Major DNS Bug 23.01 with Quad9 on SSL
-
@johnpoz said in Major DNS Bug 23.01 with Quad9 on SSL:
What it says is a "crash" was fixed when unbound restarting
It may be referring to https://docs.netgate.com/pfsense/en/latest/releases/23-01.html "A long-standing difficult-to-reproduce crash in Unbound...It is now safe again to enable DHCP registration alongside Unbound Python mode in pfBlockerNG." ...which is talking about pfBlocker vs DHCP, not that DHCP registration won't restart Unbound anymore. (I've seen others post about this sentence as well...)
-
@steveits said in Major DNS Bug 23.01 with Quad9 on SSL:
someone posted their problem seemed likely to happen when opening a group/folder of bookmarks/favorites at once...implying a higher number of simultaneous requests might trigger it.
Playing around with various settings, and I don't know if this has anything to do with the quoted comment, but I raised incoming and outgoing tcp buffers in resolver adv settings from default 10 to 20. I believe (or imagine) that it has reduced the frequency of unbound 'hangs' on my system.
-
S SteveITS referenced this topic on
-
Just thought I would comment on this as I am seeing the same symptoms. It only just started happening recently and thought it was load related but not much has changed on my end except upgrading PFSense and associated packages.
I have turned parameter off this for now... Use SSL/TLS for outgoing DNS Queries to Forwarding Servers as I need the stability.
Summary:
- Using Cloudflare SSL/TLS on 23.01 (ipv4 / ipv6 resolvers)
- Build: 23.01-RELEASE (amd64) built on Fri Feb 10 20:06:33 UTC 2023
- System Patches package with recommended fixes applied including a manual patch for redmine #13851
- Machine Core(TM) i5-8365U, 16GB Ram, 128GB SSD
- Internet Connection 100/20
- Running a number of wireguard gateways (3 servers, both ipv4 and 6)
- Running a number of packages including...
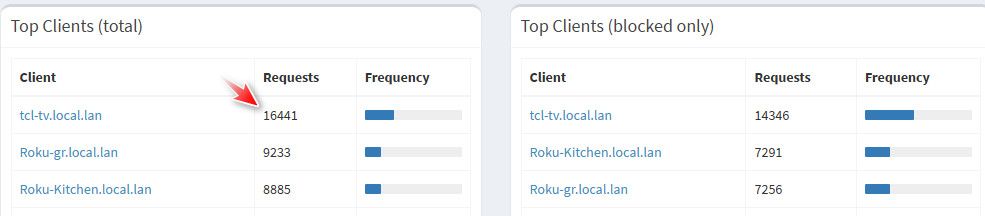
According to PFBlockerNG graph, my dns reply stats are around 10-20K per hour during the busiest times.
Over the last week or two, uptime Kuma randomly alerted me to dns issues which is the same time my family complained they couldn't access any websites or their game would fail stating their was no internet. This would happen randomly and would take a couple of minutes to clear up again.
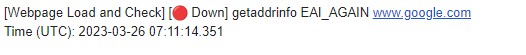
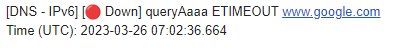
Fortunately I had graylog setup and unbound in debug mode for the most recent errors above.
Looking at the logs I note the following messages around the time where DNS briefly cut out...
