DHCP server and Firewall as static entry
-
Hello Fellow Netgate Community Members can you please help??
Quick Question:
With static assignments and setting the Squid proxy on the 192.168.1.1:3128 for example would you set up a DHCP for the firewall for a long time I did not list the firewall inside the DHCP, again I noticed it listed my firewall IP as a useable address, as soon as I added it now its green in the lease.
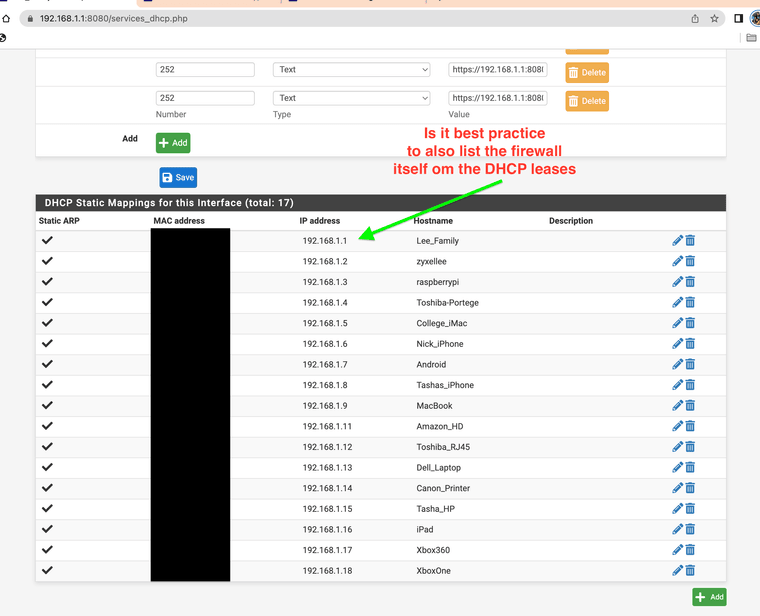
(STATIC ENTRY DHCP)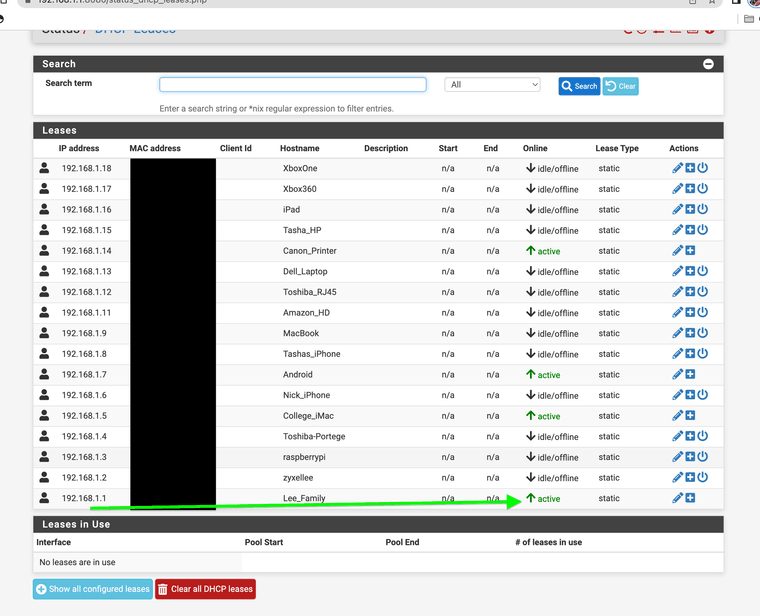
(Lease shows active)I wanted to ask what other uses do that use static MAC entry and block all others.
I was surprised that it went to green as soon as I added it, Keep in mind I never added the firewall before. I still have full use of the system both ways.
-
@JonathanLee said in DHCP server and Firewall as static entry:
I was surprised that it went to green as soon as I added it
It's 'green' if it's in the Diagnostics > ARP Table = ARP cache.
But 192.168.1.1 is not a lease - should not be a lease. Maybe it can be a DHCP lease, but I've never saw that IRL.
