Convert .crt to .pem TLS 1.3 helppp
-
I have a customer that is using Windows 11 22H2, and since this update he is no longer able to connect to WIFI due to Windows 11 22H2 new TLS 1.3 requirements.
I've been struggling with openssl to convert the .cer certificate to .pem TLS 1.3 to use it in freeradius but no joy so far.. Is this even possible?
We are using Lets Encrypt certificates generated by Acme package in pfsense.
Freeradius 3.0.26 running in a Ubuntu server Jammy 22.04. LTS.I found this workaround:
Create this registry key and deploy it via GPO would work according to this link:
https://community.ui.com/questions/Windows-11-Radius-Problem/6f96b52b-d6e7-43eb-a778-a34d527a9276HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\RasMan\PPP\EAP\13 Create DWORD key TlsVersion value FC0But it would be better to get the certificate right..
Any ideas?
Thanks. -
@mcury said in Convert .crt to .pem TLS 1.3 helppp:
We are using Lets Encrypt certificates generated by Acme package in pfsense.
Freeradius 3.0.26 running in a Ubuntu server Jammy 22.04. LTS.I would try out to set up samba and activate AD (active directory) and deploy all with GPOs or over a start script.
-
@mcury said in Convert .crt to .pem TLS 1.3 helppp:
But it would be better to get the certificate right..
The certificate has nothing to do with it.
-
@dobby_ said in Convert .crt to .pem TLS 1.3 helppp:
I would try out to set up samba and activate AD (active directory) and deploy all with GPOs or over a start script.
We are running samba-ad, users are member of the AD and freeradius is running unlang.
Only users that are member from wifi_users group can login. -
@johnpoz said in Convert .crt to .pem TLS 1.3 helppp:
The certificate has nothing to do with it.
Hello johnpoz,
It works for everyone but not Windows 11 22H2 users and according to what I have been reading, the reason is the TLS 1.3 requirement..
I was able to convert it to .p12 for Plex, but not to .pem -
@mcury said in Convert .crt to .pem TLS 1.3 helppp:
the reason is the TLS 1.3 requirement..
The cert has nothing to do with running tls 1.2 or 1.3.. you can run 1.1, 1.2 or 1.3 with the same cert.
Could have to do with cipher the client wants? You would have to look at the handshake to what is actually going wrong - the difficulty is that the tls part of the handshake is inside the encrypted eap tunnel.
-
@mcury said in Convert .crt to .pem TLS 1.3 helppp:
I was able to convert it to .p12 for Plex, but not to .pem
The certs you download from the cert manager would be pem, the format the cert is stored in is not the problem
-
@johnpoz said in Convert .crt to .pem TLS 1.3 helppp:
The certs you download from the cert manager would be pem, the format the cert is stored in is not the problem
hmm, I'll look into it, but as far as I know, freeradius requires a .pem file and Acme certificates are generated in .cer
For Plex, it was easy to convert to TLS 1.3
sudo openssl pkcs12 -export -out certificate.p12 -certpbe AES-256-CBC -keypbe AES-256-CBC -macalg SHA256 -inkey mykey.key -in mycert.cerNow I'm trying to understand the syntax, if it is possible, to convert to .pem like that..
-
@mcury you can just rename them .cer, .crt .pem are all pem files..
Looking in my acme folder I see pem files
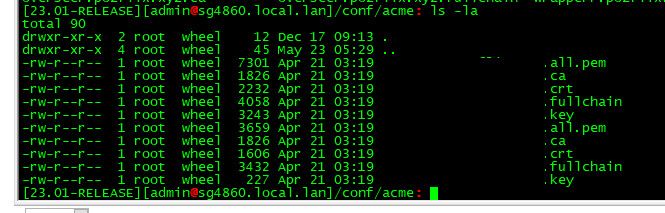
-
@johnpoz said in Convert .crt to .pem TLS 1.3 helppp:
you can just rename them .cer, .crt .pem are all pem files.
hm, I was doing like this:
openssl x509 -in mycert.cer -outform PEM -out mycert.pem openssl x509 -in ca.cer -outform PEM -out ca.pemThen, copy the .pem files along with the .key file to freeradius folder and restart the service.
It is a simple setup, EAP-TLS to freeradius, then samba use LDAP to check samba LDAP-groups.
Both are running in the same server.. freeradius just check 127.0.0.1:389 for groups, no need for LDAPSIt has been working flawless for a long time.. The problem began when users updated to Windows 11 22H2..
-
@johnpoz said in Convert .crt to .pem TLS 1.3 helppp:
Looking in my acme folder I see pem files
hmmm, weird.. these are the files I copied from /tmp folder in pfsense once the certs were generated:
~/certs$ ls -lah total 44K drwxr-xr-x 3 root root 4.0K Apr 5 20:09 . drwxr-xr-x 8 pi pi 4.0K May 19 21:23 .. -rw-r--r-- 1 root root 3.7K Apr 5 20:07 ca.cer -rw-r--r-- 1 root root 5.6K Apr 5 20:07 fullchain.cer -rw-r--r-- 1 root root 1.9K Apr 5 20:07 mycert.cer -rw-r--r-- 1 root root 826 Apr 5 20:07 mycert.conf -rw-r--r-- 1 root root 1.1K Apr 5 20:07 mycert.csr -rw-r--r-- 1 root root 220 Apr 5 20:07 mycert.csr.conf -rw------- 1 root root 1.7K Apr 5 20:07 mykey.keyEdit:
Did you tick that option "Write Certificates" ?