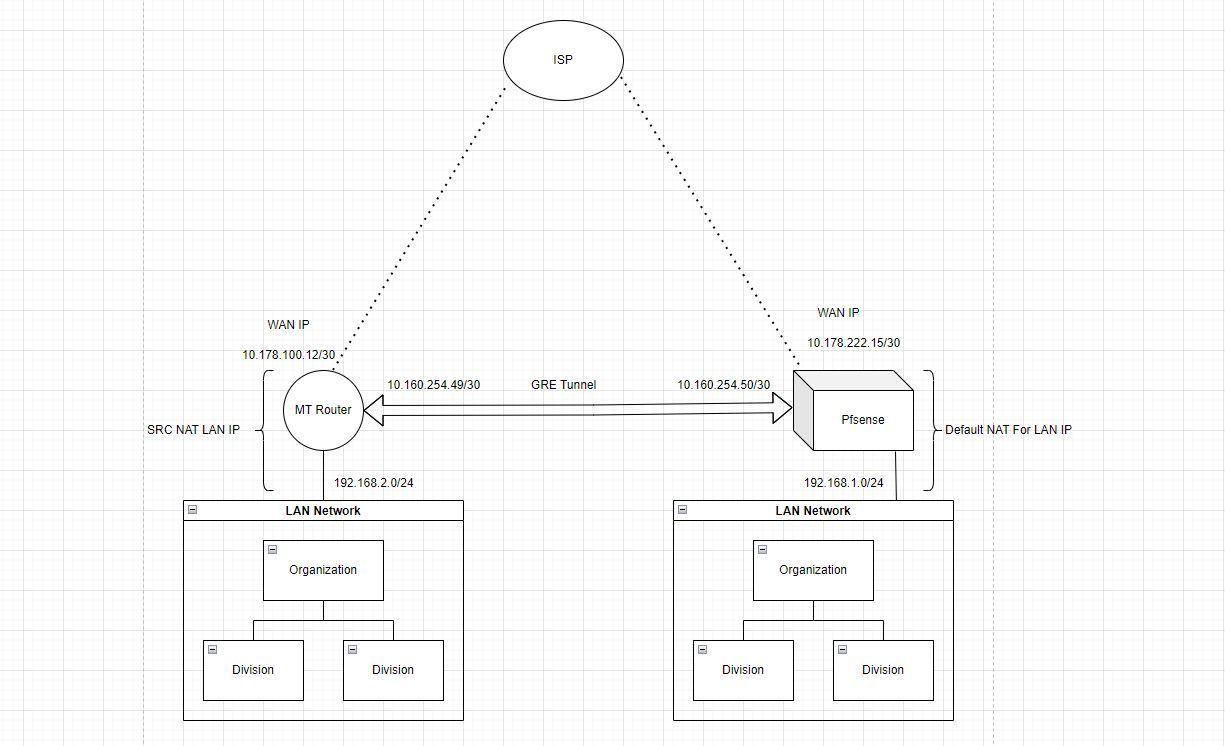
Pfsense Gre Tunnel with Mikrotik Router (Incomming Traffic Block by default deny rule pfsense)
-
@Rohit-0 On mikrotik side i hve done all the routing and it work like a charm when tunnel with Netskope FW so i think i need some changes in pfsense.
