freeradius / eap-tls / Android 13
-
Hi,
got excellent help the other day getting the above to work on an ancient Android 7 tablet. But, since I really would like to use WPA3-Enterprise I got myself a new tablet, running Android 13, only to realize it needs some different configuration...
I think I tested this by creating a new SSID, setting it up for the working WPA2-Enterprise profile, and then tried to connect with the new tablet, which it utterly refused;
Using the same SSID with my old tablet, connects right away.
I have tried to google for a solution, and there does not seem to be much available, just using plain Android. I have tried creating a bundled cert with my CA and CERT, which I didn't have any great success with either.
Has anyone figured out what changes are needed to make this work?
Thanks
-
@furom On my android tablet I had to install the ca cert on its own.
-
@johnpoz said in freeradius / eap-tls / Android 13:
@furom On my android tablet I had to install the ca cert on its own.
Thanks, I believe I did try that first of all, but will have another go... Same certificate config as before I suppose?
-
@furom Yeah pretty sure went over the config of my tablet in that other thread. I am using wpa3 enterprise.
-
@johnpoz said in freeradius / eap-tls / Android 13:
@furom Yeah pretty sure went over the config of my tablet in that other thread. I am using wpa3 enterprise.
Config is the part that is entirely clear now thanks to you. Now its most likely differences in Android versions creating some woes. Some seems to have issues already on Android 11, but most >11
-
@furom Yep. It just won't do it with the same cert-config and installing CA and CERT separately
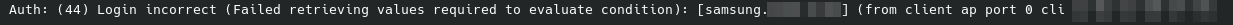
Auth: (63) Login incorrect (Failed retrieving values required to evaluate condition)I installed both certs as 'wifi" certs too
-
@furom did you remember to create your freerad user?
-
@johnpoz said in freeradius / eap-tls / Android 13:
@furom did you remember to create your freerad user?
I did, and everything else is the same as from before (and no pwd), and just verified I indeed used the new user to successfully connect the old tablet to the new SSID (on WPA2-Enterprise)...
Edit: If anyone gets what the issue might be it would be highly appreciated. I've been googling the "whole" internet almost, and nowhere is a working setup of WPA[2|3]-Enterprise using EAP-TLS for Android 13 to be found. Can this really be?
-
@furom hmmm I was just able to duplicate your issue
(15) Login incorrect (Failed retrieving values required to evaluate condition): [tablet.home.arpa/<via Auth-Type = eap>] (from client uap-pro port 0 cli 04-34-F6-AA-02-D9) 192.168.2.2 Auth-Type: eapIf I set require online certificate status - this is checking for ocsp, ie has your cert cert been revoked - did you set that up... I never do - these are stuff that only will be used local, and issued and maintained by me.. If for some reason I heed to change then - I will know about it that is for sure ;)
I don't think you can set that up in pfsense cert manager, you can create your own internal revoke list that pfsense would use, etc. But you can not be added, atleast not directly in the gui I don't think..
Example if you look at some external CA, say ones for acme lets encrypt that is most likely in your CAs in cert manager if your using acme.. Shows.
[1]CRL Distribution Point Distribution Point Name: Full Name: URL=http://x1.c.lencr.org/But when used to access wireless - how would the device even check this for the server until its already been connected, etc. You should just set that to not to check.
-
@johnpoz said in freeradius / eap-tls / Android 13:
@furom hmmm I was just able to duplicate your issue
(15) Login incorrect (Failed retrieving values required to evaluate condition): [tablet.home.arpa/<via Auth-Type = eap>] (from client uap-pro port 0 cli 04-34-F6-AA-02-D9) 192.168.2.2 Auth-Type: eapIf I set require online certificate status - this is checking for ocsp, ie has your cert cert been revoked - did you set that up... I never do - these are stuff that only will be used local, and issued and maintained by me.. If for some reason I heed to change then - I will know about it that is for sure ;)
No, for the same reasons I never do either...
I don't think you can set that up in pfsense cert manager, you can create your own internal revoke list that pfsense would use, etc. But you can not be added, atleast not directly in the gui I don't think..
Example if you look at some external CA, say ones for acme lets encrypt that is most likely in your CAs in cert manager if your using acme.. Shows.