It's the LAN base addresses, the one pfSense uses for it's LAN interface. -
@JonathanLee this is why you set the dhcp range, the range you setup should not include pfsense IP, or any other IPs that you might set on any device itself.
Pfsense warns you of this when you put an IP on an interface or change an IP of an interface.
"Don't forget to adjust the DHCP Server range if needed after applying."
The dhcpd does attempt to check if a IP is in use before leasing it anyway (ping check) - but it is good practice to set your scope in your dhcp server to not overlap with IPs that will set as static on the device.
Common practice to say set the range at like .10 to .250 or something in a /24 to allow for static IPs on either end for stuff like switches or printers or other devices you might set an IP directly on the device or via a reservation "static lease"
You can set multiple pools if your going to use static IPs on the network that fall in middle of the range for for example.
you could set pool 1 to be say
.10-.100
and 2nd pool to to be
.110 - .250
Leaving .101-.109 available as static address on the network where the dhcp would not hand out .1-.9 or .251 to .254 or .101 to .109
Now let say you set the range to .1 to .254 and your pfsense IP was .1, it shouldn't hand out that .1 address ever because you would assume pfsense could ping itself :) Unless you had disabled the ping check, it should never hand out that .1 address. But its still common and good practice to set the actual range a dhcpd can hand out leaving some IPs you can use for static devices outside the scope, be it you setup a specific lease for that IP, or set the IP directly on the device.