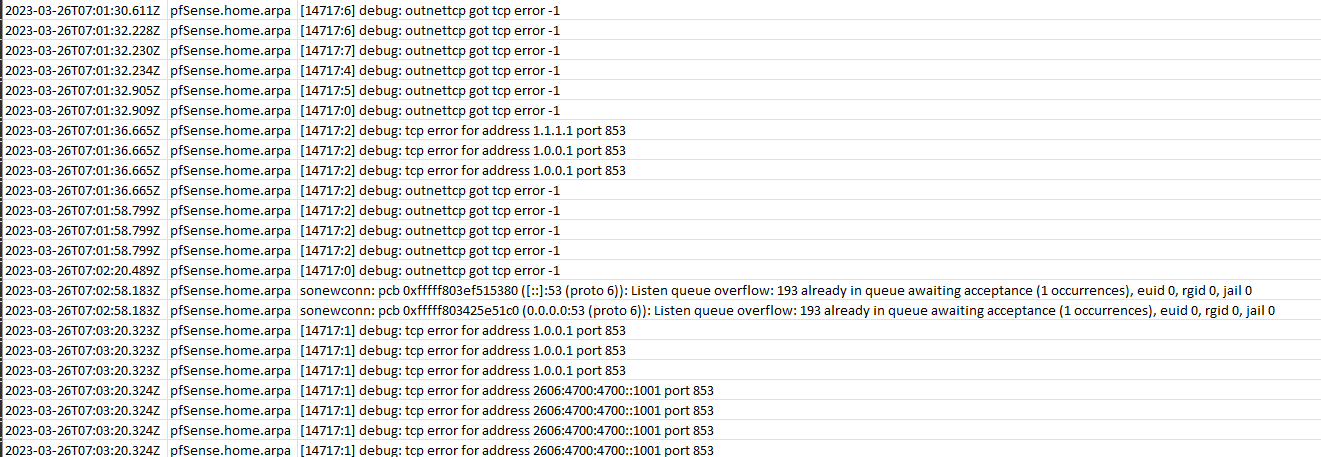
Looks like PfSense is not processing DNS requests quick enough for me. The sample above occurred whilst the internet link wasn't even loaded, neither was my machine.
I have turned this setting off and will monitor... Use SSL/TLS for outgoing DNS Queries to Forwarding Servers
I haven't done any further debugging and I hope this helps someone out, if not I apologise for this long post.
-
@joedan said in Major DNS Bug 23.01 with Quad9 on SSL:
10-20K per hour during the busiest times.
In your home? how many devices / users - you have a lot shit banging its head trying to resolve stuff your blocking.. That seems really high for a home..
That is what like 240K to 480K queries in 24 hours.. I see like 50k in 24 hours, and that is with 28 active devices doing dns.. Many of them banging their heads looking for shit that is blocked.
-
I also had occasional dns failures when using quad9 dns. I simply turned off forwarding mode and have had no issues with root servers doing the work.
I find this to be non-ideal, but at least functional. -
Just reporting in here that I have the same issues with 23.01 and Quad 9 DNS when using unbound DNS
My settings were as follows on 22.05 since 22.05 was released with no issues with internet and DNS resolution.
-
pfsense ubound DNS resolver enabled
-
Using forwarding to Quad 9 DNS servers
-
DNSSEC unticked
-
Use SSL/TLS for outgoing DNS Queries to Forwarding Servers TICKED
Upgraded to 23.01 this weekend just gone 2nd April 2023. No other settings have changed on LAN network and no other firmware's have been upgraded on any devices on network so I am confident that the only change was the upgrade to pfsense from 22.05 TO 23.01.
Everything worked fine yesterday 3rd April until this morning when I now get multiple DNS resolution issues and cannot reach websites.
I have now changed the following single setting.
- Use SSL/TLS for outgoing DNS Queries to Forwarding Servers UNTICKED
Websites are now resolving correctly.
I will continue to monitor DNS resolution over the coming days to see if the issue reappears and report back.
-
-
@johnpoz said in Major DNS Bug 23.01 with Quad9 on SSL:
In your home? how many devices / users - you have a lot shit banging its head trying to resolve stuff your blocking.. That seems really high for a home..
Yes I have around 35 devices, a few that are quite bad including a Swann Security DVR that is taking up 25% of that DNS traffic calling out dropbox domains even though I don't have that function setup.
Just wanted to loop back and advise I did resolve my issue however it involved going back about 6 backup iterations and manually reapplying all my config changes one at a time and am now back on DNS over TLS (Cloudflare) with 23.01, and all recommended patches applied. I did also move ISP's during that time of panic so unfortunately have nothing further to contribute here because I was under pressure to get things working again quickly and made significant change in such a short time.
I was never using Quad9 though which appears to be an ongoing issue with other posters.
-
@joedan said in Major DNS Bug 23.01 with Quad9 on SSL:
a few that are quite bad including a Swann Security DVR that is taking up 25% of that DNS traffic calling out dropbox domains even though I don't have that function setup
Introduction : read this first.
