Please help me oh mighty gods of pfsense and nat reflection
-
@viragomann i will try that, im afraid im not exactly great on that , but im try my best.
as for your suggestion , i just did a sample here, and it works well.. but yes... im gonna have to notify every client, change every link in every station.
and will be exactly like this
host1.mypfsense.com > 172.16.100.11
host2.mypfsense.com > 172.16.100.12the ultimate bummer, is that, one might think it would be really nice to use that oportunity to have outside domainnames that can be typed without the ports and redirected apropriatedly,...
but, if i do that, i will have to use a link for for external (with no ports) and a link for internal (with ports)... and to have 2 links will drive people nuts...so unfortunatelly i will be creating those subdomains with the redirects without ports,, and use the ports in every link so the external and internal links match.
thanks for all your time and attention
greating from brazil!
-
@fagoti
Yes, when using certain ports with NAT reflection, it cannot be simply replaced with DNS overrides.However, there is a simpler method to detect asymmetric routing, assuming the issue concerns to TCP connections:
In Status > System Logs > Settings ensure that "Log packets matched from the default block rules in the ruleset" is enabled.After facing an issue check the firewall log. If you have asymmetric routing you would see block of TCP packets with other than SYN flags, e.g. RA, PA.
-
@fagoti said in Please help me oh mighty gods of pfsense and nat reflection:
active directoty /dns - 172.16.100.1
main local network 172.16.0.0 / 16
routers 172.16.200.0 / 24Ok this problematic - so your lan is 172.16/16 but you have some other router a 172.16.200/24 - that overlaps.. Can you do a drawing.. If you have a downstream router that really should be on a transit, unless this downstream router is doing nat? if that is the case why would it be on some 172.16.200/24 that overlaps your /16?
-
thanks for trying to help too john,
my lan is indeed /16 and the subclass 200.X is reserved to routers
then , this routers are all 200.x on wan and have dhcp 192.168.x.x for their lan.client 192.168.x.x access without problems servers on 172.16.x.x
but those routers are not using nat of any kind.
-
@fagoti so its really just 172.16/16 your just putting all your routers on 172.16.200/16 range of IPs
but those routers are not using nat of any kind.
That is going to be asymmetrical, if your downstream routers are not doing nat, then that network from your upstream to downstream should be a transit network, no hosts on it..
If I am understanding yoru setup this is asymmetrical.
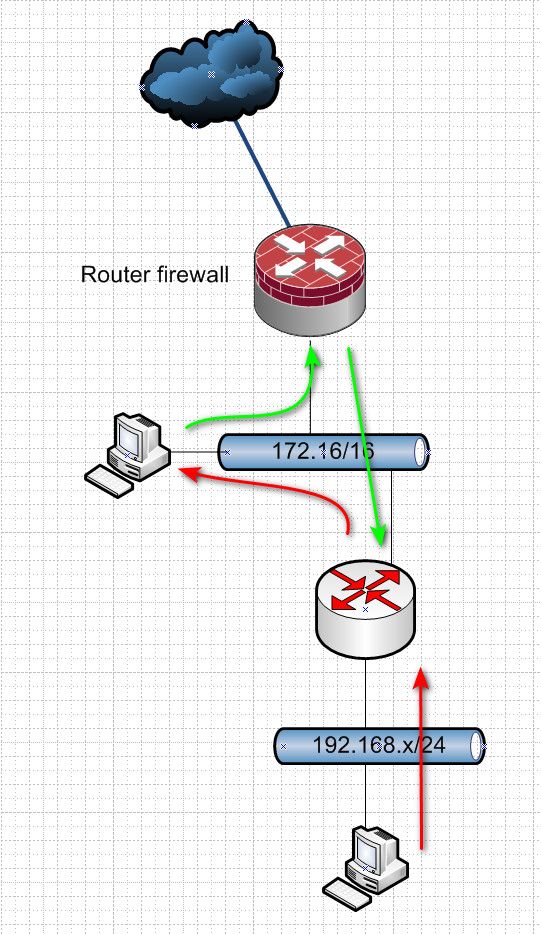
either direction ends up with asymmetrical flow, unless you were doing host routing on the clients on your 172.16/16 network
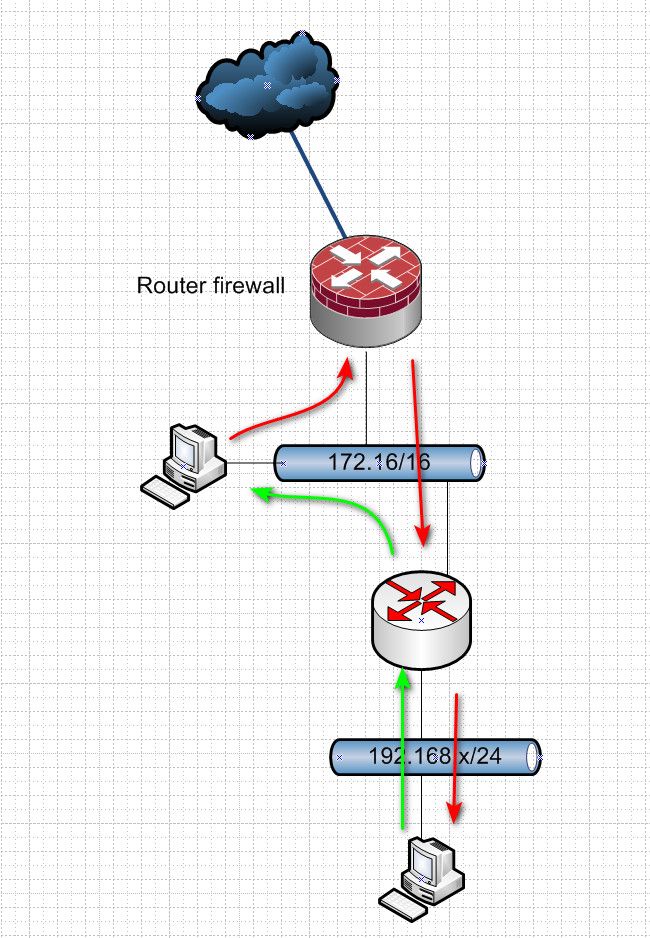
When you use downstream routers that do not nat, you should be using a transit network.
