Problem configuration OpenVPN
-
@kilian77
So your OpenVPN server is listening on the WAN, but your client tries to connect to the LAN address.If you want to do it this way, add a NAT port forwarding rule to the Lan interface for the Lan address, UDP 1194.
-
@viragomann
unfortunately that's what I already did
-
@kilian77
Hard to say if this is a proper NAT rule. If you want to hide things you should replace them with place holders to keep it readable.Anyway, OPENVPN is the wrong interface to do this.
-
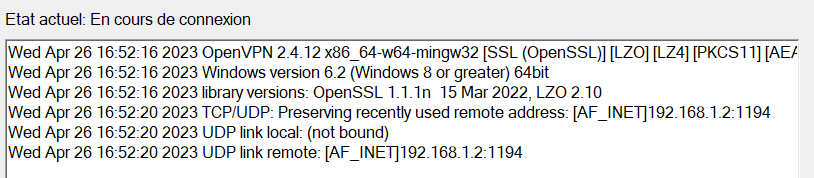
@viragomann what I sent is the nat rule of my wifi modem, I open port 1194 from the outside which comes to type on the LAN port in 192.168.1.2 and I do not understand why I always have the error of my client who says "UDP link local (not bound)
-
@kilian77 Has anyone had this error and solved it please?
-
@kilian77 said in Problem configuration OpenVPN:
Has anyone had this error and solved it please?
Take a look here : Configuring OpenVPN Remote Access in pfSense Software : follow it step by step and you have a working solution.
You use an upstream 'ISP' router.
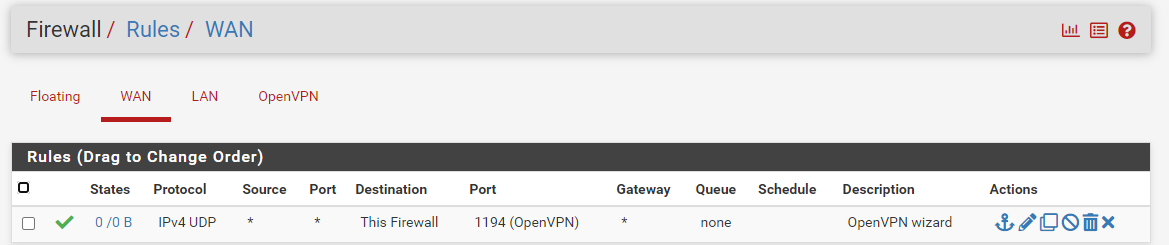
Its needs to have port "UDP 1194" to be NATted to the WAN IP of pfSense.You can easily check if traffic reaches your pfSense WAN 1194 UDP port :
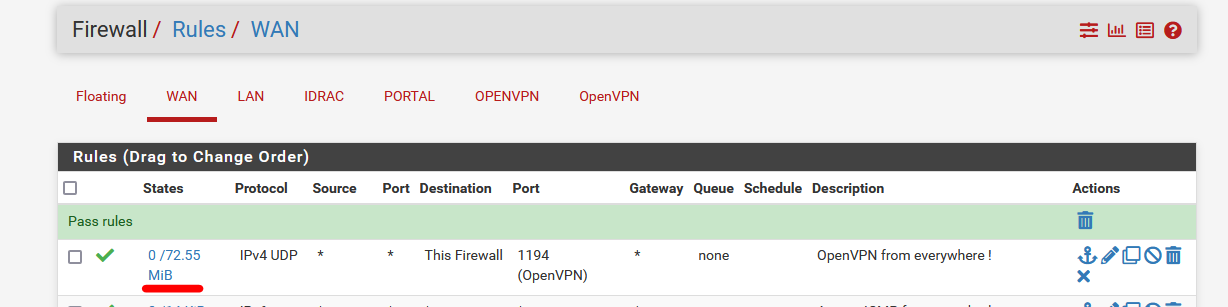
You see the state and traffic counter in front of the rule ?
If these go up, then you upstream ISP NAT rule works fine.
