Feature Request: Aliases options for use with Advanced option Source OS Access control list
-
Hello Fellow Netgate community members please tell me what you think about this idea?
Pfsense has the ability in theory to be the first firewall to compartmentalize docker os signatures apart from the host machines and actually control traffic in that manner:) Wouldn't that be cool? Again, invasive actors only attack walls at their weakest areas. What if we had an option for inputting custom os fingerprints into an alias as a set? That way there would be no need to update the older aged os fingerprint file as we could essentially add custom fingerprints sets as needed.
(Example)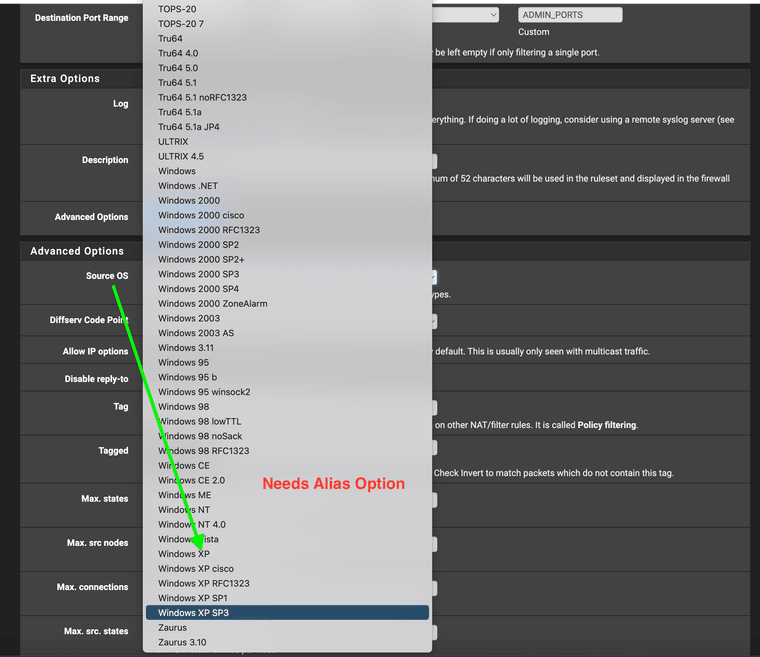
(Image: Currently this security tool on pfSense has an outdated database thus it is limited by today's standards)Current request for feature: https://redmine.pfsense.org/issues/14444
Known issue:
https://redmine.pfsense.org/issues/7260
Github with p0f code:
https://github.com/p0f/p0fThus the idea for a new feature, a way to just add useable custom fingerprints. I was able to find a os fingerprint manually. Again, how can I add it or make use of it in a security sence? Maybe just for what we use on the network? Leading to, The example of mainstream need: 200 machines that use the same Windows 11 OS and a system admin adds in that fingerprint for an ACL to pass traffic for only Windows 11. With such options the firewall in theory can block and distinguish between different Operating Systems again. Take for example Docker's new bleeding edge container of Kali's pentesting OS. Something like that can data marshal the NIC card on a machine. Docker for one does not have the same fingerprints as the primary OS so in theory the firewall would know what traffic to allow and what to stop at an OS level even with the newest Docker containers. It is harder to spoof a custom fingerprint as the invasive actor would not know what is in use, and to just add that in would give users that full security tool back, Thus, aliases options for OS fingerprints are needed to bring this security tool back.
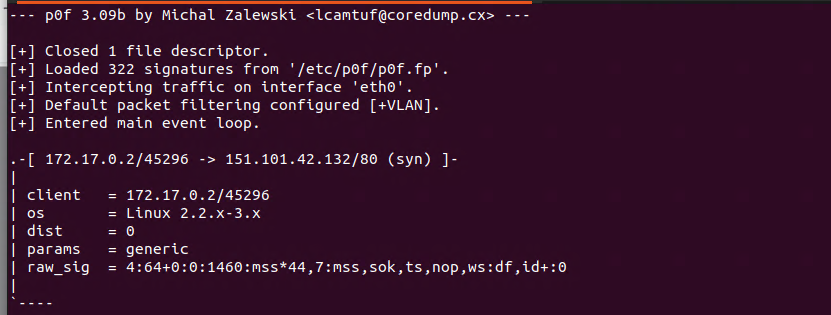
How I got my raw os signatures is listed below.
running: p0f -i (interface)
Outputs this example of what would be used with OS aliases: 4:63+1:0:1460:65228,7:mss,nop,ws,sok,ts: :0
this is freeBSD 13.12 on Hypervisor VWe know pfSense os database needs updated signatures, and p0f fingerprinting software still works great. So, the tool and features are already built into pfSense and should work great with custom aliases.
