Basic firewall rules for interfaces
-
I have another super simple, generic, noob question. I have LAN and "NET2" as interfaces. I want LAN to have access to every interface indiscriminately, and NET2 to have WAN access, but no LAN access.
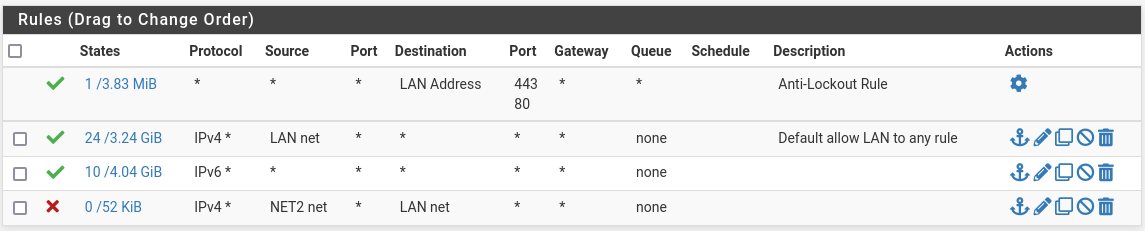
LAN:
NET2:
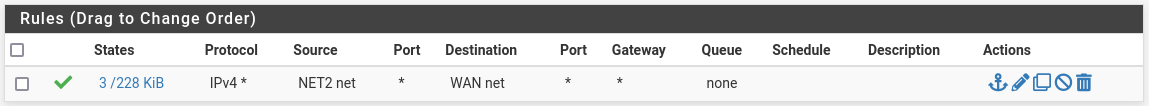
But obviously (to you) NET2 has no WAN or LAN access and idk why. What obvious netsec mistake am I making
-
LAN rule #4 is not needed because Net2 traffic will not enter the LAN interface.
Net2 rule #1 is allowing access the WAN subnet, not the internet. Notice on the LAN rules there is any:any rule. On Net2 you want block any:LAN and then allow any:any.
LAN traffic will be allowed to Net2, Net2 will be allowed to respond. A state will be created to allow the traffic flow.
As I understand the question that will get you going.
-
@bumzag What Andy said, but just noting that if you start blocking things on NET2, you probably want to allow from NET2 to the NET2 IP on pfSense port 53 for DNS (TCP+UDP). That is not allowed in your screenshot either, but would be allowed by allowing NET2 net:any. Also you may or may not want to block NET2 net to your pfSense ("this Firewall" so all IPs) ports 443/80/22.
-
Thanks for the responses. I added the block rule on NET2 and per @SteveITS added rule #3:
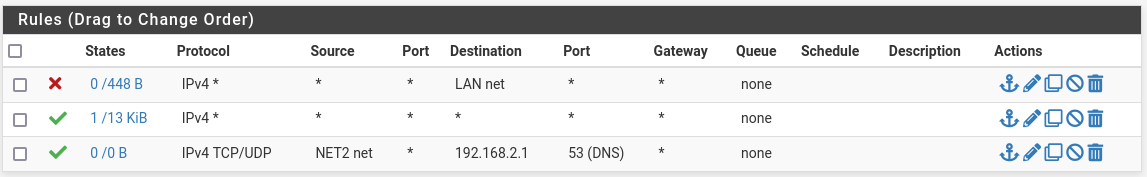
But with that block rule #1, I don't have WAN acces (or LAN which is good). I can ping 192.168.2.1 no problem but can't ping 8.8.8.8 or google.com
-
@bumzag In the order shown, the third rule will never trigger because the second rule has already allowed the traffic. (they process in order, with an implicit deny all at the end)
On NET2, are devices set to use the NET2 interface IP as their DNS?
-
@steveits said in Basic firewall rules for interfaces:
@bumzag In the order shown, the third rule will never trigger because the second rule has already allowed the traffic. (they process in order, with an implicit deny all at the end)
On NET2, are devices set to use the NET2 interface IP as their DNS?
On a NET2 device with debian 11, I changed /etc/resolv.conf to 192.168.2.1 and rebooted, still no WAN access.
-
@bumzag Is the gateway 192.168.2.1 also? I misread your post that you cannot ping 8.8.8.8 so it's not (only) a DNS problem. Try a traceroute there to see how far you get.
You have traffic matching the any:any rule ("1/13 KiB").
-
@steveits yes sorry I edited it without realizing you commented. This is my
/etc/network/interfacesfile on a NET2 deviceiface ens18 inet static address 192.168.2.2 netmask 255.255.255.0 gateway 192.168.2.1 dns-nameservers 192.168.2.1traceroute 8.8.8.8gets me1 192.168.2.2 (192.168.2.2) 3062.489ms !H 3062.423 ms !H 3062.401 ms !H -
@bumzag https://networkengineering.stackexchange.com/questions/16454/difference-between-unresponsive-and-unreachable-h-hosts-in-traceroute-out
So not a DNS issue. Routing table on the PC?
-
sorry got distracted. if I add a rule to allow NET2 to LAN, devices on NET2 have no problem reaching WAN. I'm guessing there's a gateway issue with the NET2 interface?
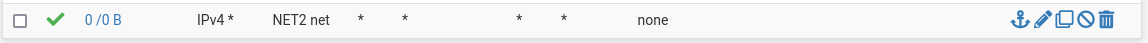
-
@bumzag I believe that rule allows Net2 to any…I think you want more like
Block net2 net to lan net
Allow net2 net to any -
im sorry but can you eli5? I don't understand, why would I add a block all rule to the LAN interface from NET2 but then add an allow all rule on the LAN interface from NET2? thanks for helping btw
-
@bumzag said in Basic firewall rules for interfaces:
I want LAN to have access to every interface indiscriminately, and NET2 to have WAN access, but no LAN access.
The block comes before the allow so LAN would be blocked