pf.os or p0f.fp
-
Hello fellow Netgate community members,
Can you please help? Does anyone know if the database used for p0f is pf.os or p0f.fp?
I want to attempt to add some container os fingerprints into that database and maybe get some upper-level guys to take a look at this.
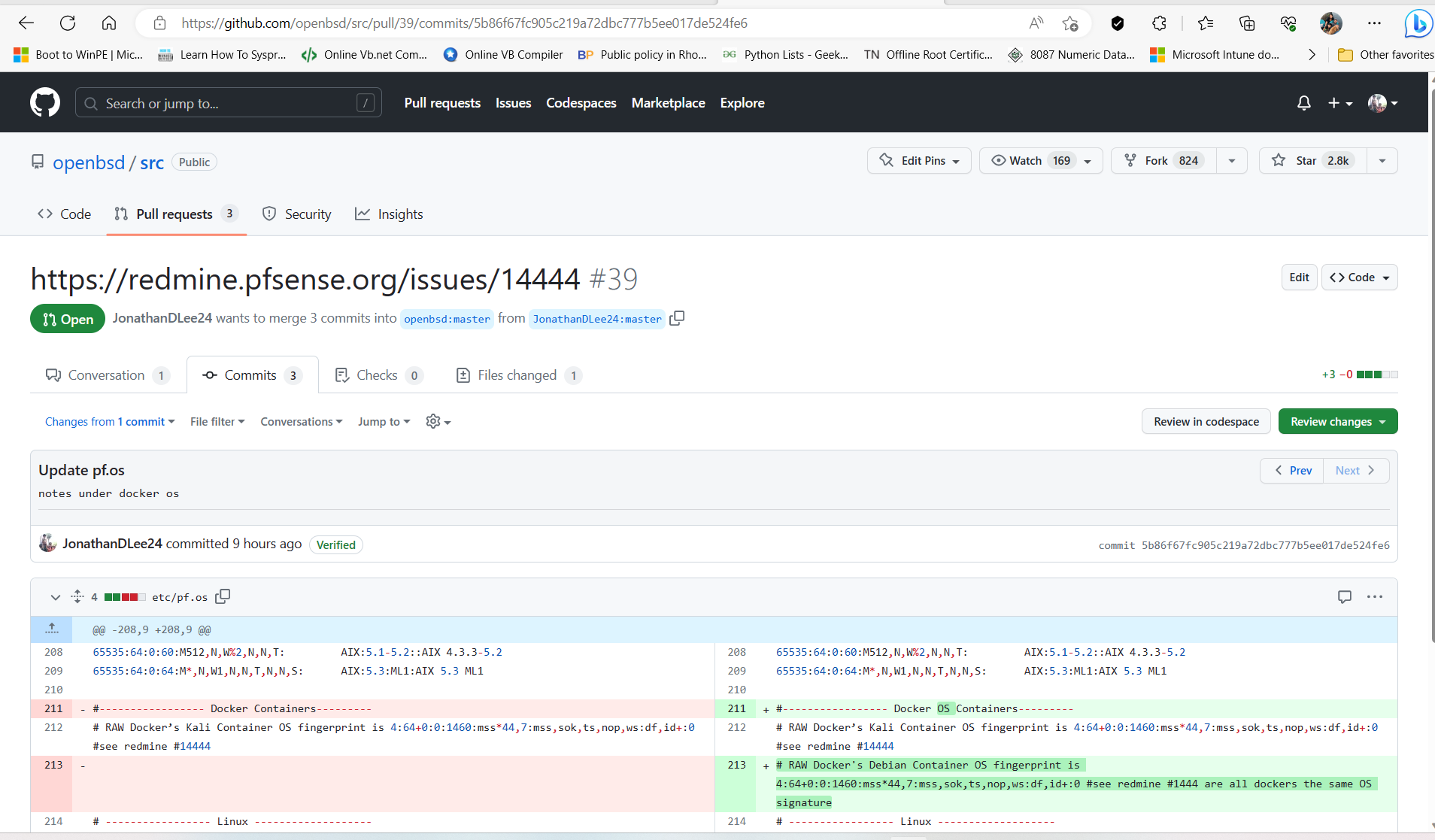
https://redmine.pfsense.org/issues/14444
Has anyone played around with OS fingerprinting?