Again, to add in the signatures, the GUI needs an alias to link them into an access control list.
I am aware that the current tool is outdated because of the associated signatures. Ref: https://redmine.pfsense.org/issues/7260
Leading to this post bring to light an idea on how to activate this feature again. We can do so with custom use fingerprints and not need to update the full f03 database.
(Image: Laptop running Ubuntu with a Docker container running raw signature)sudo apt install docker.io -y
sudo docker run -itd --rm --osfingerprints debian
sudo docker exec -it osfingerprints shentering the debian container
at shell
apt install net-tools
netstat -i
got eth0
apt install p0f
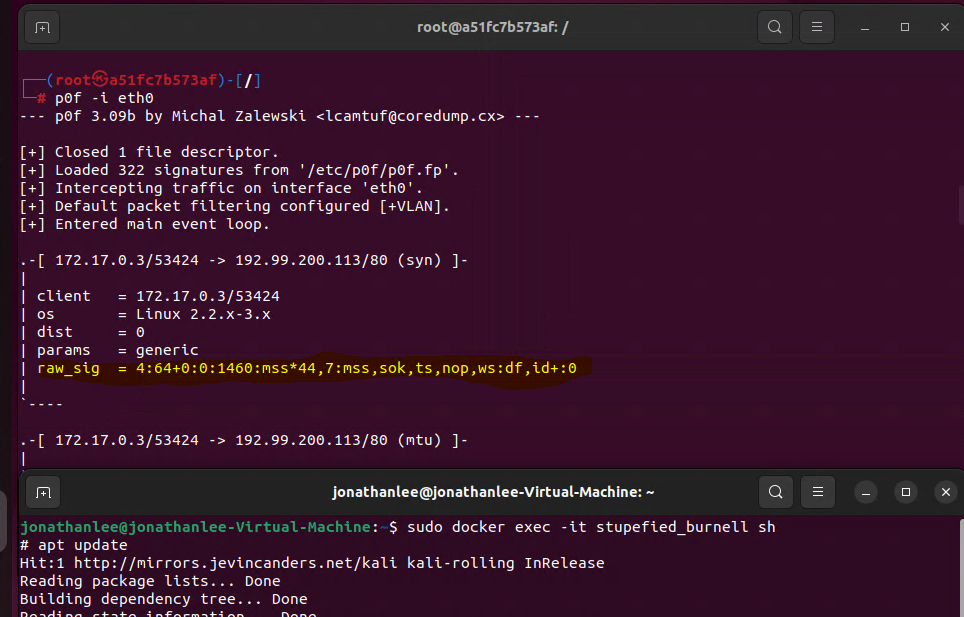
p0f -i eth0
open new tab login to docker container again and generate traffic proves that the signatures are different for a docker container OS installed in Ubuntu that is running inside of Hyper-V on Windows 10raw_sig = 4:64+0:0:1460:mss*44,7:mss,sok,ts,nop,ws:df,id+:0
We can see the differences within the docker debian container and the freeBSD version.
Therefor we could in theory also see them at the firewall with a custom fingerprint alias for access control lists.
(Image: Docker Kali Container being fingerprinted passing traffic with other login)
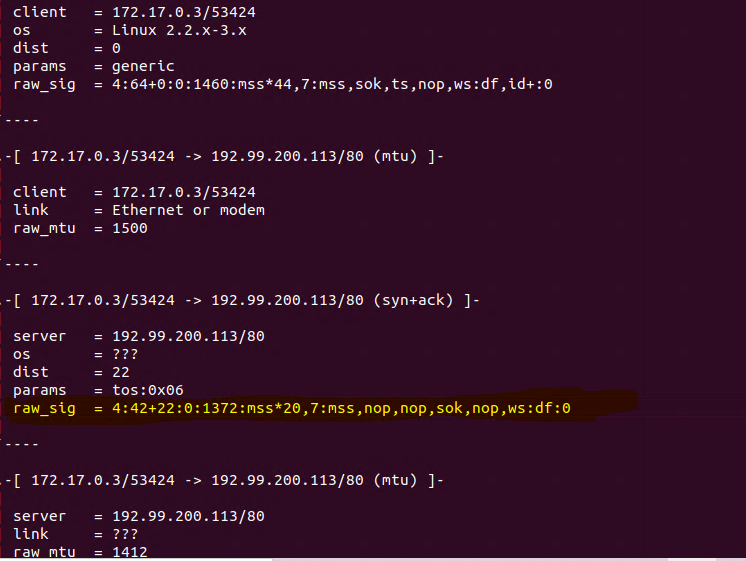
(Image: raw signatures)
Docker’s Kali Container is: 4:42+22:0:1372:mss*20,7:mss,nop,nop,sok,nop,ws:df:0In theory we could just adapt an Access Control List to whatever Docker container OS fingerprint you need blocked out on a network, or a set of os fingerprints used by known invasive actors. Again, the pfSense software would need an OS fingerprint Aliases option to help with such security feature use.