-
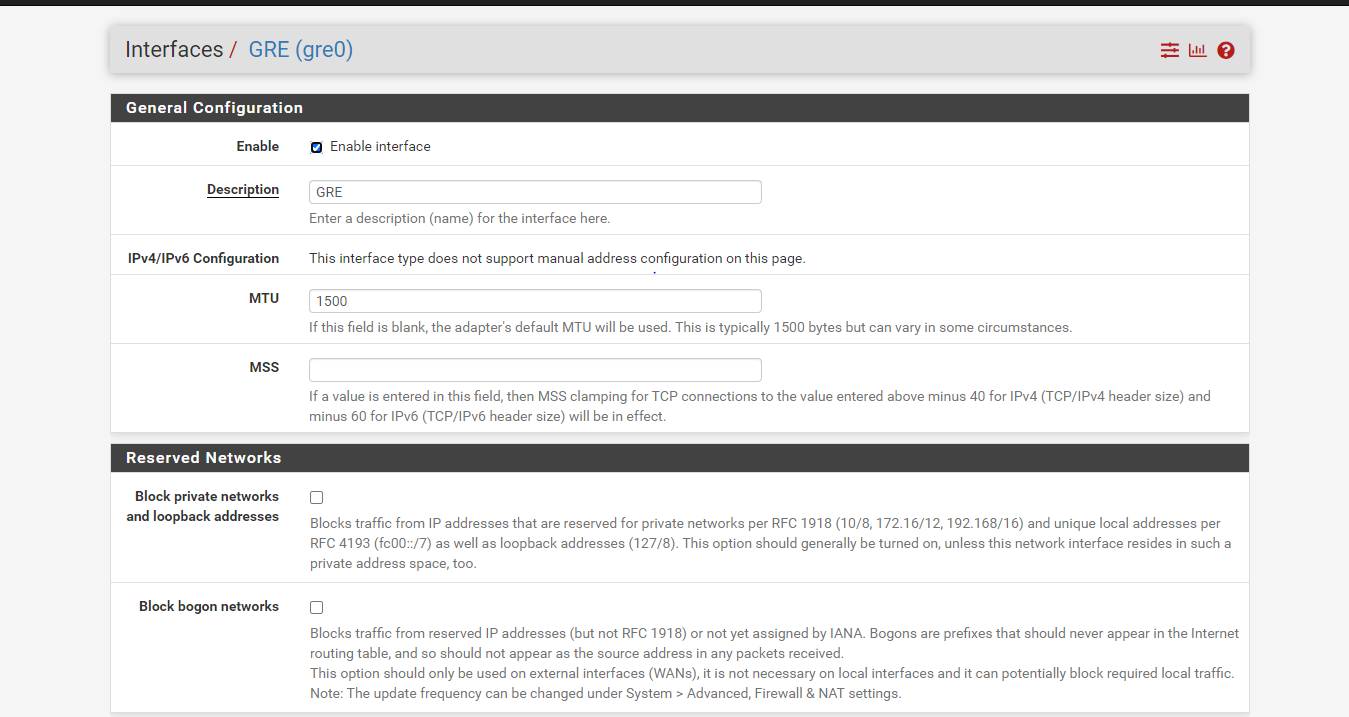
@Rohit-0 Hmm, hard to tell what causes your issue then because I agree that your firewall log should not be hit with blocks like that since you created the right allow rule on the GRE interface - unless you created the GRE interface with the wrong settings.
Please post your current:
- GRE interface definition
- Current WAN Interface addresses in both ends.
- Current pfSense outbound NAT rules
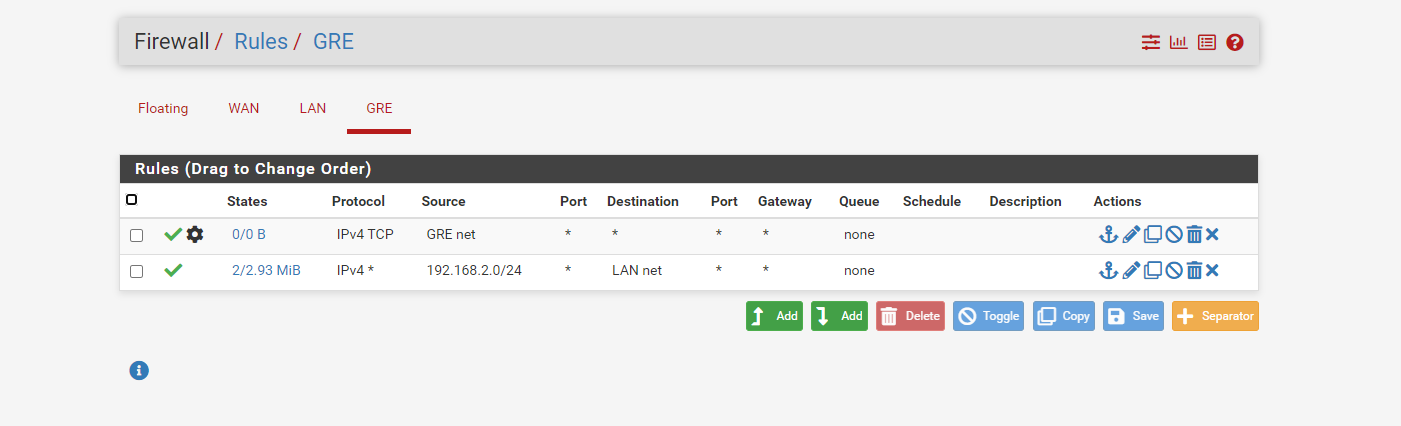
- Current pfSense GRE interface Rules
A few other observations.
