Pfsense and Videoconference is not a perfect match!?
-
I often use video conferencing with Teams, Skype, Zoom, Jitsi, etc.. Works fine. In fact, last week I was on a Teams call for about 1.5 hours. No problem.
-
My guess would also be some sort of link asymmetry with two gateways on the LAN subnet. Like perhaps local DNS using a different WAN IP.
-
My videoconferencing is working. I am using a Cisco small business layer 3 switch with pfsense. I couple of things I did that seemed to help me is I used all upper case for my L3 defined switch gateway in pfsense and I defined the pfsense WAN interface as default. I have pfsense LAN IP setup with a static IPv4 address that exists in vlan 1 on the L3 switch. vlan 1 is defined on the L3 switch with the same network as what I used on the pfsense LAN IP. No vlans are defined on pfsense. And I setup a gateway on pfsense with the vlan IP I used for the L3 switch. And default routing for 0.0.0.0 0.0.0.0 on the L3 switch points to the pfsense LAN IP. pfsense LAN port plugs into an access port defined in vlan1 or whatever vlan you are using. I have used vlan 10 in the past. I am not sure how you have yours setup but this helped me using a Cisco L3 switch.
I think with this setup you could just change your routing statement and route to a different firewall. You would have to decide how you would handle DNS. DNS could be as simple as assigning something like QUAD9 in DHCP in the L3 switch. You could run a local DNS server like Microsoft DNS server forwarding to QUAD9. I guess you could change your DNS local IP when you change your routing statement. And tell everybody to reboot client devices.
-
Thanks for all responses.
The setup is straight forward. I have a Managed Netgear switch in which port 8 is on Untagged VL666 is connected to the ISP via fiber converter.
PFsense is connected to port 1 via Dot1Q in the same Netgear switch. PF is configured with two VLANs, VL1 and VL666 with a single NIC.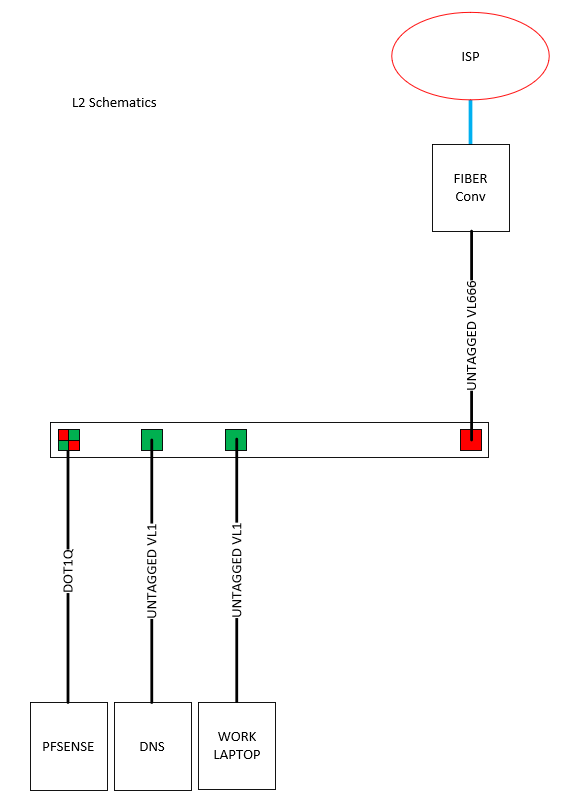
When I do Teams meetings it feels that traffic does not flow as freely as when connected via the Cisco ASA.
I have DNSBL+ Snort running + DHCP. I have 15 rules on the LAN interface
-
@madah999 said in Pfsense and Videoconference is not a perfect match!?:
Snort running
And if you turn that off?
-
Are you using router on a stick with untagged traffic? How do you know how to process the untagged traffic. Maybe I am looking at this wrong. You said 2 VLANs. I guess VL666 and VL1 on 1 interface. On your gateway WAN is default which is VL666. I guess you are using a trunk with 2 vlans. It took me a while to think about it.
Router on a stick is weird with a firewall. Why don't you use 2 interfaces defined with vlans. I guess the WAN since it is untagged it does not need to be defined as a vlan. LAN side needs a to be a vlan to be able to talk with DNS and the workstation.
