239.255.255.250 Multicast address can it be used with possible WhisperGate and or Malware?
-
@justsomeguy6575 @mtarbox @BBcan177 @SeventhSon
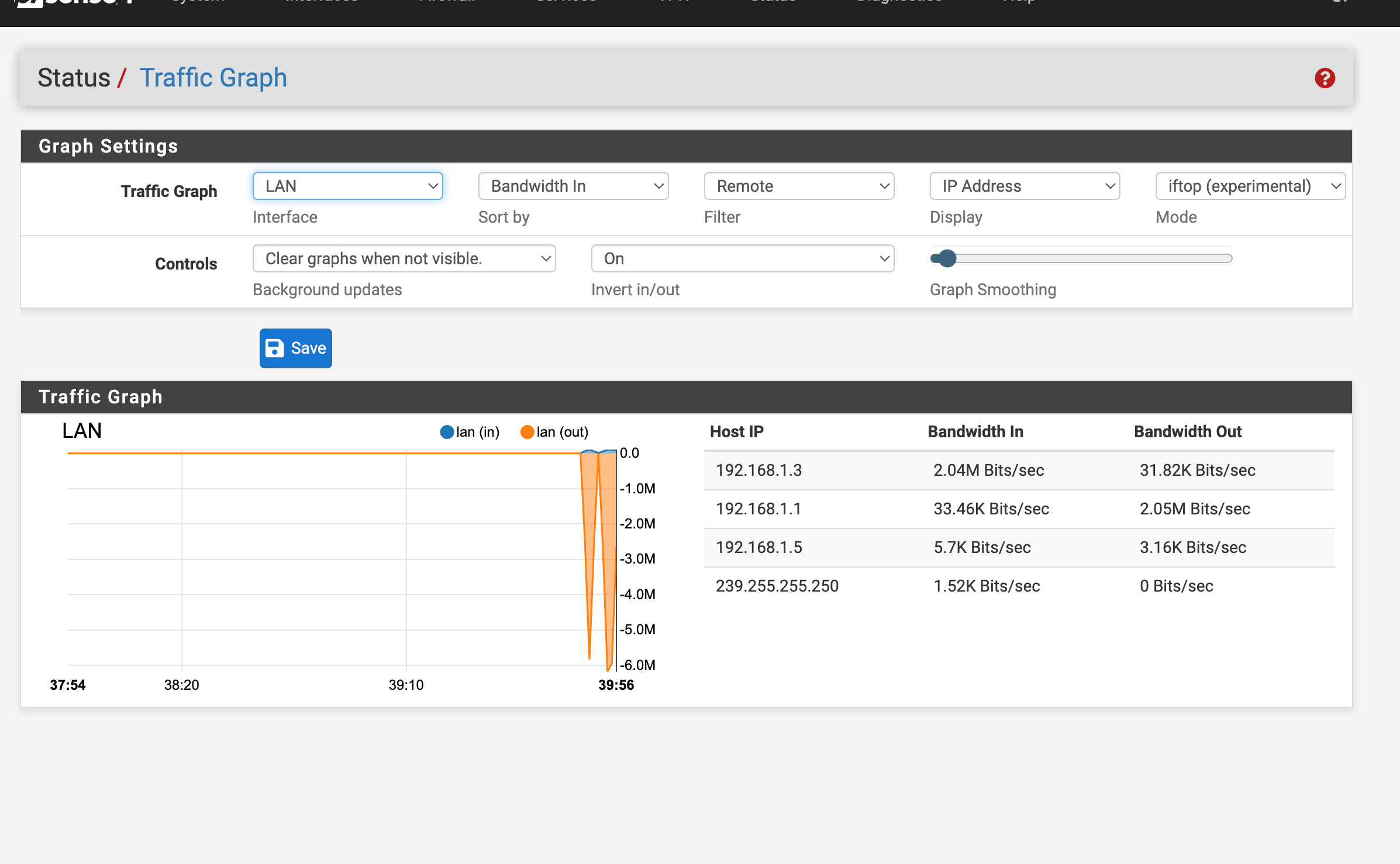
Can anyone else confirm that this IP address 239.255.255.250 can in fact cause issues?
per @johnpoz This is a multicast address right?
