Frequency of security updates
-
AFAIK there are no critical issues remaining in any current versions of pfSense. This is why we are jumping from v2.6.0 straight to v2.7.0.
In the past, when critical CVE gets patched, version number gets updated as well. For example. We had pfSense v2.5.1 and v2.5.2 before major release of pfSense v2.6.0.
-
@michmoor said in Frequency of security updates:
So for pfsense which CVE do you think is problematic and why?
None in particular. I was merely trying to get a sense of how often pfSense gets updated. I did not really know that since June there haven’t been any CVEs discovered in pfSense.
-
@dominikhoffmann I have the same question since I see my pfSense CE 2.6.0 was released 1 year ago on Jan 31, 2022 and there have been 3 releases of pfSense Plus (23.0, 22.05.1, 22.05) in that time period [corresponding to May 2022 and January 2023).
-
@joshgreyz 23.01 isn't out yet so if you're going to count that, you might as well count 2.7.
 It'll be out shortly afterward.
It'll be out shortly afterward.23.01 does have release notes which don't mention new security updates.
There is also https://www.netgate.com/security showing the last announced issue was over a year ago.
-
This post is deleted! -
@joshgreyz: Are you aware of the ability to upgrade your Community Edition to pfSense+?
-
@DominikHoffmann that doesn't negate the fact the CE has practicly been abandoned -- there's a new plus release 23.05 which just got released and crickets when it comes to CE 2.7.0...
-
@joshgreyz When the split was announced I suspected this would happen.
I believe the intent was to keep CE and + more or less equally updated with a divergence in "advanced" features. At the time I guessed that the cost would make the CE updates occur slower over time.
I made the move to Netgate HW, in my case I got a deal on used HW. -
@AndyRH Netgate maintains this list of security advisories against pfSense and we see that since CE 2.6.0 was released more than a year ago on Jan 31, 2022, that the following known security issues still exist in CE 2.6.0:
Advisory Name
Announced
Last Updated
pfSense-SA-23_07.kernel
2023-05-11
pfSense-SA-23_06.webgui
2023-05-11
pfSense-SA-23_05.sshguard
2023-02-15
pfSense-SA-23_04.webgui
2023-02-15
pfSense-SA-23_03.webgui
2023-02-15
pfSense-SA-23_02.webgui
2023-02-15
pfSense-SA-23_01.webgui
2023-02-15
pfSense-SA-22_05.webgui
2023-02-15
pfSense-SA-22_04.webgui
2022-01-25
2022-03-08
pfSense-SA-22_03.webgui
2022-01-13
2022-03-08
pfSense-SA-22_02.webgui
2022-01-12
2022-03-08
pfSense-SA-22_01.webgui
2022-01-12
2022-03-08
pfSense-SA-21_02.captiveportal
2021-04-22
2022-03-08
*** This is very concerning ***
-
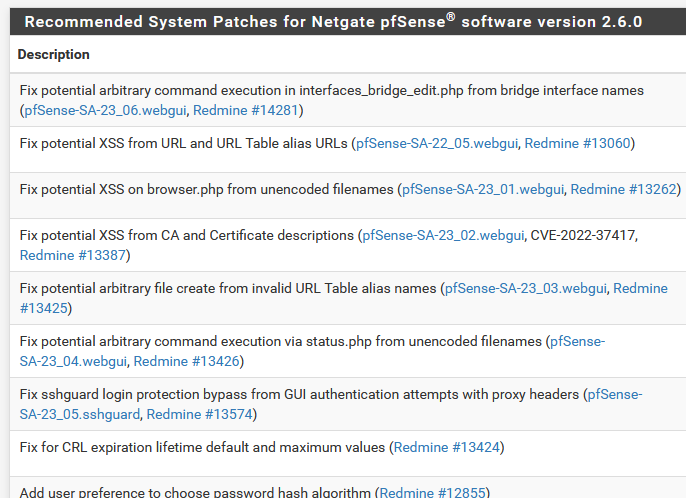
@joshgreyz Patches that apply to 2.6 are available via the System Patches package.
https://docs.netgate.com/pfsense/en/latest/releases/23-05.html#security
-
For the system (OS) FreeBSD
- it comes from the FreeBSD team
fixes and updates or upgrades
For the pfSense itself there will be more options;
- pfSense-upgrade or option (13) in console
- pkg update or upgrade
for the entire pkg`s such snort, suricata,.... - Patch system inside of pfSense
Recommended or custom patches option - Package maintainers can fix something
Available over the pkg system (updates)
What more is needed or flat Who is offering
more options? Or otherwise wich options are
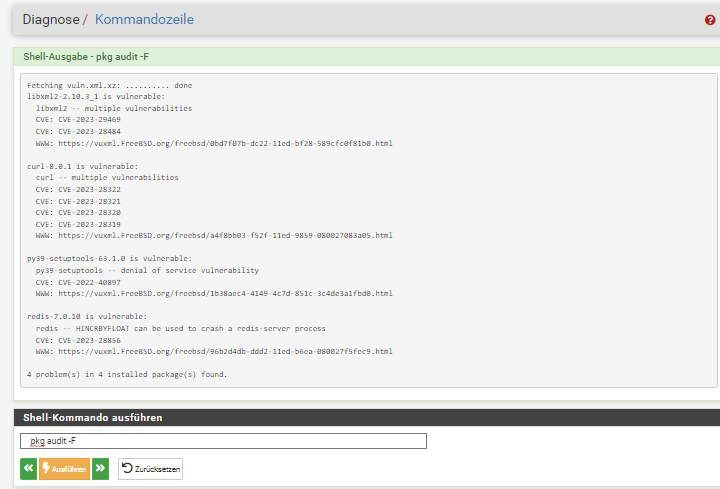
beloved to see or have here on top?pfSense 23.05 release (latest)
pfSense 2.7 Devel (latest)
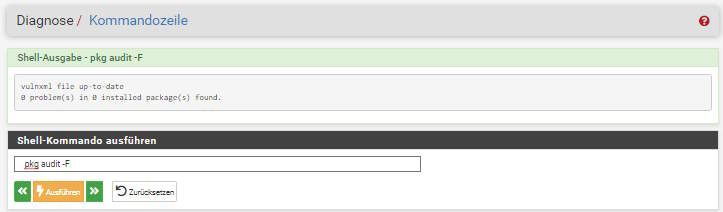
You see in 2.6 CE much patches are available and also recommended, but in 2.7 not anymore, because they are fleeting in that code of the
new 2.7 CE version.In 23.05 Release where things also solved out
and during the installation it was also updating / upgrading the squid & SquidGuard package I
was reading something about, automatically!And by side it is not really a point to find a vuln.
anywhere inside, it must be also able to use in the
used or installed software and does then also affect things or functions where it can be used.
This is not even present and able to use for others
and the software. For sure it may be also a thing
how things will be implemented, but if I personally trust not the coder of my firewall software, who should I trust then? And this is
the other point on the other end of the line. - it comes from the FreeBSD team