If a device asks ever x seconds to resolve an identical host name, then, at first, your uplink isn't used : pfSense will just serve the same info edit : from local DNS cache, as log as this is TTL permitted end edit to the device again, and again. You're just burning some watt hours at your place.
But if the TTL is short, like mere minutes or less, then, yeah, the WAN gate is opened, and you start to activate a whole lot more of software/hardware on both sidesThe thing is : as I said in the other thread : if you were looking at the WAN gate of quad9 (because, lets imagine, you work over there) : what would you do if you saw that some IP was clearly misbehaving ? => You throttle ?! As "just scale up the system up once more" without any cash flow in return will kill your job.
So, on your home site : your entire DNS just got delayed.And that's of course a 'pfSense DNS bug'

-
I agree this could be Quad9 throttling responses. But still it would have been the same in 22.05.
-
@skogs said in Major DNS Bug 23.01 with Quad9 on SSL:
I find this to be non-ideal, but at least functional.
Not wanting to start a big base line debate but why is letting a resolver do resolving non-ideal? Letting your box do DNS resolving on its own without any upstream forwarder that can be censored is a much more resilient setup (as we see) then having a single point of failure like a big DNS forwarder that throttles or censors DNS lookups (or in case of quad9 is jurisdically forced to do so). Just to try to hide your DNS queries from your ISP?
Just asking because I'm interested.
-
@jegr said in Major DNS Bug 23.01 with Quad9 on SSL:
Just to try to hide your DNS queries from your ISP?
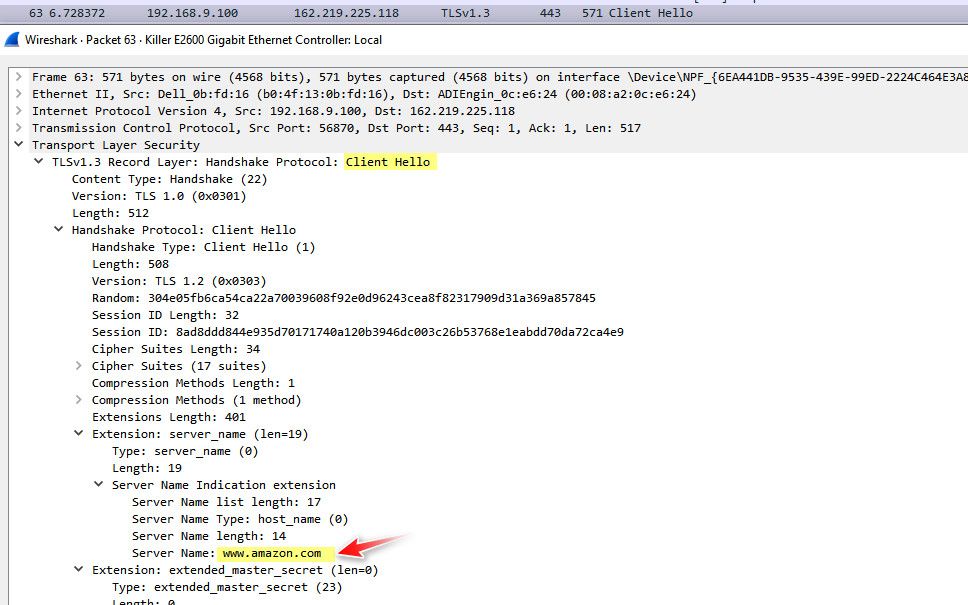
hahah - which isn't really happening anyway. So I do a dns query for www.amazon.com, which I want to hide from my isp ;)
So my isp doesn't see the dns query, but they see me go to IP address 1.2.3.4 which pretty obvious is amazon.com - and here is the big one.. They still see what you are asking for - its just not via dns..
Until such time that esni, which is dead - long live ech.. Is everywhere - you are just sending your sni in the clear in your handshake - so who exactly are you hiding your dns query from? And for what purpose?
-
@n8rfe said in Major DNS Bug 23.01 with Quad9 on SSL:
Just reporting in here that I have the same issues with 23.01 and Quad 9 DNS when using unbound DNS
My settings were as follows on 22.05 since 22.05 was released with no issues with internet and DNS resolution.
