Full mesh two device Netgate HA with 3 zones
-
We are in the process of replacing a pair of Netscreen (Juniper) SSG140s which are configured as a full mesh HA. There are three zones: WAN, DMZ and LAN. They were setup in 2011 and have been running very smoothly since.
The performance of the SSG140s is fine for our requirements (WAN is only 100M for instance), so it looks like a 6100 or 8100 would meet our needs fine from that point-of-view, if the interfaces can be configured appropriately.
Of concern is that WAN3 and WAN4 cannot be used with copper, but could one of those be used for the sync e.g.
WAN1 and WAN2 on each device connected to each WAN switch. LAN1 and LAN2 to the LAN switches and LAN3 and LAN4 used for the DMZ?
Many thanks for any advice
David
PS we had been trying a pair of Juniper SRX340s, but the GUI was painful and committing, even on a newly zeroized device with minimal configuration took over 30 seconds on a single device prior to looking at configuring an HA cluster.
-
@davids8 100 Mbps is not a problem for basically any Netgate hardware.
I am not entirely sure of your question...? What are WAN3 and 4 in your example?
pfSense can do HA. We have it in our data center. For three zones you would need 3 interfaces on each device plus one for sync.
https://docs.netgate.com/pfsense/en/latest/highavailability/ -
@steveits Many thanks for your prompt reply.
The Netgate 6100 and 8100 have 8 ports to play with, but for a fully redundant HA setup (not just the firewalls paired but also the switches on each network, plus two independent internet feeds) you have to use 2 ports for each network on each firewall, so that is 6 ports.
That would seem to leave two to play with, but on the 6100 and 8100 those last two ports are SFP and are stated not to accept RJ45 copper connections (a limitation of the C3000 series Intel processor).
- HA
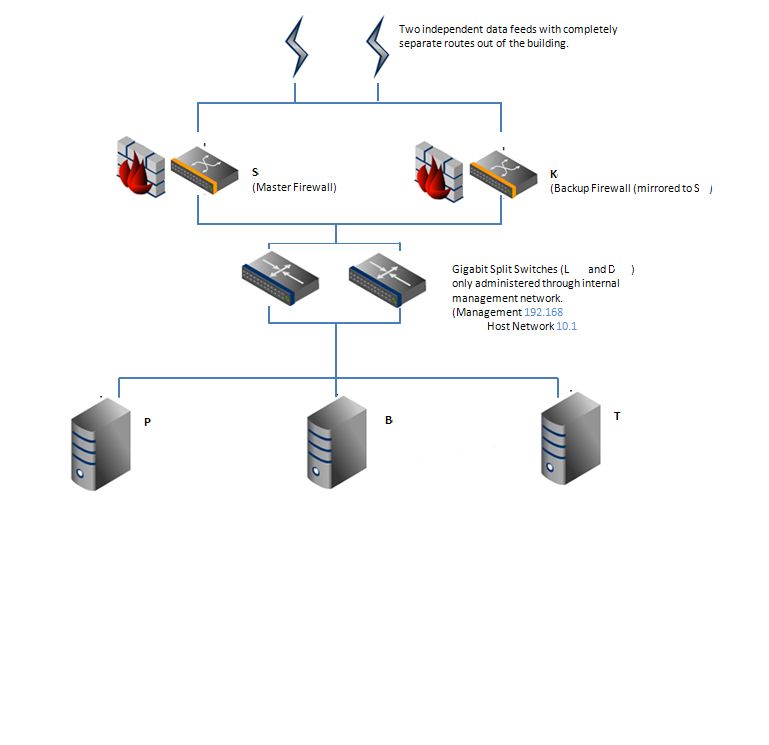 This is an incomplete diagram as the switches are segmented so the Management (Trust) and Host (DMZ) networks share the same switch. Also it doesn't show the WAN-side switches.
This is an incomplete diagram as the switches are segmented so the Management (Trust) and Host (DMZ) networks share the same switch. Also it doesn't show the WAN-side switches.
So the questions are really:
-
Can we configure one of the WAN3 or WAN4 ports to act as the sync connection between the two firewalls. Not having used anything other than copper, can fibre be used, for instance, with no intermediary device?
-
Is a combination of four ports on the same network, but with only one active at any time manageable?
Hope that helps and thanks again,
David
- HA
-
Yes, you can use the SFP+ ports as sync if you need to. You could use a DAC cable there or fiber. You can also sync across a VLAN though so it should not be a restriction.
I'm not sure exactly what you're asking in question 2, can you clarify what the 4 ports would be there?
Using LACP LAGGs for the L2 redundancy?
You might also use this sort of setup: https://docs.netgate.com/pfsense/en/latest/highavailability/layer-2-redundancy.html
Steve
-
@stephenw10 Thank you for confirming about the SPF+ ports. One thing less to worry about.
And thank you for the link to that L2 approach: I had seen that document earlier but then couldn't find it again.
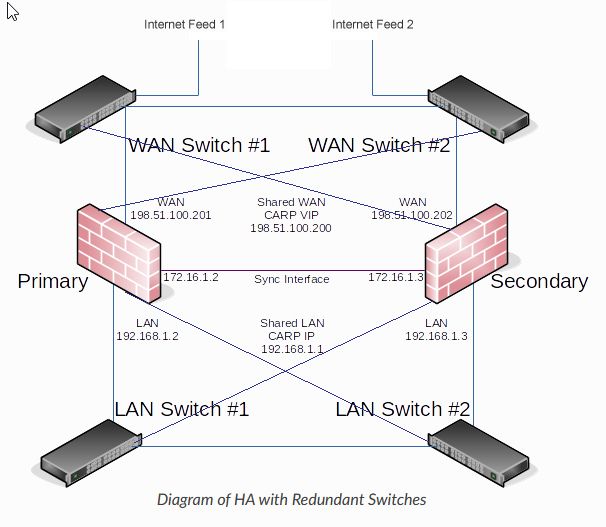
The reason for 4 ports is perhaps more easily understood from this diagram modified from the one on the L2 document you referenced. As you can see, each firewall has a connection to each switch, so if one switch fails, packets re-route via the other but still using the same firewall. That way the firewalls don't have to switch their master-slave relationship for an external failure. So two firewalls with two switch connections per network on each; four in total per network.
(The internet feeds are independent in our case with the provider using an IP test to determine if connectivity is lost on the default connection. We don't have the details of how they configure that.)
BTW, the cross-overs between the pairs of switches could be redundant with our config, but are in place without any special provision to avoid a race condition or layer 2 loop. The switches have separate management IPs, in the Trust network.
With Netscreen (now Juniper) SceenOS they had a layer 2 protocol for creating clusters of ports called NSRP (NetScreen Redudant Protocol) which handled the combining of ports across devices. Clearly with pfsense it will be necessary to achieve something like this with LAGG, perhaps using LACP or Failover (since we don't need the performance aspect of combining ports). What I can't be sure about is whether this setup was tested to work in all circumstances!
It may be the only answer may be to get a couple of suitable devices and try various configurations if no one else pops up with confirmation that this particular config works.
The switches are HPE 1620 24Gs without any link aggregation.
David
-
Mmm, really I would want to use LACP LAGG with switches that support cross chassis LAGG. On the LAN side at least.
-
@stephenw10 Thanks you. I will look into that when trying it out for real.