Ref:
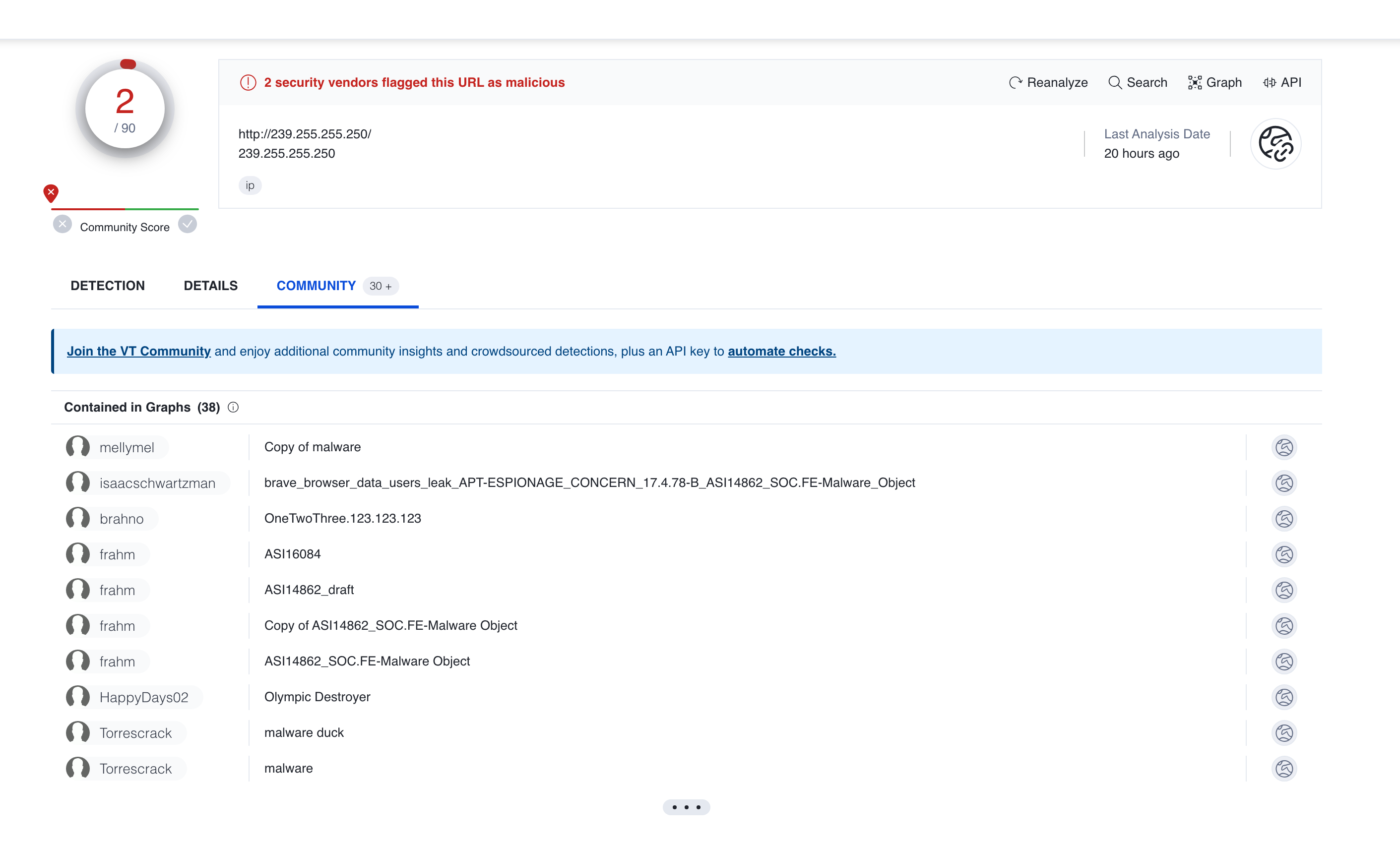
http://www.steves-internet-guide.com/introduction-multicasting/I have looked it up on Virustotal and confirmed it is also used for malware as an invasive bogon address.
