PFSENSE + IPSEC + NAT
-
Hi:
I wrote in the IPSEC section yesterday but I'm not sure if my problem should be asked here as a possible NAT problem. I copy the text:
We have a network with different subnets:
10.0.0.0/23 Main
10.0.2.0/25 Subnet
10.0.3.0/24 Subnet
10.0.4.0/27 Subnet
10.0.5.0/26 Subnet
10.0.X.0/24 SubnetWe also have an IPSEC connection to provide mutual services (WEB and DNS) of which I have no control at the other end. The services of both have the 172.19.0.0/24 network as their origin and destination.
In the PFSENSE (in high availability) I have a VIRTUAL IP 172.19.0.1 which is the gateway for the IPSEC tunnel.
Currently I have the IPSEC tunnel working correctly but I have a router with addresses 172.19.0.5 and 10.0.0.5 doing NAT from networks 10.0.0.0 to network 172.19.0.0/24 to be able to send the traffic through the IPSEC tunnel (access to networks 172.19.10.0/24. 172.19.11.0/24, ...)I have done numerous tests to try to NAT the traffic from networks 10.0.X.0 to 172.19.0.1 and thus send through the IPSEC tunnel but I can't. The tests carried out are:
- Configure Outbound NAT to the IPSec interface
- Configure Outbound NAT to the network interface 172.19.0.1 (CARP IP)
- Configure Outbound NAT to the network interface 172.19.0.2 (IP PFSense)
- Create another Virtual IP and use it for Outbound NAT.
Thanks for the help.
-
@Abelardo-A-M said in PFSENSE + IPSEC + NAT:
I wrote in the IPSEC section yesterday but I'm not sure if my problem should be asked here
Yes it should. pfSense cannot do NAT on IPSec traffic, at least not on policy based tunnels.
But it's not clear, which tunnel mode you're using and to where you have assigned the mentioned subnets. Maybe you can provide a network map.
-
@viragomann, thank you for the answer.
The network can be summarized in: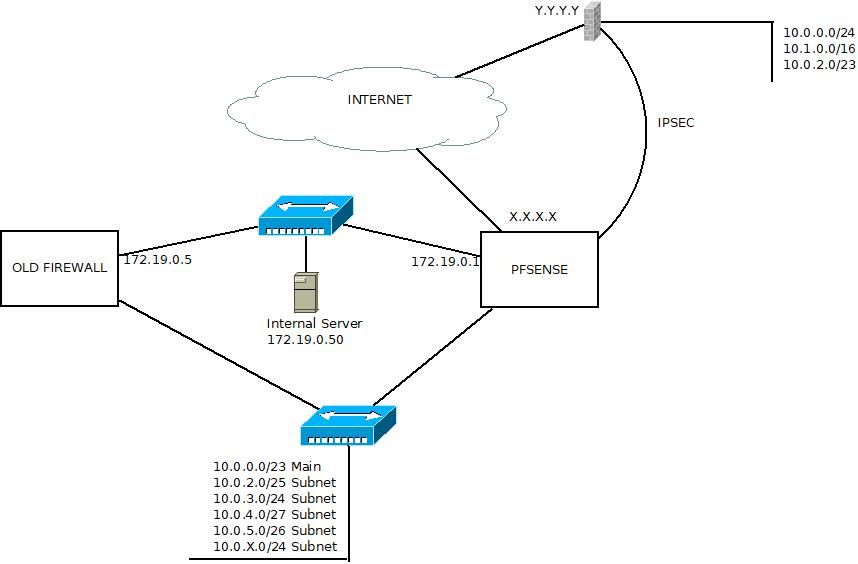
The ipsec configuration mode is "IPv4 Tunnel" and phase 2, only change Remote Network, are similar to:
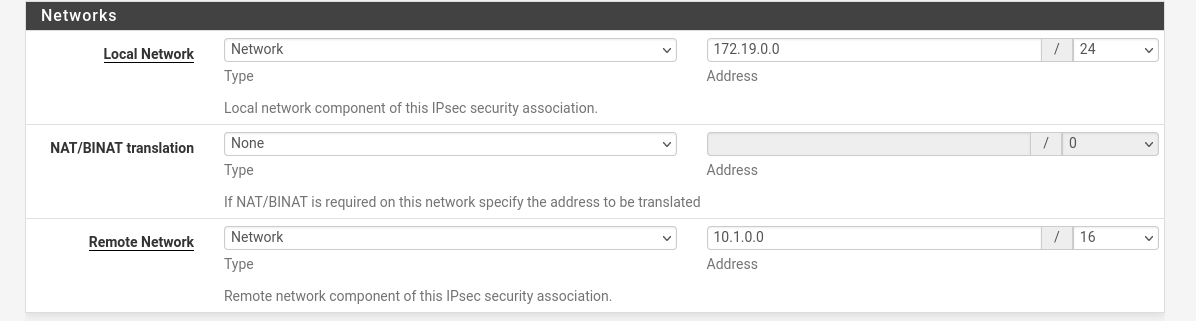
Thanks you.
