No DHCP on pfSense VLAN with Cisco Smart Switch
-
@cannondale I saw that but again lets see your cli output.. Which was not showing that it was in switchport mode..
This pretty basic stuff..
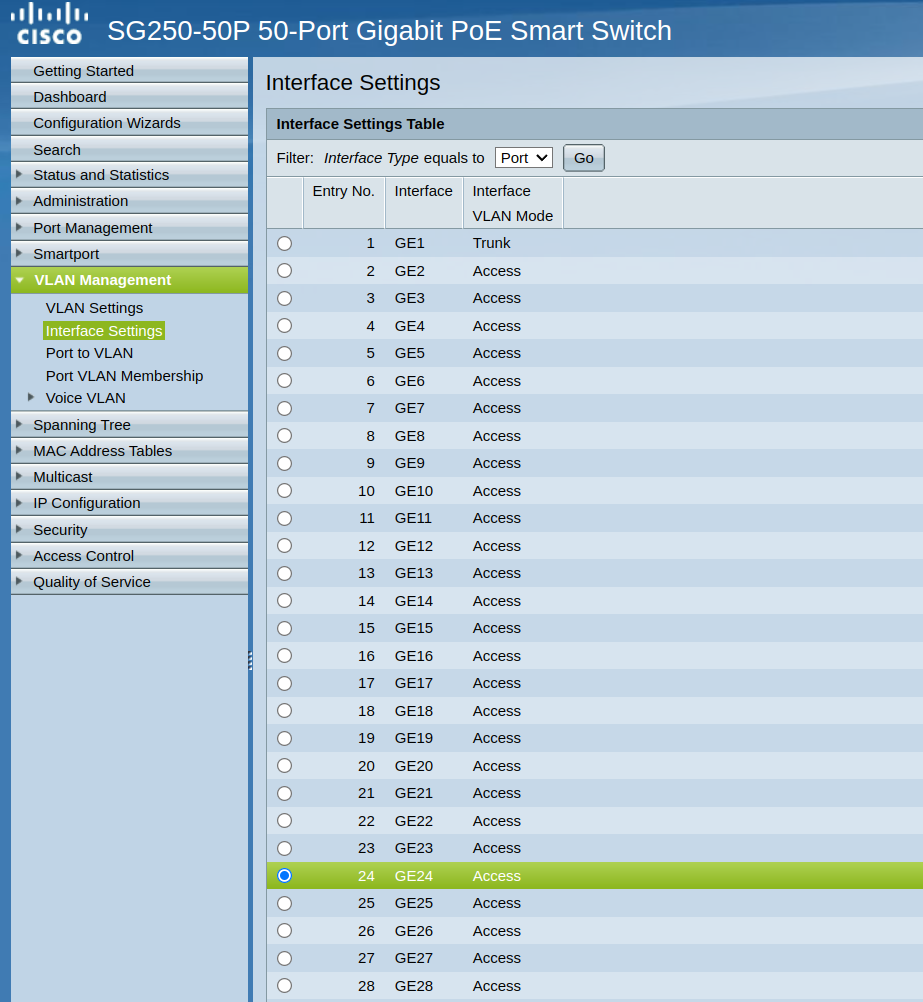
access vlan 10.. on port 24
Trunk port vlan 10 would be tagged..
Unless your tagging on your linux box the untagged traffic comes into port 24, the switch says oh this is vlan 10.. Oh its broadcast (dhcp) send it out on port 1 to pfsense, and any other ports that set to vlan 10 because its a broadcast.
So either the port is not correct as of yet, or its pvid is not 10? Or you have the client plugged into that port tagging 10 which wouldn't work.
Or you dhcp is not enabled?
-
johnpoz,
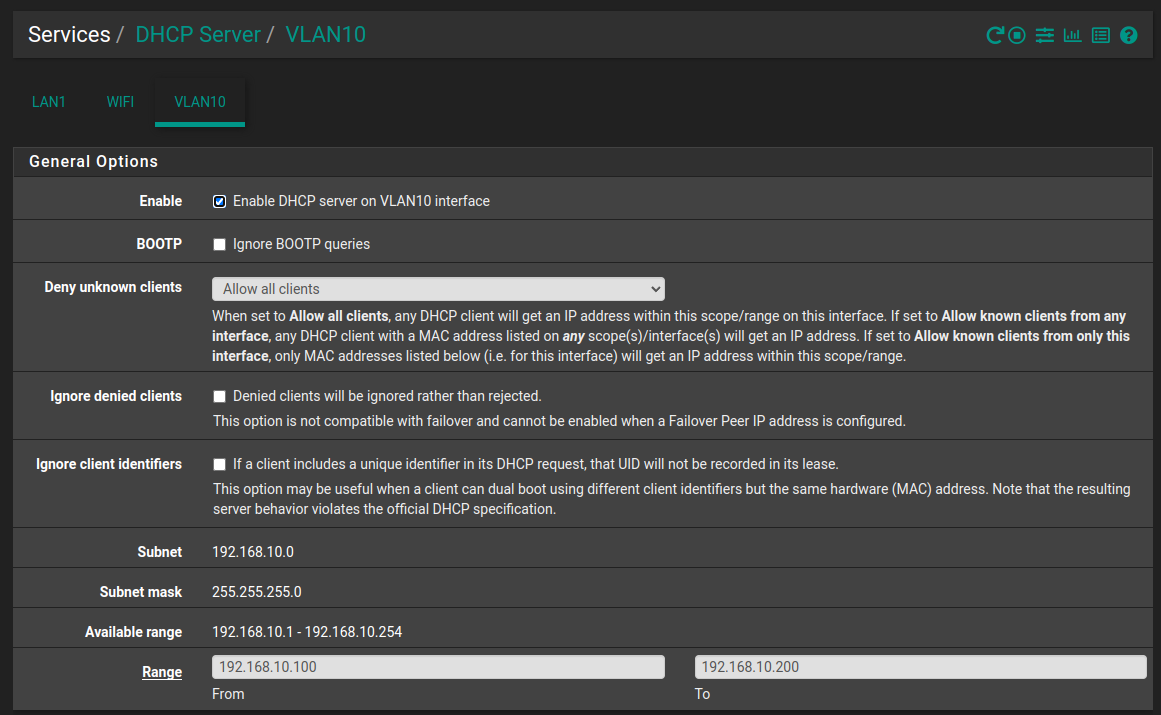
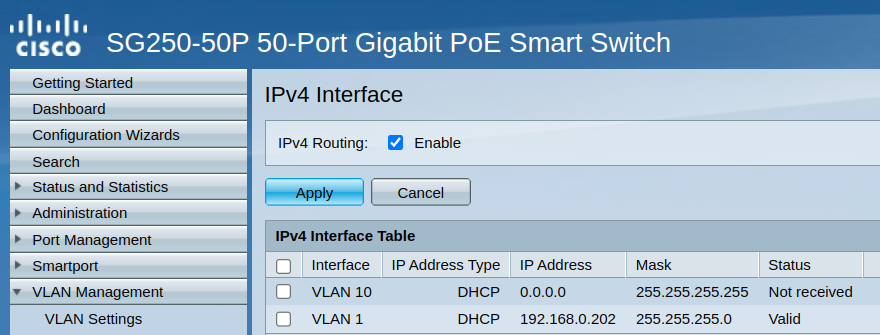
Here is the screenshot of the cli commands:
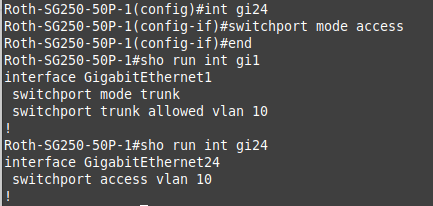
"So either the port is not correct as of yet, or its pvid is not 10?"
I don't believe that the pvid can be set on an Access port as there is no option on the WebGUI for pvid."Or you have the client plugged into that port tagging 10 which wouldn't work."
I currently have a Linux workstation plugged into port 24 (VLAN10)."Or you dhcp is not enabled"
-
@cannondale And again your cli is showing wrong... It should show that the interface is switchport mode..
