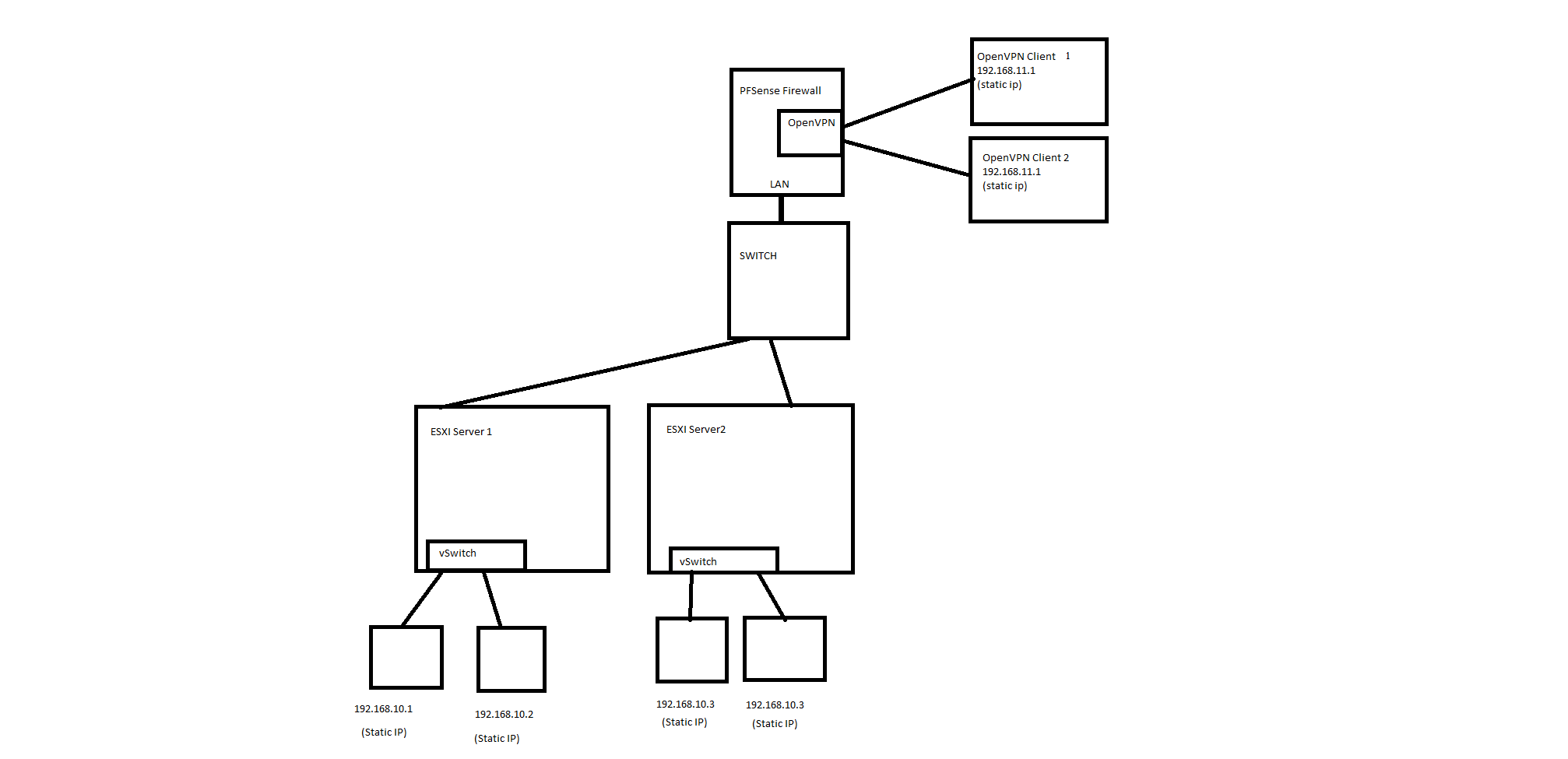
How to isolate LAN nodes
-
@cubits Using a managed switch and employing Private VLAN on the ports you want isolated.
https://kb.vmware.com/s/article/1010691
-
@lnguyen is Cisco SG-220 26 port switch a managed one?
https://www.cisco.com/c/en/us/support/switches/small-business-220-series-smart-plus-switches/series.html -
@cubits Read the KB I added to my post
-
@lnguyen ok, thanks much. I need a coffee to understand it. I will get back if I have anymore queries.
-
@cubits said in How to isolate LAN nodes:
is Cisco SG-220 26 port switch a managed one?
