connection is not private when using Chrome
-
Hi,
i installed squid on pfsense and created certificates and imported it to firefox and every things works normally,but when i imported cert. to windows globally and tried to access pfsense from chrome i got the attached error (connection is not private) and if i click on advanced to proceed i got the error:
(92) Protocol error (TLS code: X509_V_ERR_SELF_SIGNED_CERT_IN_CHAIN)
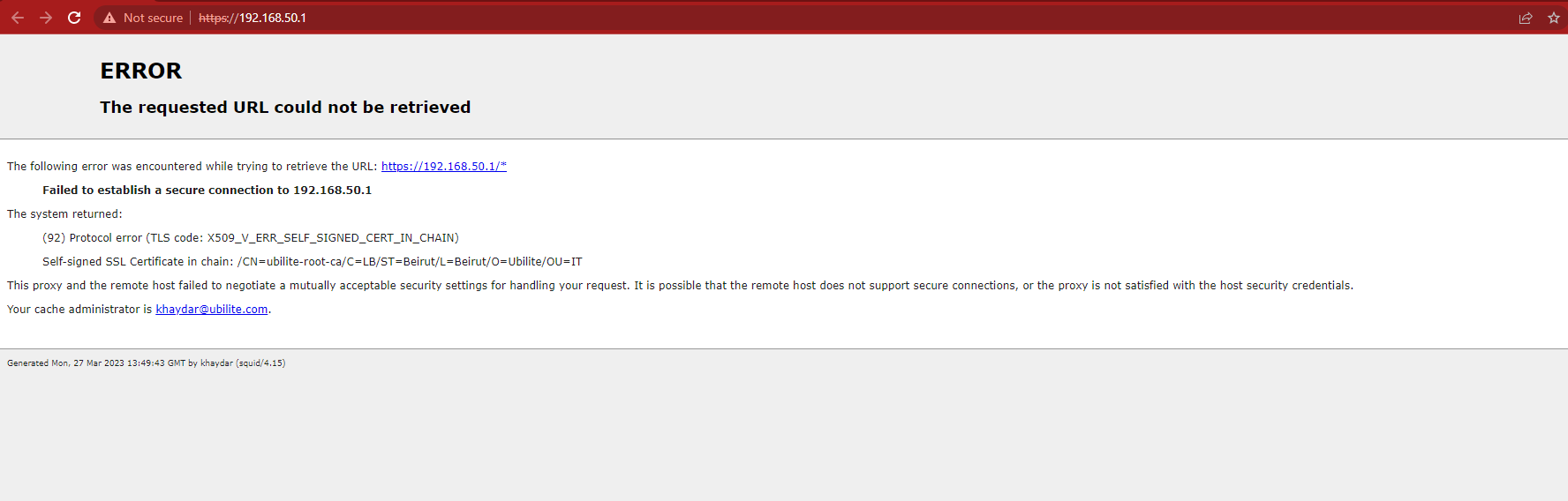
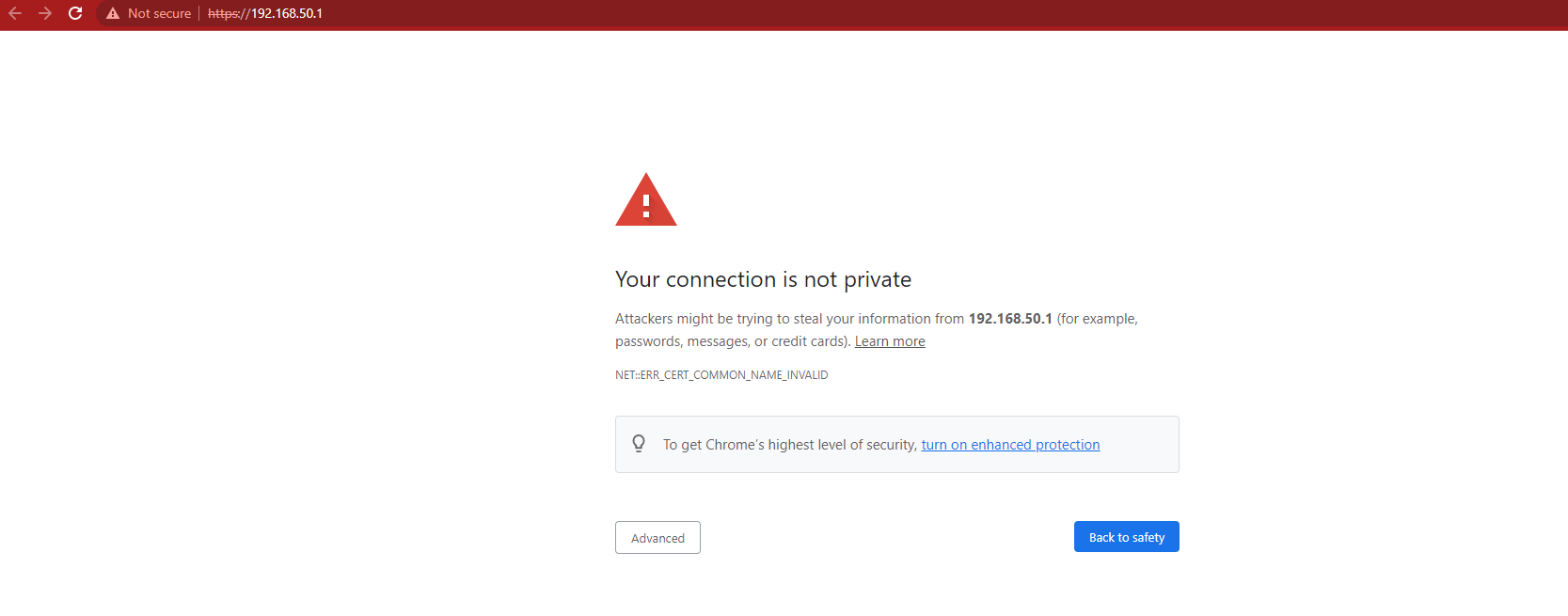
your help is very appreciated
Thanks
-
@karimhaydar31
pfsense web UI still has a self signed cert attached. Change it.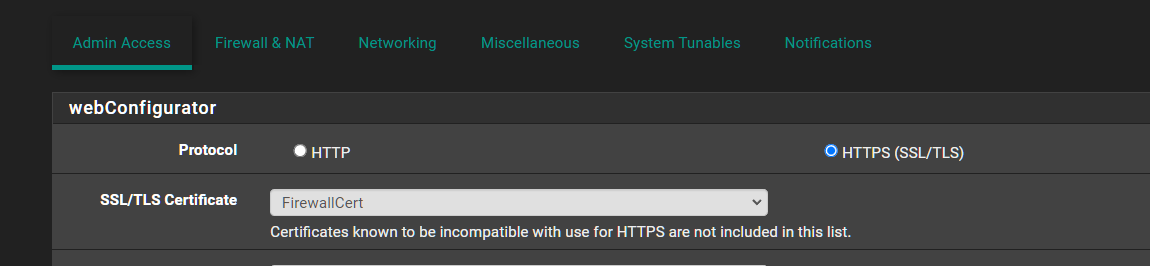
-
@karimhaydar31 said in connection is not private when using Chrome:
X509_V_ERR_SELF_SIGNED_CERT_IN_CHAIN
The certificate is valid, but not co-signed by one of the major players, like Verisign etc. see here for a list.
