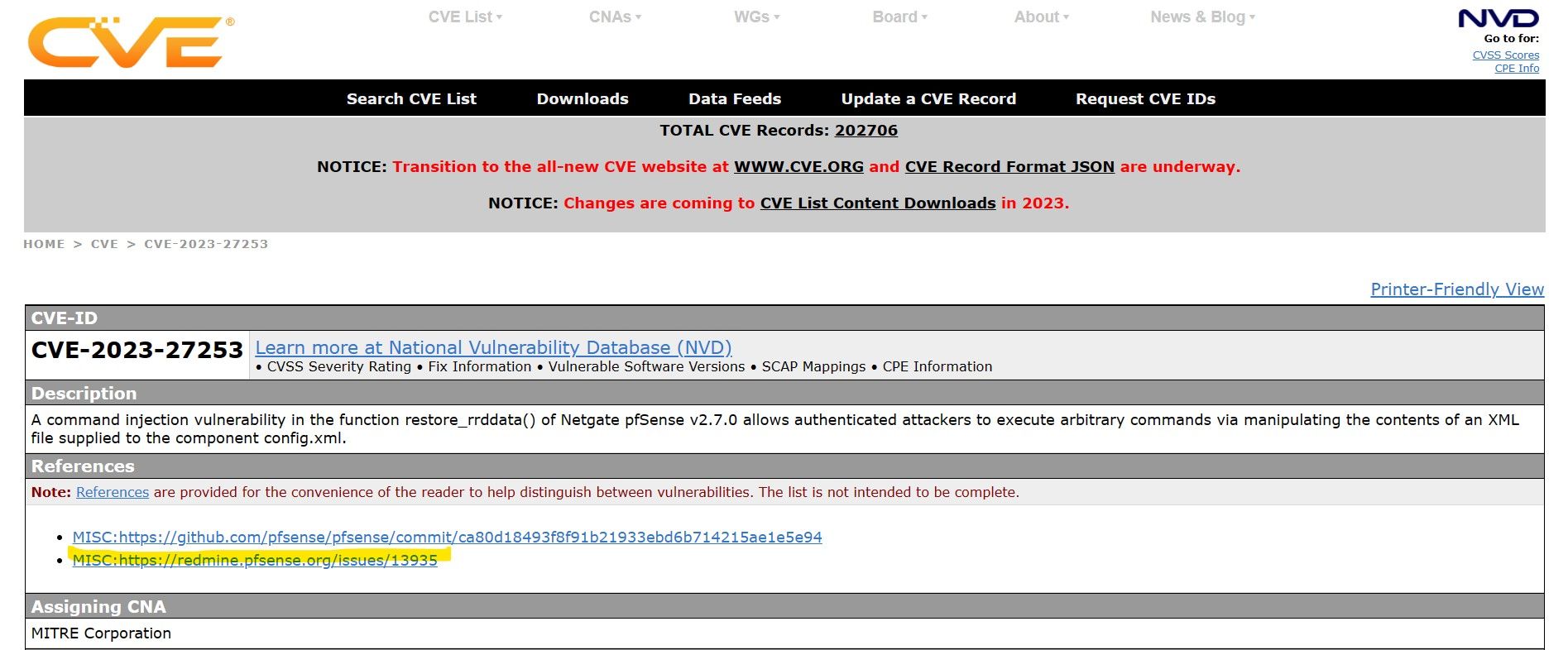
CVE forum discussion categories?
-
CVE forum discussion categories?
If it will be there, it could warn users, but also bad peoples!
Does anyone know if there is a vulnerability area to
get support on how to make the firewall even more secure?-
pfSense update or upgrade
-
Patch system
-
pkg update/upgrade