Yes. You can separate those segments with VLANs using that switch.
-
@lnguyen I read the KB article and looks like it is for installations with vCenter server. But I dont have vCenter server and just have ESXi servers. Does that mean, what I am trying to achieve is not possible with that?
-
You can still configured VLANs on the vswitches and pass those to the real switch. Then pass them all to pfSense to filter between them. Each VM could then be in a different subnet and you can filter to/from them as required.
-
@lnguyen @stephenw10
I tried everything I could, but could not get it working. I created a port group with VLAN id 10 in ESXi: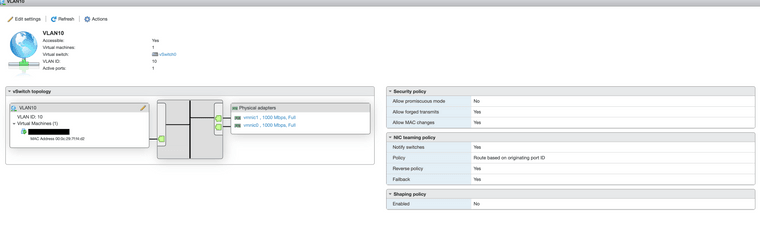
Then I attached a VM's NIC to this VLAN:
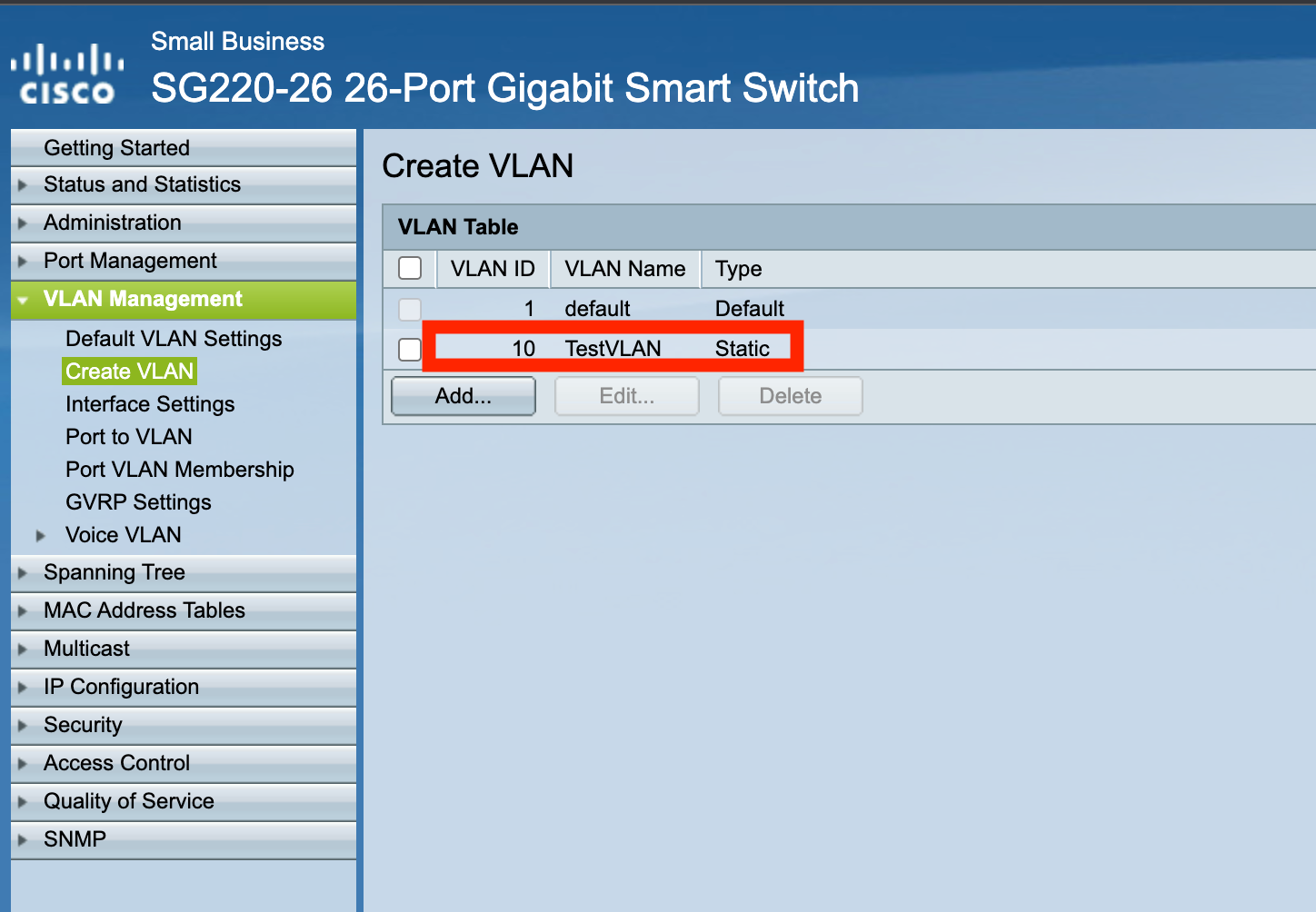
In my CISCO SG-220 switch, I added VLAN as:
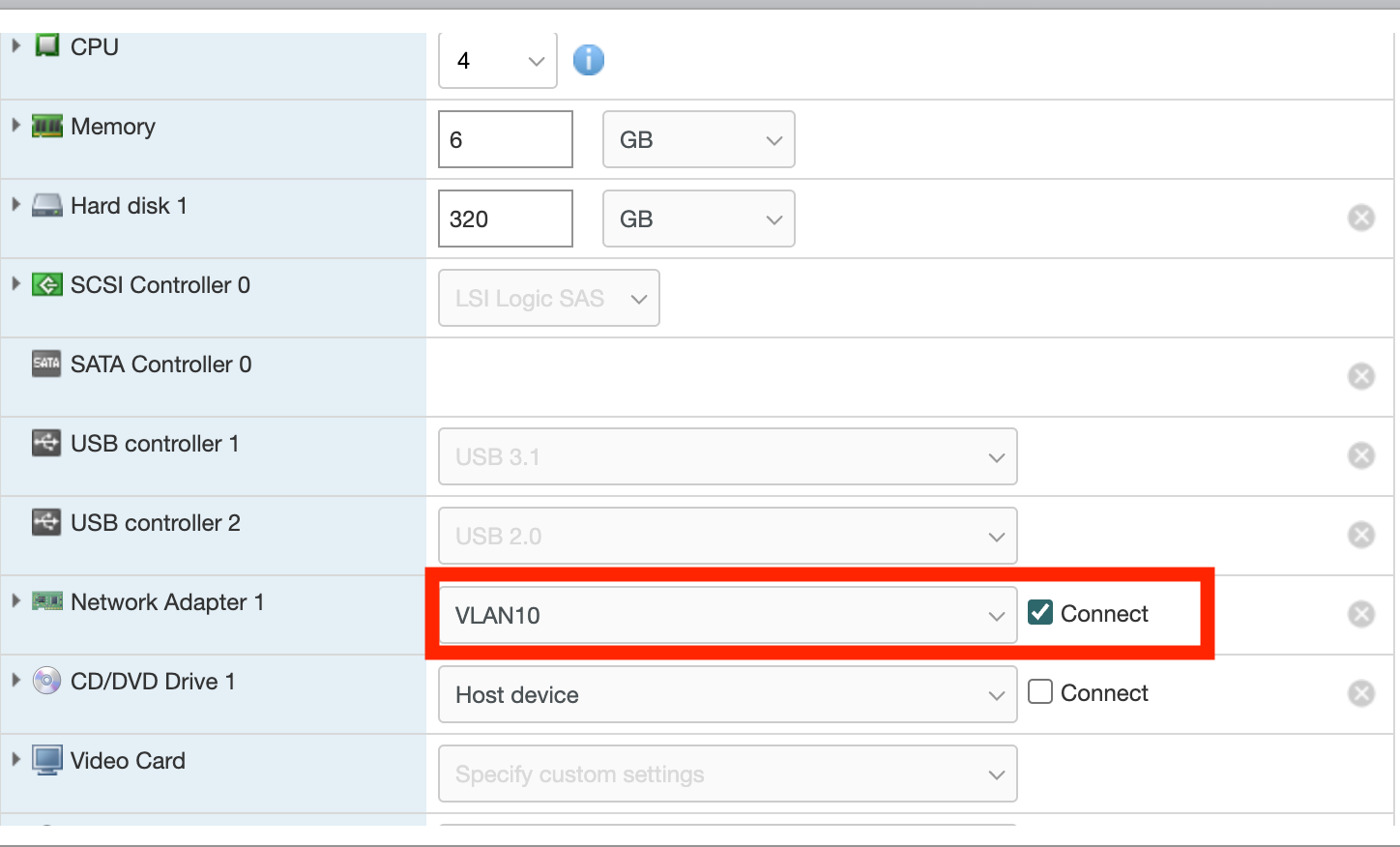
Ensured that the interfaces are trunk:
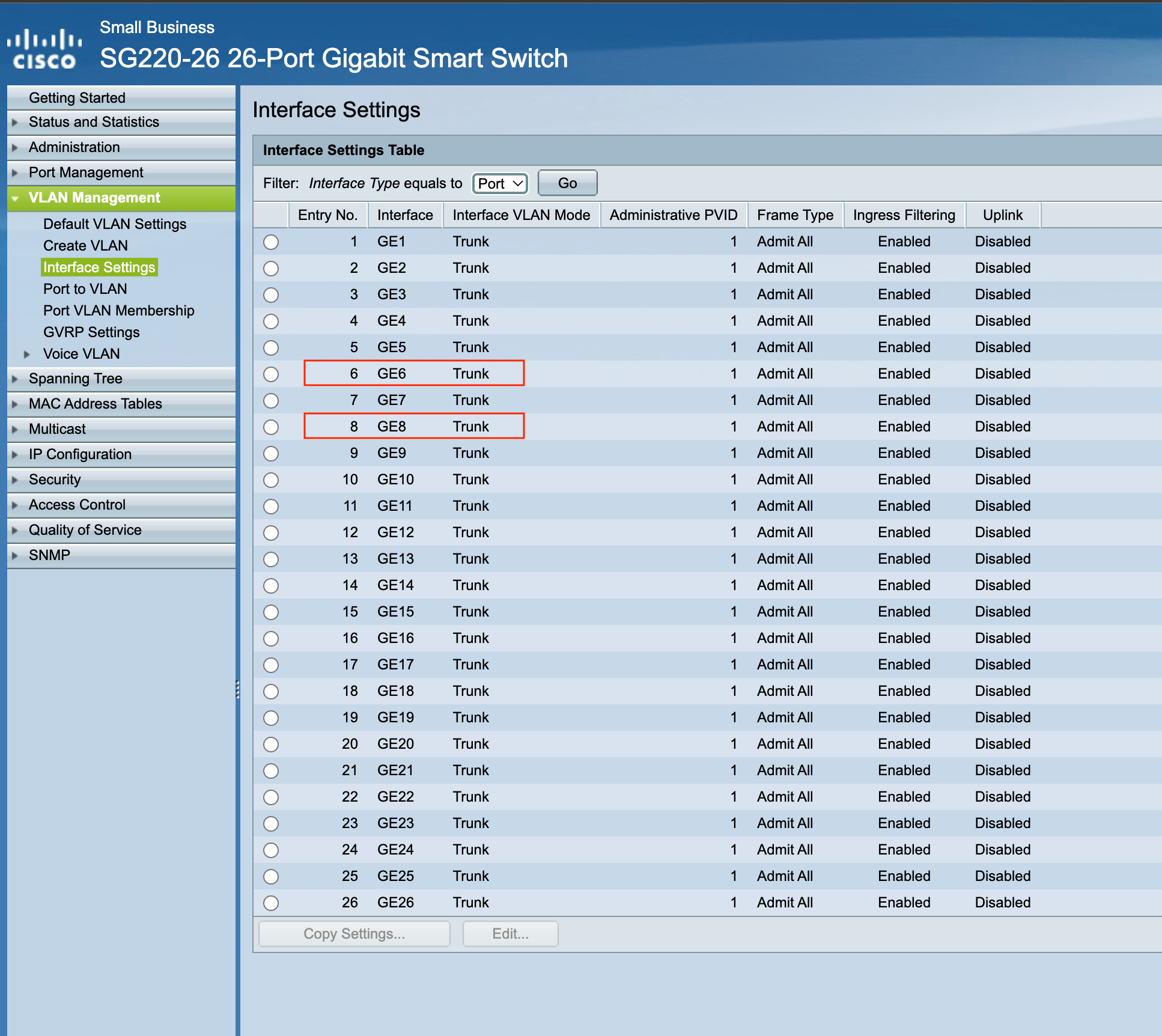
And then, I enabled VLAN tagging on the respective ports:
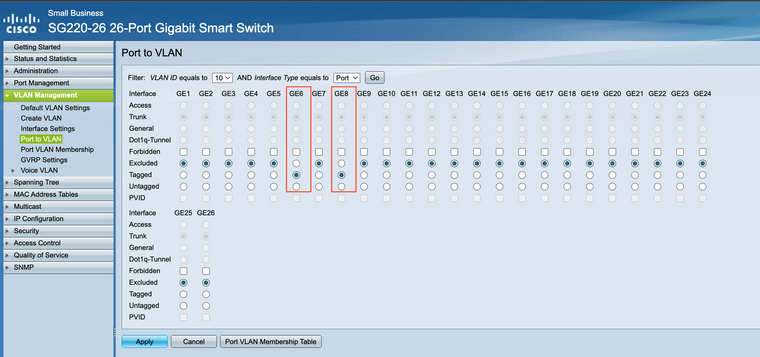
And finally, I have the pfsense with the VLAN as:
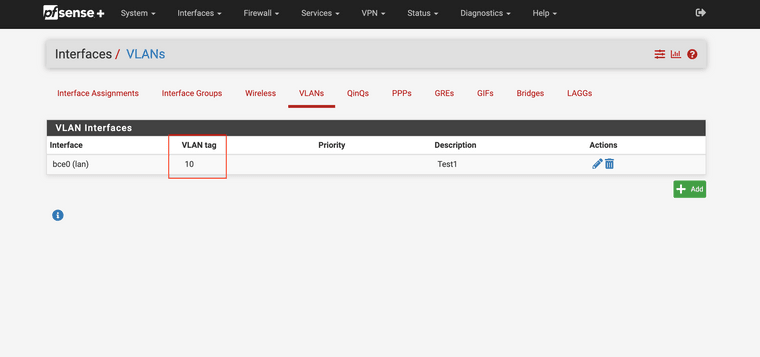
with an interface as:
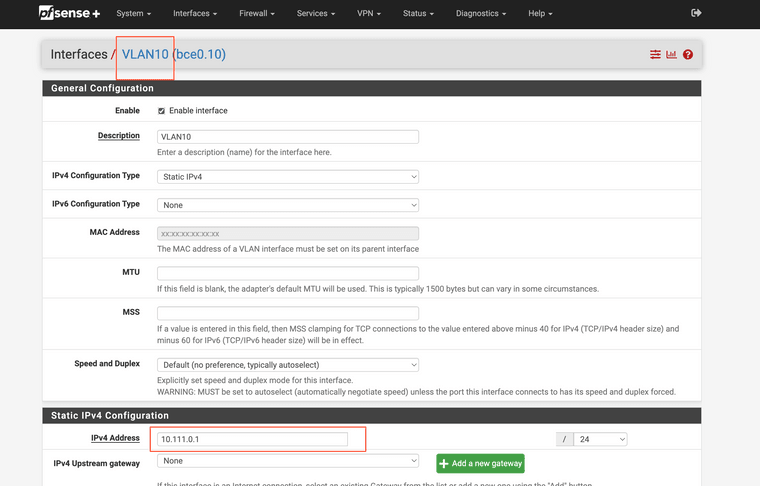
with DHCP server enabled as:
