Trouble with C.A. signing on the Https PFSense certificate
-
Hi : I'm new here a and new use to the PF Sense software using a preexisting set up I inherited.
Here is the verioning information. Version 2.6.0-RELEASE (amd64)
built on Mon Jan 31 19:57:53 UTC 2022 FreeBSD 12.3-STABLE. Please don't snipe me as I'm inhertingg this mess and trying to understand one thing. On the certifiate page for the PFSHttps website config and has the following stated.PFSense HTTPS
external - signature pending emailAddress=, ST=NY, O=BLOC, L= Elmhurst
CN=pfsensehttps-ca, C=US
Once again I'm not familiar with this software and I'm just learning this now. This license certificate was just reissued and I was wondering how do I get the the signed certificate from the C/A ? Or does this happen automatically and how long does this take ? Please let me know and thanks for your patience. -
@pf-sense-help where are you seeing that exactly.. What license certificate - there is no license certificate?
Could please post a picture of where in pfsense your actually looking..
how do I get the the signed certificate from the C/A
If you create a CA, and then sign a cert with that ca, the certificate would be available to download in the certs section of the certmanager..
So for example, I have a few CAs in pfsense, and create different certs for different uses.
If I create a cert with my HomeCA, fill in the form, and then can download the cert or key for that cert in the certifications section. Notice on the top it says it created it when I hit save.
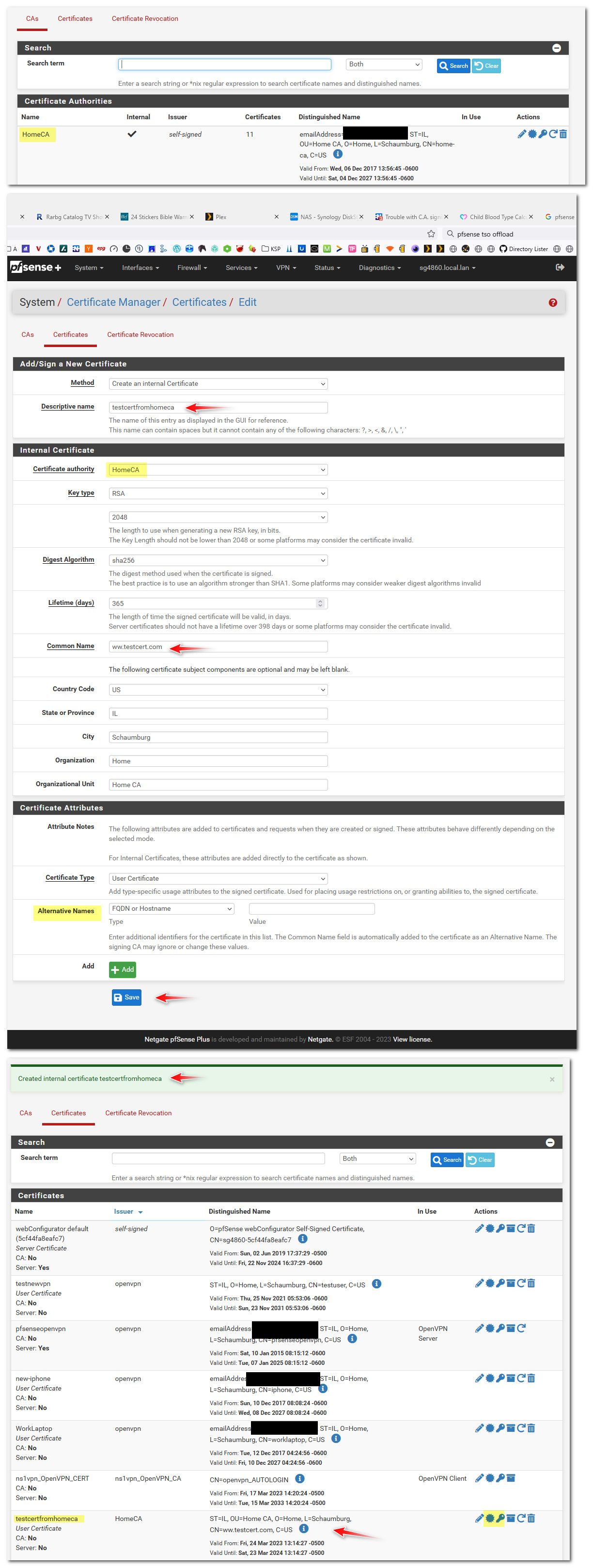
-
Hi: Thanks so much John for the quick reply. I didn't want to issue a new cert because the documentation states I would need to install the cert on all remote computers. So I just reissued it . I tried your suggestion by going the the Cert and exporting it and importing it into the the waiting certiciate but it is failing.
-
external - signature pending
That would indicate that you didn't actually create your own cert with your own CA, but you put in a CSR to some external CA to sign.. You would need to get that info on the signing from the external CA.