If they stay zero, then traffic never reaches pfSense. -
This post is deleted! -
@gertjan, first of all thank you for your answer, I re-watched the tutorial you sent me and indeed I did exactly like him by adapting my ip addresses.
WAN=192.168.50.1
LAN=192.168.1.2
VPN TUNNEL = 192.168.80.0
I also NATed the firewall and the traffic goes well but I still have the same error for 2 weeks.
If you need other information to help me do not hesitate I am active. Thanks in advanceNAT FIREWALL :
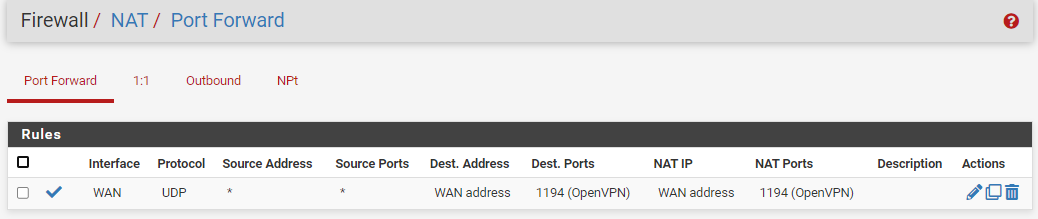
WAN FIREWALL :
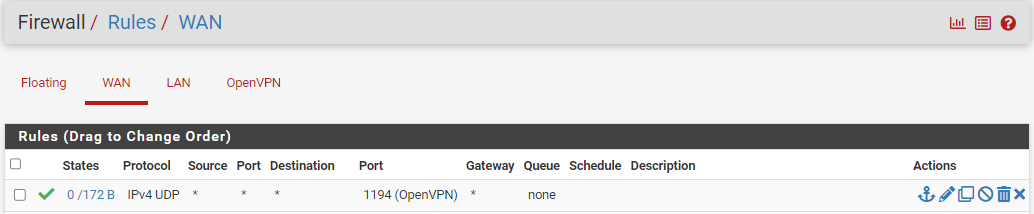
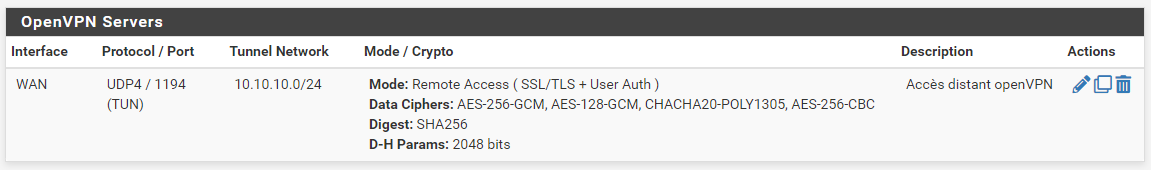
OPENVPN SERVERS :
-
@kilian77 said in Problem configuration OpenVPN:
I also NATed the firewall and the
?
You need a NAT rule for the router that is in front of pfSense (if applicable).
pfSense (see video again) does not need/have a NAT rule.
It only needs a firewall rule on the WAN interface, that permits the UDP port 1194 traffic in.
See the image above.While testing your VPN connection : do not use the local LAN (or Wifi) connection : use your phone with 4G/5G =data carrier, and use the your - real - WAN IP.
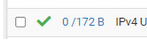
172 bytes ?