edit: example for my network I put iot devices, smart lightbulbs, alexas, thermostat, etc I have a very small dhcp range.. Because once I bring up a new device I always move them to a static lease outside the scope of the dhcpd.
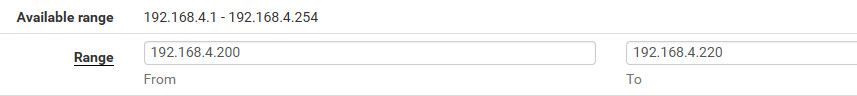
Have a small range of IPs that can be handed allows me to bring up new devices easy, but leaves me plenty of room to set a new device to specific IP via a lease.
-
@Gertjan sorry I wrote this pretty late I guess I meant to say is it best practice to add a static entry for the firewall
-
@JonathanLee said in DHCP server and Firewall as static entry:
best practice to add a static entry for the firewall
No there should be no reason to, since unless the interface is a wan interface it wouldn't be dhcp anyway. Normal common best practice is the change your dhcp range to not include the IP used by pfsense in the first place.
If you are worried that your dhcp could in theory had out a duplicate for pfsense IP.. set yoru dhcp range to not include that.. For example if pfsense is .1, then set your range to .2 - .254
-
@johnpoz thanks for the reply,
So far this is my configuration,
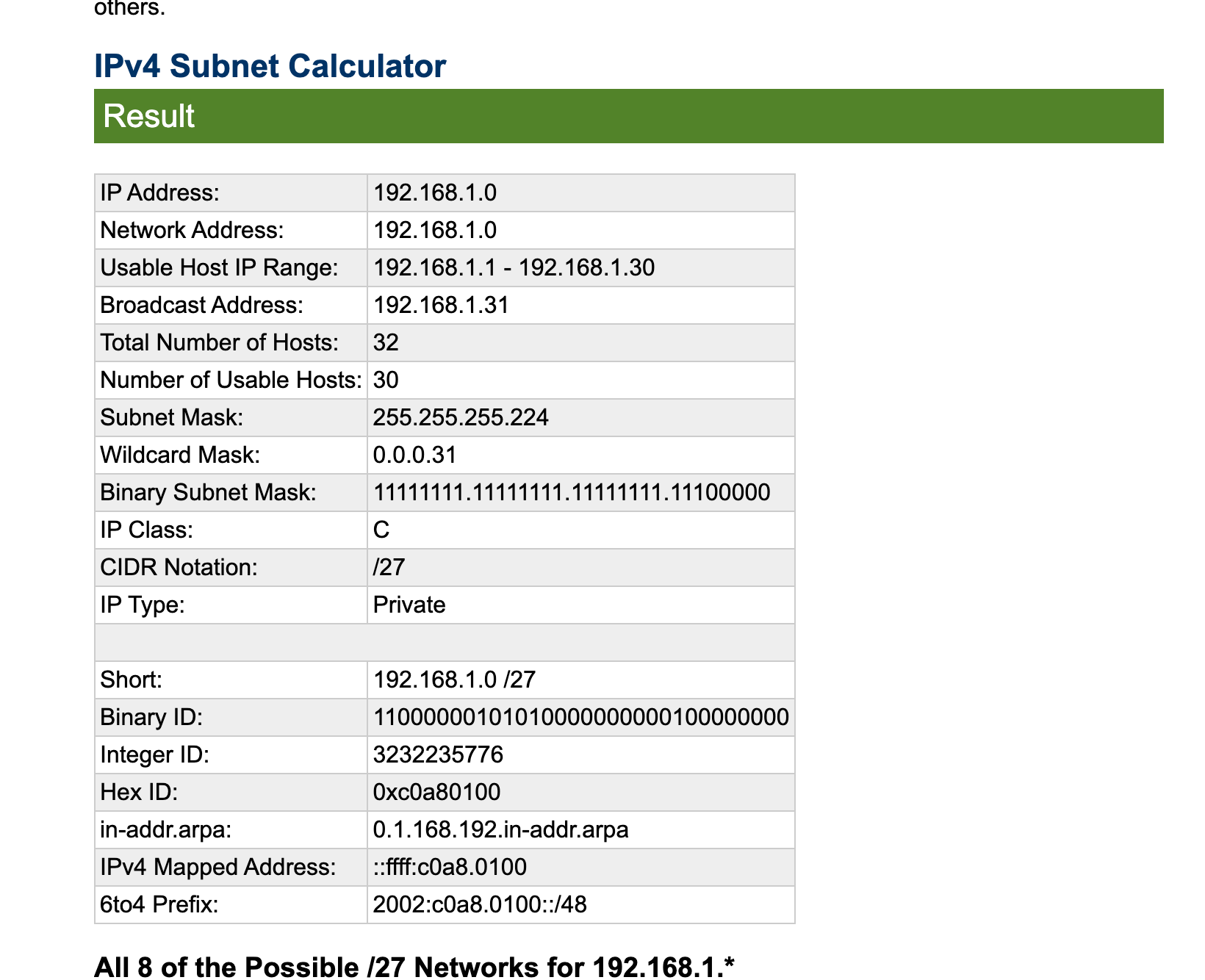
(subnet I am using)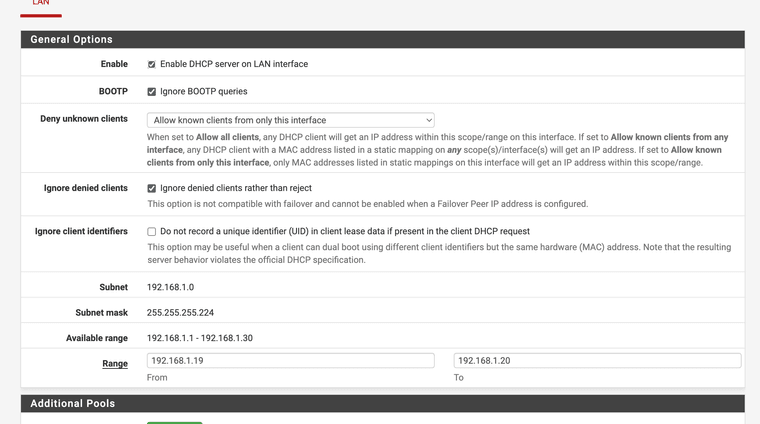
(configured in DHCP server)Addresses they are all statically assigned. I do not use any that are dynamically assigned from a pool. I try to limit this as the wifi system runs on 192.168.1.2 in bridge mode and relays the addresses.