I keep having attempted UDP connections to it.
My question is for a home network what are the requirements and recommendations for protection form abuse with this address?
-
@JonathanLee said in 239.255.255.250 Multicast address can it be used with possible WhisperGate and or Malware?:
239.255.255.250
https://en.wikipedia.org/wiki/Simple_Service_Discovery_Protocol
Can promise you that pretty much any network would see that traffic - Pretty sure for example your windows machines would be using it.. Lots of things use UPnP to discover stuff..
Why don't you take a look at who is sending it. And turn it off there if you don't want to see it or use it.
-
@johnpoz But it should be listed as a bogon address for wan side for that subnet and it's not listed I have noticed.
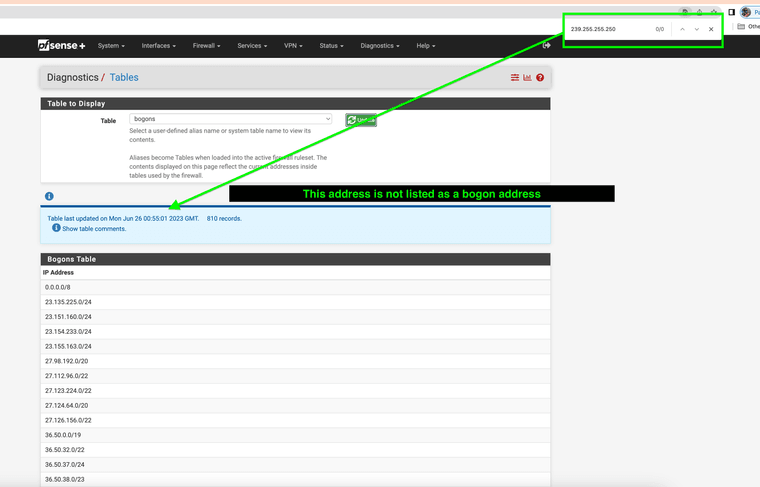
(physical address not listed as bogon address)
(multicast subnet not listed as bogon address) -
@johnpoz said in 239.255.255.250 Multicast address can it be used with possible WhisperGate and or Malware?:
239.255.255.250
Ref: ipinfo.io
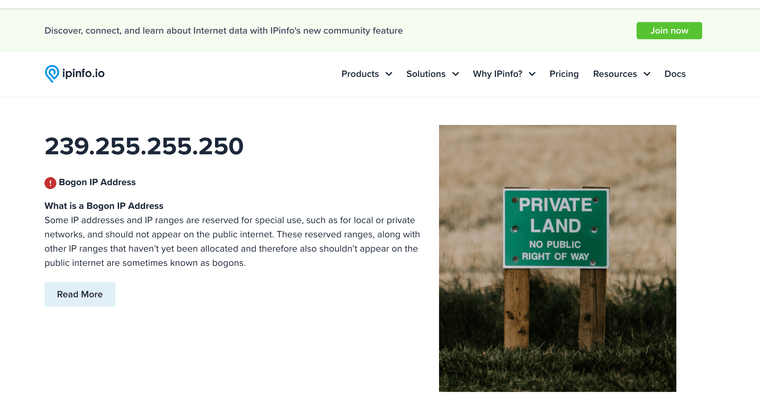
(Bogon subnet seems to be missing from pfsense lists) -
@JonathanLee said in [239.255.255.250
(multicast subnet not listed as bogon address)
Sure it is what do you think 224.0.0.0/4 covers?