[1]CRL Distribution Point Distribution Point Name: Full Name: URL=http://x1.c.lencr.org/But when used to access wireless - how would the device even check this for the server until its already been connected, etc. You should just set that to not to check.
Well, sure, the error is identical, but were you not able to connect, if this revocation list is deselected? I can't, no matter what I try it seems. Android 13 was not a lucky number for this configuration at least... :)
-
@furom if I set that to required no it doesn't connect, if I set it to not connect I get in. I also did some other testing like not providing my cert, and typo on the identity and then fail to connect.
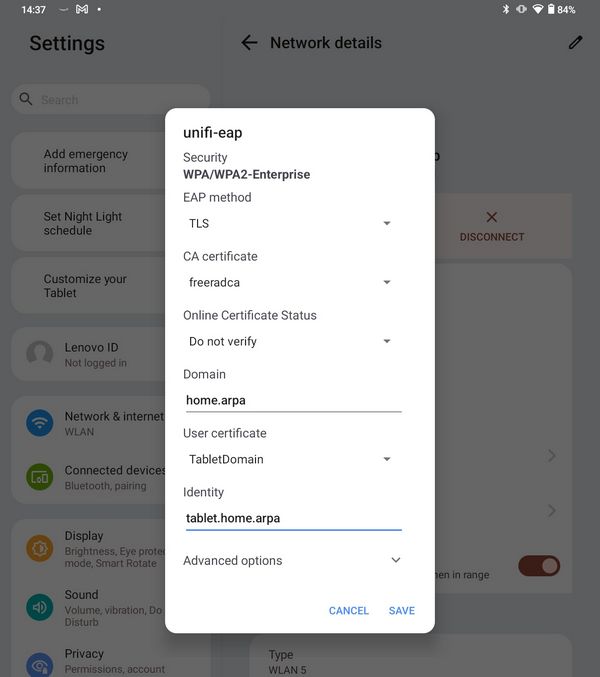
It says wpa/wpa2-enterprise - but my unifi is set for wpa3-enterprise only.. So clearly its using wpa3-enterprise. I not sure how I can get such details, not like my iphone where it says wpa3-enterprise when I install the developers profile for diagnostics..
-
@johnpoz said in freeradius / eap-tls / Android 13:
@furom if I set that to required no it doesn't connect, if I set it to not connect I get in. I also did some other testing like not providing my cert, and typo on the identity and then fail to connect.

It says wpa/wpa2-enterprise - but my unifi is set for wpa3-enterprise only.. So clearly its using wpa3-enterprise. I not sure how I can get such details, not like my iphone where it says wpa3-enterprise when I install the developers profile for diagnostics..
Yeah, this is identical to what I do, or try to... Only thing that differs is the Android version, right? I suppose it's not easy to downgrade a tablet... I believe I bought a paper-weight. Of all things to expect, this was not exactly it... but my fault not checking in advance the only thing I cared about actually worked... lol But there's always a next time...

-
@furom how exactly do you have your unifi setup for wpa3-enterprise? You didn't click on the 192 did you, our APs do not support that.
Your saying it works with wpa2-enteprise? What about wpa3-personal?