-
pen testing
-
reporting bugs
-
watching the OS thread (vuln) list
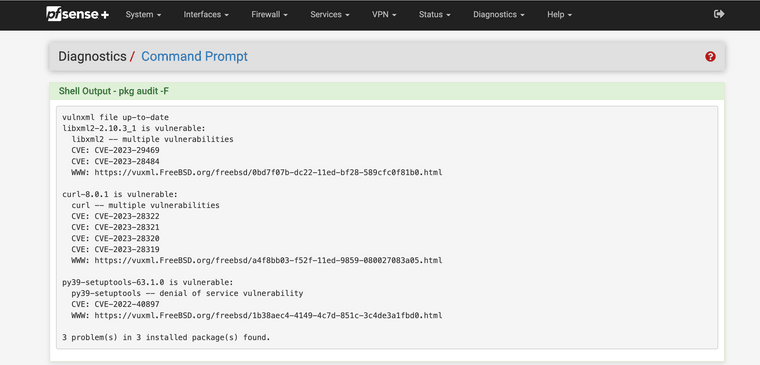
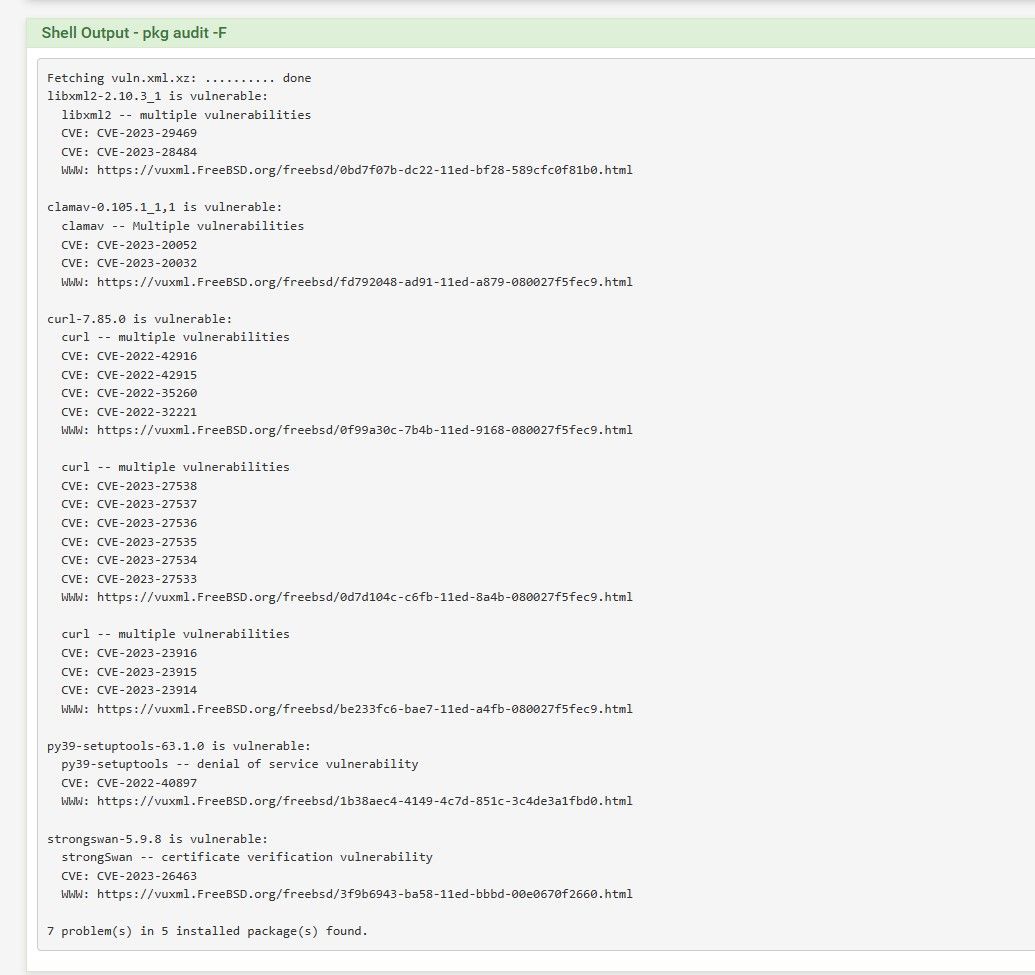
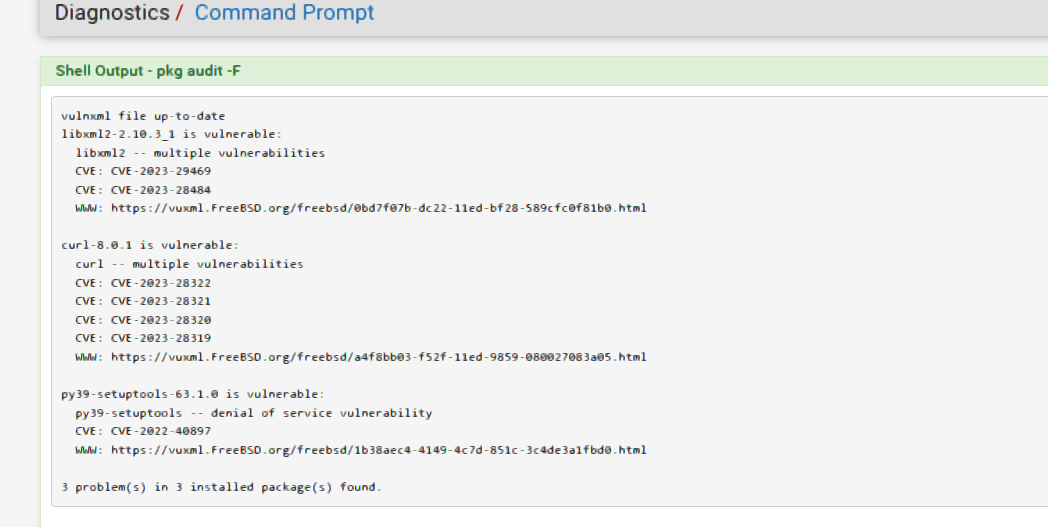
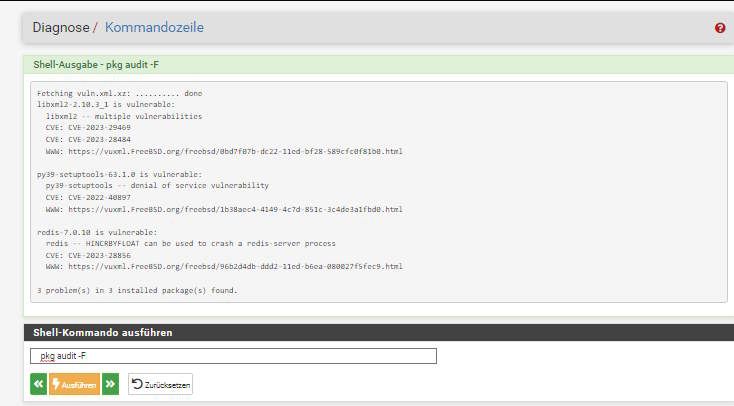
Here are my scans for 23.05 RC (latest) and 2.7 Devel (latest), only three on both systems were reported.
