Routing not working without outbound NAT
-
Hello, I have a 2 interfaces pfsense box, WAN and LAN.
I'm trying to send internet traffic to the Internet. it does not work. I have added some firewall rules to allow all traffic.
If I enable the Outbound NAT 'Manual' it starts to work fine.
Any ideas or help?
-
to add to the above, if I Disable Outbound rule generation all traffic from LAN to internet fails.
-
@Baby_newbie you need to do network address translation to move traffic from private IP addresses to the public IP address or the wan side. You need to have NAT so LAN traffic can be translated to WAN traffic on the old interwebs.
-
@JonathanLee Thanks for the reply.
Is this even if you are using rfc1918/private addressing on both sides of the interface?
The WAN interface I have gets an ip from the dhcp/broadband server = 192.168.0.201.
LAN is 192.168.2.1/24 -
@Baby_newbie said in Routing not working without outbound NAT:
I'm trying to send internet traffic to the Internet. it does not work.
If I enable the Outbound NAT 'Manual' it starts to work fine.Highly unlikely.
My advice, don't use a firewall at your knowledge state.
-
@Baby_newbie said in Routing not working without outbound NAT:
Is this even if you are using rfc1918/private addressing on both sides of the interface?
The WAN interface I have gets an ip from the dhcp/broadband server = 192.168.0.201.
LAN is 192.168.2.1/24Yes.
You router will only know the WAN network of pfSense, but not the LAN. So he might nat only this subnet.With outbound NAT enabled on pfSense, traffic from the LAN behind it is translated into the WAN address. The outer router then translates it a second time into its internet IP.
If you want to nat the traffic only once, you would have to configure the router to do the translation for the LAN subnet and also add a static route for the LAN and point it to pfSense WAN IP.
-
@Baby_newbie pfSense will auto add NAT config if you have to set to auto or hybrid. I would just leave it be. If you are new to this no problem and got this for cyber security I would set up IPS/IDS with snort and leave the default config with the PfSense wizard. That will get you running the fastest.
-
@JonathanLee said in Routing not working without outbound NAT:
pfSense will auto add NAT config if you have to set to auto or hybrid.
Yeah, but only if you state a gateway in the (WAN) interface settings. If you miss that no NAT rules are added.
-