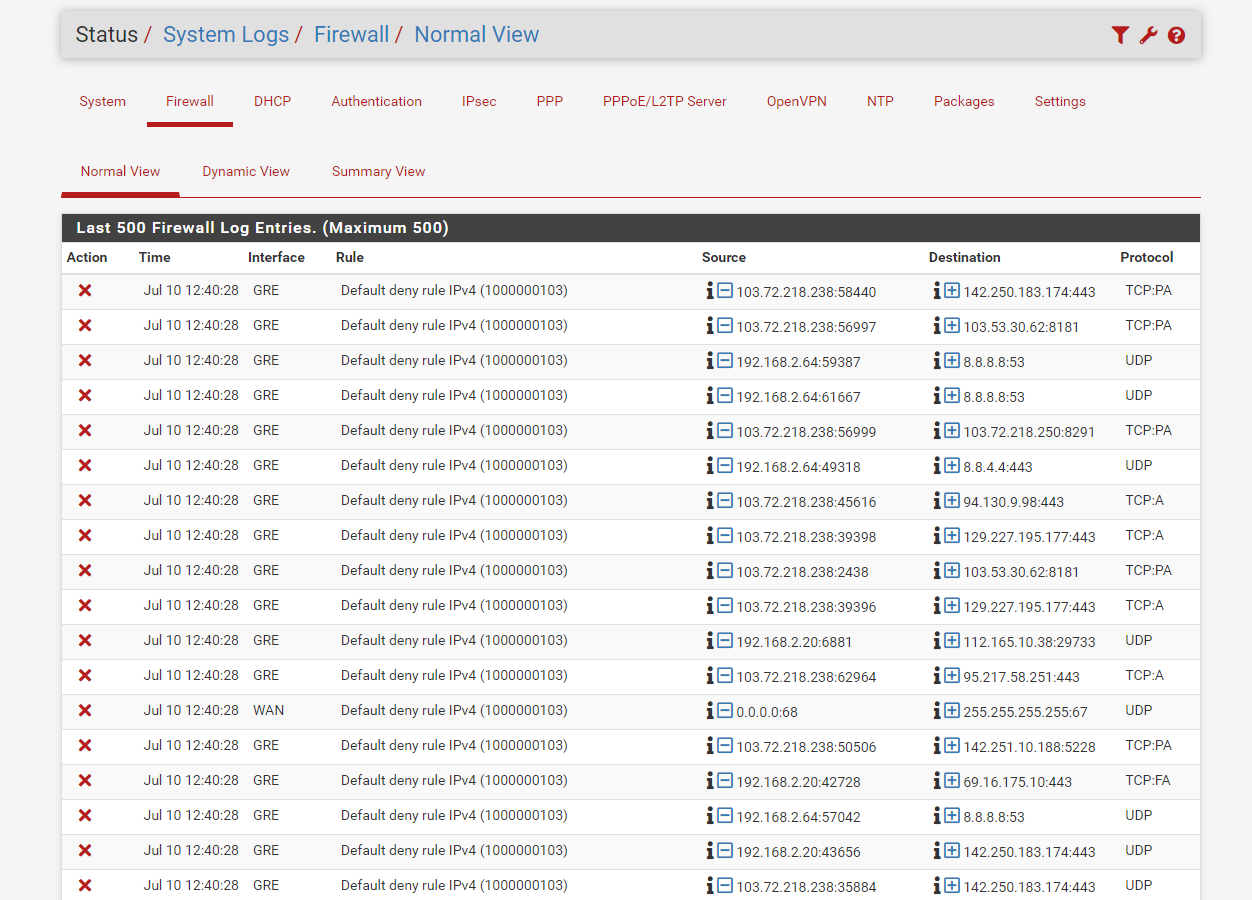
1: There is somthing wrong with your Microtik config as traffic sourced from 103.72.218.238 also gets forwarded over your GRE tunnel
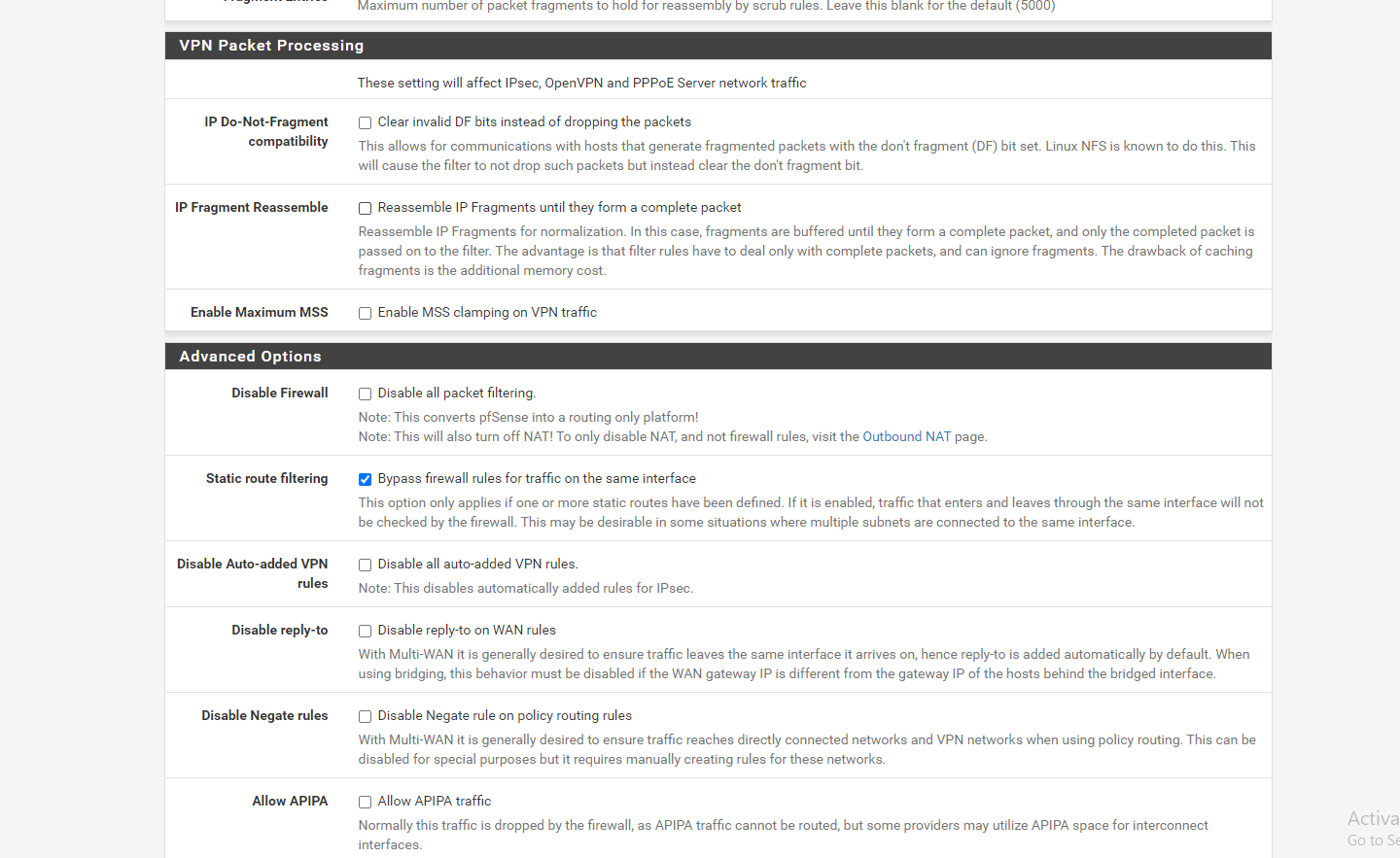
2: There is no need to tick “Static Route filtering” in advanced settings. This GRE Tunnel does not need that. -
@Rohit-0 Anyways - since the firewal log blocks TCP:FA from 192.168.2.20 towards the internet, there seems to be something causing assymetric routing as that packet is not matched to an existing state. That can be many things, but it is quite often related to faulty NAT config in either end of the setup.