-
OpenBSD ? What's that ?

-
@Gertjan I think it is what pfsense is built on. So if I can bring attention to the pf.os file missing current OS types as well as container OS signatures it might get more eyes on this, and eyes that want to make it more secure. I could not believe I could fingerprint Docker containers with p0f. p0f is a program that can fingerprint operating systems, and if you look at the ACL list on the firewalls you can set them to allow by source OS again p0f is what helps with that option, again it has not been updated it a while, it still shows XP.
My idea for a possible solution to this is to just allow aliases versions of OS fingerprints/signatures that way the user can input them. In theory the OS source options will work the same way and not need any updated list with the ability to add in a block of custom use OS signature/fingerprints. We could set ACL (access control lists) to block out specific Docker containers and or allow them on specific ACLs.
Say you only want Mac Ipad and Windows users on port 3128 and a different VLAN for docker use, you could do that if we had a way to input them without just adapting the old file.
It would be user friendly. You could set them to block containers or allow them and control at a more granular level
https://redmine.pfsense.org/issues/14444
-
I was able to fingerprint OS in Docker and in Hypervisor and they are different from the host machine.
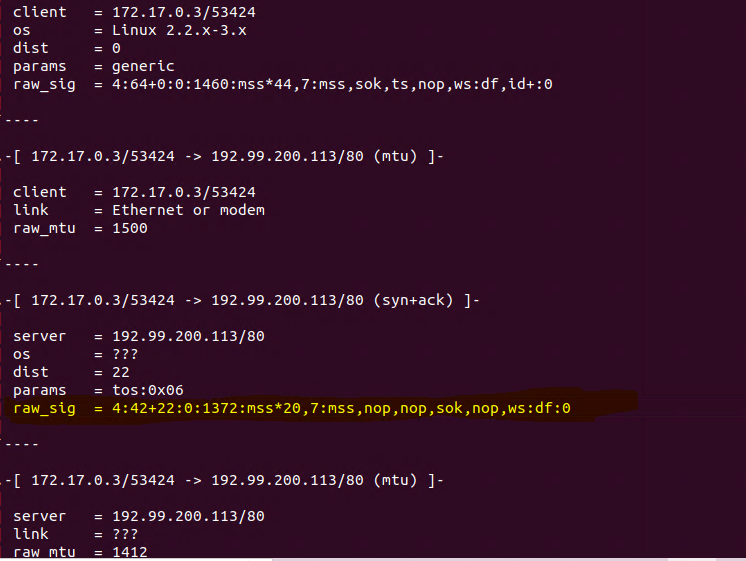
p0f ran inside of Docker’s Kali Container is 4:42+22:0:1372:mss*20,7:mss,nop,nop,sok,nop,ws:df:0 was seen and 4:64+0:0:1460:mss*44,7:mss,sok,ts,nop,ws:df,id+:0 one is the smartphone one is my container used for researching this.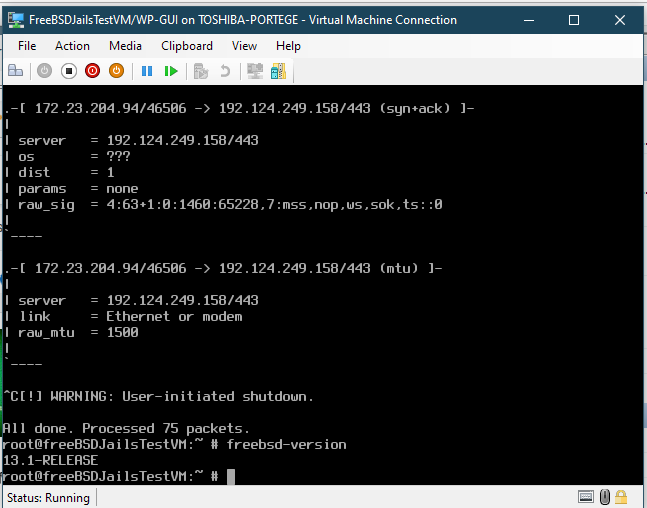
Signature example 4:63+1:0:1460:65228,7:mss,nop,ws,sok,ts: :0
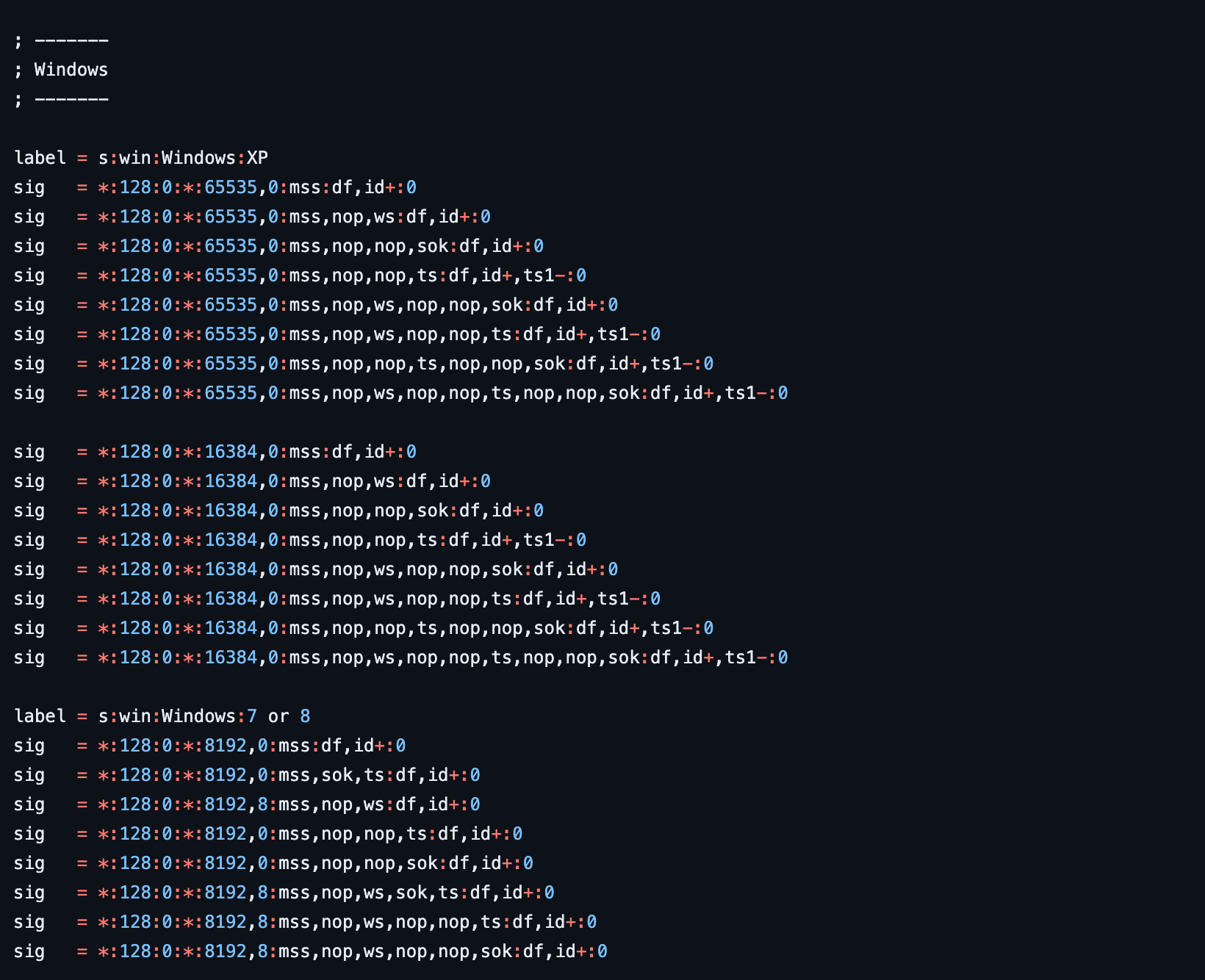
I think this is freeBSD 13.12 and or the gateway it was communicating with.Again I can't input the signatures into the firewall's GUI but they do list old signatures in the pf.os and p0f.tp databases that the firewall uses with this advanced option.
p0f.tp current signature database: Sigdatabase.txt this text file of the database shows that the new and old signatures match the style and formatting for what I just fingerprinted inside of a Docker container. Again both are the same style.