@viragomann I think what he is trying to accomplish is to disable NAT in pfsense to avoid double nat, and let the ISP modem do the natting to the internet.
If that is what he wants, he needs to add a static route in the ISP modem saying that his internal network is behing pfsense WAN's IP (next hop to internal network).
-
@viragomann With outbound NAT disabled, this is also what I was expecting the source ip not to change and having to add a static route on the BB router. Until I see the packet capture and attached capture from physical interfaces
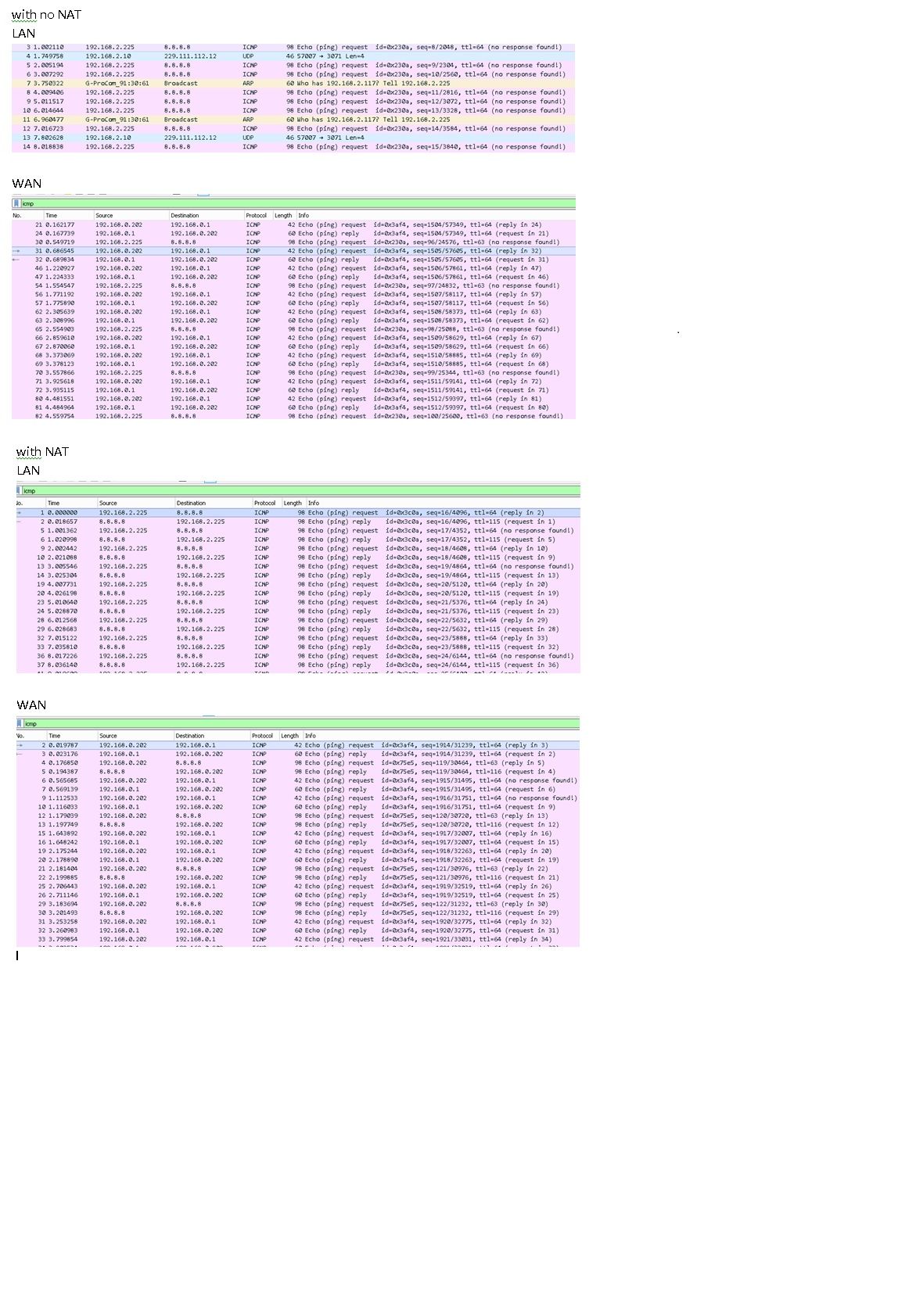
Src of icmp = 192.168.2.225
pfsense
WAN today is 192.168.0.202
LAN = 192.168.2.1No NAT
LAN
14:41:55.318906 IP 192.168.2.10.1093 > 192.168.2.1.80: tcp 0
14:41:56.050895 ARP, Request who-has 192.168.2.117 tell 192.168.2.225, length 46
14:41:56.269203 IP 192.168.2.225 > 8.8.8.8: ICMP echo request, id 57865, seq 15, length 64
14:41:57.271272 IP 192.168.2.225 > 8.8.8.8: ICMP echo request, id 57865, seq 16, length 64
14:41:58.273991 IP 192.168.2.225 > 8.8.8.8: ICMP echo request, id 57865, seq 17, length 64WAN
14:42:30.777093 IP 192.168.0.202 > 192.168.0.1: ICMP echo request, id 15092, seq 226, length 8
14:42:30.780480 IP 192.168.0.1 > 192.168.0.202: ICMP echo reply, id 15092, seq 226, length 8
14:42:31.133872 a0:bd:cd:aa:9a:48 > ff:ff:ff:ff:ff:ff, Unknown Ethertype (0x7374), length 66:
14:42:31.236228 IP 192.168.0.161.60759 > 192.168.0.255.15600: UDP, length 35
14:42:31.301052 IP 192.168.0.202 > 192.168.0.1: ICMP echo request, id 15092, seq 227, length 8
14:42:31.304596 IP 192.168.0.1 > 192.168.0.202: ICMP echo reply, id 15092, seq 227, length 8
14:42:31.338042 IP 192.168.2.225 > 8.8.8.8: ICMP echo request, id 57865, seq 50, length 64
14:42:31.831135 IP 192.168.0.202 > 192.168.0.1: ICMP echo request, id 15092, seq 228, length 8
14:42:31.835404 IP 192.168.0.1 > 192.168.0.202: ICMP echo reply, id 15092, seq 228, length 8
14:42:32.055272 a0:bd:cd:aa:9a:49 > ff:ff:ff:ff:ff:ff, Unknown Ethertype (0x7380), length 60:
14:42:32.341517 IP 192.168.2.225 > 8.8.8.8: ICMP echo request, id 57865, seq 51, length 64
14:42:32.387908 IP 192.168.0.202 > 192.168.0.1: ICMP echo request, id 15092, seq 229, length 8
14:42:32.388147 IP 192.168.0.1 > 192.168.0.202: ICMP echo reply, id 15092, seq 229, length 8
14:42:32.909470 IP 192.168.0.202 > 192.168.0.1: ICMP echo request, id 15092, seq 230, length 8With NAT
LAN