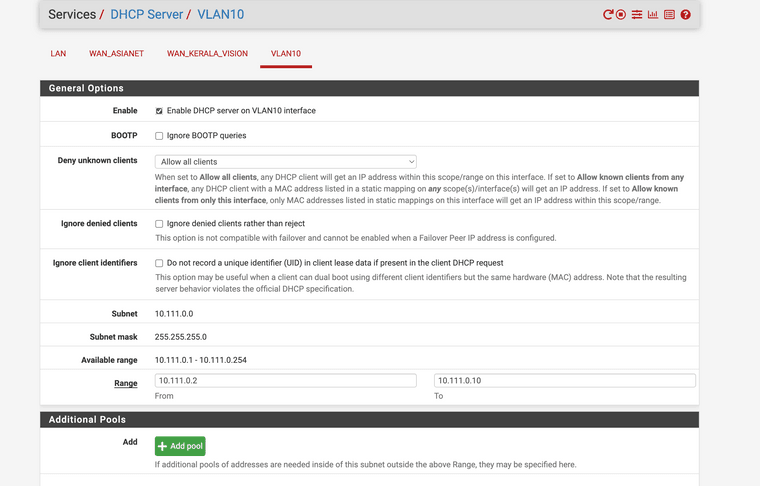
But, still, I do not get an IP address dynamically inside the VM.
What is the best way to troubleshoot this?
-
@cubits Where is your VLAN10 tag on the Cisco switchport for the uplink to the pfSense firewall?
-
Yes, which port is which there?
-
@lnguyen @stephenw10 that did the trick, thanks much for helping me out, it was GE25 on which pfsense upstream cable was in.