To 23.05 or not ? that is the question :)
-
@chudak One patch so far, for the bleeding-edgers :)
https://forum.netgate.com/topic/180313/firewall-alias-import-bug-after-upgrade-to-23-05-release-amd64 -
Successfully upgraded two systems (one Xeon D based Supermicro unit and one Intel i3 custom build) from 23.01 to 23.05. Overall, the upgrade went smooth and was fairly quick on both systems.
A minor issue was that both systems ran into the certificate error the first time when trying to upgrade (as has been documented in other threads already), but flipping the Branch back to 23.01 and then forward to 23.05 again under System -> Update allowed the upgrade to proceed the second time.
Very excited to see
IPsec Multi-Buffer (IPsec-MB) Cryptographic Accelerationbeing added in this release as well as a formal pfSense package forudpbroadcastrelay.A big Thank You to everyone who contributed to this release for all hard work and effort.
-
@chudak pull the trigger . . . upgrade, it was so smooth for me.
-
We did about a dozen boxes. Went great. No issues at all. Hoping the syslog-ng issue gets sorted out soon so we can do a bunch more.
-
@Cylosoft I updated my little SG-2100MAX I got to learn with in school with and it was like a hot knife in butter in a butter bell. Just smooth. I was impressed versus the 21.01 update that one well it had some problems.
-
Any 7100 done already?
And yes: thanks to everyone who contributed to this new release!
-
That was very useful, thx!
I got that too>>> Updating repositories metadata... Updating pfSense-core repository catalogue... Certificate verification failed for /C=US/ST=Texas/L=Austin/O=Rubicon Communications, LLC (Netgate)/OU=pfSense Plus/CN=pfsense-plus-pkg00.atx.netgate.com 34938040320:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-Plus-snapshots-master-main/sources/FreeBSD-src-plus-devel-main/crypto/openssl/ssl/statem/statem_clnt.c:1921: Certificate verification failed for /C=US/ST=Texas/L=Austin/O=Rubicon Communications, LLC (Netgate)/OU=pfSense Plus/CN=pfsense-plus-pkg00.atx.netgate.com 34938040320:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-Plus-snapshots-master-main/sources/FreeBSD-src-plus-devel-main/crypto/openssl/ssl/statem/statem_clnt.c:1921: Certificate verification failed for /C=US/ST=Texas/L=Austin/O=Rubicon Communications, LLC (Netgate)/OU=pfSense Plus/CN=pfsense-plus-pkg00.atx.netgate.com 34938040320:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-Plus-snapshots-master-main/sources/FreeBSD-src-plus-devel-main/crypto/openssl/ssl/statem/statem_clnt.c:1921: Certificate verification failed for /C=US/ST=Texas/L=Austin/O=Rubicon Communications, LLC (Netgate)/OU=pfSense Plus/CN=pfsense-plus-pkg00.atx.netgate.com 34938040320:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-Plus-snapshots-master-main/sources/FreeBSD-src-plus-devel-main/crypto/openssl/ssl/statem/statem_clnt.c:1921: pkg-static: https://pfsense-plus-pkg00.atx.netgate.com/pfSense_plus-v23_05_amd64-core/meta.txz: Authentication error repository pfSense-core has no meta file, using default settings Certificate verification failed for /C=US/ST=Texas/L=Austin/O=Rubicon Communications, LLC (Netgate)/OU=pfSense Plus/CN=pfsense-plus-pkg00.atx.netgate.com 34938040320:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-Plus-snapshots-master-main/sources/FreeBSD-src-plus-devel-main/crypto/openssl/ssl/statem/statem_clnt.c:1921: Certificate verification failed for /C=US/ST=Texas/L=Austin/O=Rubicon Communications, LLC (Netgate)/OU=pfSense Plus/CN=pfsense-plus-pkg00.atx.netgate.com 34938040320:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-Plus-snapshots-master-main/sources/FreeBSD-src-plus-devel-main/crypto/openssl/ssl/statem/statem_clnt.c:1921: pkg-static: https://pfsense-plus-pkg00.atx.netgate.com/pfSense_plus-v23_05_amd64-core/packagesite.pkg: Authentication error Certificate verification failed for /C=US/ST=Texas/L=Austin/O=Rubicon Communications, LLC (Netgate)/OU=pfSense Plus/CN=pfsense-plus-pkg00.atx.netgate.com 34938040320:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-Plus-snapshots-master-main/sources/FreeBSD-src-plus-devel-main/crypto/openssl/ssl/statem/statem_clnt.c:1921: Certificate