Warning about internal IP Range
-
@johnpoz said in Warning about internal IP Range:
127 is localhost ;) if that is what you used 127.x.x.x
That's what I thought I was going to use. My PFSense journey has been fun, I had no clue about RFC 1918 networks. Thought I could use any address I wanted.
My second choice ended with my Roku TV telling me it couldn't connect with the IP assigned. That's when I learned about RFC 1918. Teaching
myself is rewarding bit can be time consuming.In racing they say crashing is learning. I've learned a couple things......
-
@daduls said in Warning about internal IP Range:
Thought I could use any address I wanted.
Well technically that is almost true, 127/8 is all local host addresses though - can't talk to anything but yourself with 127.x.x.x, you could just randomly pick some public IP space and use it internally - just hope you don't actually ever want to go somewhere that is on that space..
Its bad practice, but technically there is nothing saying you couldn't use some of space that MS owns for example - but have a hard time actually talking to their services that might really be on some of that space.
There is plenty of rfc1918 space to choose from ;)
-
I had an interesting variant of this, related to $WORK.
openvpn client to server at work, server at work pushed down all it's data, routes.
Well slap me silly, a bunch of work pushed stuff overlapped my local home network, pretty much mucking up my default routes.
Solution? Change my local network from 192.168.x.0/24 to something like 192.168.251.0/24.Pick oddballs; 137, 237, 159, etc. Everyone picks 1-10 or 254.
-
@johnpoz said in Warning about internal IP Range:
There is plenty of rfc1918 space to choose from ;)
Today I was doing some work at my ISP's head end and I noticed a lot of addresses in 172.16.24.x. While I have seen it lately, years ago traceroute showed 10.x.y.z on their internal network.
-
I always pick even subnets, that way I can change from /24 to /23 and not affect anything.
For the VPNs I always use 172.16 addresses. -
@andyrh said in Warning about internal IP Range:
For the VPNs I always use 172.16 addresses.
I have a /56 IPv6 prefix, which gives me 256 /64s. I match up the 3rd octet, in 172.16.x.y, with the prefix ID
-
@daduls
Very time consuming!! Took all day to convert, but I moved to a 172.16.0.0 address setup. -
@kevin-4 But very rewarding when things work out. Hope your new setup stands the test of time.
-
@johnpoz
Well, everything was working fine overnight with the 172.16.0.0 and then it broke. Currently, I cannot seem to get the internet to pass to the network after the address change. The pfSense diagnostics can ping the internet and all the interfaces show working, but no internet.After getting frustrated troubleshooting, I reloaded a config file to reset everything and I was able to connect to the internet again. So I changed a single interface to one of the new address again (172.16.10.1/24) and updated the DHCP pool. I then reconnected to the pfSense via a cable using the new address and the computer won't connect to the internet. When I login to the pfSense using an interface with an old IP setup I can connect to the internet on the computer.
I have no idea what setting I'm doing wrong...
-
If you are using 172.16.0.0 and the client uses 172.16.10.1/24, these two will never connect.
The client needs too a netmask which allows to reach the 172.16.0.0 network, use a /16 (255.255.0.0) and reduce step by step if needed.Regards
-
@fsc830
Appreciate the input, but that address is just an example. I've changed all the IP's on my switches and routers to the new address so they will connect. Everything was up and running, so I'm not sure if there was a slow setting change or what?I did try a /16 instead of the /24, but it was the same deal.
-
@kevin-4 Have you updated all your firewall rules, aliases and NAT?
-
@daduls
As far as firewall rules, I added a new 'allow all' rule to the top of the interface rule set to test it, but I haven't done anything to the aliases, but I'll try disabling them Do the rules need to be recreated when an interface changes IP?When it comes to working with NAT, I wouldn't know what to check, I'm clueless...
