freeradius / eap-tls / Android 13
-
@furom what about this
https://aboutssl.org/how-to-create-and-import-self-signed-certificate-to-android-device/
Doesn't say what version of android, but it has it adding an option to the CA via openssl
openssl x509 -req -days 3650 -in CA.pem -signkey priv_and_pub.key -extfile ./android_options.txt -out CA.crt
Or I would assume the acme way would work - this isn't a self signed CA, etc. So for like the 10 you could get a domain you could use.. Or you can always get cheap domain like .xyz for like the first year for like 99 cents ;)
edit: guess I am lucky my tablet is only running 12, which accepts my CA.
edit2: also came across this
Android will not allow a Certificate Authority to be installed from certain locations. The SSL cert must be stored in local storage, but not in the "Downloads" folder and not in Google Drive. Even though this is permitted for user certificates, CA certificates won't work unless moved to a local folder that is not the downloads folder.
Where exactly are you putting the CA cert when you try to install it?
-
@johnpoz said in freeradius / eap-tls / Android 13:
@furom what about this
https://aboutssl.org/how-to-create-and-import-self-signed-certificate-to-android-device/
Doesn't say what version of android, but it has it adding an option to the CA via openssl
openssl x509 -req -days 3650 -in CA.pem -signkey priv_and_pub.key -extfile ./android_options.txt -out CA.crt
Or I would assume the acme way would work - this isn't a self signed CA, etc. So for like the 10 you could get a domain you could use.. Or you can always get cheap domain like .xyz for like the first year for like 99 cents ;)
edit: guess I am lucky my tablet is only running 12, which accepts my CA.
edit2: also came across this
Android will not allow a Certificate Authority to be installed from certain locations. The SSL cert must be stored in local storage, but not in the "Downloads" folder and not in Google Drive. Even though this is permitted for user certificates, CA certificates won't work unless moved to a local folder that is not the downloads folder.
Where exactly are you putting the CA cert when you try to install it?
In the Downloads folder... Was too lazy to create another one. I figured when installed it gets copied anyways, but is perhaps just linked... worth a try! :)
-
@furom This is where I'm at now;
(3) eap_tls: (TLS) EAP Done initial handshake (3) eap_tls: (TLS) recv TLS 1.2 Alert, fatal unsupported_certificate (3) eap_tls: (TLS) The client is informing us that it does not understand the certificate presented by the server. (3) eap_tls: ERROR: (TLS) Alert read:fatal:unsupported certificate (3) eap_tls: (TLS) Server : Need to read more data: error (3) eap_tls: ERROR: (TLS) Failed reading from OpenSSL: error:0A000413:SSL routines::sslv3 alert unsupported certificate (3) eap_tls: (TLS) In Handshake Phase (3) eap_tls: (TLS) Application data. (3) eap_tls: ERROR: (TLS) Cannot continue, as the peer is misbehaving. (3) eap_tls: ERROR: [eaptls process] = fail (3) eap: ERROR: Failed continuing EAP TLS (13) session. EAP sub-module failed (3) eap: Sending EAP Failure (code 4) ID 25 length 4I tried with a .crt cert when it needs .pem, so will convert and try again
-
@furom a .crt file is a pem.. That error could mean it its not trusting the cert, because the CA that signed it isn't trusted.
When you look in the crt does its show in the first line when open with text editor?
-----BEGIN CERTIFICATE-----
-
@johnpoz said in freeradius / eap-tls / Android 13:
@furom a .crt file is a pem.. That error could mean it its not trusting the cert, because the CA that signed it isn't trusted.
When you look in the crt does its show in the first line when open with text editor?
-----BEGIN CERTIFICATE-----
It does. Both CA & cert
also, just tried moving the certs on the tablet out of Downloads and reinstalled them, then trying against freeRad/pfSense same issue as before...
(4) eap_tls: (TLS) EAP Done initial handshake (4) eap_tls: (TLS) recv TLS 1.2 Alert, fatal internal_error (4) eap_tls: ERROR: (TLS) Alert read:fatal:internal error (4) eap_tls: (TLS) Server : Need to read more data: error (4) eap_tls: ERROR: (TLS) Failed reading from OpenSSL: error:14094438:SSL routines:ssl3_read_bytes:tlsv1 alert internal error (4) eap_tls: (TLS) In Handshake Phase (4) eap_tls: (TLS) Application data. (4) eap_tls: ERROR: (TLS) Cannot continue, as the peer is misbehaving. (4) eap_tls: ERROR: [eaptls process] = fail (4) eap: ERROR: Failed continuing EAP TLS (13) session. EAP sub-module failed -
@furom you should see your CA as trusted in your user section..
