DNS DOS flood attack
-
Hey Guys,
For the last few days my SG1100 has been flooded with spoofed DNS traffic that has affected the DNS service by making it unable to resolve any FQDN's. It's restricted to the device where the service is running and affects ALL devices connected to that firewall.
Details of the packets:
Interface: WAN
SRC addr: My IP address
SRC port: Random
DST addr: DOD / US Navy Intell.
DST port: 53I believe the addresses are spoofed because my IP address is the source on the WAN interface where it should be the destination address. Interestingly, the destination addresses ARE confirmed US Naval Intelligence servers! Someone has an axe to grind, lol!
SOLUTION
Anyway... After some switching-off, switching-on... plugging-in, plugging-out... restarting, stopping and starting... and reconfiguring... it looks like if you rely on your NetGate device to be the DNS Server, address resolution and your ability to access websites will fail. I had to stop the DNS Resolver service which stopped anymore traffic being logged and change the configuration of individual machines to use an external DNS service i.e. 9.9.9.9. This solved the problem. -
@asgr71 While I do have internal DNS servers, those servers forward internet DNS requests to PFSense which uses root servers (no public servers listed on the System/General Setup tab), as many people do and see no issue. Your info shows the source as 'My IP address' (assuming the WAN IP?) Typical random source port. Destination being port 53 some US Navy IP. Why should you expect your IP be the destination on port 53. Do you have an internet facing DNS server? I would expect that if something in the internal network or PFSense itself were trying to connect to something on the internet that the source would be PFSense on random port and destination would be whatever it was querying on 53 if DNS. Something coming from your network TO those Navy IPs.
Doesn't sound like a spoof to me. Sounds like something inside your network is hitting PFSense to resolve something over and over. And setting public DNS servers on those devices is just allowing them to jump around PFSense for DNS as opposed to resolving the issue on whatever device(s) is causing it. I'm no expert but that is what it looks like to me...
-
Thanks Tzvia for your reply...
I tried unplugging each system one by one to see if I was part of a bot-net, fortunately no change in the traffic to the WAN interface. I then reconnected all systems and pulled the internet connection and, predictably, all port 53 traffic on the WAN interface stopped. The actual firewall log indicated that the traffic was WAN Outbound.I believe that it's affecting the DNS Resolver / unbound service and the proper functioning of the device. Is this a deficiency in the software?
Here's a screen dump of the firewall logs from earlier...
First on the list:
192.112.36.4 DoD Network Information Center (DNIC)
192.33.4.12 PSInet
199.7.91.13 Uni of Maryland
192.112.36.4 DoD Network Information Center (DNIC)
192.58.128.30 VeriSign
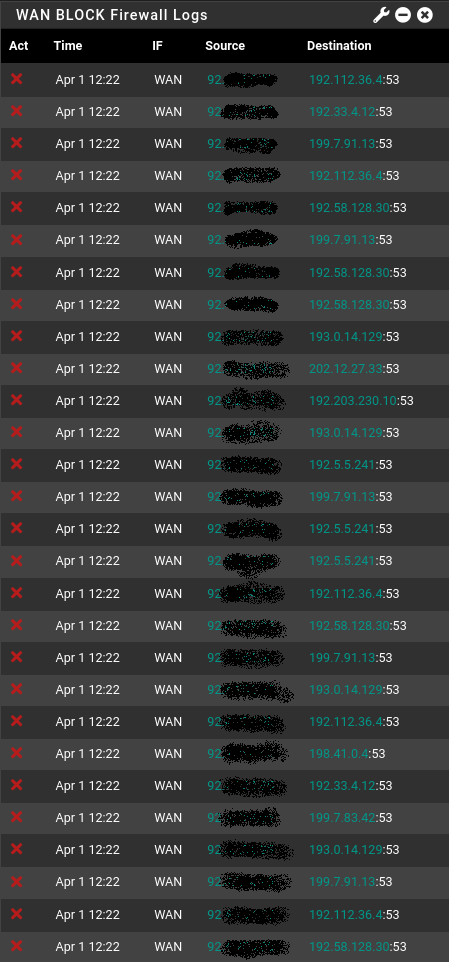
-
@asgr71 Do you have any rules on WAN?