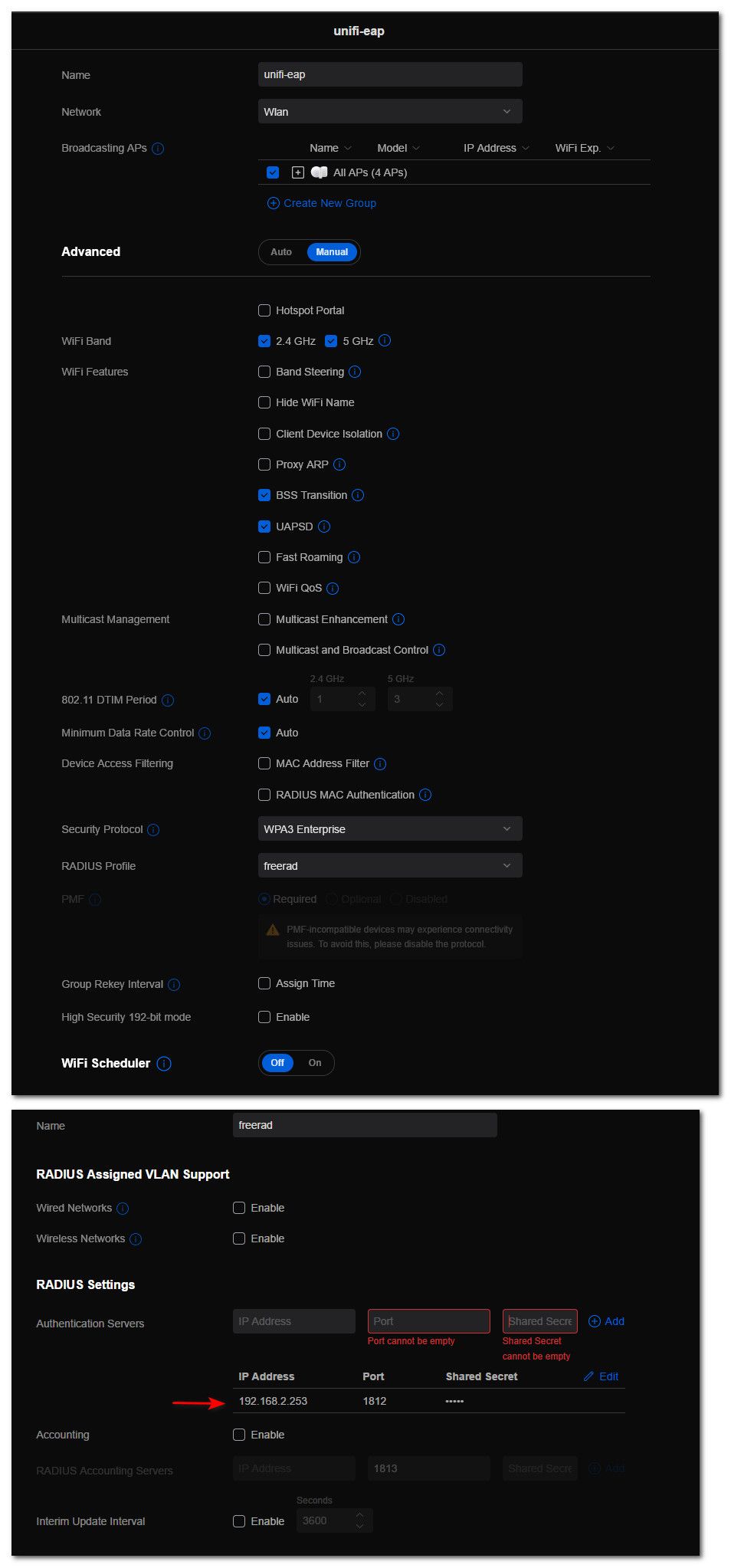
you updated your firmware on your AP right? What controller version are you running?
-
@johnpoz said in freeradius / eap-tls / Android 13:
@furom how exactly do you have your unifi setup for wpa3-enterprise?
It is identical to what you have posted, I wanted to make sure no mistakes due to non-working options
You didn't click on the 192 did you, our APs do not support that.
I did at first, but as that didn't work, didn't include that in what I was trying with later on
Your saying it works with wpa2-enteprise?
No, the new tablet does not work with any WPAx-Enterprise.
What about wpa3-personal?
WPA3-Personal connects and works. Hadn't tried that until now, but supposedly better than any of the non-working alternatives... Strange EAP-TLS still refuse though
you updated your firmware on your AP right? What controller version are you running?
Yes, I have upgraded the AP, now running on 6.5.54.14746
-
@furom well if me, what I would do to try and glean some insight to what exactly is failing..