Did you try it with the link I provided that has adding some sort of option to the CA cert.
-
@johnpoz said in freeradius / eap-tls / Android 13:
@furom you should see your CA as trusted in your user section..
Well, it does not show up there... :( Under 'User certificates' both show though, but not whats matter here...
Did you try it with the link I provided that has adding some sort of option to the CA cert.
Not yet. much going on now, but will attend that now :)
-
@furom on my tablet I don't have to do anything special with the cert, I mean a CA created in pfsense would already have the basic constraint of CA already set
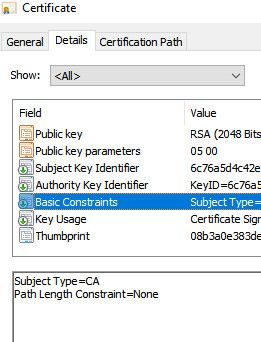
I am able to install just from the download folder - I emailed myself the CA.crt - then just installed it, and there it is listed.
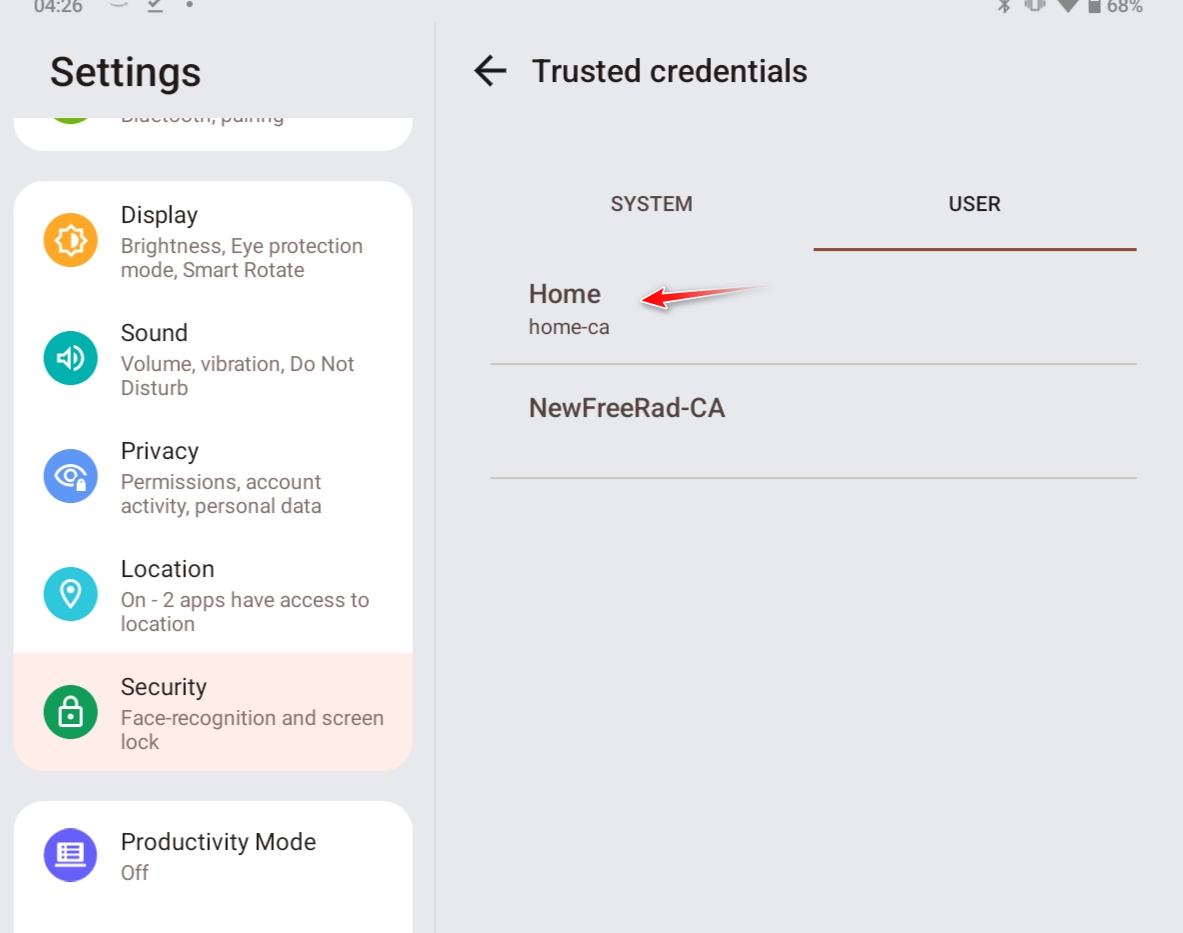