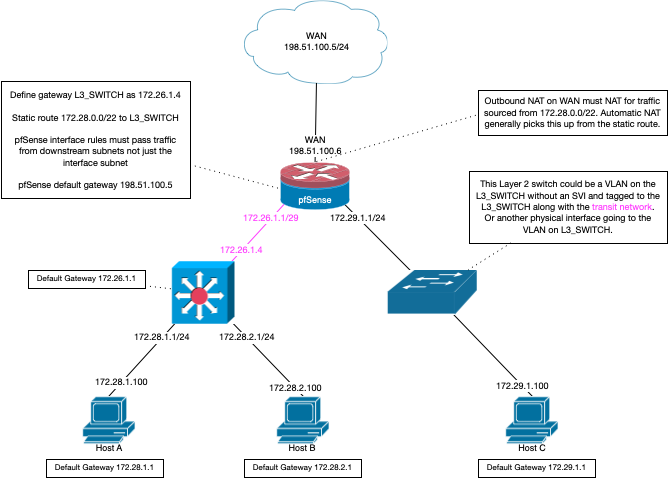
-
@johnpoz oh my, you even made diagrams... :) , thanks again, but now it got a little overwhelmed with that many networks and information
i wont be asking for more until i manage to study this with the same care and fully understand it
but it seems like a lot of changes for my already huge network.
-
@fagoti said in Please help me oh mighty gods of pfsense and nat reflection:
but it seems like a lot of changes for my already huge network.
Creating a transit is not a lot of work.. But running downstream routers that don't nat are going to cause you all kinds of grief without a transit network.. Or doing host routing on ever host..
Transit network is the correct solution..
-
im trying to reply but i keep receiving akismet spam message :/
-
im gonna try breaking my reply in parts
-
It seems you know what you are talking about.
I will give it a shot on a smaller scale here. -
I have just finished doing the "B PLAN" kindly suggested by @viragomann , and its working,
its not pretty, and has lots of places to check when it goes bad,.. but works.
i will be planning how to change all those links for everyone...
but even if i later manage to use your refined transit idea, i can still use those new links i build for split dns, so.. i guess its a good idea to go all the way with it.
-
thanks john
and by the way @viragomann thanks again, because of your quick tip i ended up improving my understanding of my win.dns features.
-
@viragomann i managed to implement a working split dns here. im quite satisfyied.
i still want to test @johnpoz advices. (but its crazy here, i have like 50 routers.. i think it would be a mess to go with it)
-
@fagoti
The transit network is needed if devices in the main network 172.16.0.0/16 should be able to communicate with devices in 192.16.0.0/24 behind routers. I didn't consider that this would be desired before.However, if you need this you can simply do that with a VLAN on the same wire. Create a VLAN on pfSense and on the routers, ensure that it doesn't overlap with other subnets, and point a static routes on both routers for the network behind them to the VLAN IP of each other.
-
@fagoti said in Please help me oh mighty gods of pfsense and nat reflection:
have like 50 routers..
Why and the F would you have so many routers.. But ok if you had like 2000 of them you could still put them on a transit network..
What are these routers.. Why would you need so many? What are they?
-
@johnpoz its a huge network... spread among a number of buildings and neighborhoods.. some of them with 20 or something rooms...
and on top of that, lots of different models of routers, more than one ptp optic fiber provider, some vlans, its pretty messy...
but its working.
and with the split dns i managed to make a little more time on that masterplanning of a better topology :P
-
@fagoti are you running in a mesh topology setup? You could also test out changes I learned with GNS3 it's a virtual network system. Just set up a virtual test with virtual versions all the routers and items all airgapped for your test. A virtual research test version of your network. GNS3 also lets you load OS onto VMs even add in servers and have it function if needed while testing it. Just double click on the host and it opens. Our cybersecurity Professor showed it off on our last days of class. It's cool. Wicked cool. That reminds I want to play with it tomorrow.
(GNS3)Ref:
https://gns3.com/I would also start testing out whitebox routers up so I could push down changes to all the routers at once from the control system. also know as SDN (Software Defined Networking).
-
-
@JonathanLee we are.
i didnt know that GNS3 system. seems like a great tool. ill be looking into it.
thanks for that great tip -
@JonathanLee hahahahhahahha lol