-
@steveits Hi Steve, no. I disabled all rules and NAT. Did have pfBlocker and Snort with IPS Option. Both services have been disabled but I'm still getting flooded with port 53 traffic.
Reverted back to Services -> DNS Resolver -> Disable and restarted Snort and all is good!
-
@asgr71 you understand those are root servers your talking too.
;; ANSWER SECTION:
4.36.112.192.in-addr.arpa. 82578 IN PTR G.ROOT-SERVERS.NET.Pfsense would not block outbound traffic from itself - unless you have a floating rule set to block outbound.. The widget your looking at there would not show that its an outbound block..
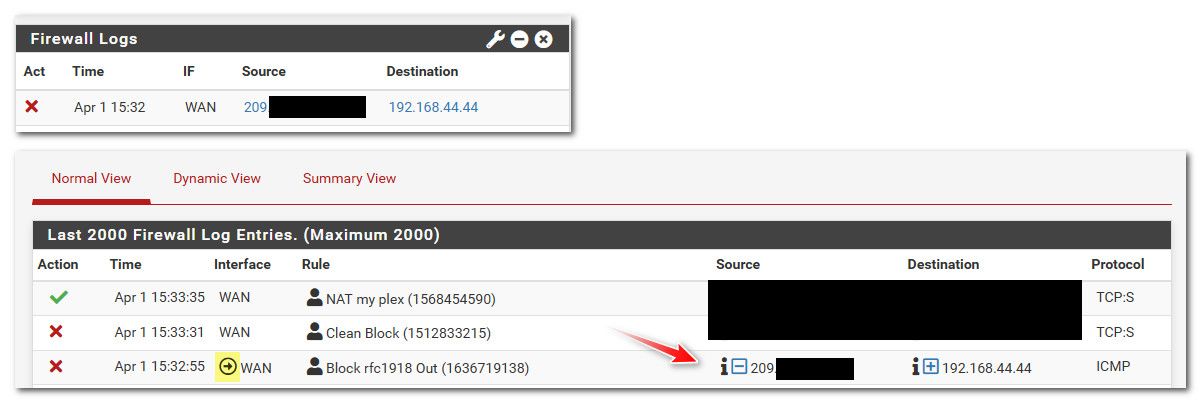
See the widget block, vs the block in the full log showing that is outbound, see the little arrow I highlighted.
All of those IPs being blocked are root servers.. Which is what outbound woudl talk to do its default resolving.
;; ANSWER SECTION: 13.91.7.199.in-addr.arpa. 14400 IN PTR d.root-servers.net. ;; ANSWER SECTION: 12.4.33.192.in-addr.arpa. 10800 IN PTR c.root-servers.net.Those are not inbound blocks those are outbound blocks.. What rules do you have in your floating tab?
What were you doing with snort? Trying to block dns? Snort shouldn't even be running on your wan interface..
The blocks you see that I posted is from my outbound block on wan if try to go to some rfc1918 address that is not any of mine - being a good netizen keeping noise off the internet. I generated those by trying to ping a 192.168.44.44 address
-
@johnpoz Thank you for your reply JP. Firewall -> Rules -> Floating is empty. Yes, did notice that I was talking to root servers... no idea why that is happening! Still don't explain why I'm getting DoD addresses as the destination!
Running SG1100 with unbound enabled and Snort with IPS Policy for 30 min and no port 53 traffic, all is quiet. If it was an interface config issue would it be intermittent or consistent?