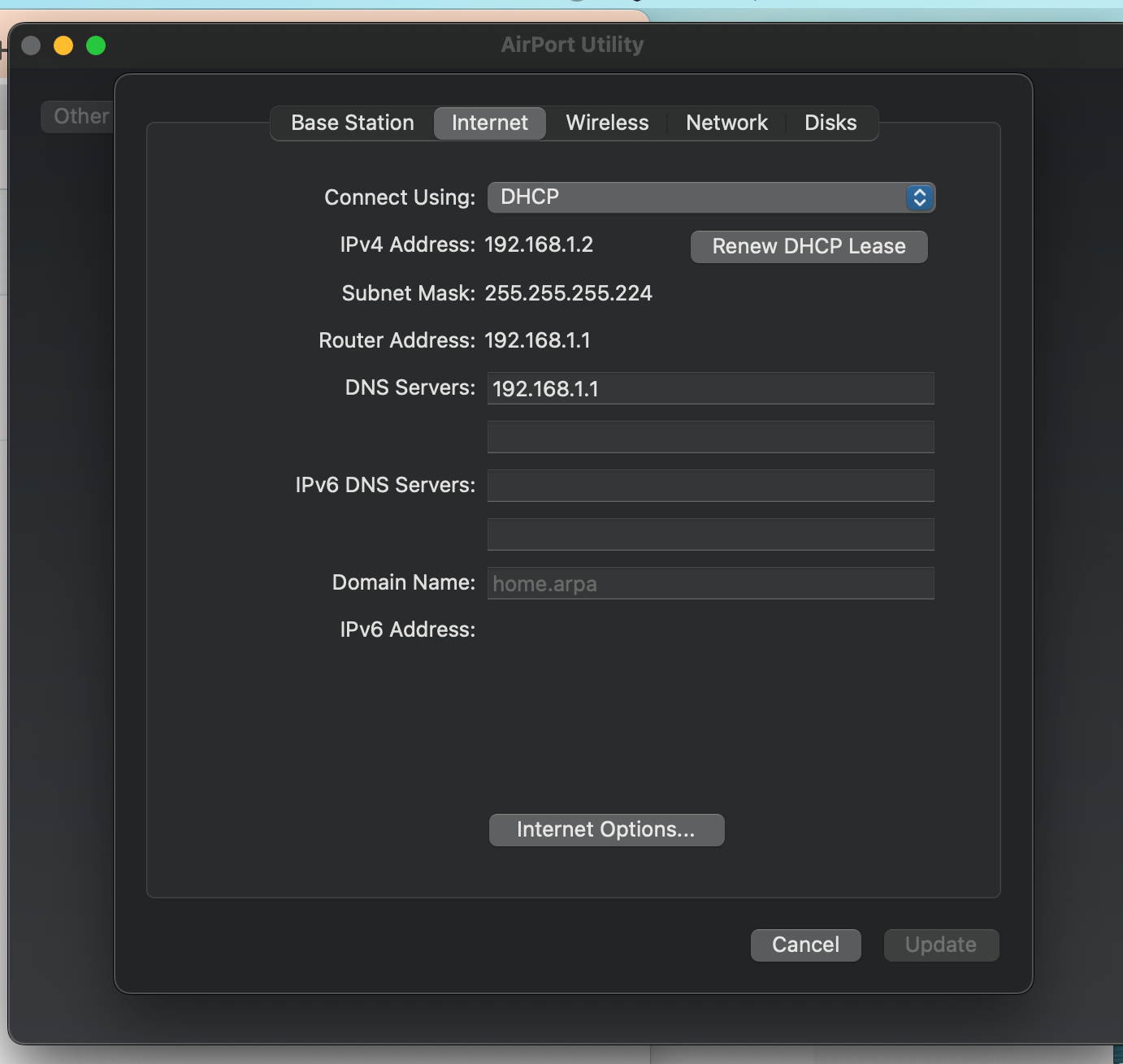
(system uses bridge mode for wifi)
(auto configures with 192.168.1.1 as the gateway to get off network)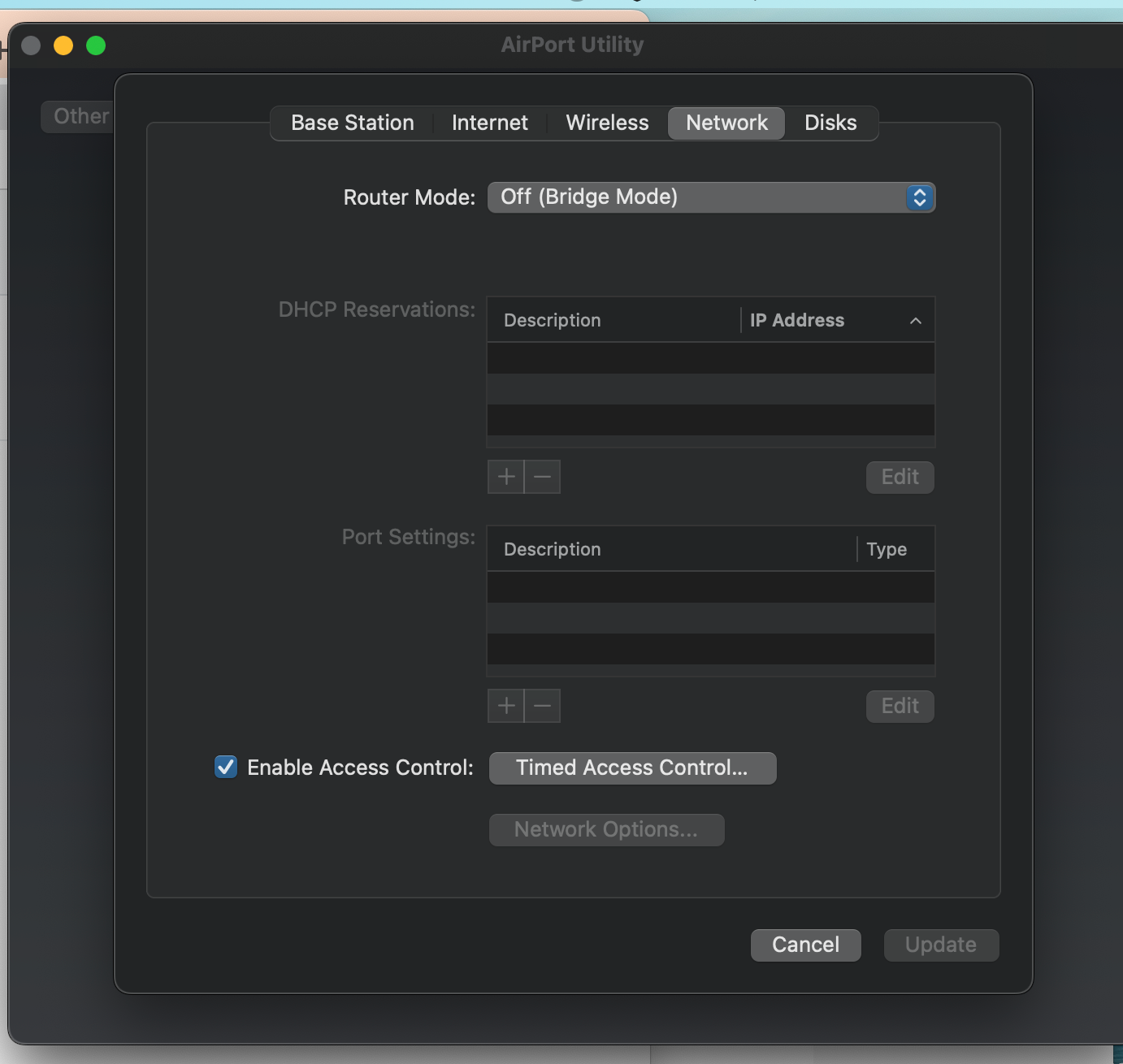
wifi uses timed access with static MAC alsoThis was my reason for thinking well maybe Squid needs to know the arp table entry, as I was having null errors on clam AV updates.