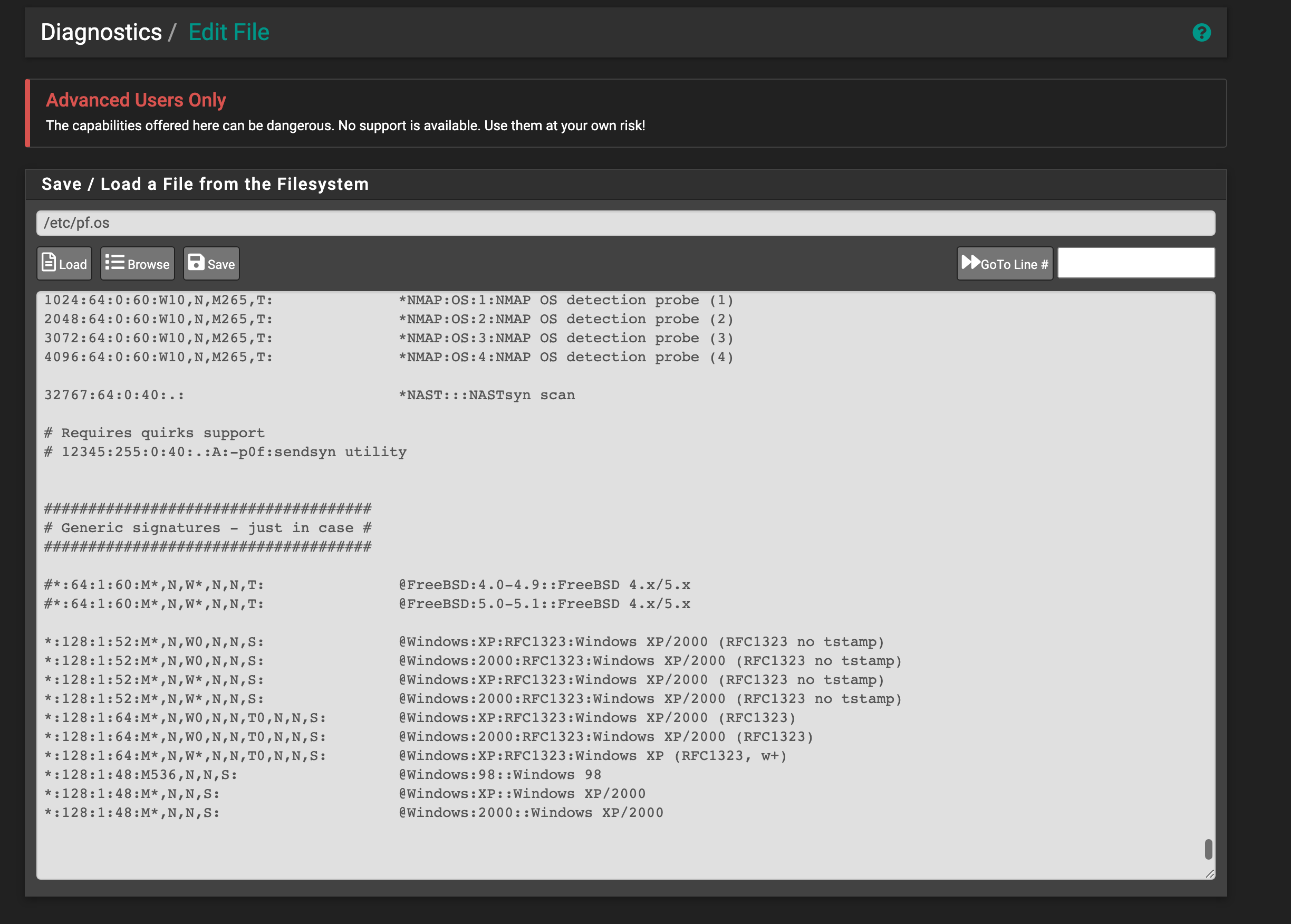
Here is the current location of the os fingerprint database used inside pfSense for advanced access control lists. As we can see it's missing the current operating systems in widely in use today.
