Pfsense as client and remote wireguard server
-
Hello
i am trying to create a VPN tunnel with following setupwireguard server on oracle cloud server
PFsense as a clienti have sucessfully
- created the WG server on the oracle cloud (10.66.66.1)
- created tunnel in the pfsense - with handshake done and green (10.66.66.3)
- created VPN interface - gave static IPv4 (10.66.66.3/32) as mentioned in the client config with no upstream gateway, and MTU 1420
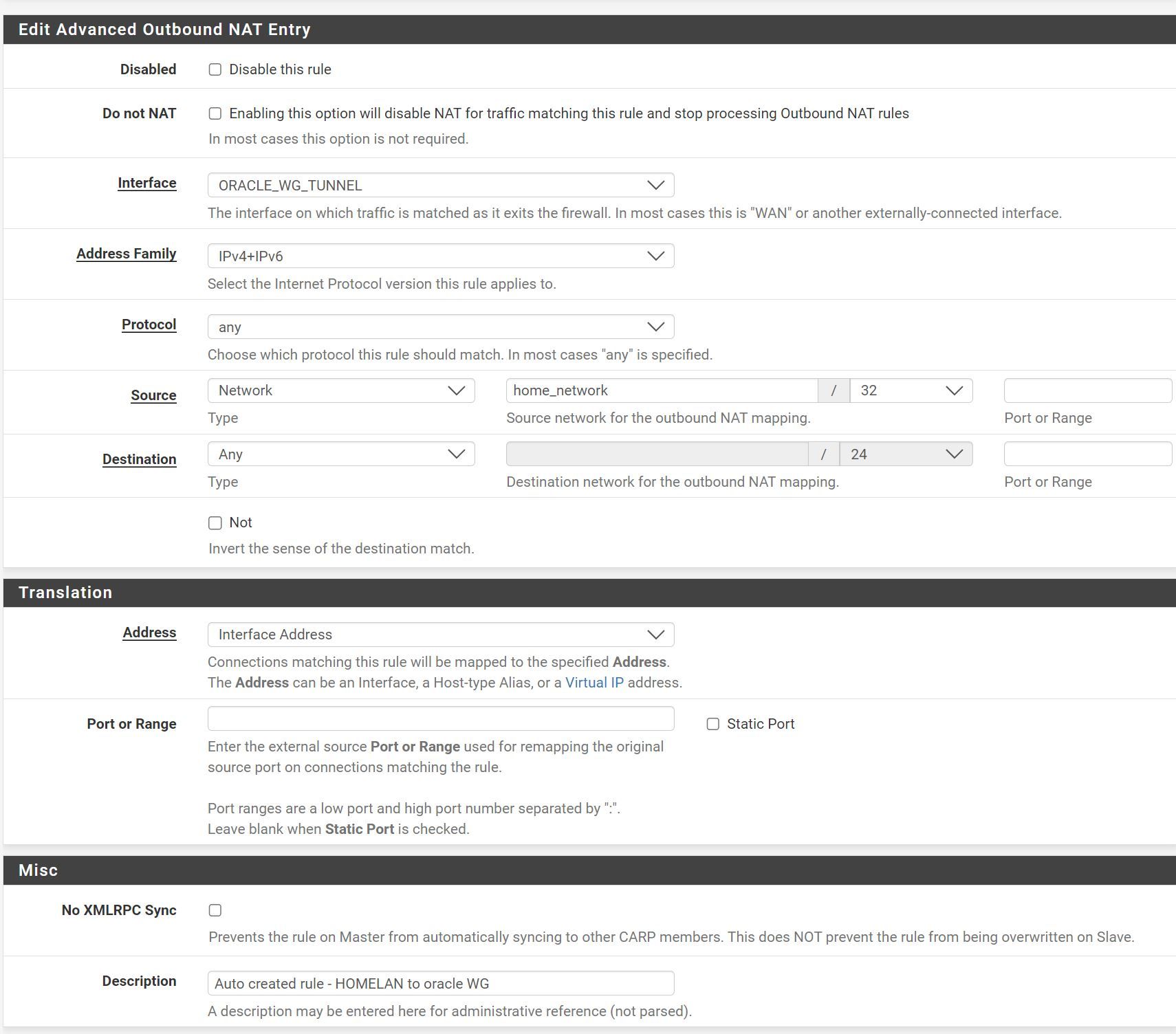
- created outbound NAT rule allowing local network to connect to oracle server on specific port — interface(oracle tunnel), source local network(192.168.1.0/24) with all ports(*),destination oracle server IP with port 51821
- able to ping all peers from the server (10.66.66.1) but not vice versa
- defined a static route 10.66.66.0/24 (oracle server wg ip) via my default WAN gateway
- wireguard firewall global rule - allow all on ipv4 and ipv6
My issues
-not able to route any traffic to the VPN
-not able to ping the server
-not able to see seperate submenu with VPN gateway on the dashboard, VPN gateway is with other gateways
-ability to make firewall rules to allow specific devices to route thru WG -
just to add
- able to ping oracle server from pfsense GUI --diag-Ping
but not able to ping from home network clients.