This was the first time I have seen it show no error on a update without having to do it multiple times,
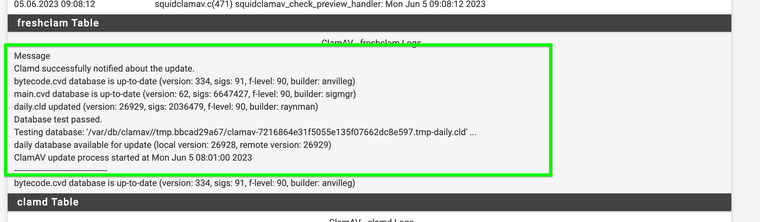
@Gertjan I have it listed under the arp cache as permanent just like before without the static entry.
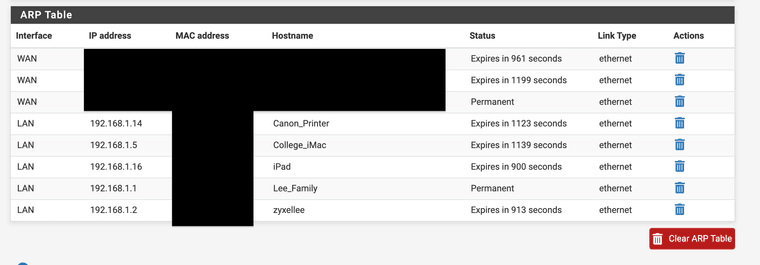
Does it matter or should I delete the entry? I was surprised to see that Clam AV no longer says NULL IP anymore when it updates.
-
@JonathanLee I don't use clamav so no idea what it use to do or does now for IP.
But if you are using a /27 then sure a range of .19-20 is pretty small for available IPs.. would allow you some IPs to set static. Setting a reservation for pfsense IP seems pointless to me, but it not going to "hurt" anything. Its never going to use it that is for sure - but hey if it makes it easier for you to read and know by looking at your reservations that IP is in use..
While I am all for proper sized segments.. it is also really common to just use a /24 for home or smb segments.. This easy allow for setting the 3rd octet for your different segments to know really easy without having to do any cidr math on which segment this IP is on ;)
There is plenty of space in the 192.168 range that using a /24 for each segment/vlan your going to setup allows for lots of vlans/segments..
No need to worry about running out of space, etc. And I also set the vlan ID to match the segment, for example my 192.168.4/24 - guess what ID that vlan has - 4 ;)
What drives me nuts is seeing use of say 10/8 or 192.168/16 - /27 seems a bit tight, but hey its your network if you want to use /27 go for it..
-
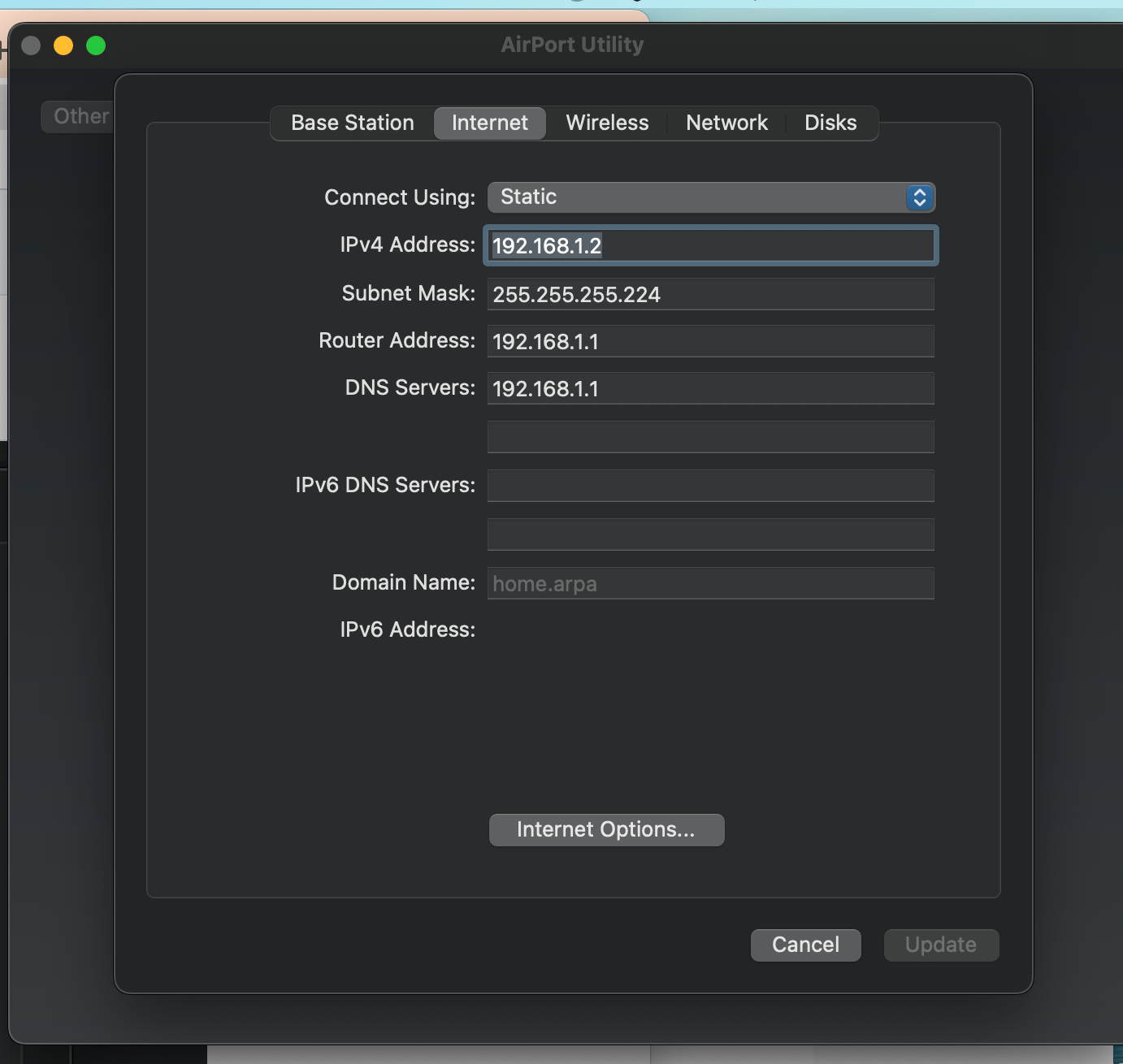
Wifi I just changed to static
Just to confirm the DHCP server on the firewall should exclude a mac/ip mapping for the firewalls interface? I have deleted it. Thanks
-
@JonathanLee said in DHCP server and Firewall as static entry:
DHCP server on the firewall should exclude a mac/ip mapping for the firewalls interface?
Yes it is good practice to not include IPs your going to use statically on your network inside the range of your dhcp server.. I mean pfsense won't even let you set a reservation for an IP that is inside your dhcp scope.
If you do not include it in the range of IPs the dhpd can hand out, then it would be impossible for the dhcp server to hand out a duplicate.
But even you did include it, again unless you on purpose disable the ping check, the dhcpd pings an IP before it hands out a lease.. It should be almost impossible for it not to be able to ping its own IP address, so even if the range included the IP of pfsense - it should never hand it out.
But I see no need to set a range that excludes your pfsense IP, and also set as reservation (that is would never use) as well..
-
@johnpoz "But I see no need to set a range that excludes your pfsense IP, and also set as reservation (that is would never use) as well.."
I was researching this to see if I could fix Squid Clam AV intermittent NULL ip error I was surprised it worked and showed with the green up check mark. Yes the Arp cache/table marks that mapping as permanent, I wonder if Squid had issues getting to it or something. I just thought last night test it, it's not gonna work but give it a go, and the thing went to green and recognized it inside of the mapping, after that I thought hmmm shouldn't that be blocked as it's the LAN interface of the firewall. Thanks for your reply
-
after other tests the NULL issue with Squid still randomly occurs even with the static entry when testing further. System normalized
-
@JonathanLee because setting a reservation that would never be used does nothing as already stated
Why you thought it had anything to do with whatever you seeing clamav I have no idea
-
@johnpoz I don't know :( I thought let me give it a try, that NULL IP thing is so random.