-
@johnpoz thanks, I did not see that before.
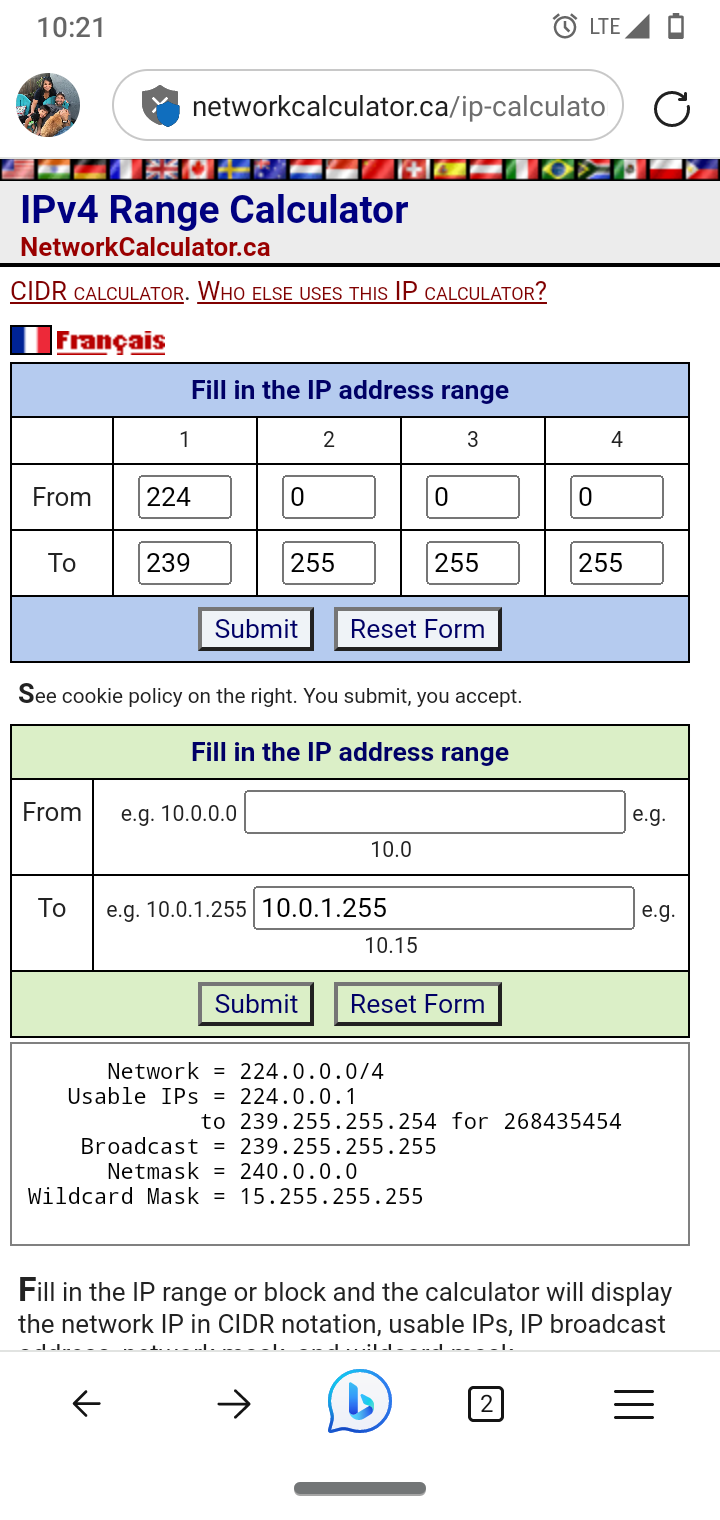
-
@johnpoz best practice is to just block the bogons on the
LANWAN side. Does the DNS resolver know not to resolve bogons?Correction I was in a parking lot picking up groceries.