Path = /etc/pf.os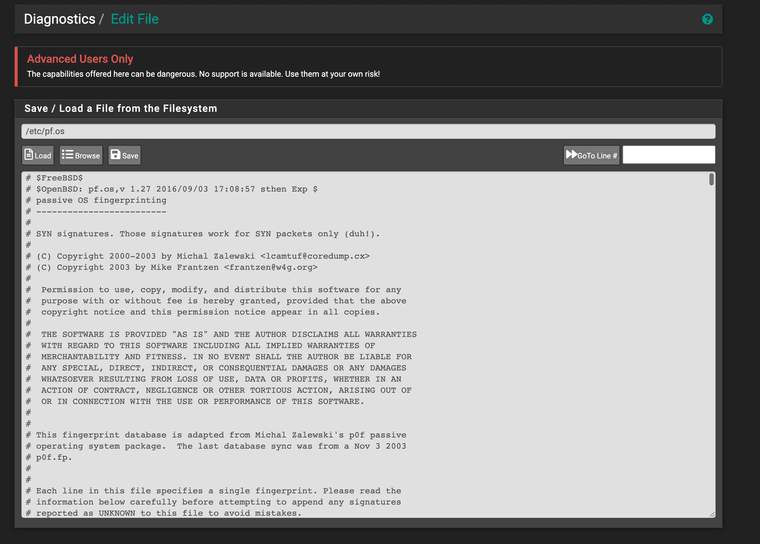
(image: /etc/pf.os)
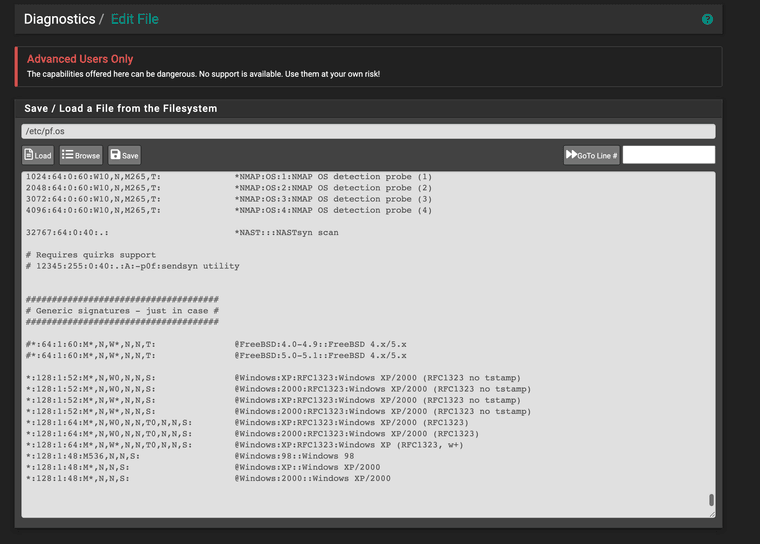
(Image: /etc/pf.os)
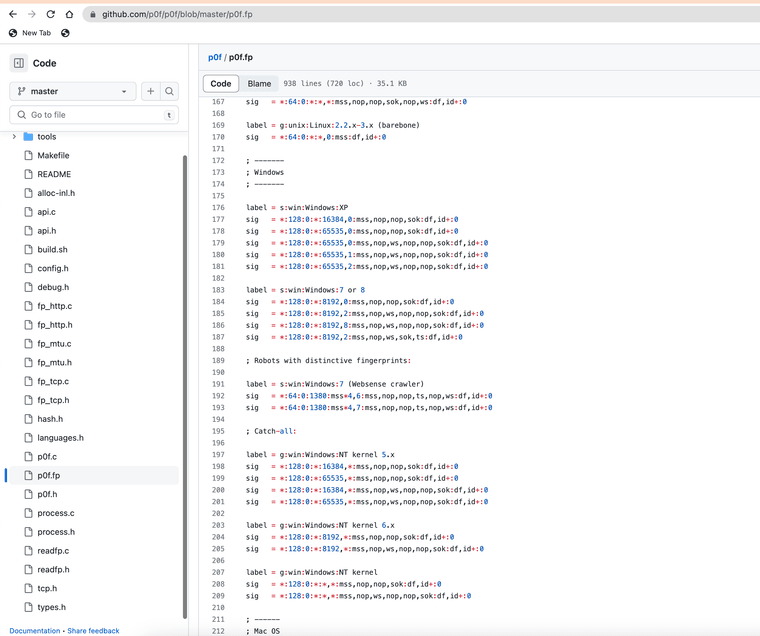
(image: https://github.com/p0f/p0f/blob/master/p0f.fp) -
Or can we manually update and start to add docker signatures?