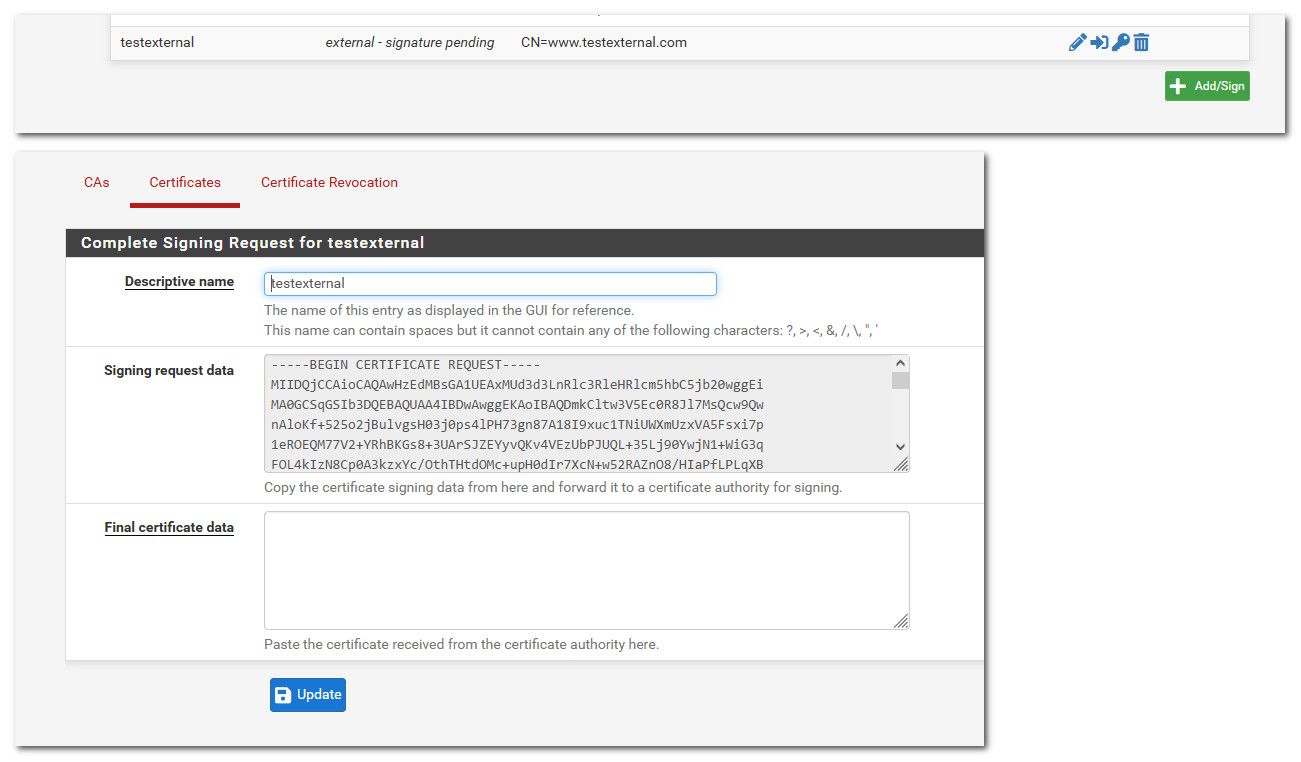
Who signed the original cert? If this is not for some public domain.. You can just create your own certs and CA.. If its a public domain, you could just use ACME to get a cert, etc.
-
Hi: I see theat the remote users are using the original CA but the following accounts are using self-signed certificates.
webConfigurator default (59c54c2a2172f)
Server Certificate
CA: No
Server: YesThere are two of these. How would I see who origially signed the one in question ?
Not aure how to do that . Thanks so much for your help. -
@pf-sense-help said in Trouble with C.A. signing on the Https PFSense certificate:
webConfigurator default (59c54c2a2172f)
That is just the cert for the pfsense web gui, only people access that should be admins.. I personally see no reason why that should ever need to be a publicly trusted CA.
If admins don't want to get bothered by their browsers about - just create a cert with your own ca, and have your admins browsers trust your ca..
-
Just to let you know I do have a private cert that OpenVPN users use to gain access to our network. I tried to export that and paste it in to vary the cert but it failed. Can I just copy the original signing request data and key from the CA cert now in use ? I tried copying the key but didn't touch the signing request data dialogue box. Wasn't sure if it would default back to the original signing request if I changed it to the one in use for our remote users
-
@pf-sense-help said in Trouble with C.A. signing on the Https PFSense certificate:
How would I see who origially signed the one in question ?
look in your cert manager..