Please set it to switchport mode via the cli. Oh looks like you did.. I would reset your interface then.. Your saying none of your interfaces in access mode show they are actually in switchport mode access?
Why are you trying to route???
Pfsense is your router - your switch would be layer 2 only..
I currently have a Linux workstation plugged into port 24 (VLAN10).
And you didn't set vlan 10 on its interface did you?
Can you post your full running config please.
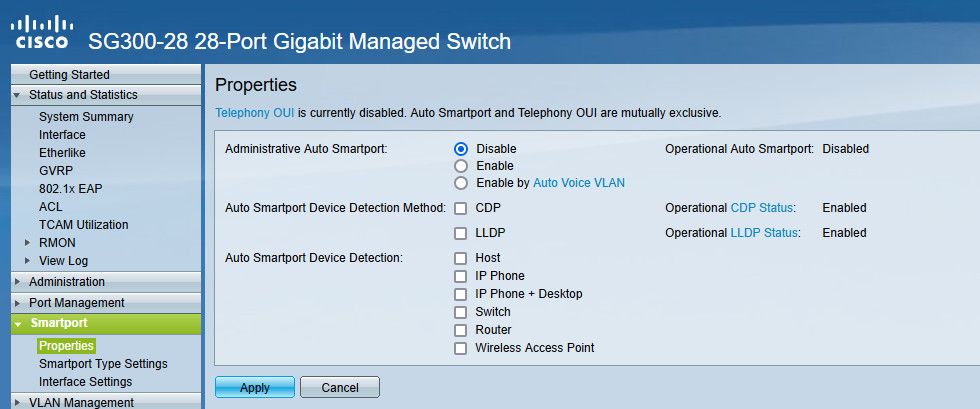
Do you have smartport enabled? I would turn that off.
-
@johnpoz
CLI output might be dependant of the switch software version
Don't know about the SG-series, but CBS-series switch software has the ports default mode as access and looks like the config only shows the switchport command when set to something other than access.
Maybe they decided to "cleanup" the config by hiding the commands that set the "default value"This is snippet from my switch (CBS250) "sh run" with ports and vlans working as intended
interface GigabitEthernet1 description Firewall switchport mode trunk switchport trunk allowed vlan 10,20,25,30,35,40,50 ! interface GigabitEthernet2 description "Wifi AP" switchport mode trunk switchport trunk allowed vlan 10,20,25,30,35,40,50 ! interface GigabitEthernet3 description "Main PC" switchport access vlan 20 ! interface GigabitEthernet4 description HomeServer switchport access vlan 20 ! -
Thanks for your continued help johnpoz!
I have confirmed that smartport is disabled.
