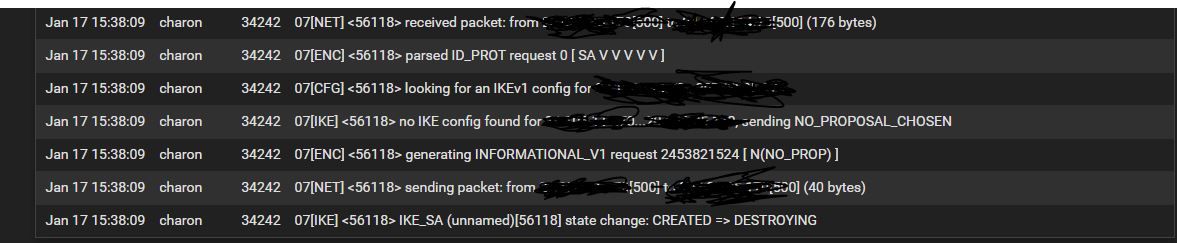
I've tried everything to no avail. This is the first time I'm seeing this but when i try to import a vpn profile using Apple Configurator, I get an error "VPN Profile installation failed". Giving up for the day. Been a long one. Will keep digging tomorrow. Thanks everyone.
-
Anyone ever experience a similar issue? I am still stumped.
-
Hard to say what might have happened from that error message. Apple can sometimes be a bit generic/unhelpful in that department.
I can say, though, that using our profile export tool on Plus I've generated and imported profiles for EAP-MSCHAPv2, EAP-RADIUS, and EAP-TLS using a variety of different P1/P2 configuration combinations and they all work perfectly with the latest version of the package (1.1_1).
-
Turns out my issue was within phase 2 on the tunnel. I mistakenly unchecked "SHA384". Smh...... Just wanted to share.