-
pfsense ubound DNS resolver enabled
-
Using forwarding to Quad 9 DNS servers
-
DNSSEC unticked
-
Use SSL/TLS for outgoing DNS Queries to Forwarding Servers TICKED
Upgraded to 23.01 this weekend just gone 2nd April 2023. No other settings have changed on LAN network and no other firmware's have been upgraded on any devices on network so I am confident that the only change was the upgrade to pfsense from 22.05 TO 23.01.
Everything worked fine yesterday 3rd April until this morning when I now get multiple DNS resolution issues and cannot reach websites.
I have now changed the following single setting.
- Use SSL/TLS for outgoing DNS Queries to Forwarding Servers UNTICKED
Websites are now resolving correctly.
I will continue to monitor DNS resolution over the coming days to see if the issue reappears and report back.
So further update.
It appears that the outages I was experiencing were nothing to do with pfsense at all.
My Virgin Media ISP in the UK had a UK wide intermittent outage that has been affecting customers for the past 48 hours.
Please ignore my post above. TLS DNS is working just fine for me on 23.01
-
-
@n8rfe said in Major DNS Bug 23.01 with Quad9 on SSL:
Please ignore my post above. TLS DNS is working just fine for me on 23.01

I'm pretty sure that even @nononono will post back in the future here with a "solved" statement.
The initial subject of the thread "Major DNS Bug 23.01 with Quad9 on SSL " boils down to .... nothing.
-
@gertjan said in Major DNS Bug 23.01 with Quad9 on SSL:
@n8rfe said in Major DNS Bug 23.01 with Quad9 on SSL:
Please ignore my post above. TLS DNS is working just fine for me on 23.01

I'm pretty sure that even @nononono will post back in the future here with a "solved" statement.
The initial subject of the thread "Major DNS Bug 23.01 with Quad9 on SSL " boils down to .... nothing.
I don't think I'd go as far as saying it's nothing. I see people having issues here, Reddit, Twitter. Settings that work in 22 don't work in 23. The defaults with forwarding don't work. With 22 you could turn on forwarding and turn on TLS and it worked. Now not so much. We have done several dozen 22 to 23 updates for customers now with different ISPs and different setups and every time we end up having to sort out DNS issues.
I think the biggest issue is we have a few customers that need to have DHCP entries included in DNS. It worked fine with 22. With 23 the restarts eventually either crash unbound entirely or it just stops responding to DNS for periods of time. We have had to setup a separate DNS server for these customers.
-
@cylosoft said in Major DNS Bug 23.01 with Quad9 on SSL:
I think the biggest issue is we have a few customers that need to have DHCP entries included in DNS. It worked fine with 22. With 23 the restarts eventually either crash unbound entirely or it just stops responding to DNS for periods of time. We have had to setup a separate DNS server for these customers.
Sorry but it's documented for far longer then 22.x that DHCP registration with unbound is a "avoid!" situation due to it restarting every time a dhcp client registers its name. Either use dnsmasq (the forwarder) or don't use DHCP registration. That is literally written in the docs for far longer then "it came up with 23.01": https://docs.netgate.com/pfsense/en/latest/services/dns/resolver-config.html
Besides, a fully dynamic DHCP address shouldn't ever be needed as a name at all. A client doesn't need to have dns resolution of its name. And if it does need it because it runs services under a FQDN/hostname, it should have a static/DHCP-set static IP so it won't accidentally change and thus would have a dns name, that can be read at runtime by unbound by the "static DHCP" option which is fine and doesn't cause problems. -
@jegr said in Major DNS Bug 23.01 with Quad9 on SSL:
@cylosoft said in Major DNS Bug 23.01 with Quad9 on SSL:
I think the biggest issue is we have a few customers that need to have DHCP entries included in DNS. It worked fine with 22. With 23 the restarts eventually either crash unbound entirely or it just stops responding to DNS for periods of time. We have had to setup a separate DNS server for these customers.
Sorry but it's documented for far longer then 22.x that DHCP registration with unbound is a "avoid!" situation due to it restarting every time a dhcp client registers its name. Either use dnsmasq (the forwarder) or don't use DHCP registration. That is literally written in the docs for far longer then "it came up with 23.01": https://docs.netgate.com/pfsense/en/latest/services/dns/resolver-config.html
Regardless of that. It works with 22. It doesn't with 23. So to our customers 23 doesn't work.