edit: you can then see the tablet trusts this certs signed by this CA
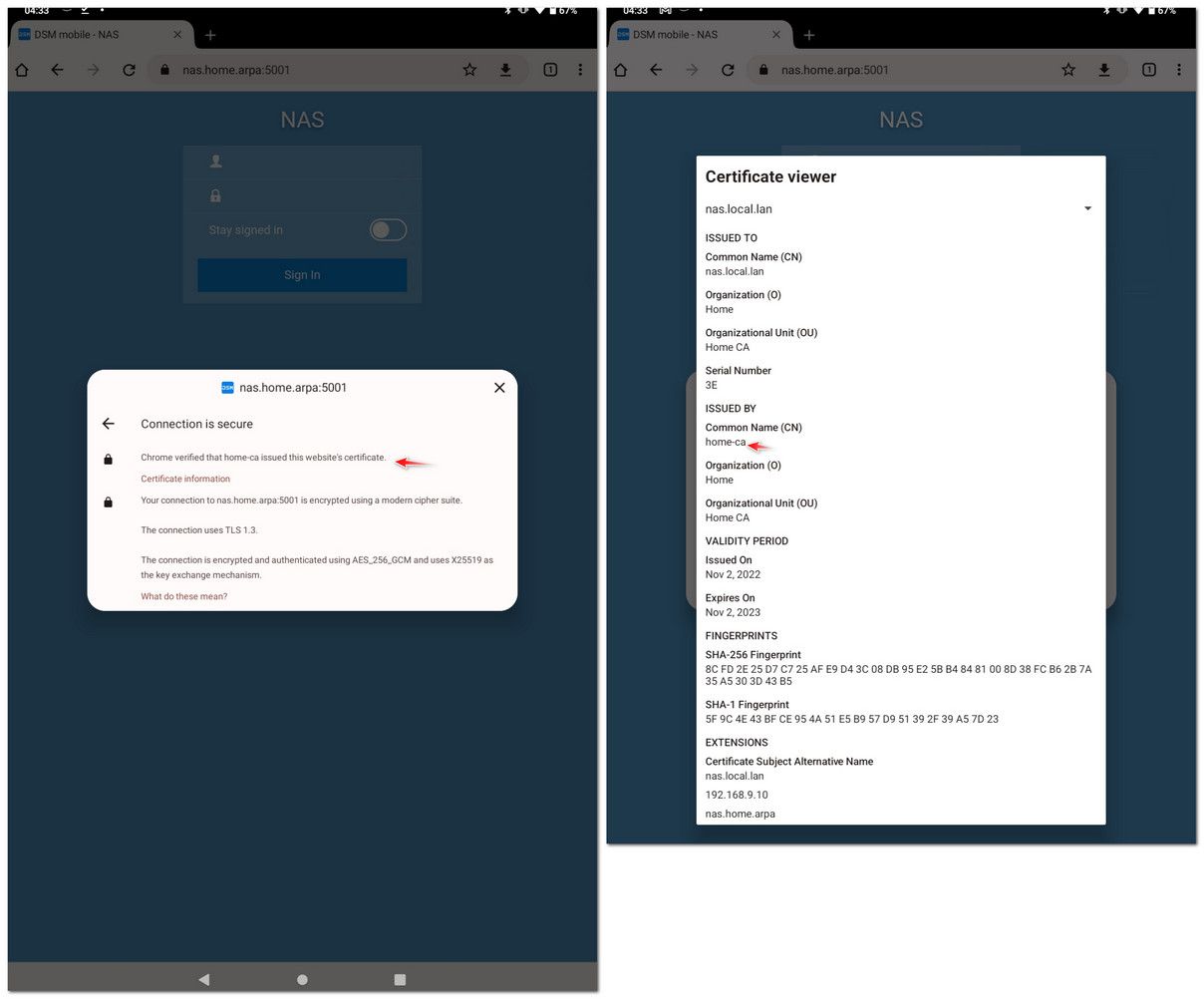
-
@johnpoz Well then, if basic constrains is already included... :/
-
@furom but possible android 13 is looking for it elsewhere? Not really an android guy, but you should be able to check on your tablet if it trusts this CA, you should see it in your user section of trusted CAs - like the 2 I have installed.
I have a few different CAs, one for home that I create certs for stuff like my nas, my printer, my pfsense gui, my switches gui's etc..
I also have another one for openvpn, and then the one I created for freerad use.
If you don't see it there - then yeah its highly unlikely that it would trust the cert your freerad server presents, etc.
But its possible wifi stuff using its own settings? Like said not an android guy, notice it doesn't show my homeca as possible ca for my wireless?