- able to ping oracle server from pfsense GUI --diag-Ping
-
any ideas...
-
@puneet1984 Did you followed this guide: https://forum.netgate.com/topic/68481/tutorial-configuring-pfsense-as-vpn-client-to-private-internet-access
If not, you could read to see where's your misstep.
-
@puneet1984 said in Pfsense as client and remote wireguard server:
created outbound NAT rule allowing local network to connect to oracle server on specific port — interface(oracle tunnel), source local network(192.168.1.0/24) with all ports(*),destination oracle server IP with port 51821
You should not have a destination port set there unless you are only trying to access a specific application on the server at that port. Even so it would be better to restrict that using firewall rules instead.
@puneet1984 said in Pfsense as client and remote wireguard server:
defined a static route 10.66.66.0/24 (oracle server wg ip) via my default WAN gateway
That is the tunnel subnet no? That should never be via the WAN it's a locally connected subnet on the WG interface.
Is there another subnet in Oracle Cloud you're trying to access over the tunnel?Steve
-
@NollipfSense
i followed the guide and yes got it working.. i was doing wrong outbound NAT rules.@stephenw10
yes you are correct...
i removed the outbound NAT rule and added
now able to ping the remote server
in the firewall rules of home networkThanks a lot guys for the help..
have another question though,
i have two WAN connections from different ISP, is there a way i can decide from which WAN connection i want to have the tunnel made.
also one WAN is double NAT and other WAN is in bridge mode with dynamic public IP allotment.
SO will WAN with double NAT will be able to connect to the oracle wg tunnel??
i am not sure whether in wireguard, server initiates the connection or peer does.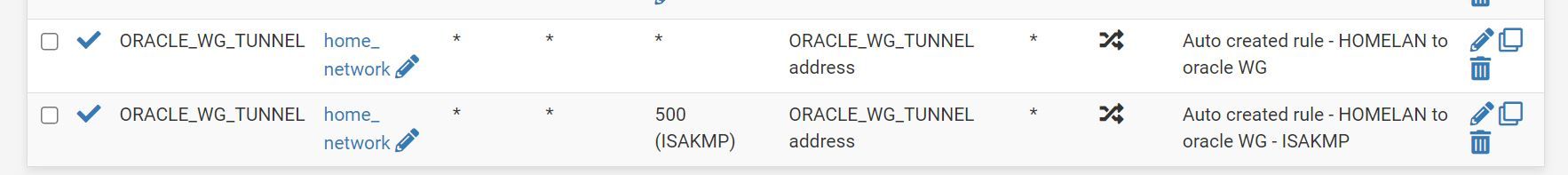
-
hello
another query -
is there a way to access home network using the oracle tunnel
normal connection --
home network (eg. NAS) <---> pfsense <--->WAN
also
pfsense <---> WG tunnel
remote device
laptop tethered to mobile device on LTE/5G<---> WG tunnelnow can laptop use home network devices ( i suppose iptables would be required on server/pfsense)
laptop <--->tethered LTE/5G <--->WG tunnel <--->pfsense <---> home network(NAS) -
@puneet1984 said in Pfsense as client and remote wireguard server:
is there a way i can decide from which WAN connection i want to have the tunnel made.
You can set a static route the OracleCloud public IP via whichever WAN gateway you want.
@puneet1984 said in Pfsense as client and remote wireguard server:
SO will WAN with double NAT will be able to connect to the oracle wg tunnel??
The client would still be able to open outbound connections through it so the server can reply back using the open states, yes.
You are running pfSense at both ends of this tunnel?
If so then both your home client and the remote access client would connect to OracleCloud and traffic could be routed appropriately there, yes. However to do that you would need to route all traffic rather than NATing it across the tunnel as you are now. That means each end would need to have the correct subnets in the peer config and static routes added.Steve
-
@stephenw10 said in Pfsense as client and remote wireguard server:
You are running pfSense at both ends of this tunnel?
not running pfsense on both ends of the tunnel...
pfsense is running on my home network..
remote server(oracle) is not on pfsense.@stephenw10 said in Pfsense as client and remote wireguard server:
You can set a static route the OracleCloud public IP via whichever WAN gateway you want.
will try it and update