pfSense 23.05 RC
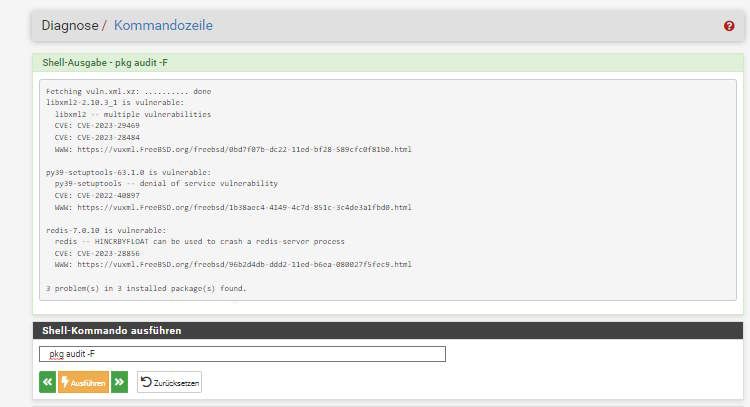
pfSense 2.7 Devel
-
-
@dobby_ I wonder why mine has curl installed
-
@jonathanlee said in CVE forum discussion categories?:
@dobby_ I wonder why mine has curl installed
It is perhaps owed to a packet dependency!
You were installing a .pkg and curl came by site
installed, because the packet is need to run curl?
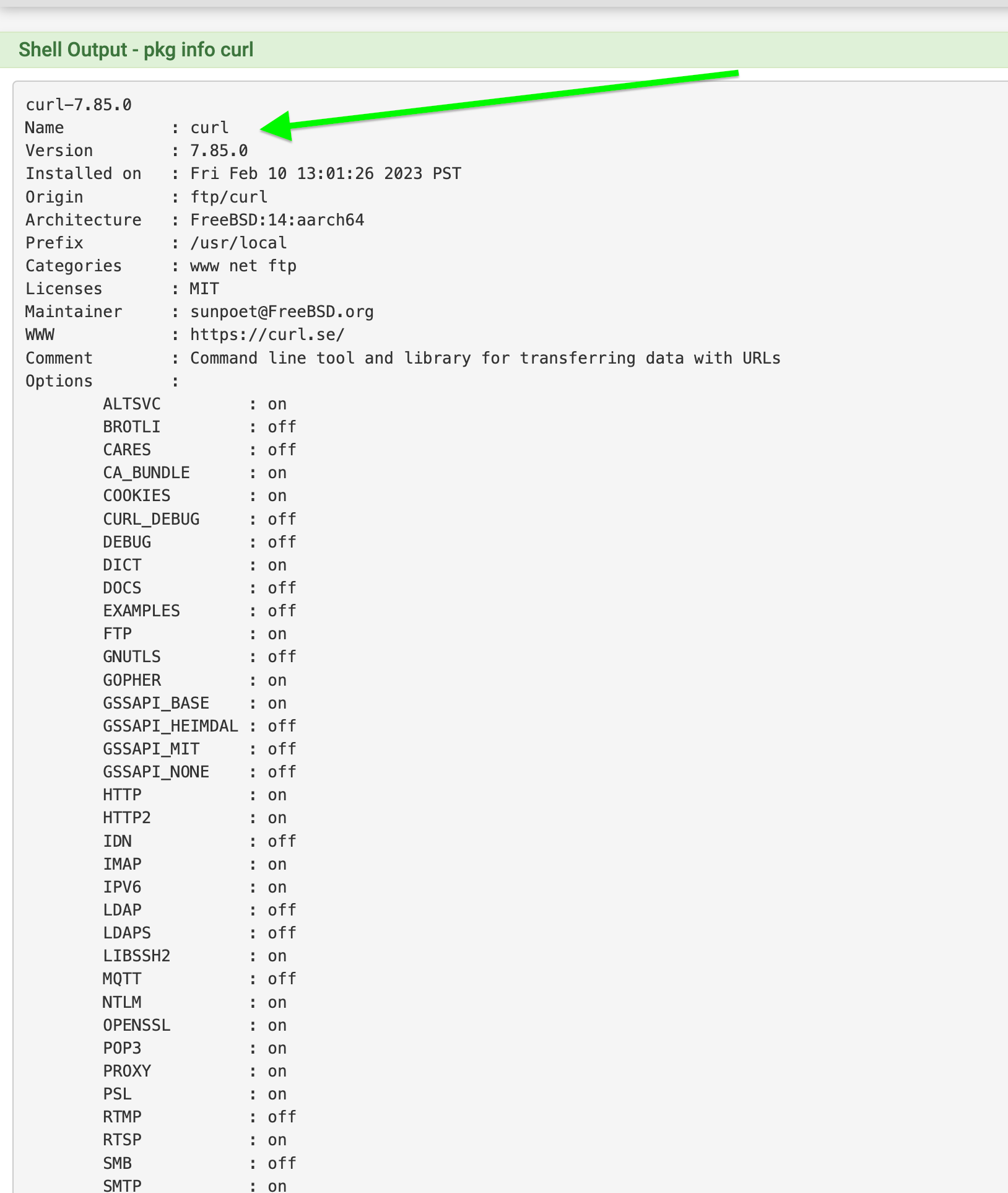
Could be or am I wrong here?23.05 RC output
[23.05-RC][root@xx xx xx]/root: pkg info curl curl-8.0.1 Name : curl Version : 8.0.1 Installed on : Wed May 10 22:13:57 2023 CEST Origin : ftp/curl Architecture : FreeBSD:14:amd64 Prefix : /usr/local Categories : www net ftp Licenses : MIT Maintainer : sunpoet@FreeBSD.org WWW : https://curl.se/ Comment : Command line tool and library for transferring data with URLs Options : ALTSVC : on BROTLI : off CARES : off CA_BUNDLE : on COOKIES : on CURL_DEBUG : off DEBUG : off DICT : on DOCS : off EXAMPLES : off FTP : on GNUTLS : off GOPHER : on GSSAPI_BASE : on GSSAPI_HEIMDAL : off GSSAPI_MIT : off GSSAPI_NONE : off HTTP : on HTTP2 : on IDN : off IMAP : on IPV6 : on LDAP : off LDAPS : off LIBSSH2 : on MQTT : off NTLM : on OPENSSL : on POP3 : on PROXY : on PSL : on RTMP : off RTSP : on SMB : off SMTP : on STATIC : on TELNET : on TFTP : on THREADED_RESOLVER: on TLS_SRP : on WOLFSSL : off ZSTD : off Shared Libs required: libssh2.so.1 libpsl.so.5 libnghttp2.so.14 Shared Libs provided: libcurl.so.4 Annotations : FreeBSD_version: 1400085 build_timestamp: 2023-05-04T16:56:37+0000 built_by : poudriere-git-3.3.99.20220831 cpe : cpe:2.3:a:haxx:curl:8.0.1:::::freebsd14:x64 port_checkout_unclean: no port_git_hash : 0799d457b1be ports_top_checkout_unclean: yes ports_top_git_hash: e7f28213b661 repo_type : binary repository : pfSense Flat size : 3.19MiB Description : curl is used in command lines or scripts to transfer data. It is also used in cars, television sets, routers, printers, audio equipment, mobile phones, tablets, settop boxes, media players and is the internet transfer backbone for thousands of software applications affecting billions of humans daily. It supports DICT, FILE, FTP, FTPS, Gopher, HTTP, HTTPS, IMAP, IMAPS, LDAP, LDAPS, POP3, POP3S, RTMP, RTSP, SCP, SFTP, SMB, SMBS, SMTP, SMTPS, Telnet and TFTP. curl supports SSL certificates, HTTP POST, HTTP PUT, FTP uploading, HTTP form based upload, proxies, HTTP/2, cookies, user+password authentication (Basic, Plain, Digest, CRAM-MD5, NTLM, Negotiate and Kerberos), file transfer resume, proxy tunneling and more. WWW: https://curl.se/ WWW: https://github.com/curl/curl2.7 Devel output