I'm not a network engineer but mvikman's explanation for why the cli is not displaying "switchport mode access" sounds reasonable as the WebGUI does show "switchport mode access" for port 24 (VLAN10).Below is the output of my running config:
config-file-header Roth-SG250-50P-1 v2.5.9.16 / RCBS3.1_930_871_108 CLI v1.0 file SSD indicator excluded @ ! unit-type-control-start unit-type unit 1 network gi uplink none unit-type-control-end ! vlan database vlan 10 exit voice vlan state auto-triggered voice vlan oui-table add 0001e3 Siemens_AG_phone________ voice vlan oui-table add 00036b Cisco_phone_____________ voice vlan oui-table add 00096e Avaya___________________ voice vlan oui-table add 000fe2 H3C_Aolynk______________ voice vlan oui-table add 0060b9 Philips_and_NEC_AG_phone voice vlan oui-table add 00d01e Pingtel_phone___________ voice vlan oui-table add 00e075 Polycom/Veritel_phone___ voice vlan oui-table add 00e0bb 3Com_phone______________ no boot host auto-config no boot host auto-update no bonjour enable bonjour interface range vlan 1 hostname Roth-SG250-50P-1 username jer password encrypted $86$5/Jf/f1pY8/95XGv$kPRdzeRMBXmEdsjyTZ1l4+OqCg9fuZ7uKSe5I7LV9IbcgUpUgGQXoGLMEO1AZF52onsZ3HTShH3OYBSXslXbVA== privilege 15 username jer2 password encrypted $86$Jd6VBm9YYE9hsEqS$Wr7/T+o2oqDACWSHr0SNJrmwXG2QQ3MS+4EG1j6BknUM6Z8LMYb1/kokfIc3KefDaW5JkhtnW3+gJTnr3sbDJA== privilege 15 username cisco password encrypted $86$/AkLn2WkB5AHHhIy$e/TgE126IBbIHLLsdMMw6ozjTovM1bR132PxH3lGmJeltzZ4U3ug9F3ZaUl+BclKIcE60h2j7Sn6o7RYksS53g== ip http timeout-policy 0 clock timezone J -4 clock dhcp timezone ip telnet server ! interface vlan 10 name "VL10" no snmp trap link-status ! interface GigabitEthernet1 switchport mode trunk switchport trunk allowed vlan 10 ! interface GigabitEthernet24 switchport access vlan 10 ! exit -
@cannondale that doesn't seem like a full config..
But what I would do is lets isolate if pfsense problem or switch problem - there is no way pfsense can hand out a dhcp if doesn't see it, and for it to see it the discover has to come in tagged for vlan 10.
So I would do a packet capture via tcpdump on that interface on pfsense - do you see the tagged traffic come?
example.. here tcpdump on my igb2 where I run tagged vlans.. See traffic from my tagged vlans 4 and 6, and there is stp that is not tagged
[23.01-RELEASE][admin@sg4860.local.lan]/root: tcpdump -i igb2 -e tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on igb2, link-type EN10MB (Ethernet), capture size 262144 bytes 06:39:53.641566 68:57:2d:98:28:22 (oui Unknown) > Broadcast, ethertype 802.1Q (0x8100), length 218: vlan 4, p 0, ethertype IPv4, office3.local.lan.62514 > 255.255.255.255.6667: UDP, length 172 06:39:53.681635 00:08:a2:0c:e6:20 (oui Unknown) > f8:e4:3b:72:18:bb (oui Unknown), ethertype 802.1Q (0x8100), length 174: vlan 6, p 0, ethertype IPv4, 165.225.60.29.https > TIAA-17503J3.local.lan.49373: UDP, length 128 06:39:53.682349 00:08:a2:0c:e6:20 (oui Unknown) > f8:e4:3b:72:18:bb (oui Unknown), ethertype 802.1Q (0x8100), length 1292: vlan 6, p 0, ethertype IPv4, 165.225.60.29.https > TIAA-17503J3.local.lan.49373: UDP, length 1246 06:39:53.684130 f8:e4:3b:72:18:bb (oui Unknown) > 00:08:a2:0c:e6:20 (oui Unknown), ethertype 802.1Q (0x8100), length 139: vlan 6, p 0, ethertype IPv4, TIAA-17503J3.local.lan.49373 > 165.225.60.29.https: UDP, length 93 06:39:53.694328 18:69:d8:39:e4:23 (oui Unknown) > Broadcast, ethertype 802.1Q (0x8100), length 218: vlan 4, p 0, ethertype IPv4, island2.local.lan.64137 > 255.255.255.255.6667: UDP, length 172 06:39:53.706147 68:57:2d:98:36:83 (oui Unknown) > Broadcast, ethertype 802.1Q (0x8100), length 218: vlan 4, p 0, ethertype IPv4, office2.local.lan.62515 > 255.255.255.255.6667: UDP, length 172 06:39:53.709447 50:14:79:d4:0f:11 (oui Unknown) > Broadcast, ethertype 802.1Q (0x8100), length 60: vlan 4, p 0, ethertype ARP, Request who-has sg4860.wpsk.local.lan (Broadcast) tell iRobot.local.lan, length 42 06:39:53.709464 00:08:a2:0c:e6:20 (oui Unknown) > 50:14:79:d4:0f:11 (oui Unknown), ethertype 802.1Q (0x8100), length 46: vlan 4, p 0, ethertype ARP, Reply sg4860.wpsk.local.lan is-at 00:08:a2:0c:e6:20 (oui Unknown), length 28 06:39:53.786496 d4:a6:51:cf:c5:45 (oui Unknown) > Broadcast, ethertype 802.1Q (0x8100), length 218: vlan 4, p 0, ethertype IPv4, endtable.local.lan.58883 > 255.255.255.255.6667: UDP, length 172 06:39:53.814764 d4:a6:51:cc:f7:a6 (oui Unknown) > Broadcast, ethertype 802.1Q (0x8100), length 218: vlan 4, p 0, ethertype IPv4, chair-lamp.local.lan.65202 > 255.255.255.255.6667: UDP, length 172 06:39:53.819990 18:69:d8:3a:03:cd (oui Unknown) > Broadcast, ethertype 802.1Q (0x8100), length 218: vlan 4, p 0, ethertype IPv4, island1.local.lan.52605 > 255.255.255.255.6667: UDP, length 172 06:39:53.843301 18:69:d8:39:ed:ba (oui Unknown) > Broadcast, ethertype 802.1Q (0x8100), length 218: vlan 4, p 0, ethertype IPv4, D5.local.lan.59982 > 255.255.255.255.6667: UDP, length 172 06:39:54.078536 70:6e:6d:f3:11:98 (oui Unknown) > 01:80:c2:00:00:00 (oui Unknown), 802.3, length 39: LLC, dsap STP (0x42) Individual, ssap STP (0x42) Command, ctrl 0x03: STP 802.1w, Rapid STP, Flags [Learn, Forward, Agreement], bridge-id 1000.70:6e:6d:f3:11:93.8035, length 43Make sure your client does a dhcp discover while your sniffing.. Do you see this traffic hit pfsense tagged vlan 10? If so then something wrong with pfsense. if it doesn't send a response - if you never see it, then something wrong downstream, your switch, the client, you sure your actually connected to port 24 and get a link light for example.