I tend to so : no traffic arrives at the pfSense WAN gate. -
@gertjan the problem with my router is that I can only NAT IPs from the 192.168.1.0 network which means that my WAN in 192.168.50.1 I cannot
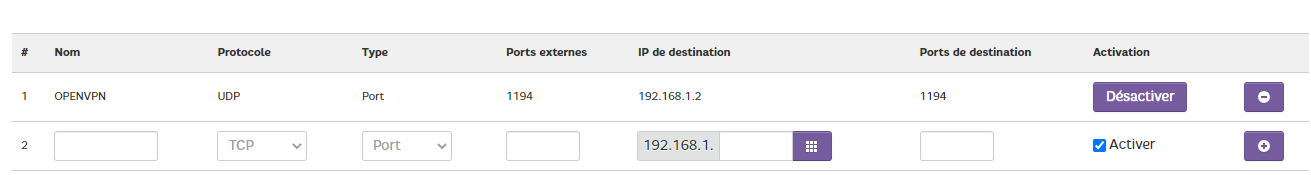
-
@kilian77 said in Problem configuration OpenVPN:
my WAN in 192.168.50.1
@kilian77 said in Problem configuration OpenVPN:
Netgate WAN port: 192.168.1.2/24
@kilian77 said in Problem configuration OpenVPN:
WAN=192.168.50.1
LAN=192.168.1.2What is it ?
How did pfSense obtain this 192.168.50.1/24 ?
Static setup ? DHCP (better) ?What is the IP of the LAN of the upstream router ??
-
@gertjan the 2 ports of the pfsense must not be in the same subnet, so I put my WAN pfsense = 192.168.50.1 and my LAN PFSENSE = 192.168.1.2
My LAN = 192.168.1.1
-
@kilian77 said in Problem configuration OpenVPN:
@gertjan the 2 ports of the pfsense must not be in the same subnet
I know ;)
He didn't know that : this breaks everything :
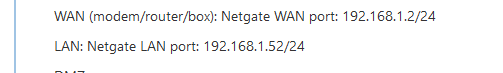
@gertjan said in Problem configuration OpenVPN:
What is the IP of the LAN of the upstream router ??
?
-
@gertjan
I made changes since my last messages here are my addresses: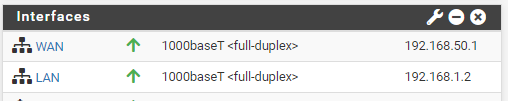
My LAN IP of my router is 192.168.1.1 -
That is as bad as it was before. So nothings works right now, and that's 'normal'.
I'll explain.
You already figured out that when you buy a connected device, like a router, they nearly all have "192.168.1.1/24" as a LAN interface.
This means you can not 'chain' these devices one after and presume it will work.
It won't work.One solution- two methods :
You change the default LAN network of your ISP router from 192.168.1.1/24 to, for example, 192.168.50.1/24 (or 192.168.2.1/24 or something like that). Keep in mind that you change all other related settings, like for example the DHCP server for the LAN interface (if applicable).
Or
You change the default LAN network of your pfSense router from 192.168.1.1/24 to, for example, 192.168.50.1/24 (or 192.168.2.1/24 or something like that). Keep in mind that you change all other related settings, like for example the DHCP server for the LAN interface.
You can keep (I strongly suggest) the default WAN settings : that is : "DHCP" for IPv4 for pfSense. Static IPv4 on for WAN is for experts and ..... well, don't do static, please.
If you can create a MAC based DHCP lease setting on your ISP router for pfSense, then do so.
Because you are natting on your ISP router, you better make sure that pfSense always obtains the same IP.Btw : these 'rules' or 'this knowledge' has nothing to do with your ISP router, or pfSense.
As soon as you you 'chain' one router after another, you have to make sure that they all use a distinct LAN 1RFD1918 network.
Otherwise you will break routing. -
@gertjan I'm sorry I'm a beginner in the matter and there are a few points that I don't understand, why should I modify the LAN address of my ISP router and also modify that of the Pfsense LAN, if they remain in the same network?
Also if I put the WAN address in DHCP it assigns me an address in the same subnet as my router.
Thank you for your answer -
@kilian77 said in Problem configuration OpenVPN:
router and also modify
One
 for you !
for you !I omitted the "Or" word : I'll edit my post above.
-
@kilian77 said in Problem configuration OpenVPN:
I'm a beginner in the matter
We're all born with zero knowledge about all this stuff.
Me, for example, wasn't even able to wipe my own .... well, you get it.I'll show you what I did.