[2.7.0-DEVELOPMENT][root@xx xx xx]/root: pkg info curl curl-8.0.1 Name : curl Version : 8.0.1 Installed on : Mon May 8 21:38:14 2023 CEST Origin : ftp/curl Architecture : FreeBSD:14:amd64 Prefix : /usr/local Categories : www net ftp Licenses : MIT Maintainer : sunpoet@FreeBSD.org WWW : https://curl.se/ Comment : Command line tool and library for transferring data with URLs Options : ALTSVC : on BROTLI : off CARES : off CA_BUNDLE : on COOKIES : on CURL_DEBUG : off DEBUG : off DICT : on DOCS : off EXAMPLES : off FTP : on GNUTLS : off GOPHER : on GSSAPI_BASE : on GSSAPI_HEIMDAL : off GSSAPI_MIT : off GSSAPI_NONE : off HTTP : on HTTP2 : on IDN : off IMAP : on IPV6 : on LDAP : off LDAPS : off LIBSSH2 : on MQTT : off NTLM : on OPENSSL : on POP3 : on PROXY : on PSL : on RTMP : off RTSP : on SMB : off SMTP : on STATIC : on TELNET : on TFTP : on THREADED_RESOLVER: on TLS_SRP : on WOLFSSL : off ZSTD : off Shared Libs required: libssh2.so.1 libpsl.so.5 libnghttp2.so.14 Shared Libs provided: libcurl.so.4 Annotations : FreeBSD_version: 1400085 build_timestamp: 2023-04-07T06:45:52+0000 built_by : poudriere-git-3.3.99.20220831 cpe : cpe:2.3:a:haxx:curl:8.0.1:::::freebsd14:x64 port_checkout_unclean: no port_git_hash : 0799d457b1be ports_top_checkout_unclean: yes ports_top_git_hash: 21d56ba2ad32 repo_type : binary repository : pfSense Flat size : 3.19MiB Description : curl is used in command lines or scripts to transfer data. It is also used in cars, television sets, routers, printers, audio equipment, mobile phones, tablets, settop boxes, media players and is the internet transfer backbone for thousands of software applications affecting billions of humans daily. It supports DICT, FILE, FTP, FTPS, Gopher, HTTP, HTTPS, IMAP, IMAPS, LDAP, LDAPS, POP3, POP3S, RTMP, RTSP, SCP, SFTP, SMB, SMBS, SMTP, SMTPS, Telnet and TFTP. curl supports SSL certificates, HTTP POST, HTTP PUT, FTP uploading, HTTP form based upload, proxies, HTTP/2, cookies, user+password authentication (Basic, Plain, Digest, CRAM-MD5, NTLM, Negotiate and Kerberos), file transfer resume, proxy tunneling and more. WWW: https://curl.se/ WWW: https://github.com/curl/curlYou may can see differences to the output from