-
@JonathanLee no you would never block bogon on lan side
You seemed to have gotten yourself all worked up over a few multicast packers that yeah your going to see on really any network because noise boxes like windows love to scream it out every few seconds
-
@johnpoz thanks for the info
-
@johnpoz This is what started to confuse me on my M1 apple I get this when I run a arp -a
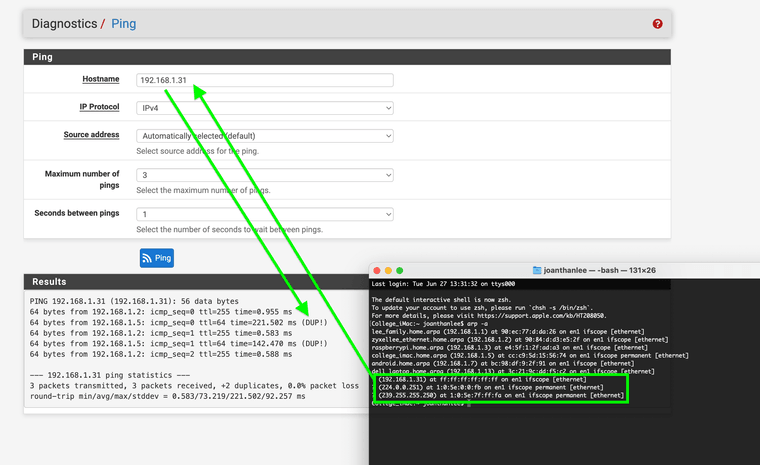
192.168.1.31??
I have no 192.168.1.31 I assume it's a container on the Apple M1 for the cache that is enabled on it.
However when I ping it on the firewall I get replies from the Apple M1 should it be accessible outside of the device itself? You can see the 239.255.255.250 listed when I run the arp -a on the apple. It does not list it in the firewall when I run arp -a.
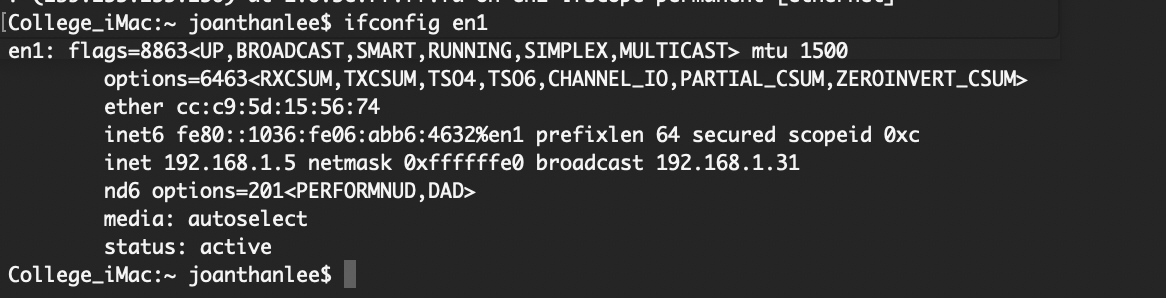
239.255.255.250 does not have all FF for its mac address however 192.168.1.31 does. I have no VM ware installed on the apple I have removed the virtual box software because it would not run at all it would crash when you tried to run my older VM of xenix that works on other systems.
-
@JonathanLee isnt it possible that the M1 has proxy ARP running?
-
@JonathanLee its its at all FFs its a broadcast address.. You have mask set at /27 says so right there in your ifconfig.. see the "broadcast 192.168.1.31"
If you send a ping to broadcast, then yeah your going to get an answer ;) if there is anything on that network that will answer ping..
here when I send a ping to .255 broadcast on a /24 in this case 9.99 answered (one of my switches is on that 9.99 address)
$ ping 192.168.9.255 Pinging 192.168.9.255 with 32 bytes of data: Reply from 192.168.9.99: bytes=32 time=7ms TTL=64 Reply from 192.168.9.99: bytes=32 time=1ms TTL=64 Reply from 192.168.9.99: bytes=32 time=1ms TTL=64Why would you think a multicast would be all FFs? But look, your going to see multicast on pretty much any network.. Lot of devices/OSes love to squawk on multicast.. I wish I could find a way for plex to freaking shut up for example...