So for wireless you might have to install the CA under the wireless settings, but I would think if you have it installed and shown under your user for the system that using the use system certs should work.
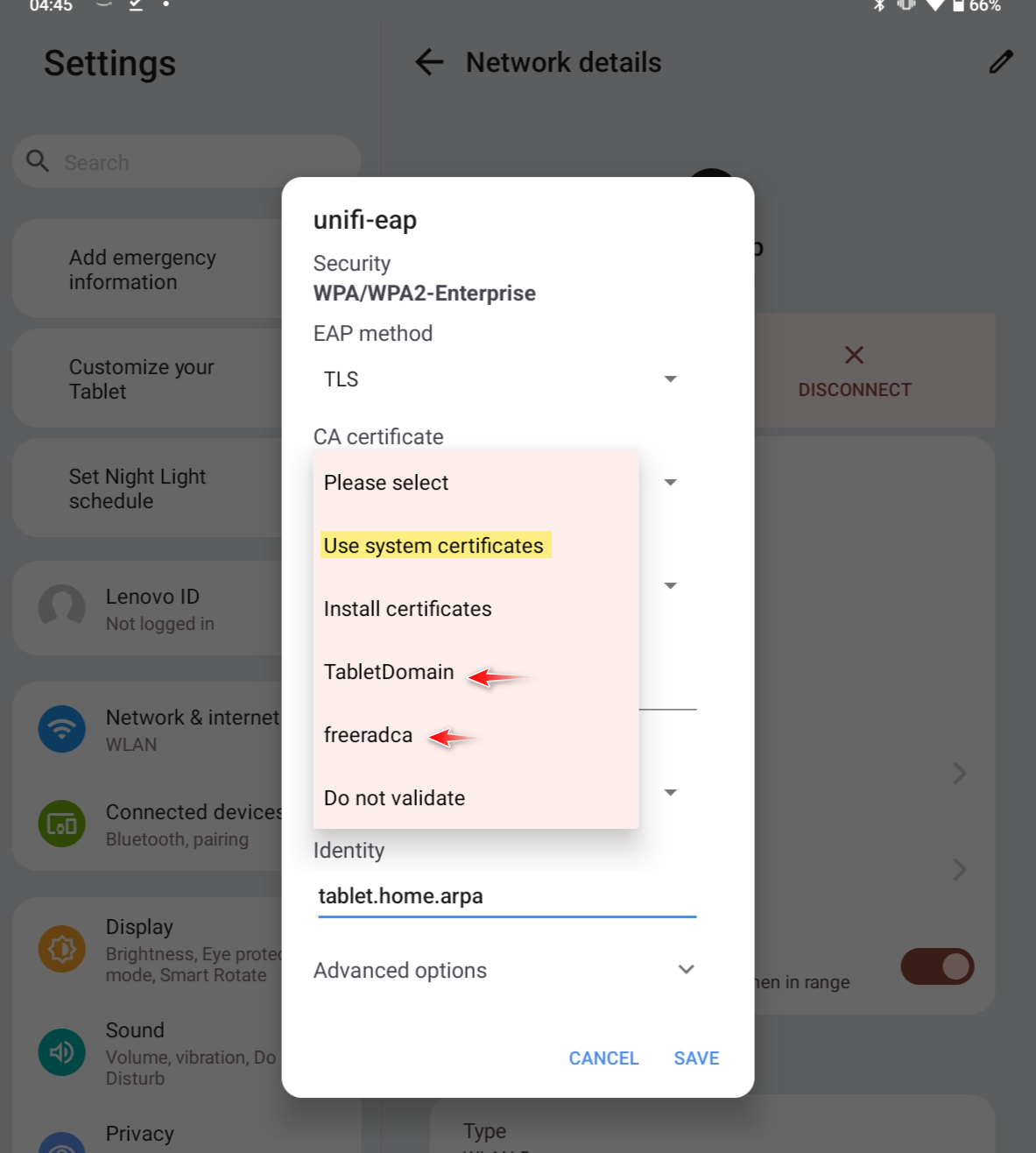
I tried using "system" in wifi and didn't work - I have to select the CA I installed using wifi
-
@johnpoz said in freeradius / eap-tls / Android 13:
@furom but possible android 13 is looking for it elsewhere? Not really an android guy, but you should be able to check on your tablet if it trusts this CA, you should see it in your user section of trusted CAs - like the 2 I have installed.
I have a few different CAs, one for home that I create certs for stuff like my nas, my printer, my pfsense gui, my switches gui's etc..
I also have another one for openvpn, and then the one I created for freerad use.
It is possible of course. It has never been this troublesome ever before, that is for sure...