your console? I mean a difference to your version?23.05 RC is pretty stable running here and has no
patches anymore, that were recommended.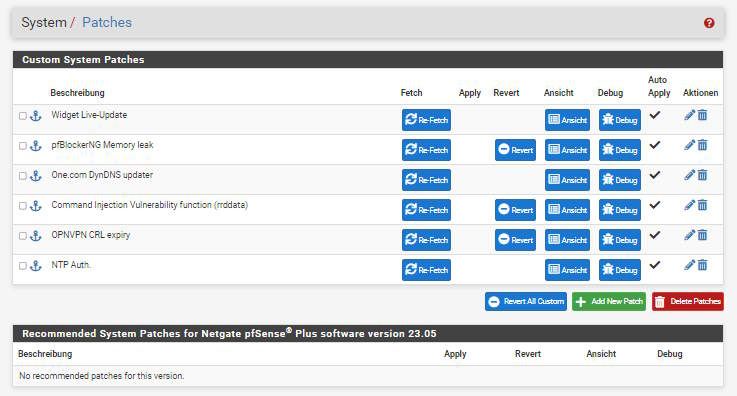
2.7 Devel is also running nice here and has no
patches anymore, that were recommended.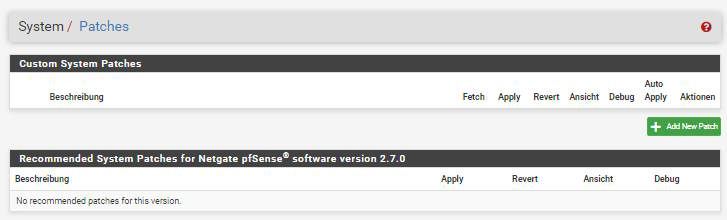
-
@jonathanlee Likely pfBlockerNG
-
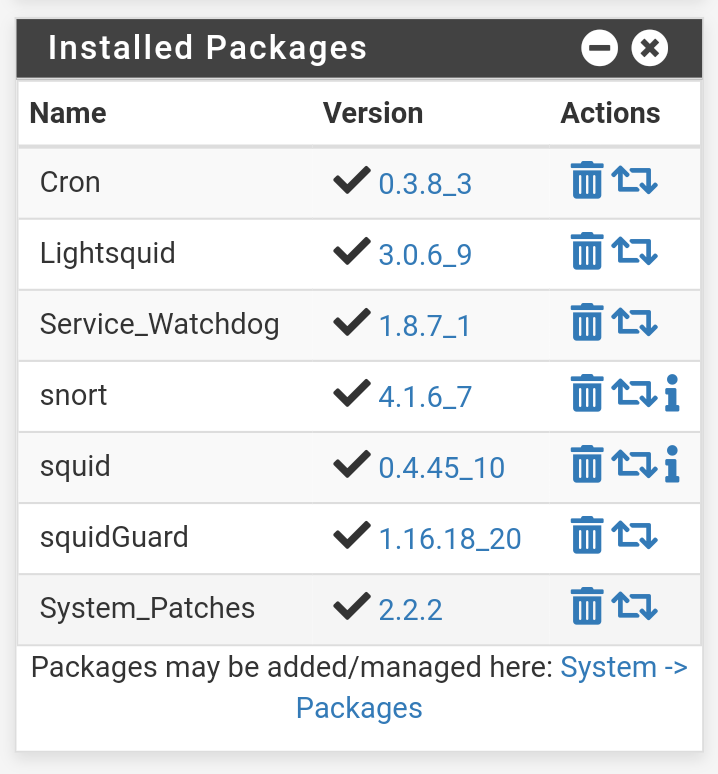
@rcoleman-netgate I have Squidguard, squid, squidlite, cron, watchdog, snort, patches,
-
@rcoleman-netgate
On 23.05 RC
pfBlockerNG_v3.2.0_5On 2.7 devel
pfBlockerNG_v3.2.0_4@JonathanLee
23.05 RC
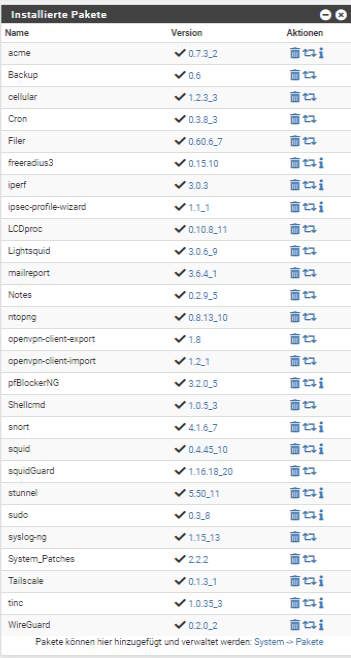
2.7 Devel
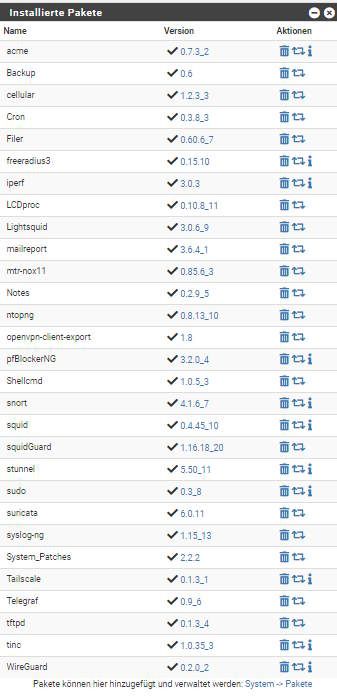
-
@dobby_ i noticed strongswan also shows as an issue for me. I am still running 23.01 the version before 23.05.
-
@jonathanlee said in CVE forum discussion categories?:
@rcoleman-netgate I have Squidguard, squid, squidlite, cron, watchdog, snort, patches,
I suspect curl() is required by System Patches. You can find dependencies from the System->Packages page.
-
@jonathanlee said in CVE forum discussion categories?:
@dobby_ i noticed strongswan also shows as an issue for me. I am still running 23.01 the version before 23.05.
Many patches were finding its way into the 23.05 and
on top I think there will be more actual packages ad/or
other version inside that will be not anymore affected
by the vuln`s you were presenting.23.05 RC Strongswan
[23.05-RC][root@xx xx xx]/root: pkg info strongswan strongswan-5.9.10_2 Name : strongswan Version : 5.9.10_2 Installed on : Wed May 10 22:13:58 2023 CEST Origin : security/strongswan Architecture : FreeBSD:14:amd64 Prefix : /usr/local Categories : security net-vpn Licenses : GPLv2 Maintainer : strongswan@nanoteq.com WWW : https://www.strongswan.org Comment : Open Source IKEv2 IPsec-based VPN solution Options : BUILTIN : off CTR : off CURL : on EAPAKA3GPP2 : off EAPDYNAMIC : on EAPRADIUS : on EAPSIMFILE : on FARP : off GCM : on IKEV1 : on IPSECKEY : on KDF : on KERNELLIBIPSEC : off LDAP : off LIBC : off LOADTESTER : off MEDIATION : off MYSQL : off PKCS11 : on PKI : on PYTHON : off SCEP : off SMP : off SQLITE : off SWANCTL : on TESTVECTOR : off TPM : off TSS2 : off UNBOUND : on UNITY : on VICI : on VSTR : on XAUTH : on Shared Libs required: libvstr-1.0.so.0 libunbound.so.8 libldns.so.3 libcurl.so.4 Shared