verification failed for /C=US/ST=Texas/L=Austin/O=Rubicon Communications, LLC (Netgate)/OU=pfSense Plus/CN=pfsense-plus-pkg00.atx.netgate.com 34938040320:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-Plus-snapshots-master-main/sources/FreeBSD-src-plus-devel-main/crypto/openssl/ssl/statem/statem_clnt.c:1921: pkg-static: https://pfsense-plus-pkg00.atx.netgate.com/pfSense_plus-v23_05_amd64-core/packagesite.txz: Authentication error Unable to update repository pfSense-core Updating pfSense repository catalogue... Certificate verification failed for /C=US/ST=Texas/L=Austin/O=Rubicon Communications, LLC (Netgate)/OU=pfSense Plus/CN=pfsense-plus-pkg00.atx.netgate.com 34938040320:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-Plus-snapshots-master-main/sources/FreeBSD-src-plus-devel-main/crypto/openssl/ssl/statem/statem_clnt.c:1921: Certificate verification failed for /C=US/ST=Texas/L=Austin/O=Rubicon Communications, LLC (Netgate)/OU=pfSense Plus/CN=pfsense-plus-pkg00.atx.netgate.com 34938040320:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-Plus-snapshots-master-main/sources/FreeBSD-src-plus-devel-main/crypto/openssl/ssl/statem/statem_clnt.c:1921: Certificate verification failed for /C=US/ST=Texas/L=Austin/O=Rubicon Communications, LLC (Netgate)/OU=pfSense Plus/CN=pfsense-plus-pkg00.atx.netgate.com 34938040320:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-Plus-snapshots-master-main/sources/FreeBSD-src-plus-devel-main/crypto/openssl/ssl/statem/statem_clnt.c:1921: Certificate verification failed for /C=US/ST=Texas/L=Austin/O=Rubicon Communications, LLC (Netgate)/OU=pfSense Plus/CN=pfsense-plus-pkg00.atx.netgate.com 34938040320:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-Plus-snapshots-master-main/sources/FreeBSD-src-plus-devel-main/crypto/openssl/ssl/statem/statem_clnt.c:1921: pkg-static: https://pfsense-plus-pkg00.atx.netgate.com/pfSense_plus-v23_05_amd64-pfSense_plus_v23_05/meta.txz: Authentication error repository pfSense has no meta file, using default settings Certificate verification failed for /C=US/ST=Texas/L=Austin/O=Rubicon Communications, LLC (Netgate)/OU=pfSense Plus/CN=pfsense-plus-pkg00.atx.netgate.com 34938040320:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-Plus-snapshots-master-main/sources/FreeBSD-src-plus-devel-main/crypto/openssl/ssl/statem/statem_clnt.c:1921: Certificate verification failed for /C=US/ST=Texas/L=Austin/O=Rubicon Communications, LLC (Netgate)/OU=pfSense Plus/CN=pfsense-plus-pkg00.atx.netgate.com 34938040320:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-Plus-snapshots-master-main/sources/FreeBSD-src-plus-devel-main/crypto/openssl/ssl/statem/statem_clnt.c:1921: pkg-static: https://pfsense-plus-pkg00.atx.netgate.com/pfSense_plus-v23_05_amd64-pfSense_plus_v23_05/packagesite.pkg: Authentication error Certificate verification failed for /C=US/ST=Texas/L=Austin/O=Rubicon Communications, LLC (Netgate)/OU=pfSense Plus/CN=pfsense-plus-pkg00.atx.netgate.com 34938040320:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-Plus-snapshots-master-main/sources/FreeBSD-src-plus-devel-main/crypto/openssl/ssl/statem/statem_clnt.c:1921: Certificate verification failed for /C=US/ST=Texas/L=Austin/O=Rubicon Communications, LLC (Netgate)/OU=pfSense Plus/CN=pfsense-plus-pkg00.atx.netgate.com 34938040320:error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed:/var/jenkins/workspace/pfSense-Plus-snapshots-master-main/sources/FreeBSD-src-plus-devel-main/crypto/openssl/ssl/statem/statem_clnt.c:1921: pkg-static: https://pfsense-plus-pkg00.atx.netgate.com/pfSense_plus-v23_05_amd64-pfSense_plus_v23_05/packagesite.txz: Authentication error Unable to update repository pfSense Error updating repositories! ERROR: It was not possible to determine pfSense-upgrade remote version ERROR: It was not possible to determine pfSense-upgrade remote version >>> Upgrading pfSense-upgrade... failed. -
Updated from 23.01 to 23.05 on two model 2100 units. One went smooth and the other I got the certificate failure, so I followed @keyser post and successfully upgraded the other. It may be premature as the upgrade happened only 6 hours ago, but it looks like the memory leak issue has been resolved.