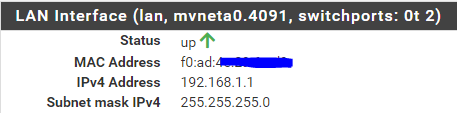
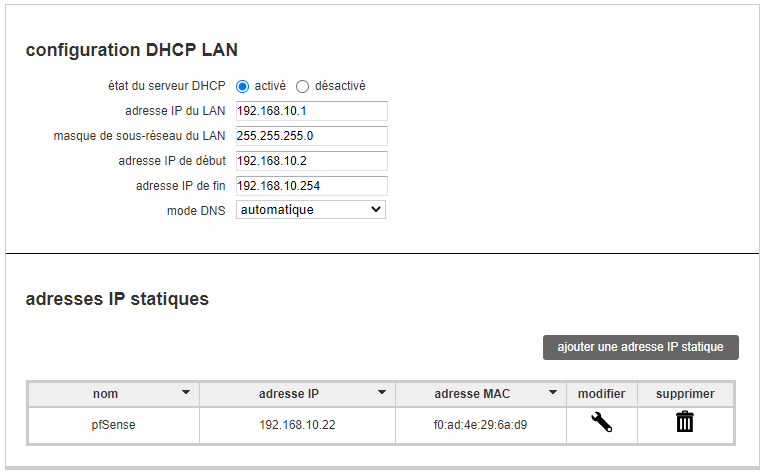
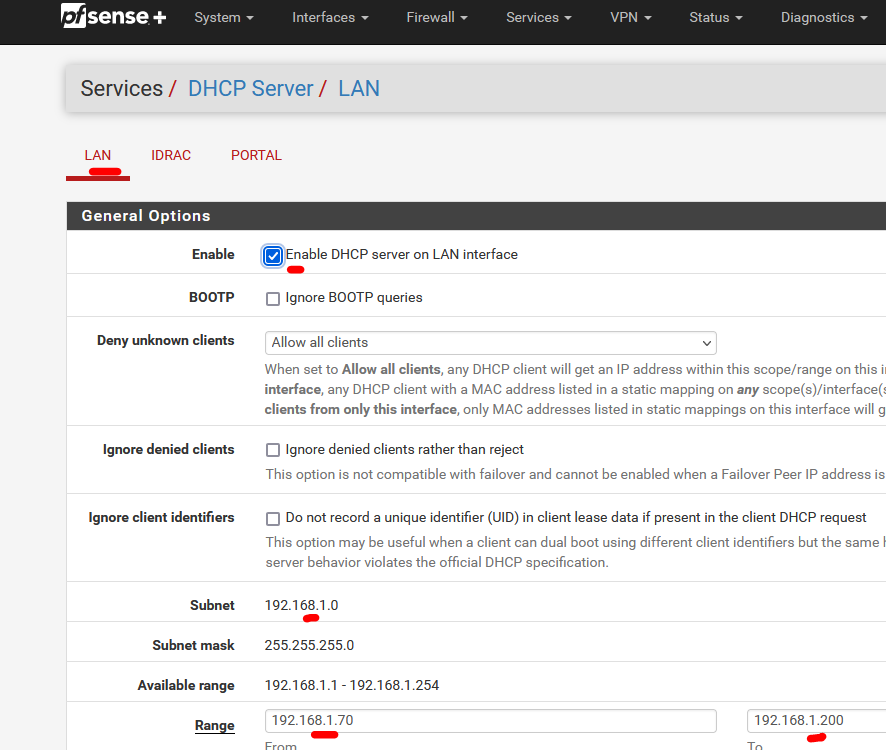
As I have somewhat the same setup as you.My pfSense "LAN" is identical as the one when it came 'out of the box", that is : when you install it :
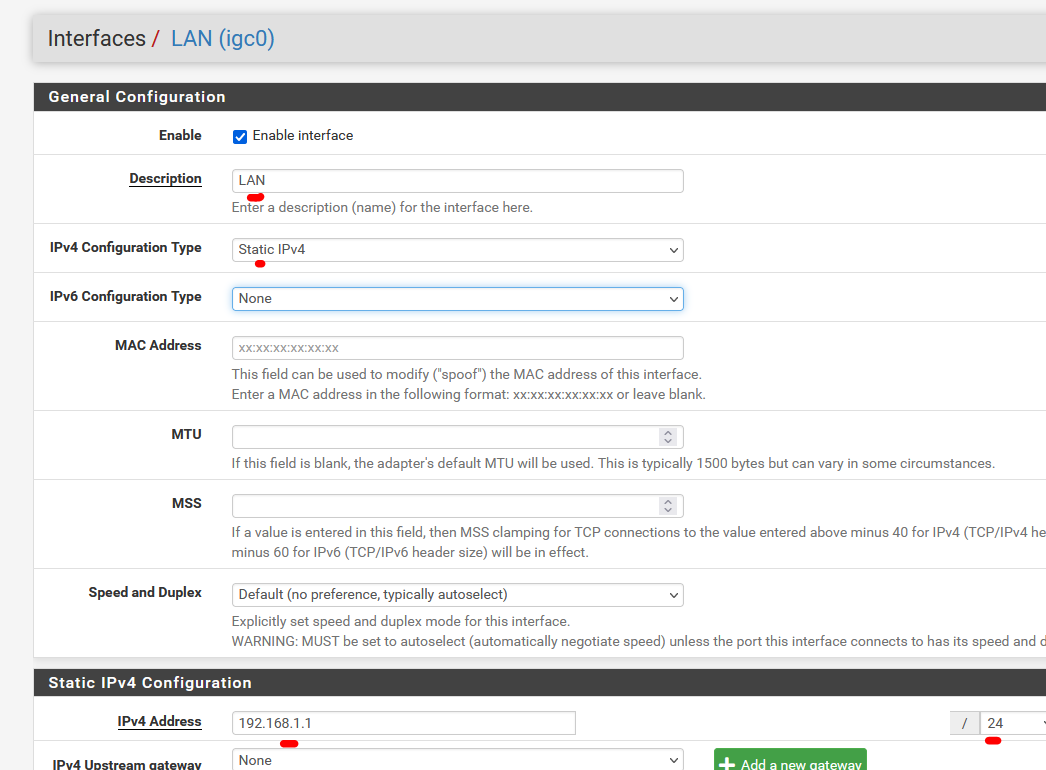
and the DHCP server page shows the same info :
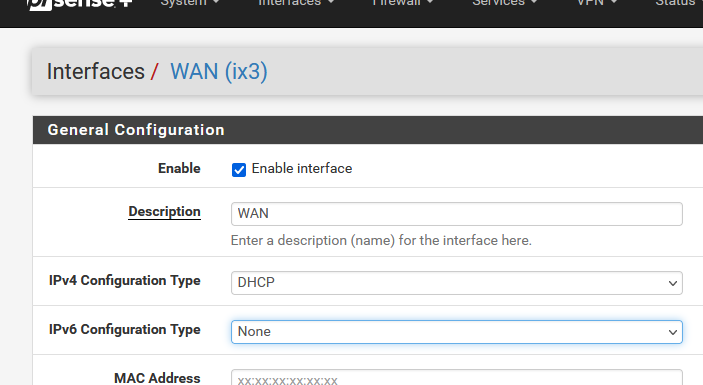
My pfSense WAN network setup is 'default' : I use 'DHCP' :
BUT I had to change my ISP router setup, as it's LAN also comes with 192.168.1.0/24 :