-
@keyser i will look into why public address is being forwarded ,
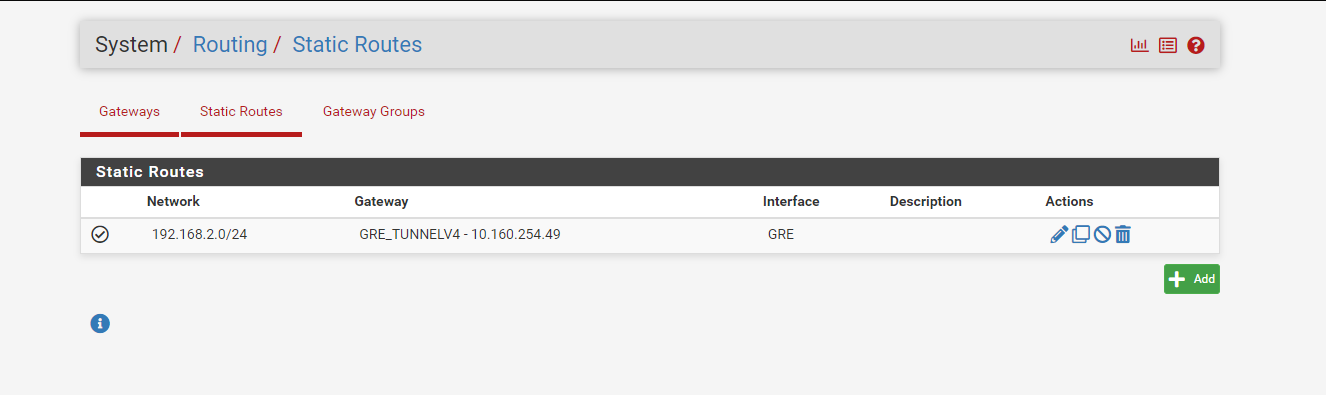
