[Solved] Please help with switch/vlan (802.1q) setup on Netgate 2100
-
@stephenw10 said in Please help with switch/vlan (802.1q) setup on Netgate 2100:
Ok the first thing to do is simply change it to dot1q mode. That should put all the ports untagged in VLAN1. It should behave exactly the same as port mode.
The untagged interface, LAN, will become the mgmt network.
Anything else will need to be added as VLANs with the appropriate firewall rules etc.
Steve
Hi Steve,
I am so frustrated right now and thankful you have responded! This is my only route to the internet, so while trying my best, all I am left with is a phone with no access to this forum...
I have been at it non-stop, trying just about everything but the correct connection I would think at this point.
I did as you suggest, switch to 802.1q. Then added my vlans (strange as they already are defined) to the switch config. I found a post on Lawrence Systems forum who also had issues like me and found out that adding all the already defined vlans to the switch worked for him. No such luck for me though... My biggest issue was/is that when it came to adoption of the Unifi switches, they either did not show at all, or refused to adopt. This, as far as I know, indicates they aren't on the same network, and really is my main concern, since I have a really bad time getting how to actually configure the built-in switch...I tried with a basic "4084" form the Netgate example, (for the fourth port); "4;5t", which to me would sound like "native lan untagged, all else tagged". This cannot be though, since what I gained best result with was "1t;4;5t", which really confuses me. That way I cold see the switches, but as "offline".
I am somewhat curious to why Netgate haven't mapped this in some nicely done wrapper, not making us users suffer so much... (or it might just be me having a trip on this one...) This chip is arguably very hard to grasp, and I'm sad to admit, I obviously can't... :( So I'm begging nicely, I have tried, a lot, and almost made it I think on a good day, but still always failed somehow... What would I need to make this work?