-
https://redmine.pfsense.org/issues/7260
There is a redmine open for the OS updates from 6 years ago no one responded.
So if there is trouble getting the signature lists updated why not add in a custom aliases option for users and forget updating it all together.
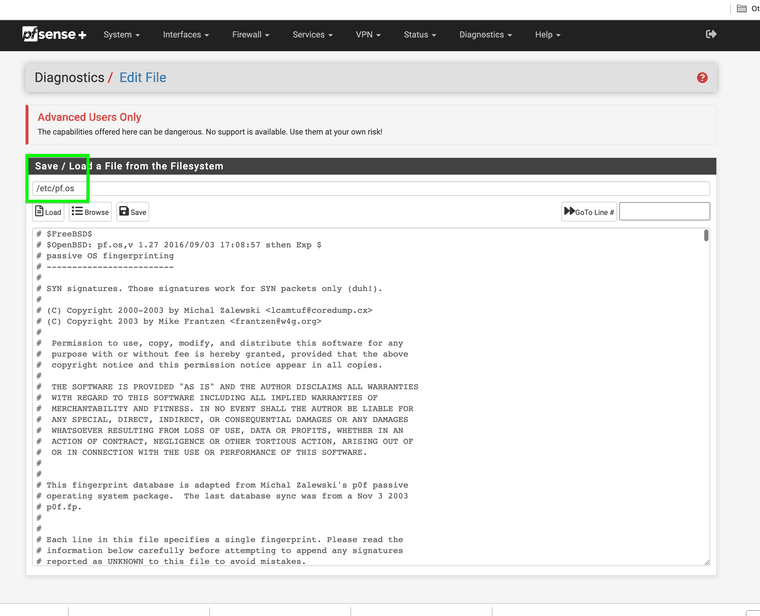
/etc/pf.os
this file is listed on the firewall also.
-
So if I bring it up on openBSD maybe it will get updated and or if I bring it to light the need for a GUI alias option that might fix it. Who knows. What do you think about the Docker fingerprinting :) cool right?
-
pfSense is build / based upon FreeBSD.
It's not 'FreeBSD', as the stock kernel is modified for pfSense needs.FreeBSD was 'forked' from the Unix BSD variant about 30 years ago.
OpenBSD has the same parent, dating from de same period.Never saw 'docker' and 'pfSense' being mentioned in the same phrase.
-
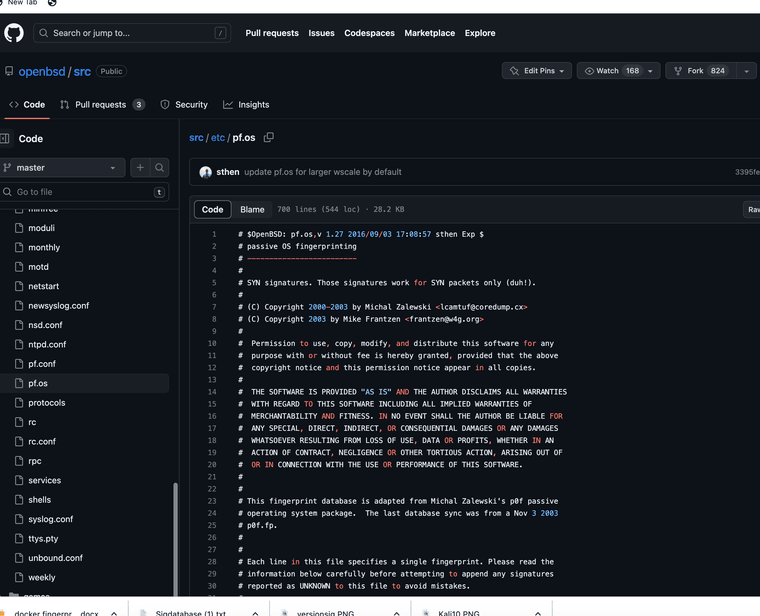
I understand again, why is the pf.os talking about pfsense inside of openBSD?