-
Thanks for the information johnpoz. Very helpful.
I ran tcpdump -i igb1 -e. Note that ibg1 is my pfSence interface.
While tcpdump was running, I unplugged and plugged the port 24 cable (VLAN10) that is connected to a Linux workstation.
I then stopped tcpdump and cut and pasted the output into a text editor to search for "vlan" but found nothing.Also checked the pfSence DHCP log and did not see DHCPREQUEST for the VLAN.
To double check the workstation connection, I plugged the workstation into another switch port and got an DHCP IP as normal. Then reconnected to port 24 (VLAN10).
-
@cannondale well if pfsense never sees anything come in tagged 10, then how would its vlan 10 ever hand out a dhcp address.
You got something funky going on in your switch I would say.. Its not a difficult config..
pfsense -- untagged/vlan 10 tagged -- switch -- untagged vlan 10 -- client
Your saying client in another port that is just default vlan 1 and untagged work fine.. But its not tagging traffic to pfsense when it should on vlan 10.
I am with you that you shouldn't have to set pvid, and ok your switch cli doesn't show switchport mode access in the client.. But something is broken if pfsense is not seeing traffic.
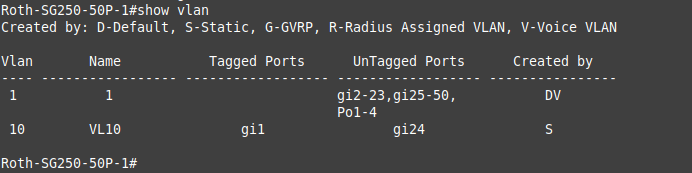
Can you do a show vlan on your sg250? I can on my sg300