-
@cylosoft said in Major DNS Bug 23.01 with Quad9 on SSL:
I see people having issues here, Reddit, Twitter.
Sure.
For me, issues can be found here : Issues exist as those can be reproduced.@cylosoft said in Major DNS Bug 23.01 with Quad9 on SSL:
Settings that work in 22 don't work in 23
What settings ?
@cylosoft said in Major DNS Bug 23.01 with Quad9 on SSL:
The defaults with forwarding don't work. With 22 you could turn on forwarding and turn on TLS and it worked.
So this (last change July 2022) DNS Forwarder Configuration or the TLS equivalent Configuring DNS over TLS or How to Enable DNS over TLS on pfSense with Cloudflare are not correct ?
They looks ok to me, I've used that page to set up forwarding to 1.1.1.1 and the IPv6 equivalent, with the cert host names.
https://1.1.1.1/help confirmed me all was ok - I was forwarding.I'm pretty sure my ISP isn't DNS bugging on me.
My pfSense can create enough entropy (see above) so my pfSense can start many (like a lot) TCP connections over TLS but I found out ones what happens with a web server (and mail etc) if entropy isn't available any more. TLS goes down fast....
Maybe this entropy thing is a non issue. I don't know.@cylosoft said in Major DNS Bug 23.01 with Quad9 on SSL:
that need to have DHCP entries included in DNS.
That one is known for years now.
Fast solution : DHCP Mac static lease.Next best :
@cmcdonald said in Major DNS Bug 23.01 with Quad9 on SSL:
I'm hopeful it will make it in 23.05.
@cylosoft said in Major DNS Bug 23.01 with Quad9 on SSL:
Reddit, Twitter.
No, thanks.
I'm not a #metoo guy. I prefer the #menot.
I don't like issues for myself, neither for others.
If I find one, I'll try to find out the 'why' part'.Btw : I was posting in the scope of this thread

So we all know what our choices are asap.
-
@cylosoft We have clients that use the option just fine. So is it a 23.01 problem or a "your configuration/setup" problem?
Besides - that isn't the context of this thread where it's about a forwarding DNS problem that seems to disappear when I read those responses and seems more related to problems of Quad9.But if that's the biggest problem you see, I'd say let's open a separate thread for the DHCP-register / crash problem. Last time I looked at those reports here, most cases where related to pfBlocker+Unbound in combination though. You're running pfB in those configs, too? Just trying to analyze the context/root of the problem :)
Cheers
-
@jegr said in Major DNS Bug 23.01 with Quad9 on SSL:
@cylosoft We have clients that use the option just fine. So is it a 23.01 problem or a "your configuration/setup" problem?
Besides - that isn't the context of this thread where it's about a forwarding DNS problem that seems to disappear when I read those responses and seems more related to problems of Quad9.But if that's the biggest problem you see, I'd say let's open a separate thread for the DHCP-register / crash problem. Last time I looked at those reports here, most cases where related to pfBlocker+Unbound in combination though. You're running pfB in those configs, too? Just trying to analyze the context/root of the problem :)
Cheers
Yeah I've gone down this road. I understand all the context. I've been on a bunch of these threads posting including this one. We have "fixed" all of our customer configurations except the DHCP. I think the main issue is that the defaults don't work with forwarding and TLS. So generally speaking everyone with forwarding likely has a similar config and now is going down slightly different variations trying to find stable.
We had a lot of customers with Quad9, TLS, forwarding. As in 24+ customers when we paused the v23 upgrades. We thought it was Quad9 originally. But switching to CF DNS didn't fix it. We also have some customers running Quad9 with TLS on a stand alone DNS server taking most of the DNS traffic and the PF box doing Quad9 with TLS. The PF box will stop and the stand alone DNS box has no issues while using the same IP, and literally traffic going out through the PF box.
Turning off forwarding or disable TLS with forwarding seems to be a fix. But for those that want forwarding and TLS we have had to disable DNSSEC, enable serve expired, and increase the message cache size. We had several customers where unbound would completely crash about once a week up until we increased message cache size.
-
Hmm, something odd there. I use DoT forwarding to Google DNS on my own firewall and I've not seen any issues.