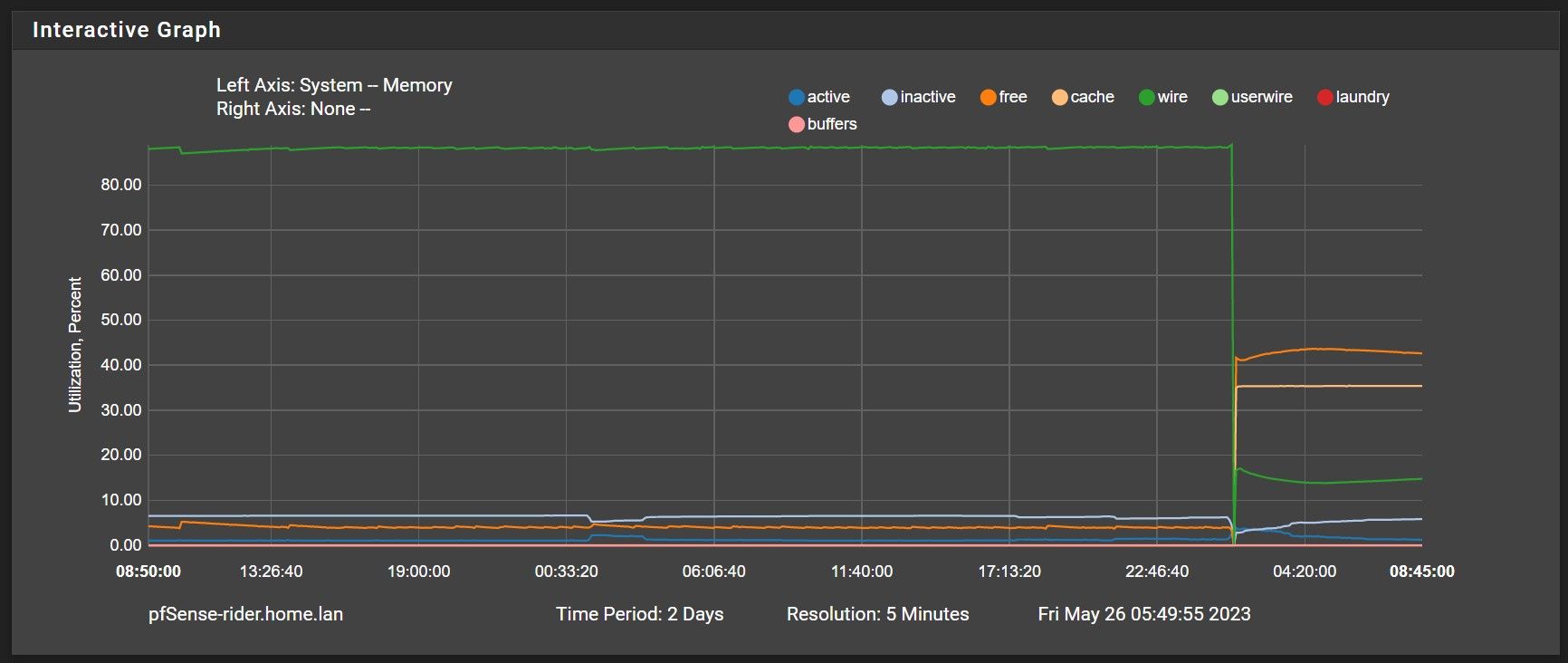
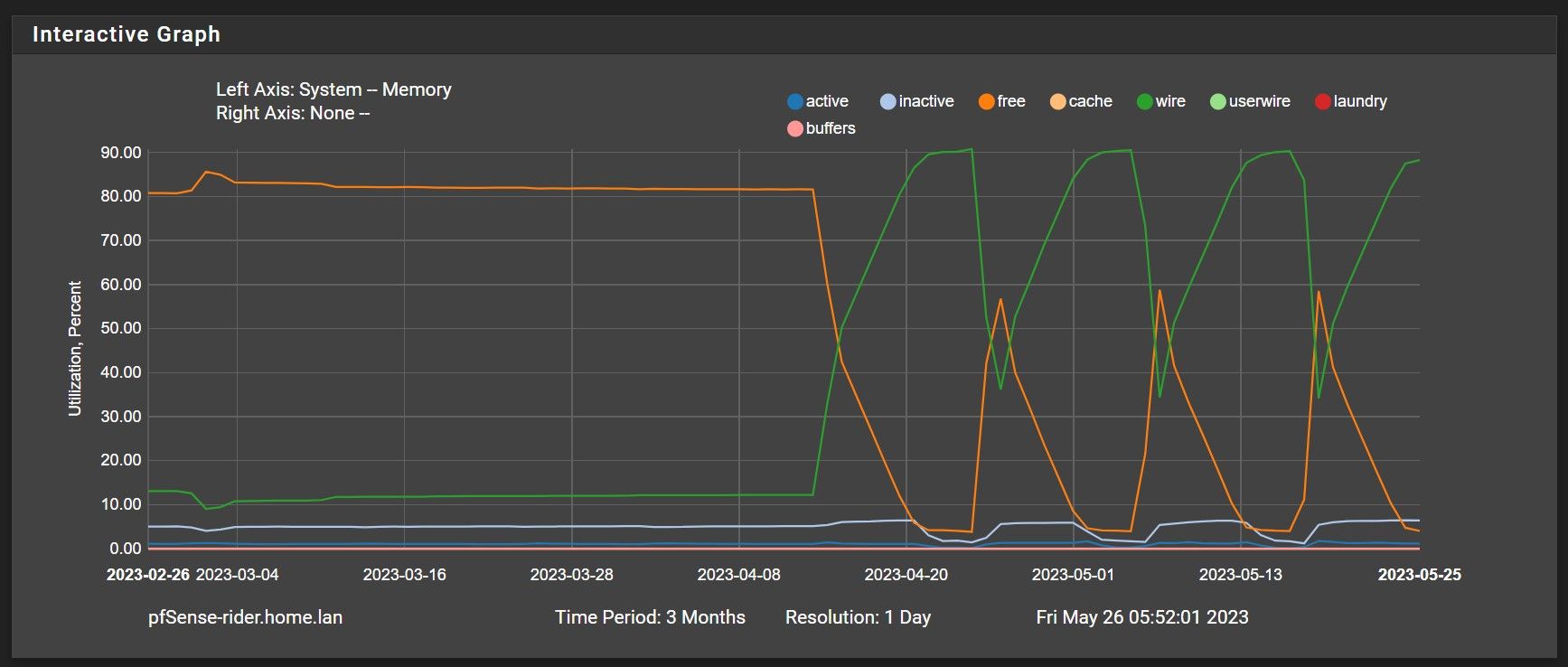
Note: upgraded to 23.01 on 4-13-23 -
@Gertjan said in To 23.05 or not ? that is the question :):
pfSense 23.05 on a 4100 : it was a click, a coffee, and done.
This made me laugh and think "The way all upgrades should be. No issues but long enough to have a coffee"
-
I had gotten hit with the cert issues on my SG3100 running 23.01 when I first tried. So I found a quick ssh fix on here and I upgraded just fine. No issues so far. I have a fairly complex config.
That was my home firewall.
The other triple digit worth of work firewalls, I'm going to wait a little bit. we'll see if there is a 23.05.1 or something.
-
On my home 2100 I saved a config locally, pre-booted, then via the console attempted to update but was stopped by the certificate error. Searching in the Upgrades forum here I followed the advice to swap the update branch back and forth. Did another pre-boot, then updated via console went fine. Less than 10 minutes on the 2100. Did a post-install reboot for good measure. I did not uninstall pfBlockerNG or Avahi first. So far so good.
-
I just ran into that "SSL routines:tls_process_server_certificate:certificate verify failed" error as well updating my sg4860.. A toggle in the update from 23.05 to 23.01 and then back cleared the error and update worked without issue.
I would always suggest if on a netgate appliance you get the new image from them just in case when doing an upgrade. They took 1 whole minute to answer my ticket and provide a link to download..
if not appliance then make sure you have a copy of the CE you can use if the worse case scenario happens..
Always better to be prepared then getting caught with pants down, and your router being down makes it kind of hard to download images ;)
Had my install media just in case
Took my config backups - again just in case
Connected to serial so could watch progress.