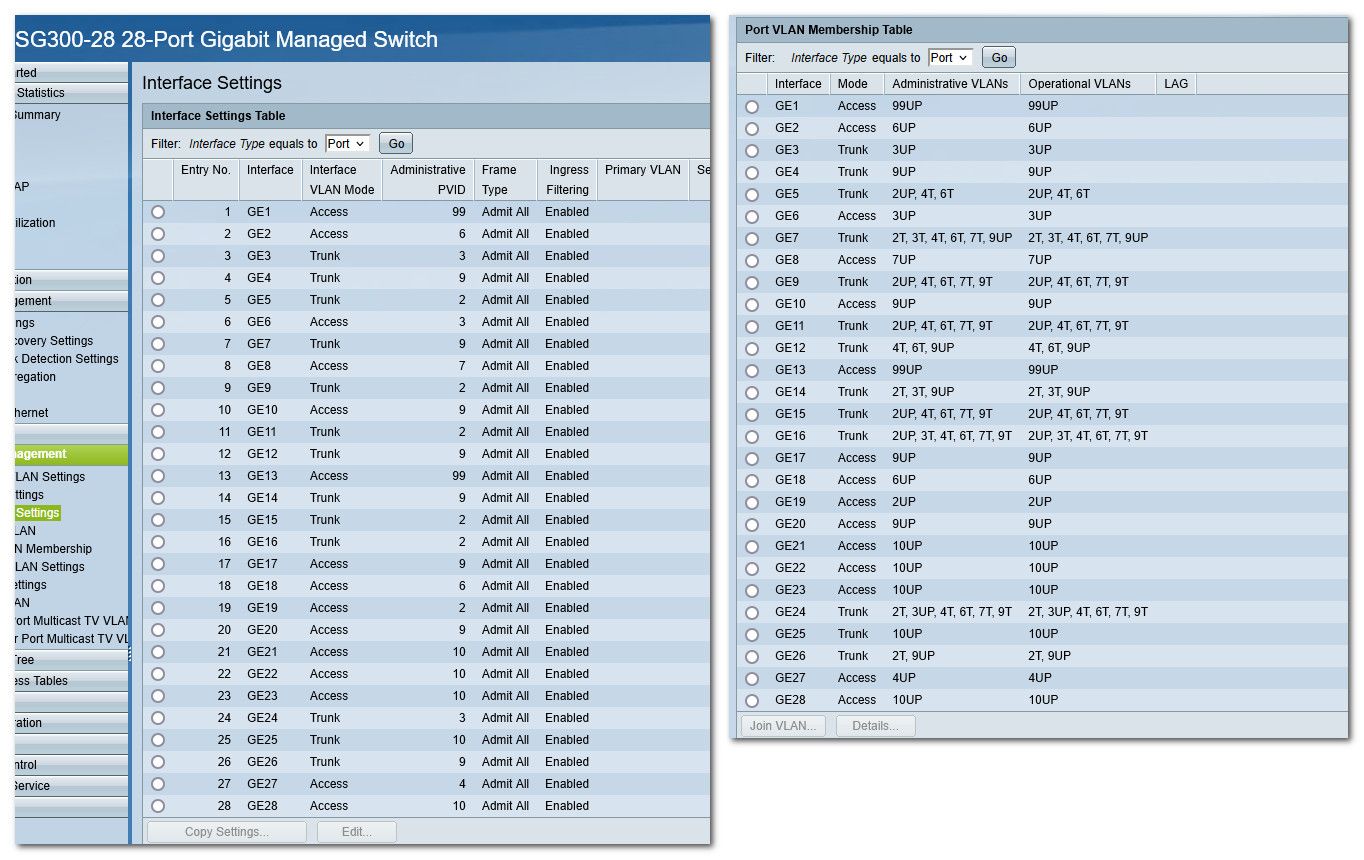
sg300-28#sho vlan Created by: D-Default, S-Static, G-GVRP, R-Radius Assigned VLAN, V-Voice VLAN Vlan Name Tagged Ports UnTagged Ports Created by ---- ----------------- ------------------ ------------------ ---------------- 1 1 S 2 Wlan gi7,gi14,gi24,gi26 gi5,gi9,gi11, S gi15-16,gi19 3 DMZ gi7,gi14,gi16 gi3,gi6,gi24 S 4 W_PSK gi5,gi7,gi9, gi27 S gi11-12,gi15-16, gi24 6 W_Guest gi5,gi7,gi9, gi2,gi18 S gi11-12,gi15-16, gi24 7 W_Roku gi7,gi9,gi11, gi8 S gi15-16,gi24 9 9 gi9,gi11,gi15-16, gi4,gi7,gi10,gi12, D gi24 gi14,gi17,gi20, gi26,Po1-8 10 disabled gi21-23,gi25,gi28 S 99 wan gi1,gi13 S 172 transit S sg300-28#is your vlan 10 maybe disabled?
What does it show for pvid, I agree it should auto set to 10 when you set the port to access.
Do you have these tables in your gui - where you can see the pvid, and you that the vlan is operational, etc.
-
-
@cannondale Ok how would your untagged lan1 network even work with this setup.
Your pfsense is connected to port 1 right?
But you don't have vlan 1 on this port - so how is untagged traffic getting to pfsense you said you plugged into another port and got an IP on your lan network.
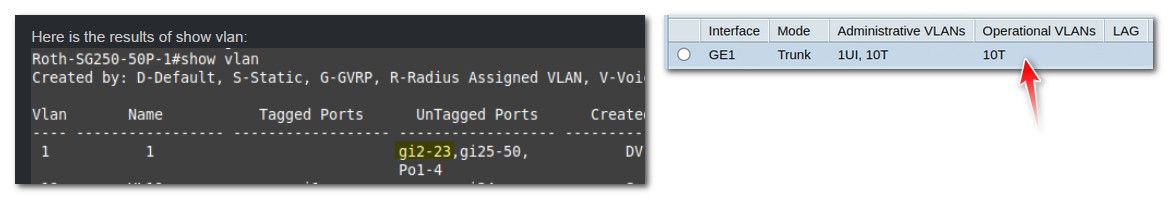
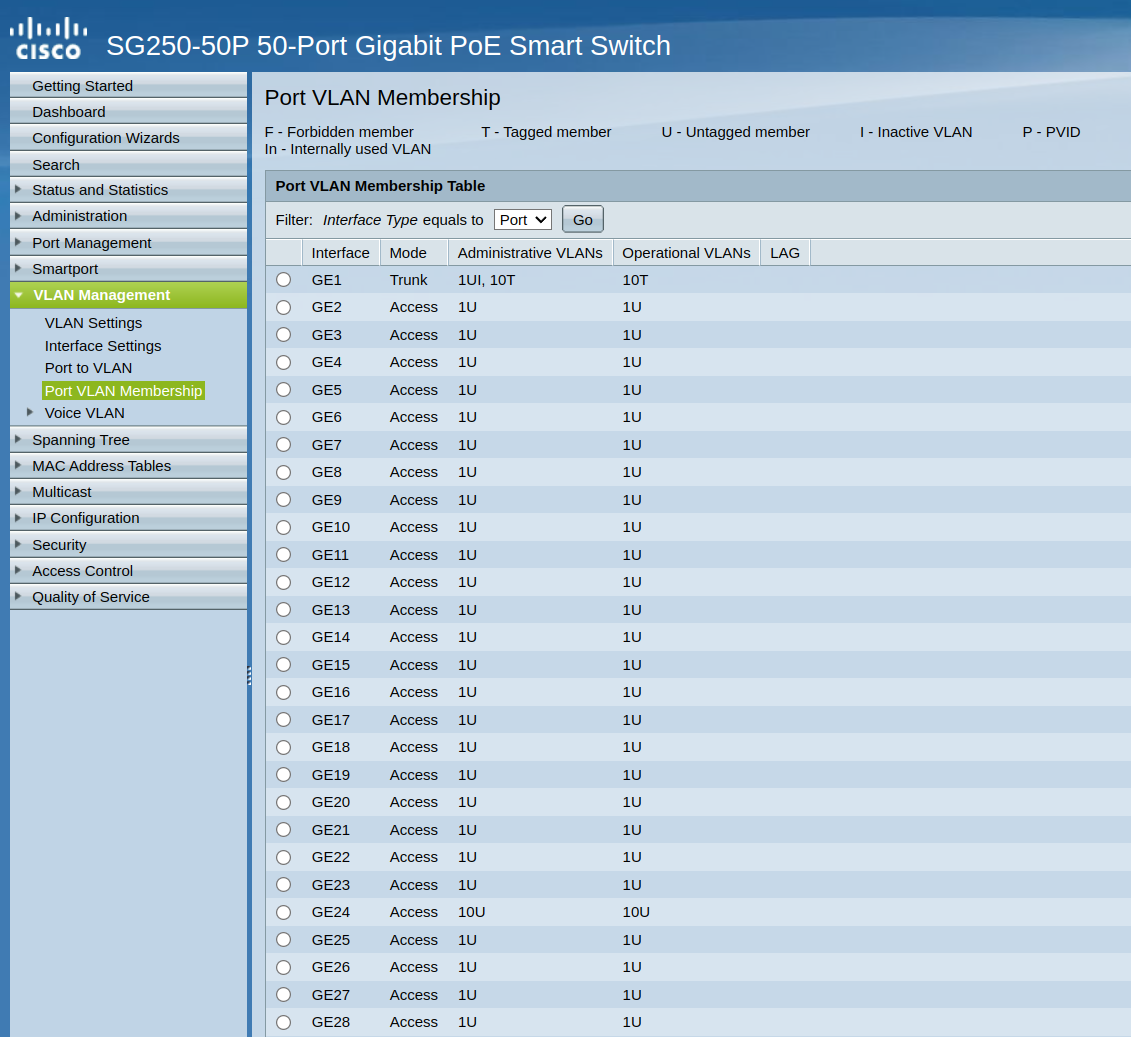
is that a UI, with the I meaning inactive..