Libs provided: libvici.so.0 libtls.so.0 libstrongswan.so.0 libstrongswan-xcbc.so libstrongswan-xauth-pam.so libstrongswan-xauth-generic.so libstrongswan-xauth-eap.so libstrongswan-x509.so libstrongswan-whitelist.so libstrongswan-vici.so libstrongswan-updown.so libstrongswan-unity.so libstrongswan-unbound.so libstrongswan-stroke.so libstrongswan-sshkey.so libstrongswan-socket-default.so libstrongswan-sha2.so libstrongswan-sha1.so libstrongswan-revocation.so libstrongswan-resolve.so libstrongswan-rc2.so libstrongswan-random.so libstrongswan-pubkey.so libstrongswan-pkcs8.so libstrongswan-pkcs7.so libstrongswan-pkcs12.so libstrongswan-pkcs11.so libstrongswan-pkcs1.so libstrongswan-pgp.so libstrongswan-pem.so libstrongswan-openssl.so libstrongswan-nonce.so libstrongswan-md5.so libstrongswan-md4.so libstrongswan-kernel-pfroute.so libstrongswan-kernel-pfkey.so libstrongswan-kdf.so libstrongswan-ipseckey.so libstrongswan-hmac.so libstrongswan-gcm.so libstrongswan-fips-prf.so libstrongswan-eap-ttls.so libstrongswan-eap-tls.so libstrongswan-eap-sim.so libstrongswan-eap-sim-file.so libstrongswan-eap-radius.so libstrongswan-eap-peap.so libstrongswan-eap-mschapv2.so libstrongswan-eap-md5.so libstrongswan-eap-identity.so libstrongswan-eap-dynamic.so libstrongswan-drbg.so libstrongswan-dnskey.so libstrongswan-des.so libstrongswan-curve25519.so libstrongswan-curl.so libstrongswan-counters.so libstrongswan-constraints.so libstrongswan-cmac.so libstrongswan-blowfish.so libstrongswan-attr.so libstrongswan-aes.so libstrongswan-addrblock.so libsimaka.so.0 libradius.so.0 libcharon.so.0 Annotations : FreeBSD_version: 1400085 build_timestamp: 2023-05-04T17:08:03+0000 built_by : poudriere-git-3.3.99.20220831 cpe : cpe:2.3:a:strongswan:strongswan:5.9.10:::::freebsd14:x64:2 port_checkout_unclean: no port_git_hash : 78ba9de1f8df ports_top_checkout_unclean: yes ports_top_git_hash: e7f28213b661 repo_type : binary repository : pfSense Flat size : 3.24MiB Description : Strongswan is an open source IPsec-based VPN solution. Strongswan for FreeBSD implements both the IKEv1 and IKEv2 (RFC 5996) key exchange protocols. WWW: https://www.strongswan.org2.7 Strongswan