Clicked confirm on update - approx 13 minutes latter I was logging in to gui.
So far all looks good.. All packages updated, I didn't uninstall them before hand.
My HE tunnel is up, my vpn tunnel is up, I show vpn server running, my tailscale shows good.. Still need to test connections for those - but don't foresee any issues.Packages like pfblocker, haproxy, freerad all seem to be working just fine.
Other then the slight little blimp with the verify cert thing, looks like another smooth and simple upgrade. I like the new package capture features - those will come in handy for sure. And will have to test the new L2 filtering - that seems interesting, and a long wished for option from many users.
-
@johnpoz
Except for the haproxy, I had exactly that experience.
I saw the "SSL routines:tls_process_server_certificate:certificate verify failed" thing, but, thanks, forum, that was gone after forcing a branch switch twice.And thanks to the gigabit fiber connection, downloading was way faster as upgrading.
The entire processes took a cope of minutes.@johnpoz said in To 23.05 or not ? that is the question :):
pants down
I was trusting plan Zfs (snapshot).
-
@johnpoz said in To 23.05 or not ? that is the question :):
I would always suggest if on a netgate appliance you get the new image from them just in case when doing an upgrade. They took 1 whole minute to answer my ticket and provide a link to download..
Always better to be prepared then getting caught with pants down...
The Netgate support is quick for sure but they probably would not be if all the 'worried well' hit them for images as a matter of routine come update time.
I'd be concerned that Netgate Tac Team could become overwhelmed just when we need them to be at their best.
I appreciate that this is coming from someone who experienced a flawless update with my 6100 and that things always feel very different when you have an unexpected issue.
 ️
️ -
@RobbieTT said in To 23.05 or not ? that is the question :):
if all the 'worried well' hit them for images as a matter of routine come update time.
true - I ran into this once, new update had just dropped.. And took them like 23 minutes ;)
That is why you don't plan on asking for the image 5 minutes before you plan on doing the update.. I knew I wasn't going to run the update til this weekend.. So had plenty of time to get the image.. Even if they took awhile..
Kind of miss the days where you could just login and grab image any time you wanted to be honest.. But I am a self help sort of person, and don't really like having to count on someone else to get stuff done ;)
btw - just checked my phone vpn in both openvpn and tailscale - both working just fine using cell network as connection.
-
@RobbieTT That was my initial thought but I expect by now they have a pushbutton/one click way to respond, or at least they should. The answer is so fast. Even if one keeps every other or every third image file then one can reinstall and upgrade to Previous Stable. Or keep an old router on the shelf for such an an emergency…can’t download a file directly on your cell phone. :) There is a special Netgate Partner (-only) site where the files are posted but they seem to take a few weeks to post after release which implies to me they’re not all that concerned about offloading from TAC.
With CE of course one can just download it. tip: leave the Architecture field empty and it will show the previous version also.
-
7100 upgraded. Hit the cert error, clicked the Save button on the Update Settings tab then the upgrade ran with no problems.
-
@mcury said in To 23.05 or not ? that is the question :):
Upgraded successfully here, SG-4100.
1- Disabled RAM disk
2- Boot environments restore to a point in which I didn't have packages installed (just usual config)
3- Upgraded
4- Reinstalled and reconfigured packages
5- Enabled RAM disk againYou got me interested by the "RAM disk" point
Can you share your experience with it? -
@chudak The main benefit of a RAM disk is fewer and faster writes, which is nice on eMMC storage.
The down side, it only copies logs hourly at best. Enabling requires a restart. Many packages will copy their data to storage at restart but I think not all. PfBlocker’s giant UT1 list takes more than 1 GB to download and process.
Since 22.01 I think, it only allocates used space and does not preallocate RAM.
I’ve never bothered disabling RAM disks for upgrades.
https://docs.netgate.com/pfsense/en/latest/config/advanced-misc.html#ram-disk-settings
-
@chudak said in To 23.05 or not ? that is the question :):
You got me interested by the "RAM disk" point
Can you share your experience with it?As @SteveITS just mentioned, it increases the eMMC lifespan and this is the main reason I use it.
I disable RAM disk to upgrade because I'm not sure what will happen to /tmp once the upgrade is download and decompressed for installation.
This is just a step I usually take to avoid problems during upgrade, just to make sure everything will work and have enough space, but as others mentioned, not necessary. But I think it is a good decision to take, to turn it off before upgrade.