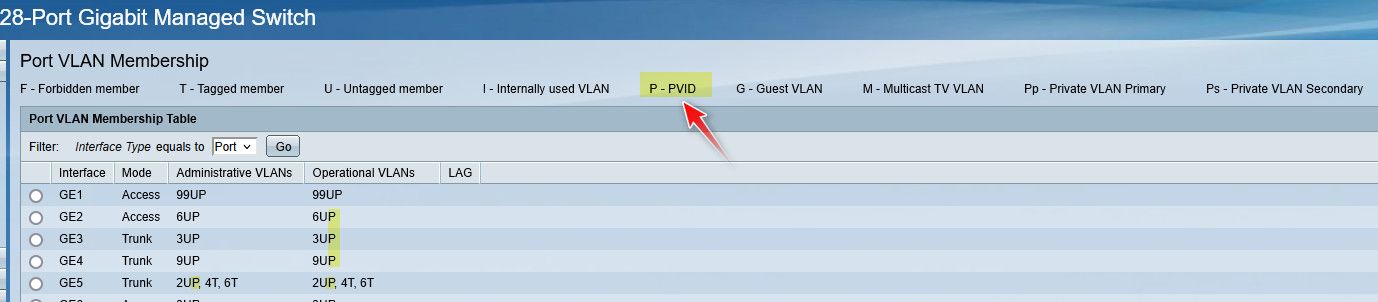
edit: also where is your pvid listing? Your table shows a P for PVID, but your output doesn't show any - see how mine marks what the pvid
-
Yes pfSense is connected to port 1 of the switch. There are many other machines/devices currently connected to this switch on LAN1 (igb1). All work as expected and have been for months. Only the newly created VLAN10 on port 24 does not work.
I plugged the workstation (connect to port 24 (VLAN10)) into another switch port and got an DHCP IP as a test to confirm that the workstation was requesting an IP from DHCP on LAN1 (igb1).@johnpoz said in No DHCP on pfSense VLAN with Cisco Smart Switch:
also where is your pvid listing? Your table shows a P for PVID
Not sure why the GUI does not show the PVID in the table on the membership page.
However, it does show PVID under the Customer Mode if I select port 24 and display the membership port details page: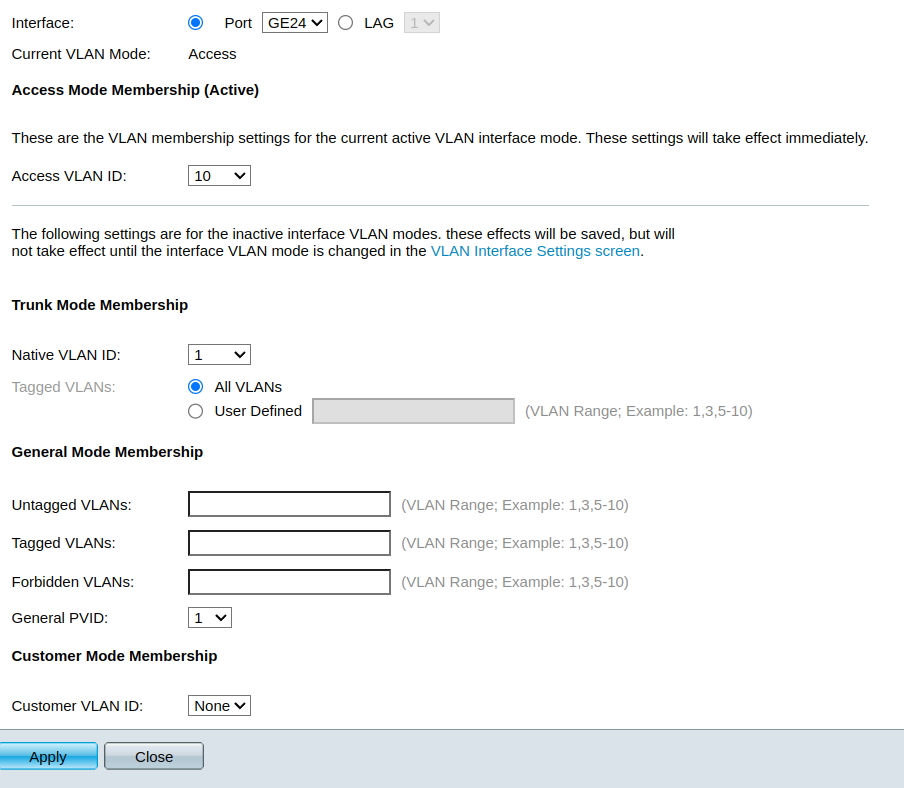
I suspect that the GUI displays the PVID in the membership table depending on the port mode but that's just a guess!