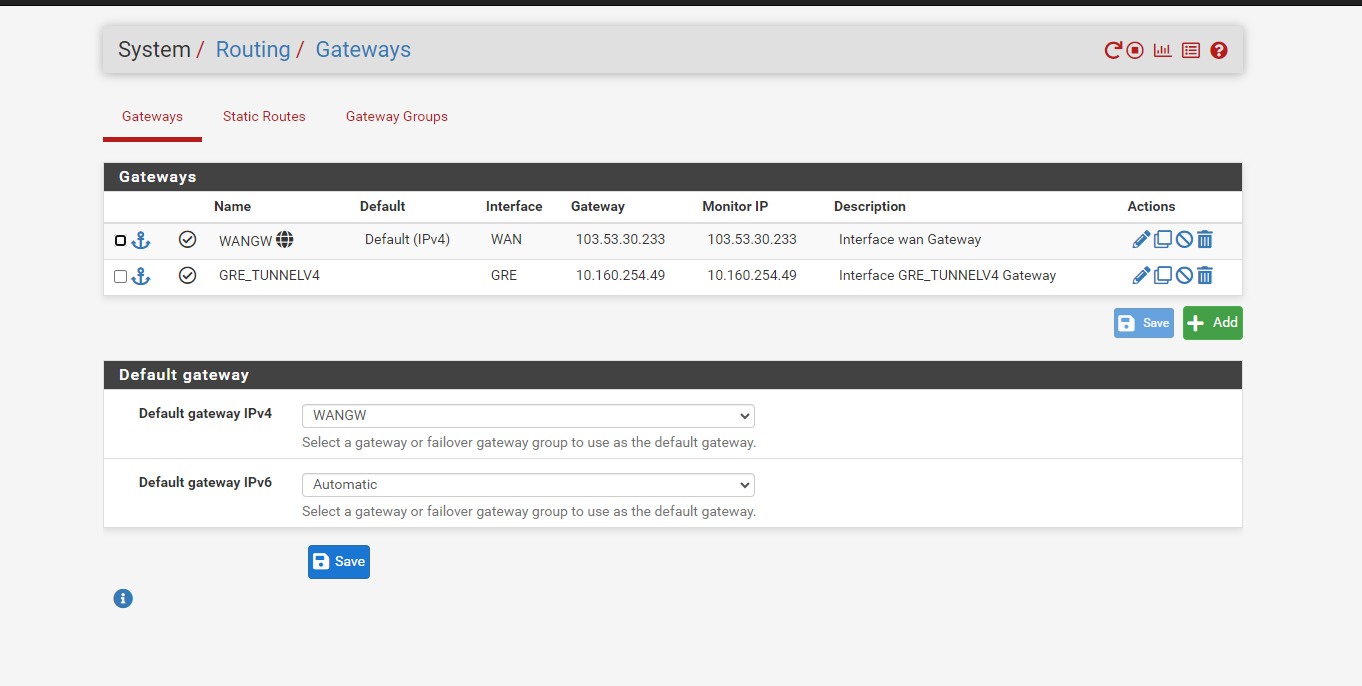
here are my pfsense setting snapshot