I will try the separate radserver once more. I just realized I did not install its server cert etc as also is needed...
I'd rather not go the acme way, I don't want nor need the domain... Sad it must be a requirement, it is so close (and will probably just work) but still so far away... :)
-
@furom said in freeradius / eap-tls / Android 13:
I will try the separate radserver once more
This has nothing to do with it.. Your device needs to trust the CA that you sign the freerad server cert you are using in the freerad setup.
And the freerad server needs to trust the client cert the client presents.. Be that freerad running on pfsense or not would have have nothing to do with your client trusting the CA, or presenting the correct cert that the freerad server will accept.
If you can not get the CA installed on your tablet, or be able to set not to validate it - its not going to work. I believe later versions of android removed that option, which people are complaining about since they are having a hard time getting the CA actually installed as well..
I am not having this issue, as you can see I can install CAs under the wifi setting.. But if you miss a step your going to have a bad day.. Your freerad server should have the same CA, and a server cert you created. Your client needs to trust the CA and present a cert also signed by the CA.
Make sure you have fqdn set for the CN..
-
@johnpoz said in freeradius / eap-tls / Android 13:
@furom said in freeradius / eap-tls / Android 13:
I will try the separate radserver once more
This has nothing to do with it.. Your device needs to trust the CA that you sign the freerad server cert you are using in the freerad setup.
And the freerad server needs to trust the client cert the client presents.. Be that freerad running on pfsense or not would have have nothing to do with your client trusting the CA, or presenting the correct cert that the freerad server will accept.
If you can not get the CA installed on your tablet, or be able to set not to validate it - its not going to work. I believe later versions of android removed that option, which people are complaining about since they are having a hard time getting the CA actually installed as well..
You are right of course... I'm just sad I can't get this to work... And by the looks of it, by design, so not likely to suddenly start working in a later version... :(
-
@furom Or your just missing a step? Or forgetting to set fqdn? I wish I had a android 13 to test with.. I hope my son's is running newer version on his phone - if he doesn't come over on monday for bbq, next time he comes over I will be sure to test.
Maybe take a few days off from this.. Just use wpa3 personal for now.
-
@furom Something like this might be a short-term solution...
https://forum.xda-developers.com/t/samsung-galaxy-tab-a8-2021-sm-x200-android-12-android-13-treble-flash-guide.4497299/
to downgrade to v12... but really don't want to mess with it already...And even then, I would want to use Samsung official software, which I doubt is made available...
-
@johnpoz said in freeradius / eap-tls / Android 13:
@furom Or your just missing a step? Or forgetting to set fqdn? I wish I had a android 13 to test with.. I hope my son's is running newer version on his phone - if he doesn't come over on monday for bbq, next time he comes over I will be sure to test.
Maybe take a few days off from this.. Just use wpa3 personal for now.
Yeah, WPA3 is working at least, I must be happy with that... And you have gone to lengths to try, I really appreciate that!
I am still intrigued by the Jenkins error though... Why would freeradius/pfSense or openssl try to read anything from such path, that isn't even on the system? Makes no sense either...
-
@furom Well... couldn't leave it be... :) So I disabled scrubbing in pfSense and bumped fragment_size in freeRadius to 1500, and well, it's still not working, but different song, not sure if better though
Sat May 27 17:12:20 2023 : Debug: (2) eap: Expiring EAP session with state 0x9d6486969c558b0b Sat May 27 17:12:20 2023 : ERROR: (2) eap: rlm_eap (EAP): No EAP session matching state 0x9d6486969d548b0b Sat May 27 17:12:20 2023 : Debug: (2) eap: Either EAP-request timed out OR EAP-response to an unknown EAP-request Sat May 27 17:12:20 2023 : Debug: (2) eap: Failed to get handler, probably already removed, not inserting EAP-FailureThis is all of it though, and tablet shows no error, just hangs a few seconds until it times out. What "No EAP session matching state" means... A thread talking about the same error it was high server load, not the case here though; freeradius is running in a VM with almost idle CPU's and lots of memory - it should not complain about that part at least
-
 J johnpoz referenced this topic on
J johnpoz referenced this topic on
-
Hey, I have a free radius server that support eap tls 1.3.
I send an eap tls authentication using Windows 11 and see by wireshark that packet are really eap tls 1.3.
but then when i do it using MacOS / iphone / android that support eap tls 1.3 by default (as wrote in apple and android forums) i see an Client hello of 1.2 without the extension of support version and the authentication is by eap tls 1.2.
Anyone saw this issue/ know if they are really support authentication of eap tls 1.3 ? I use same certificates for all of the clients and install them.
Thanks, Nir.