-
@johnpoz said in No DHCP on pfSense VLAN with Cisco Smart Switch:
is that a UI, with the I meaning inactive..
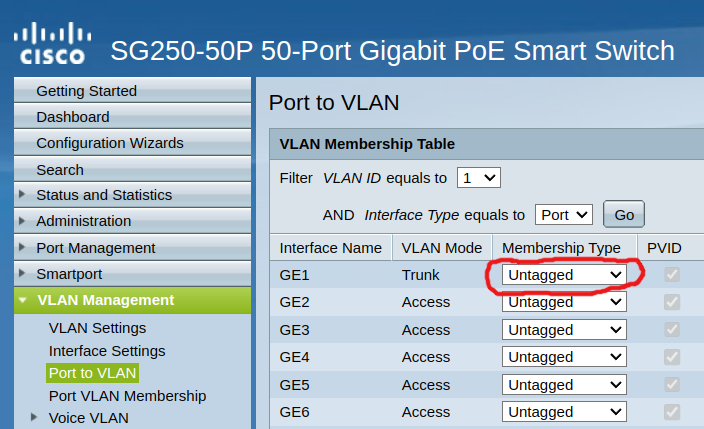
Regarding, the I meaning inactive for port 1, I went into the Port to Lan settings for port 1 and found it was set to "Excluded". I changed it to "Untagged" as I believe that is what it should be. Although it did make any difference. All LAN1 traffic works as expected and VLAN10 still does not.
-
@cannondale well one thing for sure - not a fan of what I have seen of the sg250 cli vs gui ;)
Your table legend clearly shows that P would be for the pvid, yet it doesn't show it in the table. From your table vlan 1 on your port 1 is inactive and not even listed as operational on that port, so how would it work?
Here is what my opinion sofar - something wrong in your switch.. This isn't complicated - native vlan (which is working) comes in untagged, with a trunk port your your other vlans you setup on the trunk would be tagged.
Traffic coming in on an access port in vlan X should go out any other ports in vlan X be tagged or untagged via the settings on the port... So when your client sends a discover broadcast into a access port in vlan 10, it should come out the port that is marked to be tagged vlan 10..
Are you running maybe dhcp snooping/guarding?
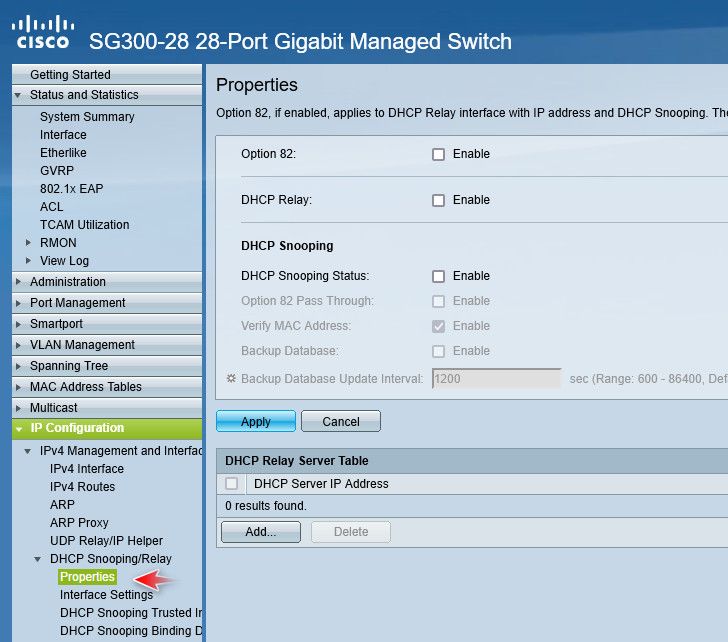
-
@johnpoz said in No DHCP on pfSense VLAN with Cisco Smart Switch:
Are you running maybe dhcp snooping/guarding?
This is not an option in the GUI:
-
@cannondale well I am at a loss.. Other than the inconsistencies about your pvid, and showing vlan 1 inactive on your port 1, but your saying it works.. this is pretty basic stuff.
I have never had any issues setting tagged and untagged vlans on any cisco switch ever worked on, or even any other cheap vlan switch or any other..
Its just tagged or untagged..
But from your sniff if pfsense never sees traffic come in tagged, then no its not going to work.
Maybe someone with a sg250 will chime in on something we are missing..
-
Thanks for all your help johnpoz! Not sure where to go from here but will wait for others to hopefully chime in as you suggest.
-
@cannondale I would think someone around here would have a sg250 - @stephenw10 and crazy amount of stuff in his lab, or @Derelict also..
I even looked if I could get one off amazon for reasonable price ;) I don't mind having switches to play with on my shelf.. I got netgear, dlink, even crappy tplink that had all kinds of issues with vlan, not being able to remove vlan 1 - but they finally fixed that.. And even a unifi flex mini, etc. But my main switches are sg300, a 28 and 10 port..
With work have used pretty much every enterprise/smb switch under the sun and have never seen such an issue..
