Warning about internal IP Range
-
@kevin-4
I went ahead and deleted the firewall rules and aliases and now only have an allow all for testing. I also looked at the NAT and it shows an automatic entry for the new IP address. -
@kevin-4
First, I'm new to this, what got my vlans seeing traffic instead of the allow all rule was the "443,80,and 53" rules below. Notice I also kept the allow all rule below these though.....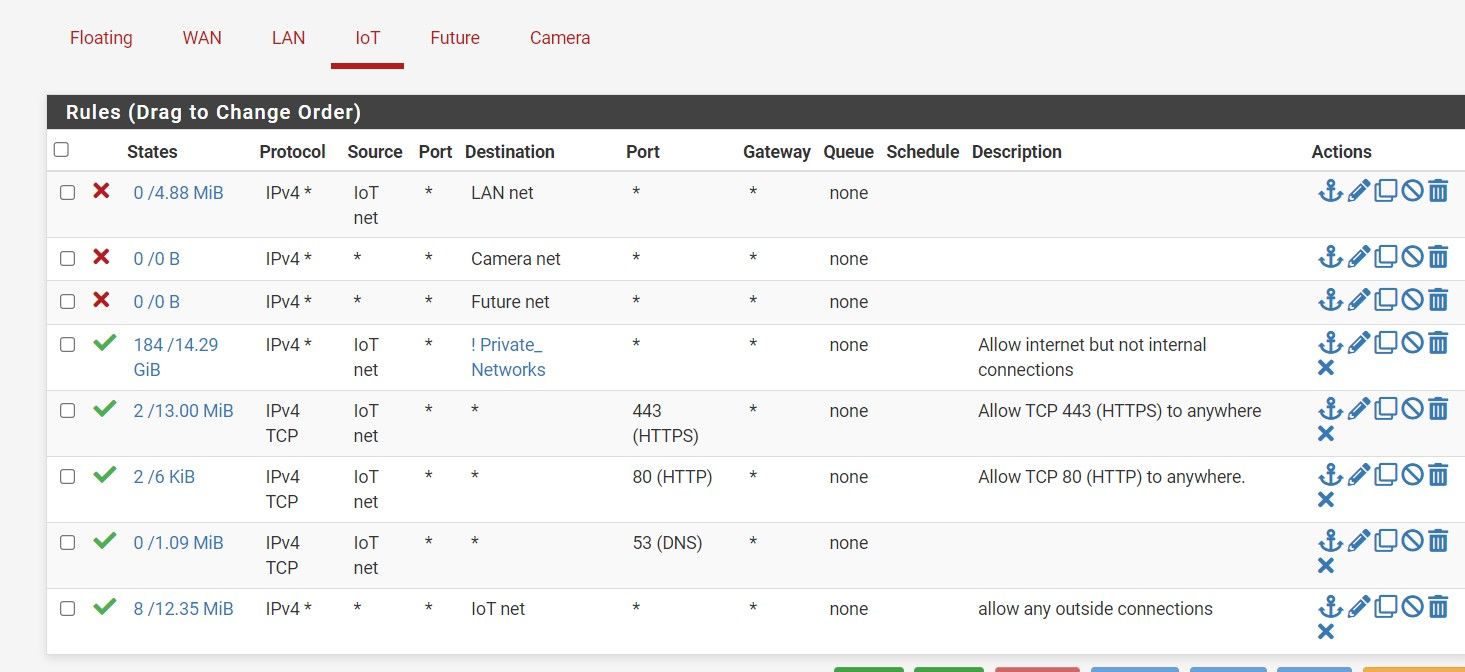
-
@daduls
Well, I couldn’t get it to work correctly so I’ve gone ahead and reinstalled the old configuration just to get back up and running. I’m going to do some research to see if I can figure out what’s going on and maybe try again when I have more time. Thanks to everyone for their input. -
@kevin-4
Are you changing your LAN or adding a vlan? Don't know your setup but since you have the old config backed up you could go through "System-General Setup" if its for your LAN? -
@daduls
I was changing my LAN and VLANS to the 172.16.x.x. As I am studying the proper use of IP address and subnet schemes, I realize I should have used the /16 with a subnet of 255.255.0.0 as FS380 suggested above, instead of the 255.255.255.0 (/24).I'll give it another try next week when I get a chance.
-
Using a /24 for a single interface/subnet is typical and shouldn't cause a problem.
Firewall and NAT rules would usually not need changing because they use aliases such as 'LANnet' and that would be updated. However if you have rules using specific IPs those obviously would.
Steve
-
@kevin-4 said in Warning about internal IP Range:
I realize I should have used the /16
No that is not a good idea.. /24 is the standard typical size that should be used on most networks, especially a home... It gives you plenty of IPs to work with 254.. Is easy to tell network X from network Y via the 3rd octet, and doesn't waste while large the limited rfc1918 space..
/16 - you have plans of ever coming anywhere close to 65K devices on the network?
Using such a large space also increase possible overlap.. talking to remote network..
LAN and VLANS to the 172.16.x.x
That wouldn't work with a /16 that would be the same network.. if using /24 for example 172.16.100, and 172.16.101/24 would be different networks.
-
@johnpoz
Well, ok. That you all for that advice. I'm in over my head when it comes to IP's and their relationship to the subnets. (though I'm learning.).With that said, I'm still confused as to why my Netgate 6100 running pfSense+ stopped feeding the internet to the internal network after I made changes from:
192.168.10.x to 172.16.10.x
192.168.20.x to 172.16.20.x (VLAN)
192.168.30.x to 172.16.30.x (VLAN)
With subnet of 255.255.255.0
All the networks are on the same interface and when I had completed the above changes to all the devices, everything was working fine.NOTE: I am making all the changes to the network addresses because I want to use something less common on my private network and I thought it would be fun to do so.
Hours later I changed my VPN IP address from 192.168.100.0/24 to 10.11.12.1/24 (Which I did thinking that I'd not see this network very often when if I use the VPN on a public network.). As soon as I made the change, the internal network (which was still working), stopped receiving the internet from the firewall and I couldn't fix it.
Looking back, I should have changed the VPN back to see if that was the cause, but at the time I figured it couldn't be that. After a few hours of troubleshooting I converted back to the old setup via a backup config file.
Is there anything obviously wrong with what I am attempting?
-
@kevin-4
When I made a change after setting up my VPN I experienced a very similar outcome. I don't think all the additional configurations (VPN) follow the changes to the LAN IP. Where some would think this convenient, security is never convenient and PFSense is designed to be secure.My solution was to start over. I reinstalled from usb with my new IP, recreated all the vlans and the VPN.
All I can say is it was tedious but it works. I'm much more 'begin with the end in mind now".......
-
The subnet changes you made should have been fine. There's nothing wrong with those values.
I would guess that you either lost the default route/gateway for some reason or created a subnet conflict with that VPN subnet.
Its possible your ISP could be using an IP in that subnet for their gateway IP. It would probably have to be a PPPoE WAN for that though. For example my ISP here uses 172.16.13.252 for the gateway and that's inconvenient.Steve
-
@daduls
I’ve been thinking the same thing. Do a factory reset and start over using the new configurations. I have learned a lot of cool stuff trying to work on this issue. There is a YouTube channel CertBros that are awesome in their networking fundamental videos. It filled in a lot of gaps in for me.I appreciate your input @daduls
-
@stephenw10
I appreciate the confirmation of the values. I’ll try again soon.