I changed it to 192.168.10.0/24 :
I've set the LAN IP of my ISP router to "192.168.10.1:"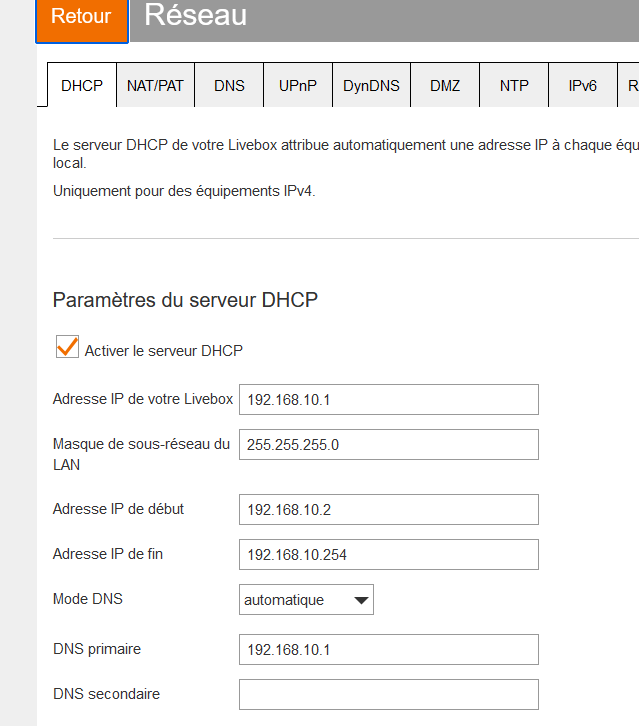
(sorry, the box shows french words, probably becuse I'm in France ;) )
( Livebox is the 'name' of my router - dono why)I made sure that the device (I call it "pfSense") with MAC 90:EC:77:29:39:xx always obtains the IP 192.168.10.4.
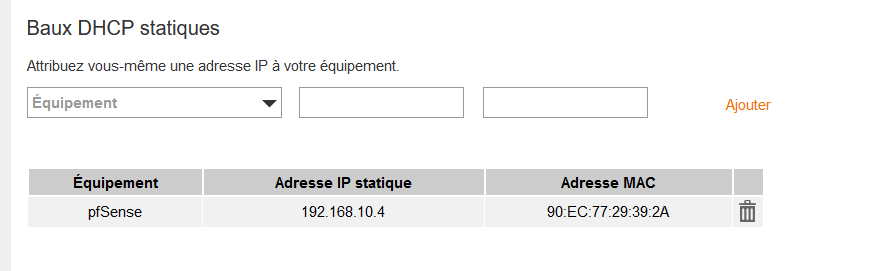
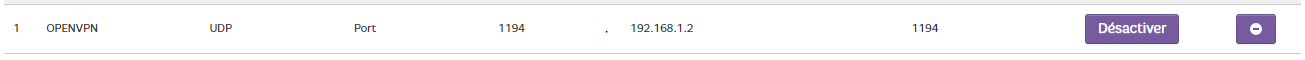
I created a NAT rule in my ISP box, so port 1194 protocol UDP is natted to the device 'pfSense', which is 192.168.10.4
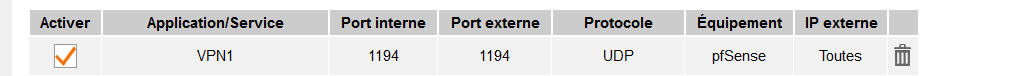
At this moment, when I hit my ISP router's WAN port - which uses my 'Internet' IP on port 1194, with protocol 1194, that traffic will get send to 192.168.10.4:1194.
On the pfSense side, when you use the OpenVPN server create Wizard, the wizard will create a firewall rule (a NAT rule is not applicable / not needed because the endpoint is pfSense itself).