I would do a killall radiusd
then start it in debug mode with
radiusd -X
Then try your auth - you will be flooded with info.. just a small snip of my tablet authing
(4) TLS-Session-Information = "(TLS) recv TLS 1.2 Handshake, CertificateVerify" (4) TLS-Session-Information = "(TLS) recv TLS 1.2 Handshake, Finished" (4) TLS-Session-Information = "(TLS) send TLS 1.2 ChangeCipherSpec" (4) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, Finished" (4) TLS-Session-Cipher-Suite = "ECDHE-ECDSA-AES128-GCM-SHA256" (4) TLS-Session-Version = "TLS 1.2" (4) Sent Access-Challenge Id 24 from 192.168.2.253:1812 to 192.168.2.4:33751 length 119 (4) EAP-Message = 0x0187003d0d800000003314030300010116030300282a3c2d8e314713ca963244f76526de3b14e6c288b234f0f7c6bd662fda640482f8cbd79a8fc0bf63 (4) Message-Authenticator = 0x00000000000000000000000000000000 (4) State = 0x8f9121a78b162c3e188eee1434fd9653 (4) Finished request Waking up in 4.8 seconds. (5) Received Access-Request Id 25 from 192.168.2.4:33751 to 192.168.2.253:1812 length 251 (5) User-Name = "tablet.home.arpa" (5) NAS-IP-Address = 192.168.2.4 (5) NAS-Identifier = "1618d6c21f6b" (5) Called-Station-Id = "16-18-D6-C2-1F-6B:unifi-eap" (5) NAS-Port-Type = Wireless-802.11 (5) Service-Type = Framed-User (5) Calling-Station-Id = "04-34-F6-AA-02-D9" (5) Connect-Info = "CONNECT 0Mbps 802.11b" (5) Acct-Session-Id = "CF1EEF7980492BF6" (5) Acct-Multi-Session-Id = "80BA7EF3E58094C1" (5) WLAN-Pairwise-Cipher = 1027076 (5) WLAN-Group-Cipher = 1027076 (5) WLAN-AKM-Suite = 1027077 (5) WLAN-Group-Mgmt-Cipher = 1027078 (5) Framed-MTU = 1400 (5) EAP-Message = 0x028700060d00 (5) State = 0x8f9121a78b162c3e188eee1434fd9653 (5) Message-Authenticator = 0xe0ac3128b8fedaa1ac89444320ac40c9 (5) Restoring &session-state (5) &session-state:Framed-MTU = 994 (5) &session-state:TLS-Session-Information = "(TLS) recv TLS 1.3 Handshake, ClientHello" (5) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHello" (5) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, Certificate"You may need to reboot your AP if your not seeing any info - seems the AP caches some of the info or something..
-
@johnpoz said in freeradius / eap-tls / Android 13:
@furom well if me, what I would do to try and glean some insight to what exactly is failing..
I would do a killall radiusd
then start it in debug mode with
radiusd -X
Then try your auth - you will be flooded with info.. just a small snip of my tablet authing
You may need to reboot your AP if your not seeing any info - seems the AP caches some of the info or something..
This sounds like fun! :) I'll give it a go. I just tried EAP-PEAP and TTLS, neither worked so this will perhaps reveal something interesting... I have read that later Android handled CA's differently and won't trust anything easily, which probably is a good thing for the most part...
Edit: Omg... Well, you weren't kidding about barfing a lot of data... Saw several errors swoshing by, will look for them now
-
@furom It looks like this should contain the interesting error
(4) ERROR: Failed retrieving values required to evaluate condition (4) [expiration] = noop (4) [logintime] = noop (4) pap: WARNING: Auth-Type already set. Not setting to PAP (4) [pap] = noop (4) } # authorize = updated (4) Found Auth-Type = eap (4) # Executing group from file /usr/local/etc/raddb/sites-enabled/default (4) authenticate { (4) eap: Expiring EAP session with state 0x4c94f6214f91fbc3 (4) eap: Finished EAP session with state 0x4c94f6214f91fbc3 (4) eap: Previous EAP request found for state 0x4c94f6214f91fbc3, released from the list (4) eap: Peer sent packet with method EAP TLS (13) (4) eap: Calling submodule eap_tls to process data (4) eap_tls: (TLS) EAP Done initial handshake (4) eap_tls: (TLS) recv TLS 1.2 Alert, fatal internal_error (4) eap_tls: ERROR: (TLS) Alert read:fatal:internal error (4) eap_tls: (TLS) Server : Need to read more data: error (4) eap_tls: ERROR: (TLS) Failed reading from OpenSSL: error:14094438:SSL routines:ssl3_read_bytes:tlsv1 alert internal error (4) eap_tls: (TLS) In