Trunk with native untagged vlan and then tagged vlan, device in on port untagged.. Its pretty basic stuff - so missing something stupid.. Does the port 24 work if you just set it back to vlan 1, maybe the port is bad?
-
I have created vlan 20 on switchport 22 as another test.
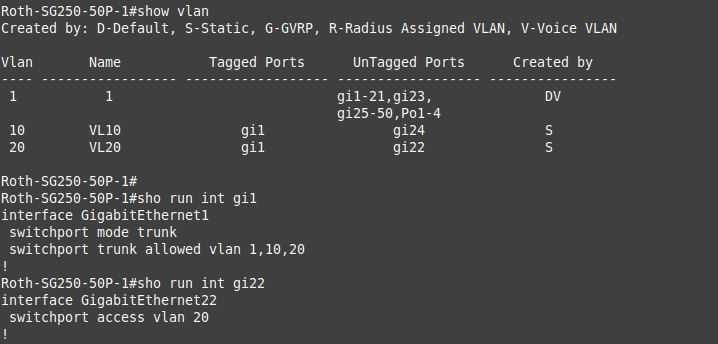
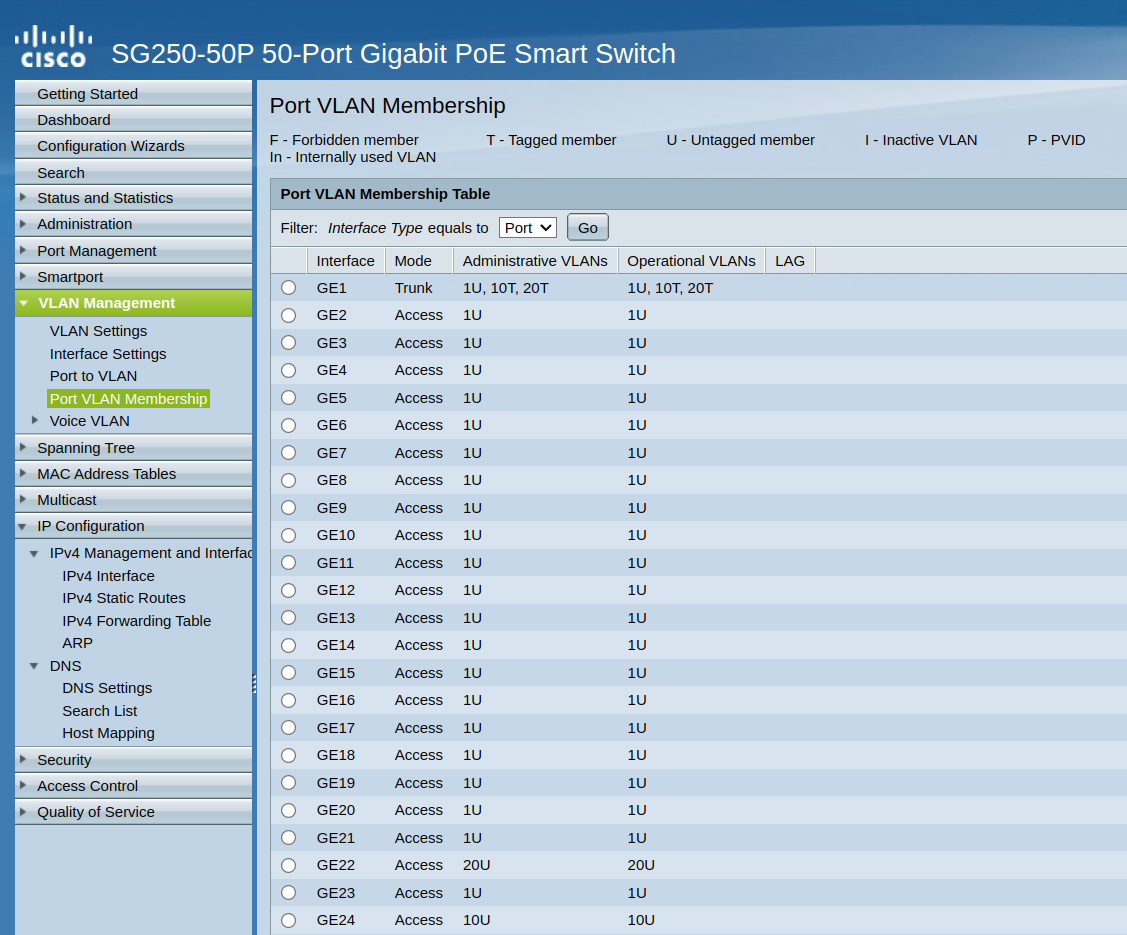
Do I need to add/configure VLAN20 in pfSense in order to run tcpdump?
-
@cannondale no you don't need to have it setup in pfsense to see the vlan tag with tcpdump -e
But now your port vlan membership looks better it doesn't have 1UI, still odd that it doesn't show the P for for which vlan is the pvid, even though it lists there at the top of the table in the legend that P would mean PVID.. so those 1U should show up as 1UP
-
Great! I'll give that a try.
@johnpoz said in No DHCP on pfSense VLAN with Cisco Smart Switch:
But now your port vlan membership looks better it doesn't have 1UI
I went into the Port to Lan settings for port 1 and found it was set to "Excluded". I changed it to "Untagged" earlier.
@johnpoz said in No DHCP on pfSense VLAN with Cisco Smart Switch:
still odd that it doesn't show the P for for which vlan is the pvid, even though it lists there at the top of the table in the legend that P would mean PVID.. so those 1U should show up as 1UP
Agreed! You would know better than me! Maybe a quirky Cisco thing! :)
I have only had this switch for about two months. I knew going in that Cisco UI's were a bit funky but it had the features that I was looking for!