Example here is my default selfigned web gui cert that I do not use. And then a cert that is externally signed by acme for example
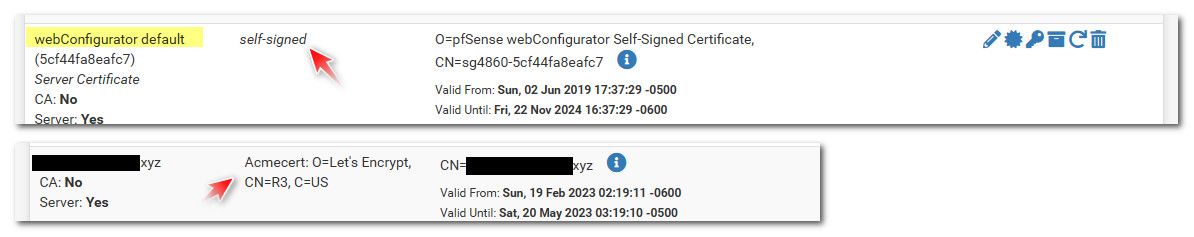
Here is the cert I use for my web gui, cert I signed with CA in pfsense that I created, and my browser trusts.. I have also added SAN of pfsense IP.. So I can access it via my browser by fqdn or IP (rfc1918) and my browser trusts it
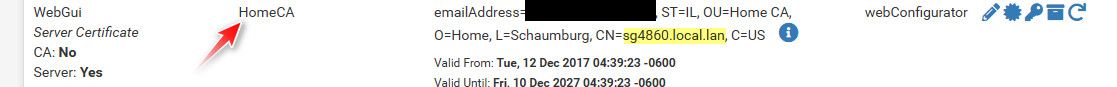
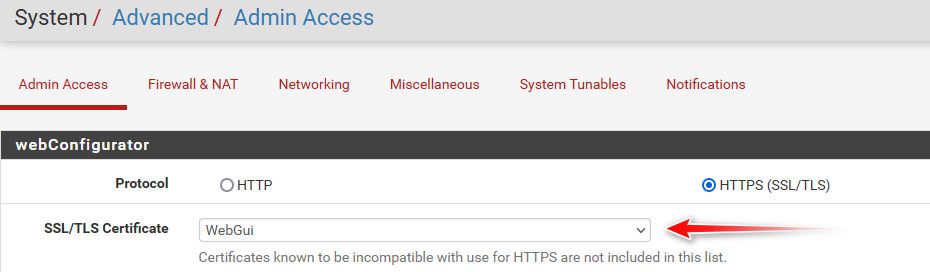
-
Hi Thanks again.
As I stated prior the Issuer just says " external - signature pending"
Can I use my original CA that is set up for network access for remote users or is there something
special about the PFSense HTTPS that it would need to be digned by an external CA signer ? -
@pf-sense-help said in Trouble with C.A. signing on the Https PFSense certificate:
Can I use my original CA that is set up for network access for remote users or is there something
A CA in pfsense that you used to create your openvpn certs? Yeah you can use that CA to sign your web gui cert.. There is nothing special - As long as your browser trusts the CA, any cert signed by that CA would be trusted.
-
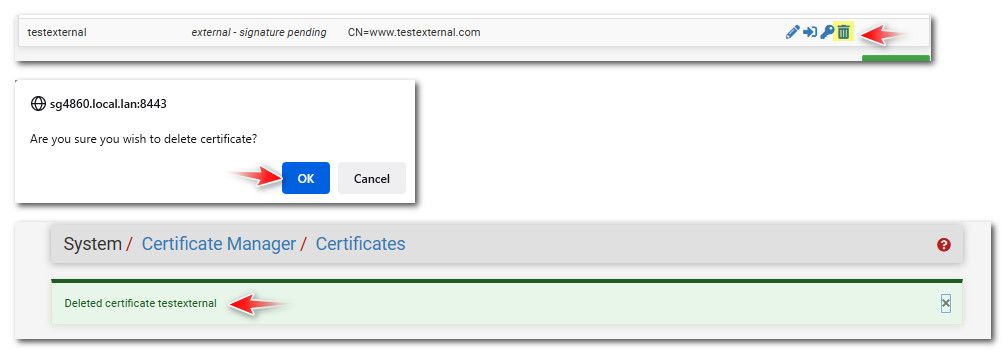
Here's the problem when I go to the original certificate request I can't delete or change the request as it is still pending. Does the certificate final data get emailed to the email adress on the the email included in the distinguished name line ?
-
@pf-sense-help said in Trouble with C.A. signing on the Https PFSense certificate:
I can't delete or change the request as it is still pending
-
 J jimp moved this topic from Problems Installing or Upgrading pfSense Software on
J jimp moved this topic from Problems Installing or Upgrading pfSense Software on
-
Hi: Just a quick update. I was able to delete and create a new the Https PFSense certificate.
I used the original CA which is the only one listed on the CA's page. It is now self-signed and in the right object container. Before the oject container was not correct. Thanks for help.
I'm not really sure why a reissue would have went from self-signed to request an outside CA signing? Not really sure how to check to see if this is implemented as you described earlier allowing secure broswer access automatically. Thanks so much for your input in this situation it is greatly appreciated.Thanks!!!!
-
@pf-sense-help here is a quick walk thru I did years ago, that still valid
https://forum.netgate.com/post/831783
This is how you would create a CA, sign a cert and have your browser trust it. You can use whatever sections of it you need if parts have already been accomplished.