I also asked here,,
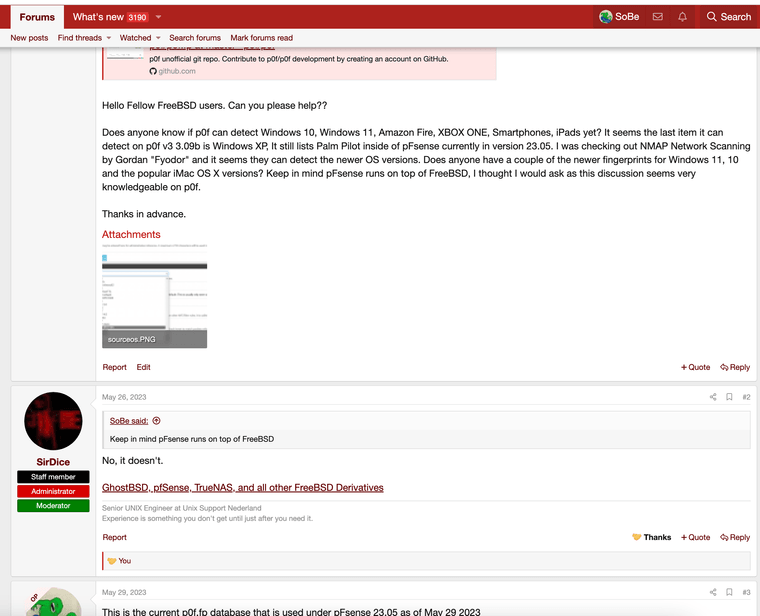
https://forums.freebsd.org/threads/p0f3-question-on-current-os-fingerprinting.89218/#post-612200
that file pf.os matches the file pf.os inside of pfsense. I thought maybe they are related guess not. Again if someone is using it on openBSD maybe they can help updating it .. . . I could not find it on the pfsense master only on the openbsd
(pfsense)
(openbsd)
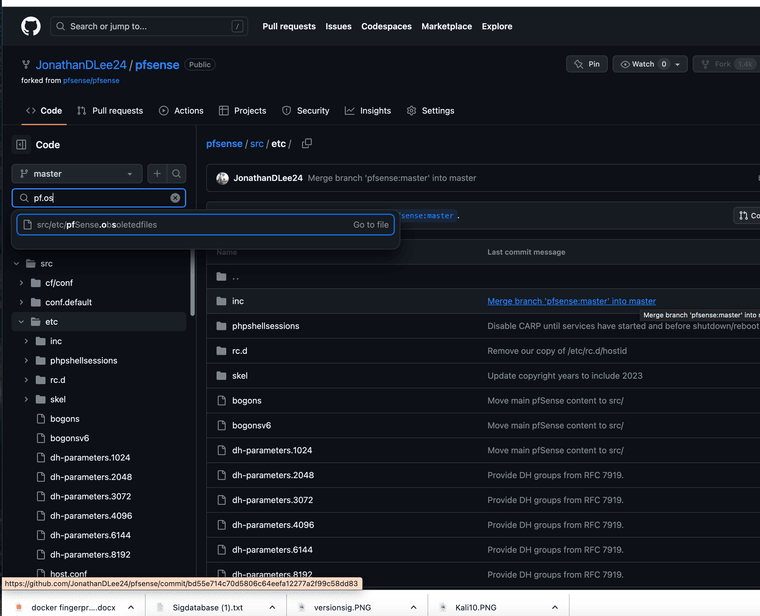
(recent fork of pfsense showing it not listed)Again pf0/pf0 fork lists it's database as p0f.fp and not p0f.os that is used on pfsense.
(p0f.fp) -
@Gertjan Pfsense has the ability in theory to be the first firewall to compartmentalize docker os signatures apart from the host machines and actually control traffic in that manner:) wouldn't that be cool? Again, invasive nation state actors only attack walls at their weakest areas.