I have the Netgate 2100, a laptop with a temporary Unifi controller installed, in the same network. In 802.1q mode I cannot seem to make things work, no matter the rules added. I always (so far) have had to switch back to "port mode" to make it work...
I am very proud to run pfSense, but this one I simply do not grasp...
I know I can't expect a full solution here, and yes, I do want to learn and evolve, but please give me something more than I already have figured our myself so far...
Long post, sorry, but feeling a little stressed by this.
Thanks
-
Ok, first let's define what exactly you are trying to achieve here?
Also confirm that when you switch from port to dot1q everything worked as it had before?
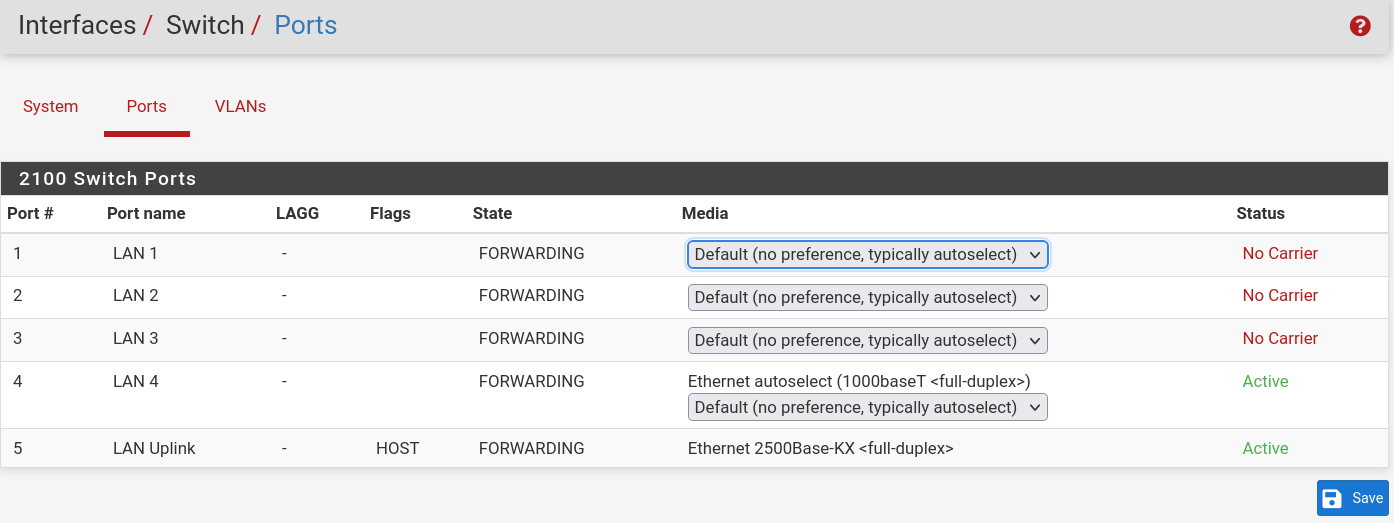
The switch should look like this when you do that:
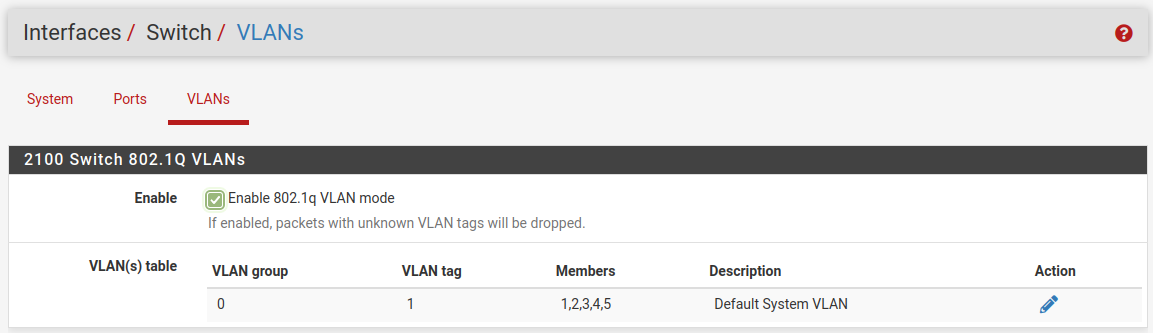
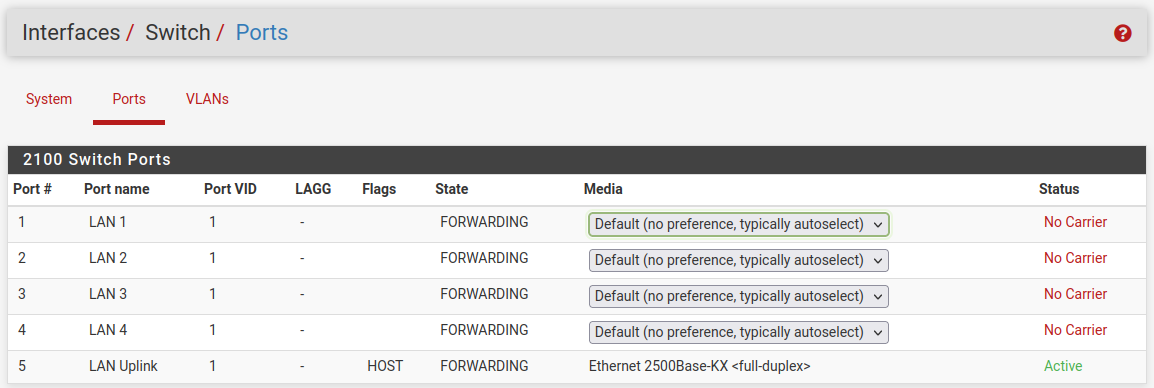
At that point there is only one VLAN and it's untagged on every port so it behaves just like an unmanaged switch.
-
 S stephenw10 moved this topic from General pfSense Questions on
S stephenw10 moved this topic from General pfSense Questions on
-
@stephenw10 said in Please help with switch/vlan (802.1q) setup on Netgate 2100:
Ok, first let's define what exactly you are trying to achieve here?
I have been trying to enable 802.1q mode in order to better control my network, and also assign tags to devices that uses it. I hade this working with the previous much simpler fw/router which sent out these tags by default.
As is, I have pfSense, switches and their controller on VLAN 1. I know it's somewhat "bad practice" but read that one of the main reasons for having a management lan were insecure protocols in the past - not so much needed these days, would you agree?
Also confirm that when you switch from port to dot1q everything worked as it had before?
The switch should look like this when you do that:


At that point there is only one VLAN and it's untagged on every port so it behaves just like an unmanaged switch.
Well, for me it does not exactly work as before after switching... When I switch mode, I can only access pfSense from it's own built-in ports, but this may be expected? But yes, it looks like the screenshots. So far so good I suppose.
Then we come to the tricky part...