-
A Abelardo A.M. referenced this topic on
-
@Abelardo-A-M said in PFSENSE + IPSEC + NAT:
We also have an IPSEC connection to provide mutual services (WEB and DNS) of which I have no control at the other end.
To which networks do these services belong to?
You have some overlapping subnets. If you need to connect all with all, it cannot be done with a /24 local network in the phase 2.
Changes would be needed to do at both sites.So which networks / IPs do you need to connect?
The services of both have the 172.19.0.0/24 network as their origin and destination.
The diagram show the 172.19.0.0/24 only on one site.
but I have a router with addresses 172.19.0.5 and 10.0.0.5 doing NAT from networks 10.0.0.0 to network 172.19.0.0/24 to be able to send the traffic
I assume, you want to get rid of this now?
through the IPSEC tunnel (access to networks 172.19.10.0/24. 172.19.11.0/24, ...)
Cannot see these subnets in the drawing.
-
@viragomann,Sorry, I made a mistake in writing the text and layout by changing the original configuration to a dummy one. I send them corrected.
-
Local networks:
Range 10.0.0.0/x -
Networks reachable by IPSEC:
Range 192.168.0.0/16 -
Network through which IPSEC is accessed:
Range 172.19.0.0/24 -
IP used in the range 172.19.0.0/24
pfSense Ip 172.19.0.1/24
Internal server 172.19.0.50/24
Old firewall doing NAT to IPSEC and I want to remove 172.19.0.5/24
Also in the pfSense configuration in phase 2, the correct remote network would be networks in the range 192.168../x
In the old firewall there is a redirection of ports 80 and 443 to another server in the range 10.0.0.0/x and I would like to know if pfSense could have a Virtual IP in the range 172.19.0.0./24 and do that redirection . The purpose of all this is to remove the old firewall.
Perhaps the simplest solution is to mount a hardware that makes the IPSEC tunnel and the routed by pfsense.
Thanks for the help
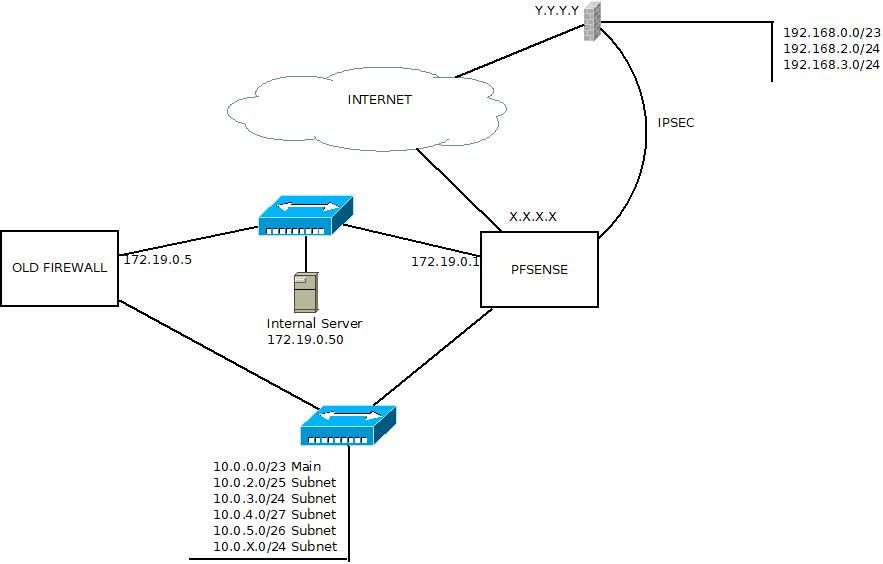
-
-
@Abelardo-A-M
In the phase 2 enter your local network, so 10.0.0.0/16At NAT/BINAT translation select Network and enter 172.19.0.0/24.
Remove all IPs out of 172.19.0.0/24, even the virtual from pfSense.
In the old firewall there is a redirection of ports 80 and 443 to another server in the range 10.0.0.0/x and I would like to know if pfSense could have a Virtual IP in the range 172.19.0.0./24 and do that redirection .
I never did this, but it should be possible with a simple NAT port forwarding rule on the IPSec interface.
-
@viragomann Thanks you for the answer.
I have never tried the solution you indicate because the pfSense documentation says:
NAT+IPsec cannot be configured between two different sized subnets (e.g. It cannot NAT a /24 subnet to a /27 subnet).
Another question is, if I remove the pfSense IPs on the 172.19.0.0/24 network, how does the 172.19.0.50 server route the packets to the IPSEC networks?
Thanks you.
-
@Abelardo-A-M said in PFSENSE + IPSEC + NAT:
NAT+IPsec cannot be configured between two different sized subnets (e.g. It cannot NAT a /24 subnet to a /27 subnet).
That's true. I was expecting that the NAT subnet is used as a round robin IP pool. Maybe you want to try it out.
Otherwise you have to use a single address out of 172.19.0.0/24.if I remove the pfSense IPs on the 172.19.0.0/24 network, how does the 172.19.0.50 server route the packets to the IPSEC networks?
If you use BINAT with a single address, maybe you can keep the subnet. Not sure.
Give it a try.