pfSense+ DNS slow (10+ms)
-
Good Afternoon!
So I recently finally got the chance to buy a pfSense+ box after many years of using pfSense on a BYOD box and... its been something... Been having a ton of issues, but for this post, is anyone aware if there are specific DNS resolution performance issues with pfSense plus or with the Netgate 1537? I have tried both copying the configuration from my old pfSense BYOD box, and following the pfSense resolver configuration to the letter with no success.
Cached results load in sub 1ms, however regardless of what external DNS server I use uncached domains are 10ms+ latency which is HORRIBLE. I have tried a dozen DNS servers, and if I bypass my firewall and use the DNS servers directly I get 2-3MS resolutions (I live near a google datacenter)
-
@surroundtortilla said in pfSense+ DNS slow (10+ms):
I use uncached domains are 10ms+ latency which is HORRIBLE.
Really 10ms is horrible? Where did you come up with that metric?
The closest googledns is 30 ms away for me.. so kind of impossible to get back something from them in 10ms even if they had it cached, etc.
-
@surroundtortilla Google presumably has most domains cached. You can set unbound to forward there if you want. Otherwise it connects to the root servers then individual DNS servers for each domain.
-
@johnpoz said in pfSense+ DNS slow (10+ms):
The closest googledns is 30 ms away for me.. so kind of impossible to get back something from them in 10ms even if they had it cached, etc.
I presume you didn't read the entire post? As explained, if I bypass the firewall and use the same server its a 2-3MS delay, which is a 3-4x delay... Its individual timing is pretty good; however, when it adds a factor of delay that high, it certainly gives me cause for concern.
-
@surroundtortilla and your sure your using the same server you talked to before - changing IPs can alter routing, can alter geo info, google dns is anycast.. So you might have gotten answer from box A, and then getting answer from box B.
So when you bypass psfense, your using the same IP that pfsense uses?
10ms query time is not horrible.. You think tha less than 10ms difference is going to slow down your browsing?
So are you forwarding in pfsense, are you using dot? Are you asking for dnssec while forwarding - which is not something you would do when forwarding, etc.
Out of the box unbound is a resolver, so it wouldn't even be asking googledns..
I never understand why people care if it takes 10ms or 100ms to resolve something or get an answer from a forwarder - that is one time thing.. All other queries for the life of ttl is locally cached, not only at unbound, but also your OS, and your browser etc..
10ms is not something to worry about when it comes to dns.
-
@johnpoz said in pfSense+ DNS slow (10+ms):
it
I will agree with you, 10MS is still a fantastic experience; but it's just really confusing that the box averaging 1% load, is adding a 6-7ms latency to resolve something is odd, especially when my last box added 1-2ms, and was a $300 mini box from 5-6 years ago.
DNS is disabled per pfSense best practices I am not currently using DNS over TLS, but is in my eventual plan. DNS is configured as a forwarder to Google DNS atm.
-
@surroundtortilla Was your prior router forwarding, or resolving directly?
-
@surroundtortilla said in pfSense+ DNS slow (10+ms):
DNS is configured as a forwarder to Google DNS atm.
If I forward to googledns... I don't see 10 added to my query, directed I get
;; ANSWER SECTION: www.google.com. 250 IN A 142.250.191.100 ;; Query time: 14 msec ;; SERVER: 8.8.8.8#53(8.8.8.8) ;; WHEN: Mon May 01 21:30:04 Central Daylight Time 2023If I setup unbound to just forward to 8.8.8.8 and turn off dnssec I get this. This is right after a flush..
;; ANSWER SECTION: www.google.com. 3600 IN A 142.250.191.100 ;; Query time: 15 msec ;; SERVER: 192.168.9.253#53(192.168.9.253) ;; WHEN: Mon May 01 21:32:35 Central Daylight Time 2023 ;; MSG SIZE rcvd: 59Doing a bunch of queries direct to 8.8.8.8 I seem get between 11 and 21ms
;; ANSWER SECTION: www.google.com. 182 IN A 142.250.191.100 ;; Query time: 21 msec ;; SERVER: 8.8.8.8#53(8.8.8.8) ;; WHEN: Mon May 01 21:34:04 Central Daylight Time 2023 ;; MSG SIZE rcvd: 59I wouldn't worry about 10ms or even for that matter 100.. 10 ms is 0.01 of a second.
you see the 3600 ttl on my query to unbound, because I have min ttl set to 3600..
maybe your unbound is way busier than you think it is - maybe you have some box pounding asking the same thing over and over again?
I had some issues with my internet the other day (cable cut) - and when devices can not resolve either because your blocking or not working, some of these iot devices can just hammer dns..
2023-04-29 09:38:51 RATE_LIMIT Client 192.168.7.3 has been rate-limited (current config allows up to 1000 queries in 60 seconds) 2023-04-29 14:06:25 RATE_LIMIT Client 192.168.4.80 has been rate-limited (current config allows up to 1000 queries in 60 seconds) 2023-04-29 14:40:29 RATE_LIMIT Client 192.168.4.77 has been rate-limited (current config allows up to 1000 queries in 60 seconds) 2023-04-29 15:22:20 RATE_LIMIT Client 192.168.4.79 has been rate-limited (current config allows up to 1000 queries in 60 seconds) 2023-04-29 17:20:24 RATE_LIMIT Client 192.168.4.76 has been rate-limited (current config allows up to 1000 queries in 60 seconds)My alexa's were going crazy when my internet was down asking for dns..
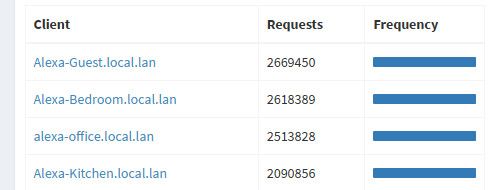
That is the number of their queries in 24 hour period - little bastards!! ;)