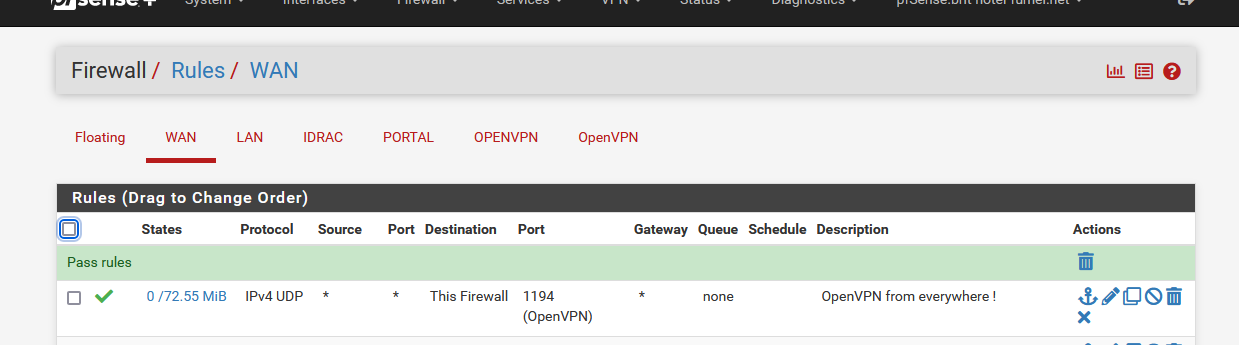
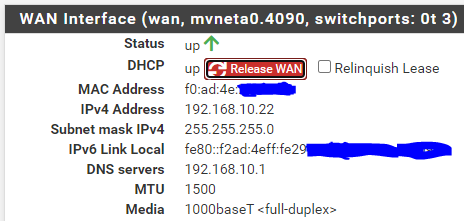
When I connect everything I see this :
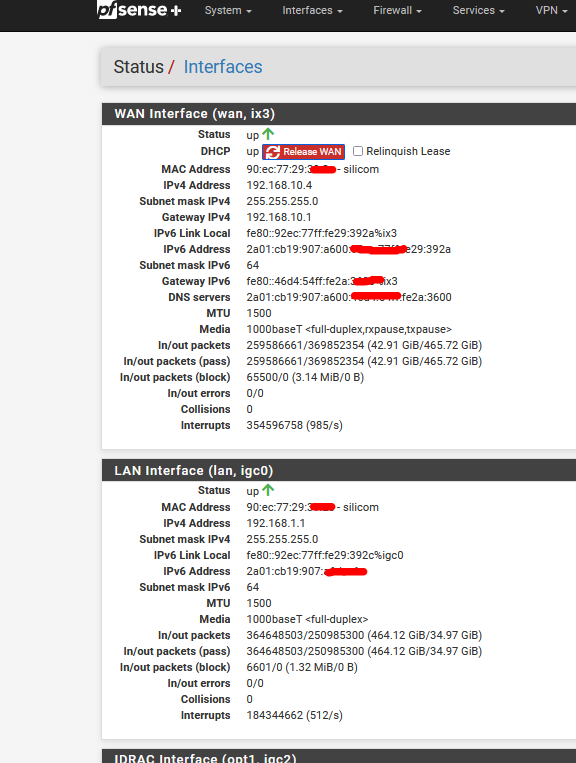
You can see that my ISP router gave 192.168.10.4 to the WAN IP of pfSense.
It will always have this same IP, this is important, as if it got another IP in the 192.168.10.x/24 range, that could break 1194/UDP forwarding == the ISP router's NAT rule.You see also a lot of IPv6 info, as I mostly use IPv6 these days.
IPv6 is a bit like IPv6, packets, ports and stuff, and made easier as IPv4. You need a degree in rocket science to make it work
( just keep it for later) -
@gertjan Thanks for your help,
I'll test tomorrow and I'll come back to you for an update -
@gertjan @gertjan Hello again, I'm coming back to you because I had the opportunity to do some tests again today and it's not better than before.
I reset everything to start on a new configuration to follow what you told me.
I have my LAN at 192.168.1.1 with the same DHCP as you, for the WAN I have
my address in 192.168.10.22 assigned in DHCP by my box and I changed the LAN network of my router to 192.168.10.1I also created a static DHCP address for the pfsense and a nat rule for
the UDP protocol.
I re-created a CA and a certificate as well as a VPN server and a user but I still have the same error which is starting to drive me crazy.