ash-4.4# tcpdump host 239.255.255.250 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes 16:56:51.900218 IP nas.local.lan.51573 > 239.255.255.250.ssdp: UDP, length 101 16:57:01.901295 IP nas.local.lan.51573 > 239.255.255.250.ssdp: UDP, length 101 16:57:11.901589 IP nas.local.lan.51573 > 239.255.255.250.ssdp: UDP, length 101 16:57:21.902645 IP nas.local.lan.51573 > 239.255.255.250.ssdp: UDP, length 101 16:57:31.904568 IP nas.local.lan.51573 > 239.255.255.250.ssdp: UDP, length 101I took to blocking it at my switch.. I looked and looked to try and get plex to stop it, but it just wont shut up..
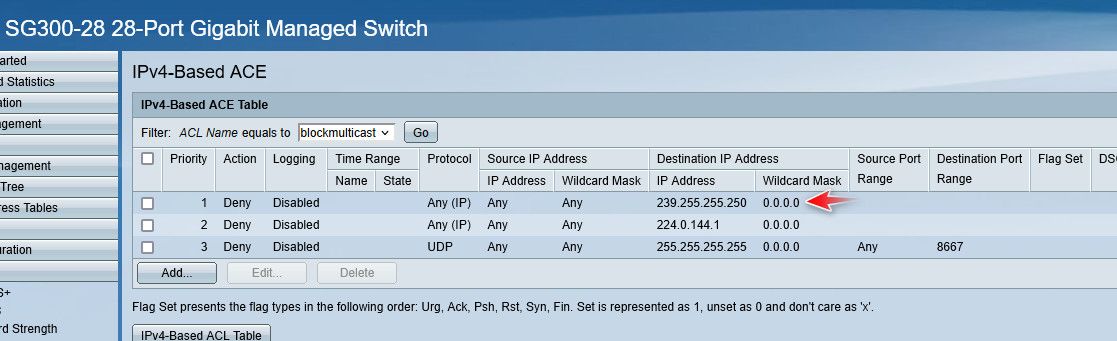
If you don't like seeing the in your firewall logs, look to see what is sending it and try and turn it off there - you can really quiet windows down if you turn off some services, and make some reg changes. If it really bothers you get a switch that allows you to block it.. Or you could make some firewall rules to block it and not log it, or allow it if its say mdns and your wanting to discover over vlans with something like avahi...
But yeah on pretty much any network your going to see a bunch of it..
edit: same with broadcast - see that port block on 8667, my wifi light bulbs send out tons of those!! So I block it at the switch port the AP are connected to, so it won't go to the rest of my network..
edit2: look here my other switch at 9.98 chimed in with broadcast ping
Pinging 192.168.9.255 with 32 bytes of data: Reply from 192.168.9.99: bytes=32 time=1ms TTL=64 Reply from 192.168.9.99: bytes=32 time=1ms TTL=64 Reply from 192.168.9.99: bytes=32 time=1ms TTL=64 Reply from 192.168.9.98: bytes=32 time=1ms TTL=64 Reply from 192.168.9.99: bytes=32 time=1ms TTL=64edit3: here on one of my other networks 2.200 is answering
user@NewUC:~$ ping -b 192.168.2.255 WARNING: pinging broadcast address PING 192.168.2.255 (192.168.2.255) 56(84) bytes of data. 64 bytes from 192.168.2.200: icmp_seq=1 ttl=64 time=331 ms 64 bytes from 192.168.2.200: icmp_seq=2 ttl=64 time=240 ms 64 bytes from 192.168.2.200: icmp_seq=3 ttl=64 time=160 msWhich is my IPad ;) 192.168.2/24 is one of my wifi networks.