This is a better WPAD file
server.modules = (
"mod_access",
"mod_staticfile",
"mod_expire",
"mod_setenv"
)
server.document-root = "/var/www/html"
server.errorlog = "/var/log/lighttpd/error.log"
server.pid-file = "/run/lighttpd.pid"
server.username = "www-data"
server.groupname = "www-data"
server.port = 80
server.bind = "192.168.1.6"
server.tag = ""
server.range-requests = "disable"
server.max-connections = 10
connect-timeout = 2
server.max-keep-alive-idle = 2
server.max-keep-alive-requests = 1
server.max-read-idle = 2
server.max-write-idle = 2
dir-listing = "disable"
$HTTP["request-method"] =~ "^(TRACE|TRACK)$" {
url.access-deny = ( "" )
}
# Cache WPAD and proxy PAC files for 1 day (good practice)
expire.url = (
"/wpad.dat" => "access plus 1 day",
"/proxy.pac" => "access plus 1 day"
)
# Disable access logs to reduce SD card wear (optional)
accesslog = ""
$HTTP["url"] =~ "^/(wpad\.dat|proxy\.pac)$" {
setenv.add-response-header = (
"X-Content-Type-Options" => "nosniff",
"X-Frame-Options" => "DENY",
"Content-Security-Policy" => "default-src 'none';",
"Cache-Control" => "public, max-age=86400",
"Referrer-Policy" => "no-referrer",
"X-Download-Options" => "noopen",
"X-Permitted-Cross-Domain-Policies" => "none"
)
# Allow only GET and HEAD methods
$HTTP["request-method"] !~ "^(GET|HEAD)$" {
url.access-deny = ( "" )
}
# Restrict access by IP subnets
$HTTP["remoteip"] == "192.168.1.0/27" { }
else $HTTP["remoteip"] == "2001:470:8052:a::/64" { }
else {
url.access-deny = ( "" )
}
}
# Deny all other URL requests
$HTTP["url"] !~ "^/(wpad\.dat|proxy\.pac)$" {
url.access-deny = ( "" )
}
# Strict URL parsing for security and consistency
server.http-parseopts = (
"header-strict" => "enable",
"host-strict" => "enable",
"host-normalize" => "enable",
"url-normalize-unreserved"=> "enable",
"url-normalize-required" => "enable",
"url-ctrls-reject" => "enable",
"url-path-2f-decode" => "disable",
"url-path-2f-reject" => "enable",
"url-path-dotseg-remove" => "disable",
"url-path-dotseg-reject" => "enable",
)
url.access-deny = ( "~", ".inc" )
static-file.exclude-extensions = ( ".php", ".pl", ".fcgi" )
# Add WPAD MIME type for correct browser handling
mimetype.assign = (
".dat" => "application/x-ns-proxy-autoconfig",
".pac" => "application/x-ns-proxy-autoconfig"
)
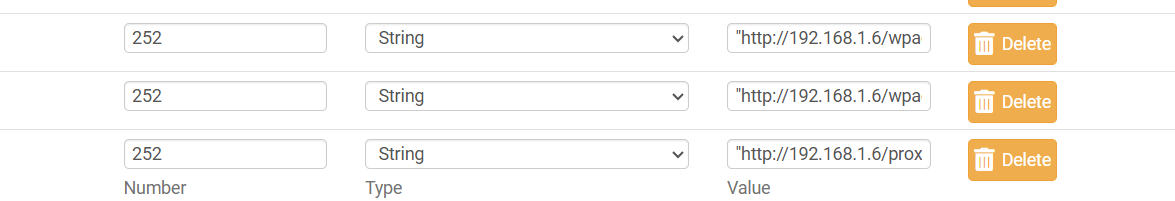 7
0 Votes18 Posts6k Views
7
0 Votes18 Posts6k Views 1
0 Votes1 Posts779 Views
1
0 Votes1 Posts779 Views