-
@kevin-4
I went ahead and deleted the firewall rules and aliases and now only have an allow all for testing. I also looked at the NAT and it shows an automatic entry for the new IP address. -
@kevin-4
First, I'm new to this, what got my vlans seeing traffic instead of the allow all rule was the "443,80,and 53" rules below. Notice I also kept the allow all rule below these though.....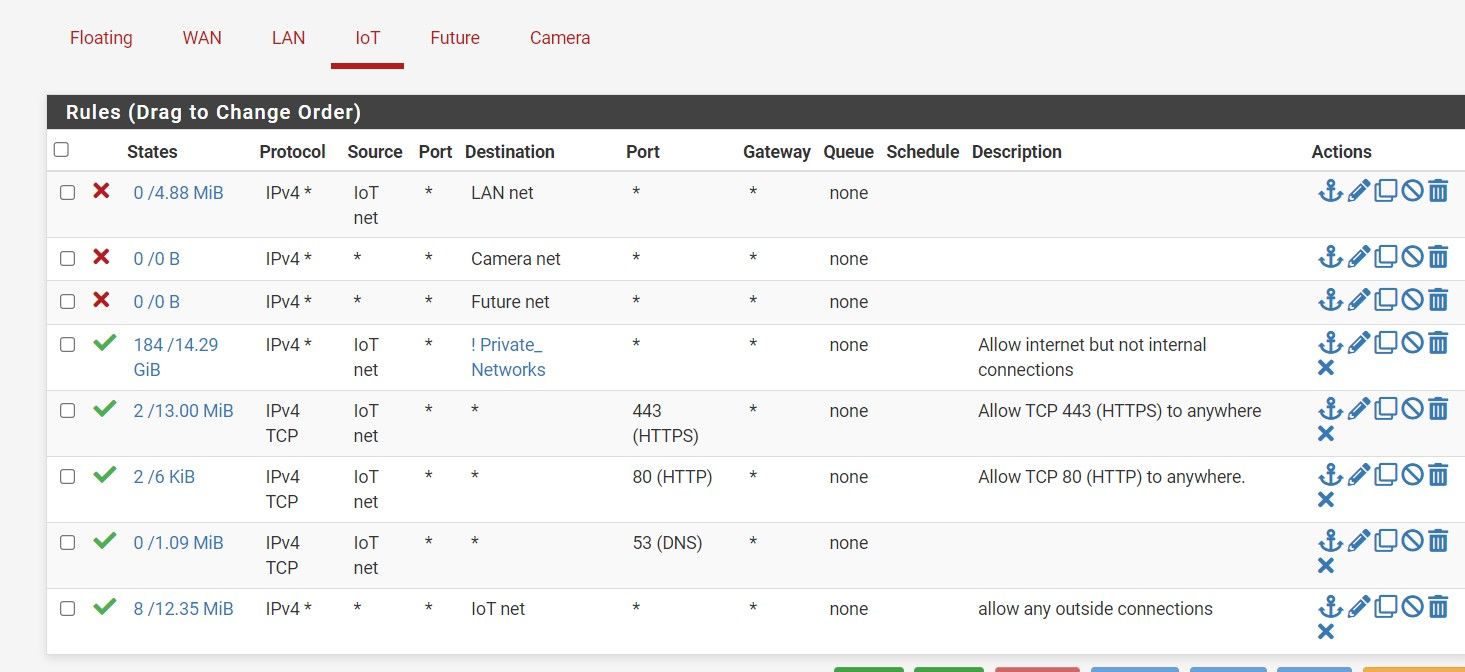
-
@daduls
Well, I couldn’t get it to work correctly so I’ve gone ahead and reinstalled the old configuration just to get back up and running. I’m going to do some research to see if I can figure out what’s going on and maybe try again when I have more time. Thanks to everyone for their input. -
@kevin-4
Are you changing your LAN or adding a vlan? Don't know your setup but since you have the old config backed up you could go through "System-General Setup" if its for your LAN? -
@daduls
I was changing my LAN and VLANS to the 172.16.x.x. As I am studying the proper use of IP address and subnet schemes, I realize I should have used the /16 with a subnet of 255.255.0.0 as FS380 suggested above, instead of the 255.255.255.0 (/24).I'll give it another try next week when I get a chance.
-
Using a /24 for a single interface/subnet is typical and shouldn't cause a problem.
Firewall and NAT rules would usually not need changing because they use aliases such as 'LANnet' and that would be updated. However if you have rules using specific IPs those obviously would.
Steve
-
@kevin-4 said in Warning about internal IP Range:
I realize I should have used the /16
No that is not a good idea.. /24 is the standard typical size that should be used on most networks, especially a home... It gives you plenty of IPs to work with 254.. Is easy to tell network X from network Y via the 3rd octet, and doesn't waste while large the limited rfc1918 space..
/16 - you have plans of ever coming anywhere close to 65K devices on the network?
Using such a large space also increase possible overlap.. talking to remote network..
LAN and VLANS to the 172.16.x.x
That wouldn't work with a /16 that would be the same network.. if using /24 for example 172.16.100, and 172.16.101/24 would be different networks.