14:45:20.180546 IP 192.168.2.225 > 8.8.8.8: ICMP echo request, id 64777, seq 19, length 64
14:45:20.200514 IP 8.8.8.8 > 192.168.2.225: ICMP echo reply, id 64777, seq 19, length 64
14:45:21.183339 IP 192.168.2.225 > 8.8.8.8: ICMP echo request, id 64777, seq 20, length 64
14:45:21.202300 IP 8.8.8.8 > 192.168.2.225: ICMP echo reply, id 64777, seq 20, length 64WAN
14:47:12.454980 IP 192.168.0.202 > 8.8.8.8: ICMP echo request, id 8708, seq 131, length 64
14:47:12.471696 IP 8.8.8.8 > 192.168.0.202: ICMP echo reply, id 8708, seq 131, length 64
14:47:12.513886 IP 192.168.0.202 > 192.168.0.1: ICMP echo request, id 15092, seq 753, length 8
14:47:12.517257 IP 192.168.0.1 > 192.168.0.202: ICMP echo reply, id 15092, seq 753, length 8
14:47:13.064666 IP 192.168.0.202 > 192.168.0.1: ICMP echo request, id 15092, seq 754, length 8
14:47:13.068606 IP 192.168.0.1 > 192.168.0.202: ICMP echo reply, id 15092, seq 754, length 8
14:47:13.354923 IP 192.168.0.161.38660 > 192.168.0.255.15600: UDP, length 35
14:47:13.457792 IP 192.168.0.202 > 8.8.8.8: ICMP echo request, id 8708, seq 132, length 64
14:47:13.476287 IP 8.8.8.8 > 192.168.0.202: ICMP echo reply, id 8708, seq 132, length 64
14:47:13.611799 IP 192.168.0.202 > 192.168.0.1: ICMP echo request, id 15092, seq 755, length 8
14:47:13.615125 IP 192.168.0.1 > 192.168.0.202: ICMP echo reply, id 15092, seq 755, length 8@Baby_newbie said in Routing not working without outbound NAT:
-
@Baby_newbie You are not getting an answer with NAT disabled, most probably the packet is being dropped in your device ahead of pfsense, because it doesn't have a route to your internal network (behind pfsense).
A router only has routes to directly connected networks, and a default route to Internet.
So, you ping from LAN, your pfsense sends the packet without NAT, your ISP modem sends it to the Internet and doesn't know how to forward it back to your internal LAN, and drop it.
Add a route as mentioned earlier and it will work.
But note that ISP modems usually don't give you that configuration option.Edit:
Another option, which I prefer, is to configure your ISP modem as bridge. -
@mcury Thank you for your response.
I think I see what was happening. I was being confused by two sets of icmp flows. One generated by me and a second that is generated by the pfsense box itself.
Any ideas why the pfsense continuously sends icmp on the WAN to its gateway?
-
@Baby_newbie it sends them to make sure the gateway is still working.
-
@JonathanLee Thank you.