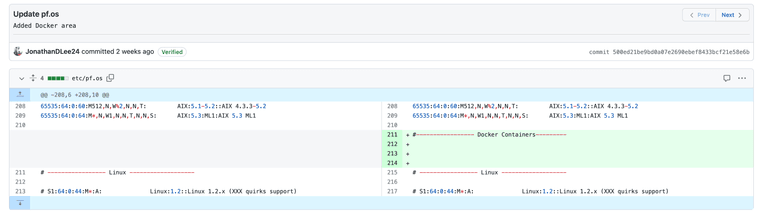
(Image: https://github.com/openbsd/src/pull/39/commits/500ed21be9bd0a07e2690ebef8433bcf21e58e6b) -
I have absolutely no idea what you’re talking about.
-
@JimBob-Indiana Thanks for the reply,
Main Issue: pfSense's ACL (access control list) under advanced has a source OS option, this would work again if we could add OS alias fingerprints into it bypassing the outdated OS fingerprint database that is showing. If we could just use fingerprints we need or custom fingerprints this full source os security tool will function again. The last Windows entry for the database is Windows XP. The information above is me showing how to fingerprint and help to provide context with this issue.
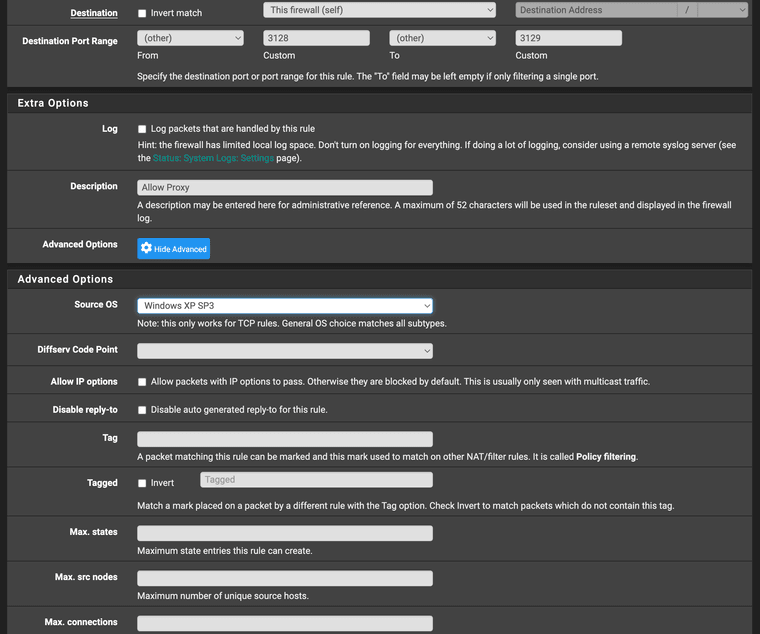
-
@JimBob-Indiana in the photos I was running p0f fingerprinting on Docker's bleeding edge Kali Pentesting container to show case what I learned, that containers have different signatures. Leading to if any invasive container was running the firewall should be able to compartmentalize that os fingerprint on the container from the host OS fingerprint and only allow traffic that is approved. The container data marshals the NIC (network interface card) but the signatures for traffic being passed I found are different. I however still need to run Wireshark or something to see if the signatures are different when leaving the host OS. The screens with code is the current outdated databases holding the OS fingerprint signatures. Each OS (operating system) has a different signature. If your on a office network most often all the machines use the same OS and vendor ID, so it would create a secure way to see if a invasive container is running on a network. I have learned in college that 3rd party containers are a huge cyber security issues, most antivirus can't scan them, and 3rd party software made to find them can't find them all. It's a weak point in cyber security, I want to find something that can start to make it secure. Again Netflix and other companies use containers alot I have learned. Even Facebook, containers spin up and spin down as needed but whole operating systems can run discreetly on them invasive ones as well as admin approved containers. This could in theory help bring to light the differences on a PfSense firewall level.
-

freeBSD Jails, Kubernetes, Docker containers
<---VS--->pfSense and Squid Proxy OS fingerprint identification
-
 J JonathanLee referenced this topic on
J JonathanLee referenced this topic on