I have (before) tried to create a new VLAN-tag, say 4084 with members port 4 (untagged) and port 5 (tagged), and then under "Ports" assigned that to port 4. That would then be a "Discrete Port", right?
-
@furom Assuming you have removed all other VLANs from port 4, and given it the PVID as well (when you go 802.1Q mode PVID is now set on the ports page) you should be set.
My switch on the 7100:
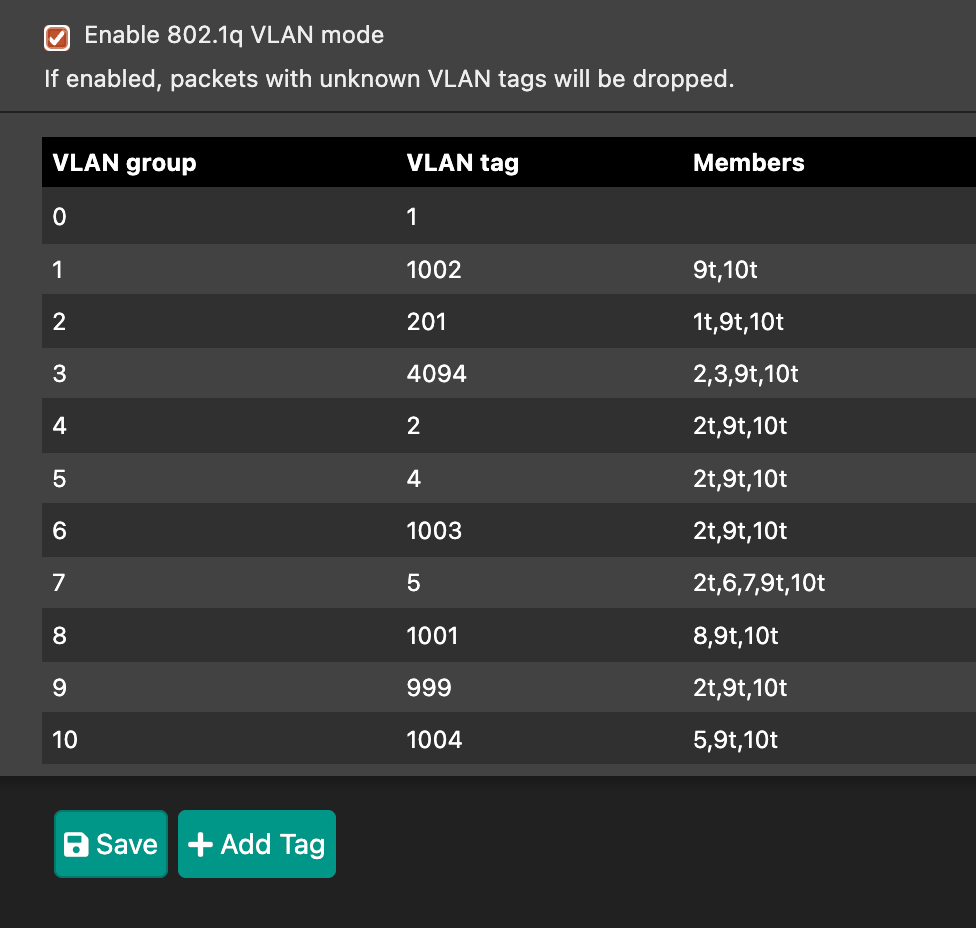
And the ports tab:
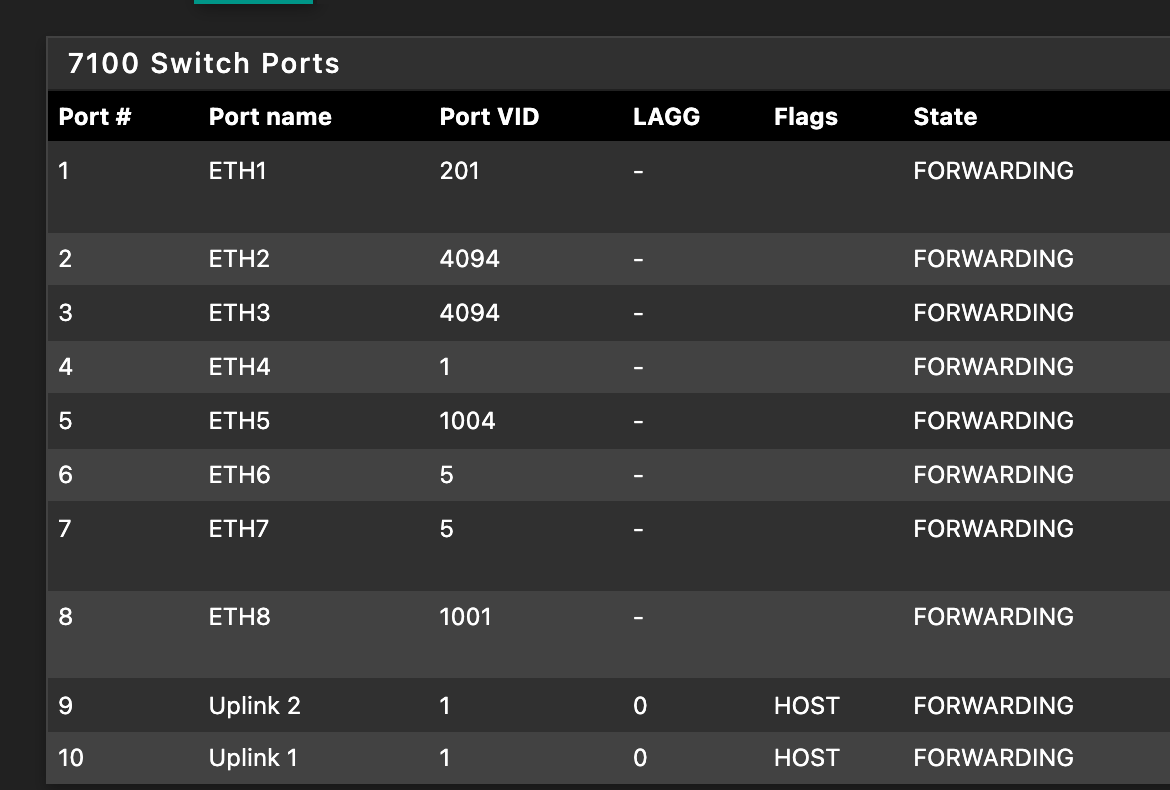
The 2100 is similar but not 100% identical. You don't have ports 5-8 on the switch or 9/10 for your lagg, but you have 1-4 and 5 is your uplink into pfSense.
-
@rcoleman-netgate said in Please help with switch/vlan (802.1q) setup on Netgate 2100:
@furom Assuming you have removed all other VLANs from port 4, and given it the PVID as well (when you go 802.1Q mode PVID is now set on the ports page) you should be set.
Hm. So, as I have switches and controller (+pfSense) on the native VLAN, should it work if I define a VLAN-tag as 4084 for example, with members (4,5t) and then connect it to the 2100 Switch port 4?
Should I then be able to
- on 2100 port 1: connect Unifi controller (VLAN 1)
- and find my switches in "online" state? - on 2100 port 4: connect a Unifi switch that will now
- get an IP from VLAN 1, and have access to all other defined VLAN tags?
- which then should mean that the switch config I already have, would just work?
It feels like I have bee trying this over and over and always missed something vital. Will I need any additional rules for this to work in it's most basic form, meaning continue to add rules and configuration?
Thanks
- on 2100 port 1: connect Unifi controller (VLAN 1)
-
Importantly you need to set the PVID on port 4 to 4084 on the Ports tab. Otherwise you are untagging traffic leaving port 4 but not tagging the reply traffic coming into port 4.
@furom said in Please help with switch/vlan (802.1q) setup on Netgate 2100:
on 2100 port 1: connect Unifi controller (VLAN 1)
- and find my switches in "online" state?
Yes, as long as those switches are also on VLAN 1.
Also important to note that VLAN1 only actually exists inside the switch. It's actually untagged traffic everywhere else.@furom said in Please help with switch/vlan (802.1q) setup on Netgate 2100:
on 2100 port 4: connect a Unifi switch that will now
- get an IP from VLAN 1, and have access to all other defined VLAN tags?
- which then should mean that the switch config I already have, would just work?
If you have setup VLAN 4084 as shown in the doc then a switch on port will only have access to VLAN 4084 and not VLAN1. So no it won't get an IP from VLAN1. And no it won't have access to any tagged vlan.