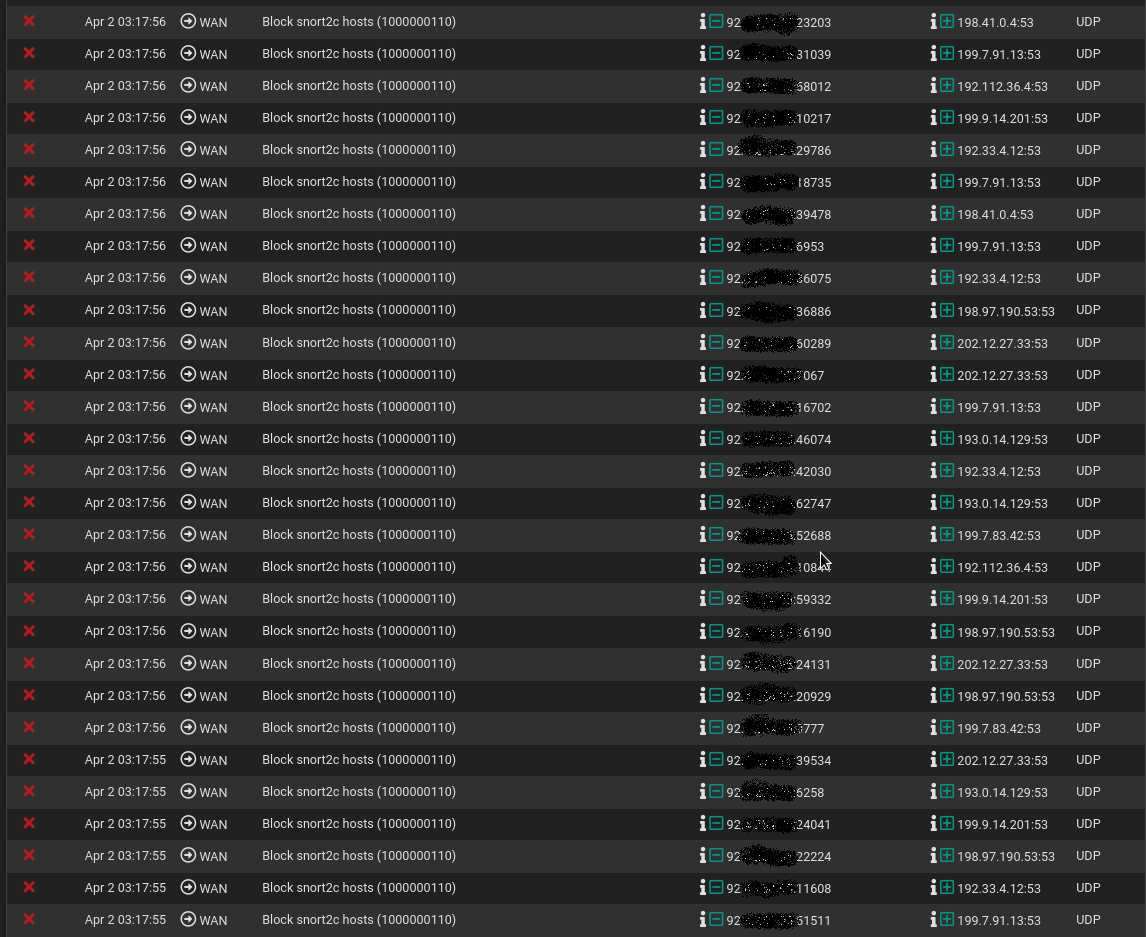
Running Snort on WAN because I had NAT ports open but blocking BOTH in/out bound IP addresses. Had a feeling that a system may have been compromised behind the firewall and didn't want to let established connections through the WAN interface... is this wrong?
-
@asgr71 if snort is running on WAN that is outside the firewall.
Snort-fw-pfSense-fw-Snort
Generally, running on WAN scans packets the firewall will drop anyway so takes extra CPU cycles. Running on LAN it can see the internal IPs. If snort is doing the blocking it could be something that tries, fails, and retries repeatedly because it keeps failing?
-
@asgr71 said in DNS DOS flood attack:
why I'm getting DoD addresses as the destination!
Where does it say DoD address? As I said that is an outbound block.. There is zero reason to run snort on the the wan.. But yeah some of the address space the roots are on would be DoD space..
CIDR: 192.112.36.0/24
Organization: DoD Network Information Center (DNIC)NetRange: 198.97.180.0 - 198.97.199.255
Organization: Headquarters, USAISC (HEADQU-3)But many of them are not.
CIDR: 199.9.14.0/23
Organization: B.Root-Server-OPS (BROOT)inetnum: 202.12.27.0 - 202.12.27.255
descr: root DNS server
country: JPRoot servers are hosted globally - they are not all DoD that is for sure..
NetRange: 199.7.91.0 - 199.7.91.255
Organization: University of Maryland (UNIVER-262)@asgr71 said in DNS DOS flood attack:
is this wrong?
Yeah...
-
@johnpoz Thanks again john. Decided to by-pass the whole local network and plugged the internet straight into Wireshark. Couldn't find any DNS packets! Did a factory reset and assigned Snort to the LAN interface and all is good! Thanks for your help.