The thing is, your browser only accepts (and stays silent) certificates if they were co or toot signed by one of the authorities that are on 'the list' (in your device).
You could actually empty this list, and your browser would not even trust https://www.micirostf.com any more.So, the easiest thing to do, is : export the certificate that is being used by the Webconfigurator, and import it into you browser / OS.
Now, your browser / OS it trust it, and no more errors. That's all it takes !You could also get your hands on a certificate that is trusted out of the box.
A trusted certificate is free.
Example : if these are your general settings :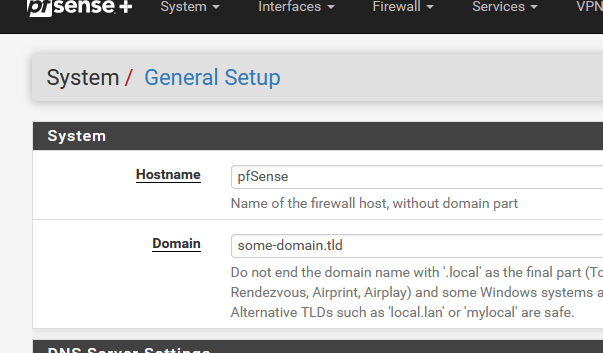
and you actually own, or rent the some-domain.tld domain name, you could obtain certificate for *.some-domain.tld for free.
The pfSense package "acme" is all about that functionality.
Again : the certificate will be free, the domain name will cost some money.