If that's what you want you would need to leave port 4 as an untagged member of VLAN1. Leave the PVID on port 4 as 1. And set port 4 as a _tagged_member of VLAN 4084, and any other VLANs you need at the switch.If you post some screenshots of you setup I'm sure we will be able to see what's happening.
-
@stephenw10 said in Please help with switch/vlan (802.1q) setup on Netgate 2100:
Importantly you need to set the PVID on port 4 to 4084 on the Ports tab. Otherwise you are untagging traffic leaving port 4 but not tagging the reply traffic coming into port 4.
@furom said in Please help with switch/vlan (802.1q) setup on Netgate 2100:
on 2100 port 1: connect Unifi controller (VLAN 1)
- and find my switches in "online" state?
Yes, as long as those switches are also on VLAN 1.
Also important to note that VLAN1 only actually exists inside the switch. It's actually untagged traffic everywhere else.@furom said in Please help with switch/vlan (802.1q) setup on Netgate 2100:
on 2100 port 4: connect a Unifi switch that will now
- get an IP from VLAN 1, and have access to all other defined VLAN tags?
- which then should mean that the switch config I already have, would just work?
If you have setup VLAN 4084 as shown in the doc then a switch on port will only have access to VLAN 4084 and not VLAN1. So no it won't get an IP from VLAN1. And no it won't have access to any tagged vlan.
If that's what you want you would need to leave port 4 as an untagged member of VLAN1. Leave the PVID on port 4 as 1. And set port 4 as a _tagged_member of VLAN 4084, and any other VLANs you need at the switch.If you post some screenshots of you setup I'm sure we will be able to see what's happening.
Thank you, this is good. I will shortly start testing again an will manage some screenshots to I hope! :)
-
Well, thanks to you guys I'm getting closer! I'm back up and running again with 802.1q, but I still don't see any vlans using tcpdump;
tcpdump -i enp3s0 -eI did see them at one point, but was then connected before the switch... and nothing else worked. :)
I have come up with this so far;
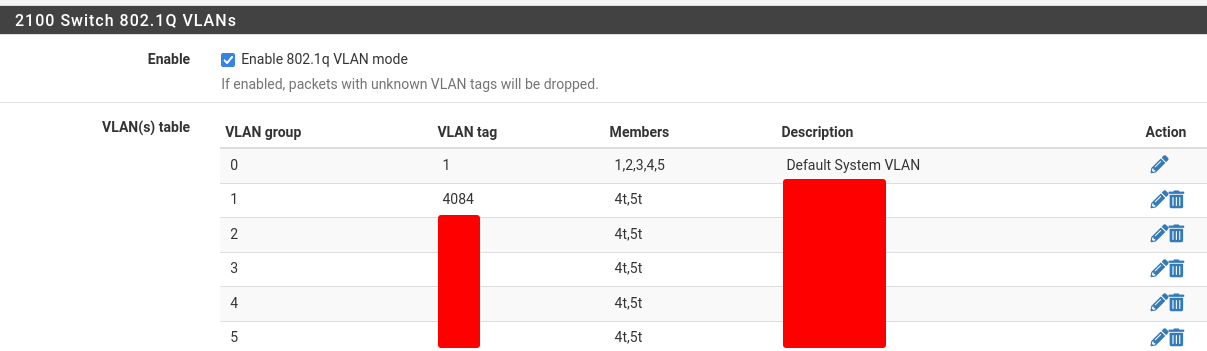
Some more questions;
- Where does the 4084 comes into play as it is just defined but not used? Do I even need it as is?
- Why do I need to have vlan config both here and in Interfaces/VLANs. Guessing this was just a mapping of sorts?
- What would I need to do to pass the vlan tag to an application for example? As is now, are they really broadcasted if I cannot see them?
- Also... As I will be running the Unifi controller in a VM, which will need VLAN 1... I remember you said it only lives within the switch... So I guess I actually really need a management vlan after all... Why isn't VLAN 1 possible to send out as tagged?
Thanks
-
@furom said in Please help with switch/vlan (802.1q) setup on Netgate 2100:
Some more questions;
- Where does the 4084 comes into play as it is just defined but not used? Do I even need it as is?
That depends on you. Why do you even have a vlan 4084 if you aren't gonna use it?
- Why do I need to have vlan config both here and in Interfaces/VLANs. Guessing this was just a mapping of sorts?
Where you are showing is the switch config. Interfaces/vlans is the router config.
- What would I need to do to pass the vlan tag to an application for example? As is now, are they really broadcasted if I cannot see them?