[2.7.0-DEVELOPMENT][root@xx xx xx]/root: pkg info strongswan strongswan-5.9.10_2 Name : strongswan Version : 5.9.10_2 Installed on : Mon May 8 21:38:18 2023 CEST Origin : security/strongswan Architecture : FreeBSD:14:amd64 Prefix : /usr/local Categories : security net-vpn Licenses : GPLv2 Maintainer : strongswan@nanoteq.com WWW : https://www.strongswan.org Comment : Open Source IKEv2 IPsec-based VPN solution Options : BUILTIN : off CTR : off CURL : on EAPAKA3GPP2 : off EAPDYNAMIC : on EAPRADIUS : on EAPSIMFILE : on FARP : off GCM : on IKEV1 : on IPSECKEY : on KDF : on KERNELLIBIPSEC : off LDAP : off LIBC : off LOADTESTER : off MEDIATION : off MYSQL : off PKCS11 : on PKI : on PYTHON : off SCEP : off SMP : off SQLITE : off SWANCTL : on TESTVECTOR : off TPM : off TSS2 : off UNBOUND : on UNITY : on VICI : on VSTR : on XAUTH : on Shared Libs required: libvstr-1.0.so.0 libunbound.so.8 libldns.so.3 libcurl.so.4 Shared Libs provided: libvici.so.0 libtls.so.0 libstrongswan.so.0 libstrongswan-xcbc.so libstrongswan-xauth-pam.so libstrongswan-xauth-generic.so libstrongswan-xauth-eap.so libstrongswan-x509.so libstrongswan-whitelist.so libstrongswan-vici.so libstrongswan-updown.so libstrongswan-unity.so libstrongswan-unbound.so libstrongswan-stroke.so libstrongswan-sshkey.so libstrongswan-socket-default.so libstrongswan-sha2.so libstrongswan-sha1.so libstrongswan-revocation.so libstrongswan-resolve.so libstrongswan-rc2.so libstrongswan-random.so libstrongswan-pubkey.so libstrongswan-pkcs8.so libstrongswan-pkcs7.so libstrongswan-pkcs12.so libstrongswan-pkcs11.so libstrongswan-pkcs1.so libstrongswan-pgp.so libstrongswan-pem.so libstrongswan-openssl.so libstrongswan-nonce.so libstrongswan-md5.so libstrongswan-md4.so libstrongswan-kernel-pfroute.so libstrongswan-kernel-pfkey.so libstrongswan-kdf.so libstrongswan-ipseckey.so libstrongswan-hmac.so libstrongswan-gcm.so libstrongswan-fips-prf.so libstrongswan-eap-ttls.so libstrongswan-eap-tls.so libstrongswan-eap-sim.so libstrongswan-eap-sim-file.so libstrongswan-eap-radius.so libstrongswan-eap-peap.so libstrongswan-eap-mschapv2.so libstrongswan-eap-md5.so libstrongswan-eap-identity.so libstrongswan-eap-dynamic.so libstrongswan-drbg.so libstrongswan-dnskey.so libstrongswan-des.so libstrongswan-curve25519.so libstrongswan-curl.so libstrongswan-counters.so libstrongswan-constraints.so libstrongswan-cmac.so libstrongswan-blowfish.so libstrongswan-attr.so libstrongswan-aes.so libstrongswan-addrblock.so libsimaka.so.0 libradius.so.0 libcharon.so.0 Annotations : FreeBSD_version: 1400085 build_timestamp: 2023-04-27T06:52:01+0000 