PS
I have never used Netgear only Cisco. -
@coxhaus said in Pfsense and Videoconference is not a perfect match!?:
Maybe I am looking at this wrong
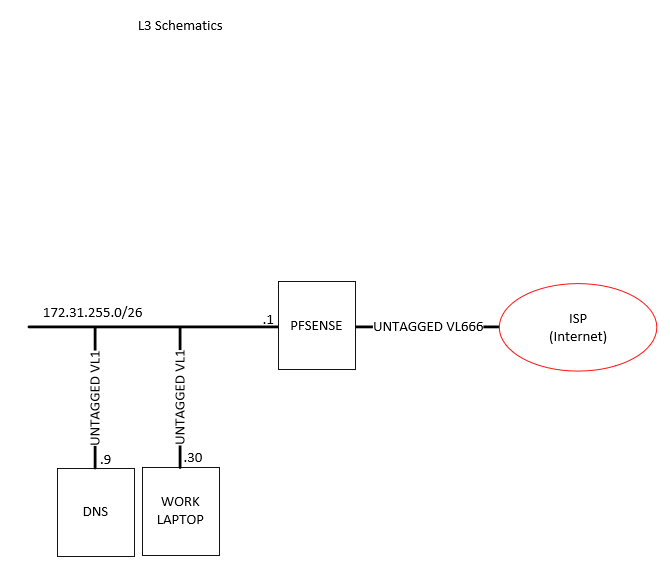
Maybe not - might be a good catch - lists tagged with 802.1q but then his drawing shows untagged for vl666 and untagged fro vlan1? into pfsense - if that is one physical interface one of those has to be tagged..
so a bit confused as well with the L3 diagram
-
I would not want a Netgear switch software standing between my workstation and my DNS server. It seems very unsafe to me. I would rather be behind the firewall. But everybody gets to choose.
You are only logically behind the firewall not physically behind a firewall. There is a big difference in my mind.
His terminology may be Netgear. -
I would prefer to use two tagged VLANs on the trunk rather than tagged (666) and untagged just because it's much easier to make mistakes with tagged and untagged. I'm assuming here that VLAN1 only exists inside the switch. You shouldn't ever use VLAN1 on a trunk directly if you can possibly avoid it.
I wouldn't have any real concerns with a setup like this. It should work fine.
However if there were some layer 2 issue here it would affect far more than just streaming video.
Steve
-
@stephenw10 said in Pfsense and Videoconference is not a perfect match!?:
ather than tagged (666) and untagged just because
But his L3 drawing shows 666 and 1 both untagged..
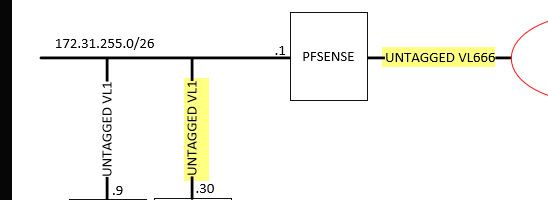
Which wouldn't be good setup that is for sure. If there is only 1 physical interface on pfsense.
What I assumed from his L2 drawing is 666 was tagged into pfsense, and 1 was untagged.. He labeled it 802.1q so assume that vlan 1 is the the default native and would be untagged across a trunk, But then on his L3 he shows both untagged.
edit: but yeah if he was running both untagged into pfsense you would assume he would be seeing much more than just issues with video calls. Not even sure how you could really set that up in pfsense? On the switch sure you could send both untagged, but then there would be no wan connectivity at all since how would pfsense see the wan if was looking for tag 666 and it was untagged?
-
Yeah I assumed the tagging was on the L3 diagram just for clarity (though I'm not sure it helps!) since the switch isn't marked on there.
What is not clear is whether the internal subnet is tagged between the switch and pfSense as VLAN1 or untagged. Either could work but I hate seeing VLAN1 tagged anywhere except inside a switch.
https://docs.netgate.com/pfsense/en/latest/vlan/security.html#using-the-default-vlan-1
I also don't like seeing tagged and untagged traffic on the same link though if I can avoid it. I'd rather see two tagged VLANs (other than 1!) on the trunk to pfSense.
Steve
-
Yes, untagged traffic ends up on the default vlan which can be any vlan.
-
Hi
I have been traveling so I have not been able to respond.
I have made some changes and to my Pfsense which has fix many issues. Yes this is a simple setup with a single NIC computer running Pfsense.
Yes, It is a router on stick which I find is good for a small home office. You need to trust VLAN technology to be able to use router on stick designs.
I trust vlans and vlans is very practical in many ways. I will later on change from VL1 to something else as it is not recommended for security reasons
to use VL1. Pfsense, Netgear and Cisco talk vlan via Dot1q protocol, Cisco used to also do vlans via their proprietary protocol ISL but they have skipped that one
many years ago.I have been using my own DNS for many years because of security and the low latency in DNS resolution. I like to keep my data in my log own files
rather having them at Google Datacenters :)So I was running version 2.6 when I had "my" issues. I noticed in systems log that when I was loading the NIC with "more" traffic, NIC often
"decided" to restart which of course caused issues. I use a builtin Realtek Gigabit card in my Pfsense server and have found out that more people
than I have had issues with Realtek.I have now upgraded the Pfsense to version 2.7, I have not started services like Snort, DNSBL for now.
I only run Ntopng 5.7.2 and the setup seem to work much better with my HW compared to when I was using 2.6 version of Pfsense.
No more odd NIC restarts when I load traffic on the network,I am really happy right now and I love Pfsense. :)