Applications don't use vlans. If you want to use 4084 as a separate network, all you have to do is tag 4084 on the unifi switchport that is plugged into port 4 of the router, then untag 4084 on another unifi port. If you plug into the "other" port, you will be on the vlan 4084 network.
- Also... As I will be running the Unifi controller in a VM, which will need VLAN 1... I remember you said it only lives within the switch... So I guess I actually really need a management vlan after all... Why isn't VLAN 1 possible to send out as tagged?
Thanks
The controller doesn't need to use vlan1. Mine uses vlan 160. -
@furom said in Please help with switch/vlan (802.1q) setup on Netgate 2100:
Where does the 4084 comes into play as it is just defined but not used? Do I even need it as is?
Nowhere? if you aren't using it I would just not enable it - thus taking some system load off your 2100.
Why do I need to have vlan config both here and in Interfaces/VLANs. Guessing this was just a mapping of sorts?
One is the switch, the other is pfSense. The 2100 cannot talk to the switch with VLANs unless they're associated on the switch as well.
What would I need to do to pass the vlan tag to an application for example? As is now, are they really broadcasted if I cannot see them?
Application layer is on top of the network layer in the OSI model. Your question doesn't have an answer.
Also... As I will be running the Unifi controller in a VM, which will need VLAN 1... I remember you said it only lives within the switch... So I guess I actually really need a management vlan after all... Why isn't VLAN 1 possible to send out as tagged?
VLAN1 is typically untagged on your network. Not the best idea moving forward to rely on that VLAN except that for the sake of the switch built into the 2100 this is the best situation as the idea is that all ports on the LAN will work out of the box.
-
Thanks guys,
I removed the redundant 4084, but I am still wondering.. I need my hypervisor to see the vlan tags to assign correct networks to the VM's. I'm just asking so I know if there is any point in even trying - I did not see any tags with tcpdump, so my guess is they aren't available with this config? What will I need to do for that to work? -
Where are you running that tcpdump? How is it connected?
As you have configured any traffic on those VLAN will leave port 4 tagged. So if you have the hypervisor connected to port 4 it will see them. If there's another switch in between that will need to pass those VLANs tagged.
It's important to realise than packet tagged with VLAN 1 is not the same as untagged packets. Those two are often conflated and both shown as 'VLAN1'. So, yes, you could pass out VLAN1 packets tagged but it's almost certainly not what you want to do!
https://docs.netgate.com/pfsense/en/latest/vlan/security.html#using-the-default-vlan-1Steve
-
@stephenw10 said in Please help with switch/vlan (802.1q) setup on Netgate 2100:
Where are you running that tcpdump? How is it connected?
As you have configured any traffic on those VLAN will leave port 4 tagged. So if you have the hypervisor connected to port 4 it will see them. If there's another switch in between that will need to pass those VLANs tagged.
It's important to realise than packet tagged with VLAN 1 is not the same as untagged packets. Those two are often conflated and both shown as 'VLAN1'. So, yes, you could pass out VLAN1 packets tagged but it's almost certainly not what you want to do!
https://docs.netgate.com/pfsense/en/latest/vlan/security.html#using-the-default-vlan-1Steve
Perfect! Then I'll add some to the switch to enable port 3 as well for the hypervisor with the vlans I need :) I will also take a moment to document what I have learned and configured.
Thank you so much for great help!
-
@furom I still have much to configure, but one thing I notice is it became a LOT snappier!! So happy, would there be any reason for that or is it just more efficient to run vlans in 802.1q mode?
-
This post is deleted! -
Hmm, nothing specific I can think of. Not for normal use. Possibly you had something it was trying to query it couldn't access that now it can. Things on the dashboard can cause delays if they can't access resources.
-
@stephenw10 said in [Solved] Please help with switch/vlan (802.1q) setup on Netgate 2100:
Hmm, nothing specific I can think of. Not for normal use. Possibly you had something it was trying to query it couldn't access that now it can. Things on the dashboard can cause delays if they can't access resources.
Well, I must have had that from the beginning, it is blazing fast in comparison... But must be as you suggest, some miss-configuration. I will pay close attention when enabling all I had before where/if it slows it down much.
Thanks :)
-
@furom said in [Solved] Please help with switch/vlan (802.1q) setup on Netgate 2100:
it is blazing fast
Nice.