Handshake Phase (4) eap_tls: (TLS) Application data. (4) eap_tls: ERROR: (TLS) Cannot continue, as the peer is misbehaving. (4) eap_tls: ERROR: [eaptls process] = fail (4) eap: ERROR: Failed continuing EAP TLS (13) session. EAP sub-module failed (4) eap: Sending EAP Failure (code 4) ID 5 length 4 (4) eap: Failed in EAP select (4) [eap] = invalid (4) } # authenticate = invalid (4) Failed to authenticate the user (4) Using Post-Auth-Type Reject (4) # Executing group from file /usr/local/etc/raddb/sites-enabled/default (4) Post-Auth-Type REJECT { (4) attr_filter.access_reject: EXPAND %{User-Name}The top 4 rows repeat a few times without the other errors. Interestingly, it says that it needs to 'read more data', and the first error reads like this
(1) ERROR: Failed retrieving values required to evaluate condition (1) [expiration] = noop (1) [logintime] = noop (1) pap: WARNING: Auth-Type already set. Not setting to PAP (1) [pap] = noop (1) } # authorize = updated (1) Found Auth-Type = eap (1) # Executing group from file /usr/local/etc/raddb/sites-enabled/default (1) authenticate { (1) eap: Expiring EAP session with state 0x4c94f6214c96fbc3 (1) eap: Finished EAP session with state 0x4c94f6214c96fbc3 (1) eap: Previous EAP request found for state 0x4c94f6214c96fbc3, released from the list (1) eap: Peer sent packet with method EAP TLS (13) (1) eap: Calling submodule eap_tls to process data (1) eap_tls: (TLS) EAP Got final fragment (131 bytes) (1) eap_tls: WARNING: (TLS) EAP Total received record fragments (131 bytes), does not equal expected expected data length (0 bytes)So something is going on here...
-
@furom said in freeradius / eap-tls / Android 13:
(4) eap_tls: (TLS) EAP Done initial handshake
(4) eap_tls: (TLS) recv TLS 1.2 Alert, fatal internal_error
(4) eap_tls: ERROR: (TLS) Alert read:fatal:internal error
(4) eap_tls: (TLS) Server : Need to read more data: error
(4) eap_tls: ERROR: (TLS) Failed reading from OpenSSL: error:14094438:SSL routines:ssl3_read_bytes:tlsv1 alert internal error
(4) eap_tls: (TLS) In Handshake Phase
(4) eap_tls: (TLS) Application data.
(4) eap_tls: ERROR: (TLS) Cannot continue, as the peer is misbehaving.Well that for sure would explain why your eap-tls is not working... But your saying you got your old tablet working.. Are you not using the same certs that you used for server and same CA?
So something wrong with the client cert, or how the client is sending it? Or just how the client does the handshake?
edit: My son has a android phone - not sure when he will be over next... We might be doing some sort of bbq on monday, so if so I will try to get his phone connected, not sure what its running.. But I do know it is an android device.
-
@johnpoz said in freeradius / eap-tls / Android 13:
@furom said in freeradius / eap-tls / Android 13:
(4) eap_tls: (TLS) EAP Done initial handshake
(4) eap_tls: (TLS) recv TLS 1.2 Alert, fatal internal_error
(4) eap_tls: ERROR: (TLS) Alert read:fatal:internal error
(4) eap_tls: (TLS) Server : Need to read more data: error
(4) eap_tls: ERROR: (TLS) Failed reading from OpenSSL: error:14094438:SSL routines:ssl3_read_bytes:tlsv1 alert internal error
(4) eap_tls: (TLS) In Handshake Phase
(4) eap_tls: (TLS) Application data.
(4) eap_tls: ERROR: (TLS) Cannot continue, as the peer is misbehaving.Well that for sure would explain why your eap-tls is not working... But your saying you got your old tablet working.. Are you not using the same certs that you used for server and same CA?
So something wrong with the client cert, or how the client is sending it?
Glad to hear it makes some sense at least. Not looking great, so much I do understand... :)
No, I created a second cert for the new tablet as I may want them both still...
I now copied the cert I used on the old tablet (working with WPA2-Enterprise/eap-tls/Android 7) to the new one, and errors are identical
-
@furom Perhaps a fragmentation problem ?
Try to edit eap.conf and set fragment_size = 1344A nanoHD and a unifi6-lite only worked with wpa2-enterprise after doing this change.