built_by : poudriere-git-3.3.99.20220831 cpe : cpe:2.3:a:strongswan:strongswan:5.9.10:::::freebsd14:x64:2 port_checkout_unclean: no port_git_hash : 78ba9de1f8df ports_top_checkout_unclean: yes ports_top_git_hash: 78ba9de1f8df repo_type : binary repository : pfSense Flat size : 3.24MiB Description : Strongswan is an open source IPsec-based VPN solution. Strongswan for FreeBSD implements both the IKEv1 and IKEv2 (RFC 5996) key exchange protocols. WWW: https://www.strongswan.org -
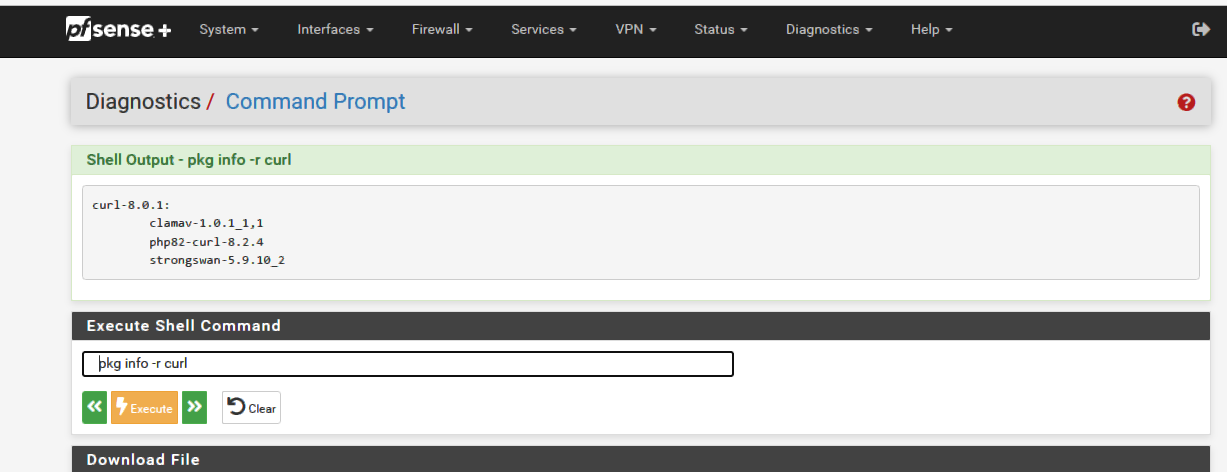
@dobby_ how did you update curl?
-
@jonathanlee said in CVE forum discussion categories?:
@dobby_ how did you update curl?
I never did that! I was only installing 23.05 RC and on the
other hardware 2.7 Devel, both are amd64 (x86_64), so
I don´t know in real but I am imagine that in the newer
versions are also newer packets (pkg`s) installed or the
last available versions of some packets, modules and so
on and so on. -
pkg info -r curl should tell you what packages are depending on the curl package
-
-
This time I have one more then you!
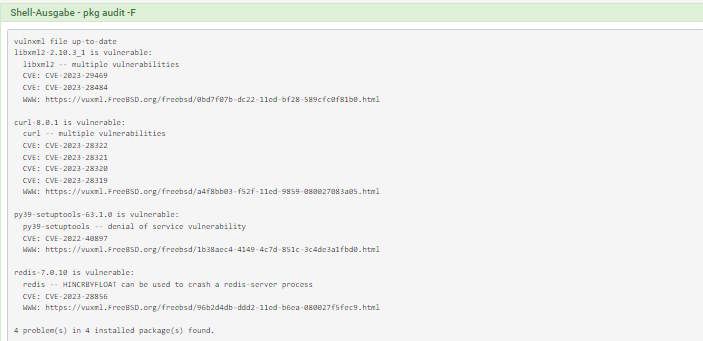
-
@dobby_ I wonder how we can fix curl issues
-
@jonathanlee said in CVE forum discussion categories?:
@dobby_ I wonder how we can fix curl issues
Before it wasn`t marked as vuln. and now it is also shown
in the newer version, perhaps they found the problems
in the last days/hours and before it was not known.As an example and compared to the 2.7 Devel version
(latest) you may able to see what we can await from
the real 2.7 Release.
-
More often than not even if something is marked as a problem in cURL, the actual bug does not affect how cURL is used in pfSense software.
Many of these bugs end up being about connecting to random/arbitrary malicious servers or using options/features/functions that never get enabled on pfSense, and so on.
So it's not enough to see that something is flagged as being potentially vulnerable you also have to know if that vulnerable use case applies to cURL in this type of environment.
Usually if something is worth worrying about we'll bump the package even for older releases and then people can upgrade it manually from the shell, but sometimes that isn't feasible.
-
I got rid of some multiples in CURL and Strongswan by installing and uninstalling the package NUT again. NUT had some left over files from the last pfSense version.