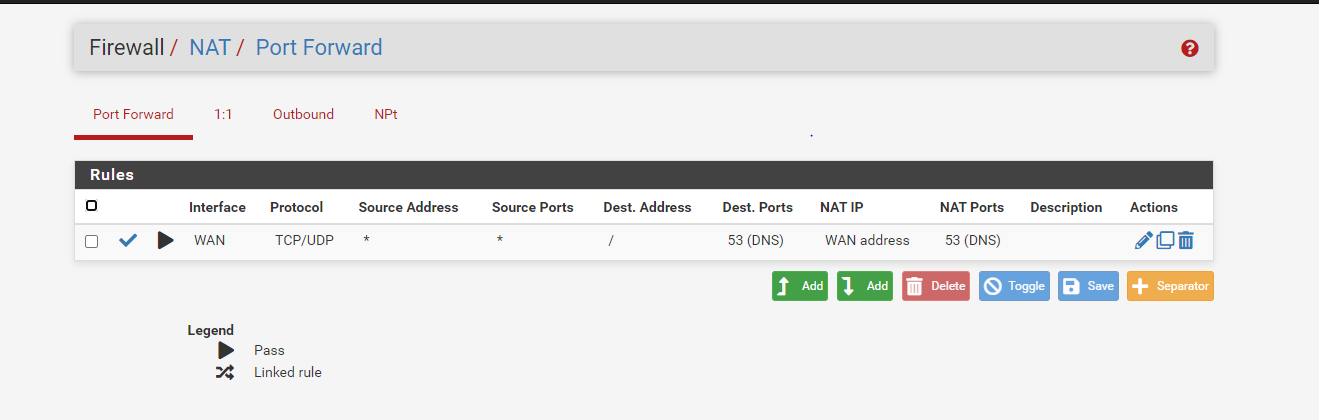
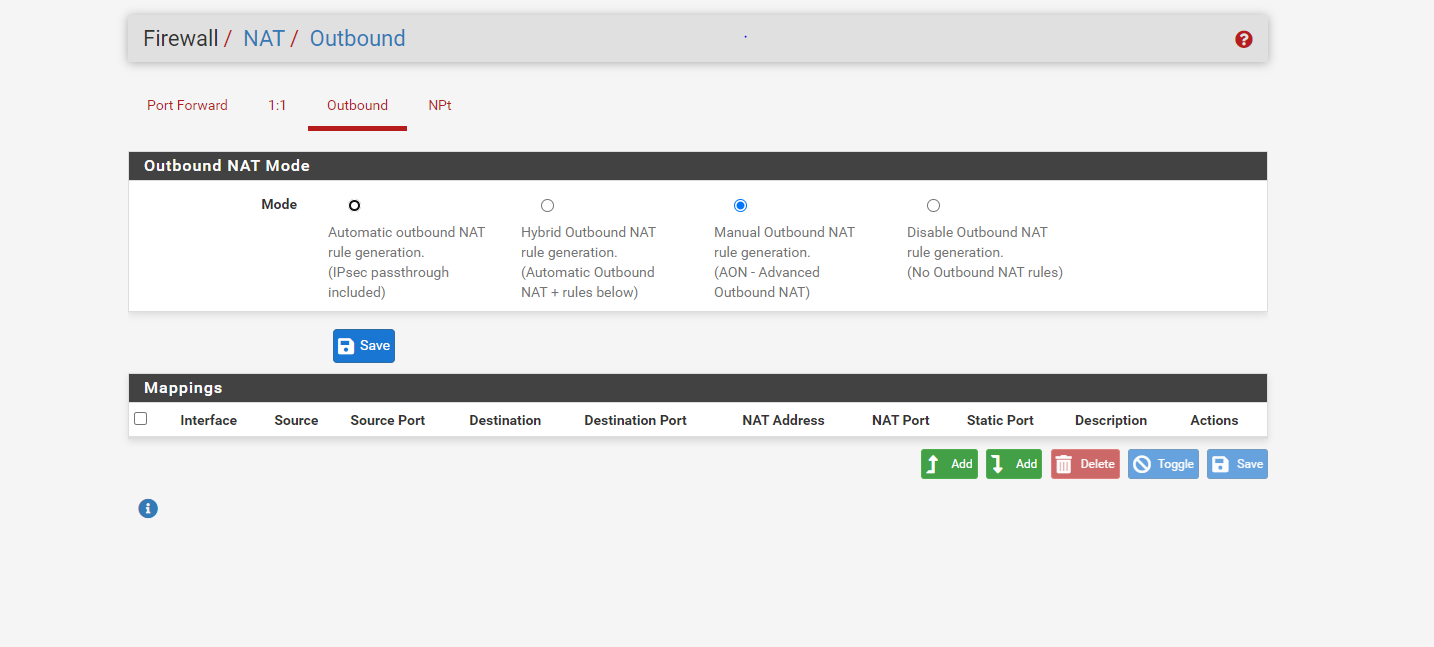
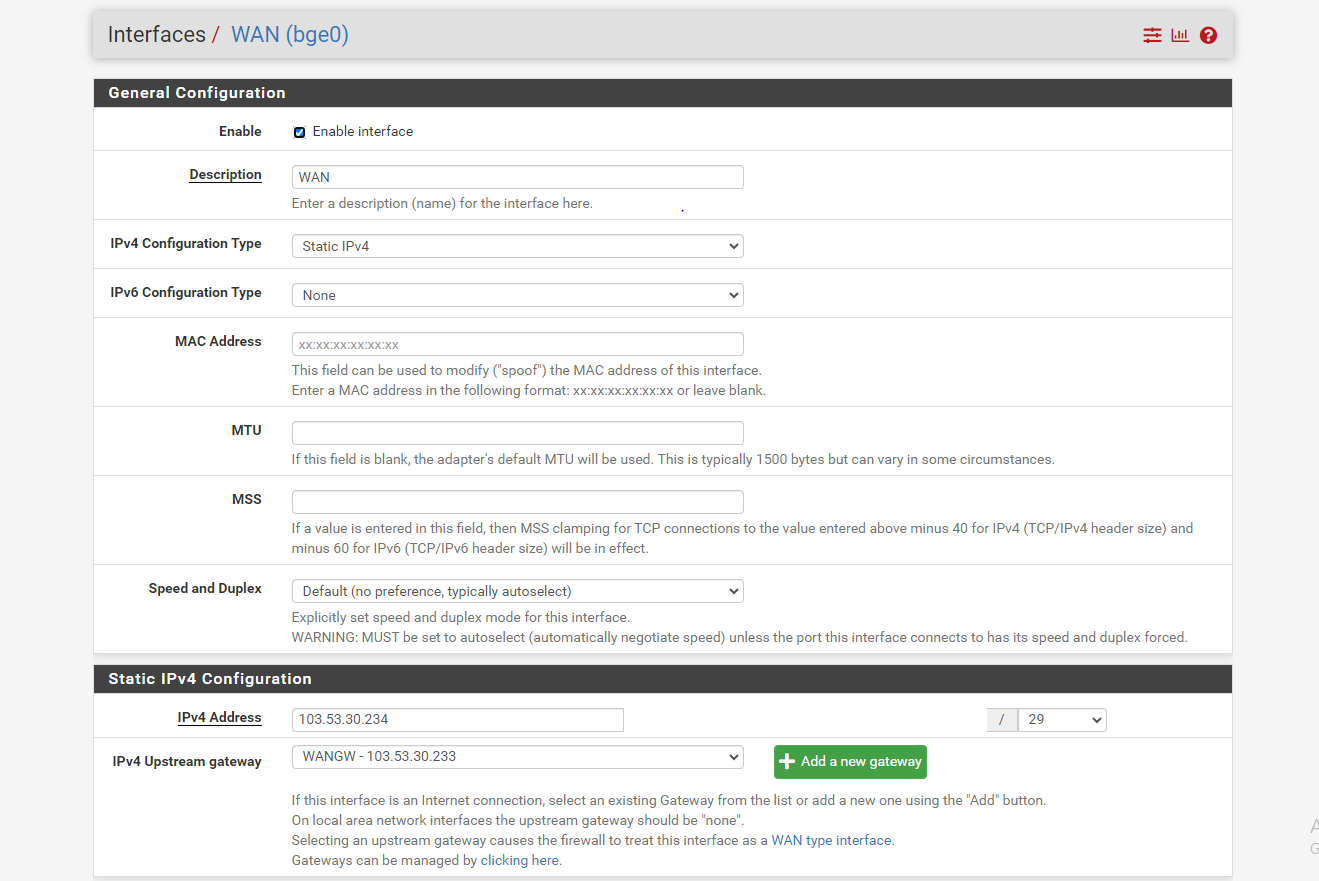
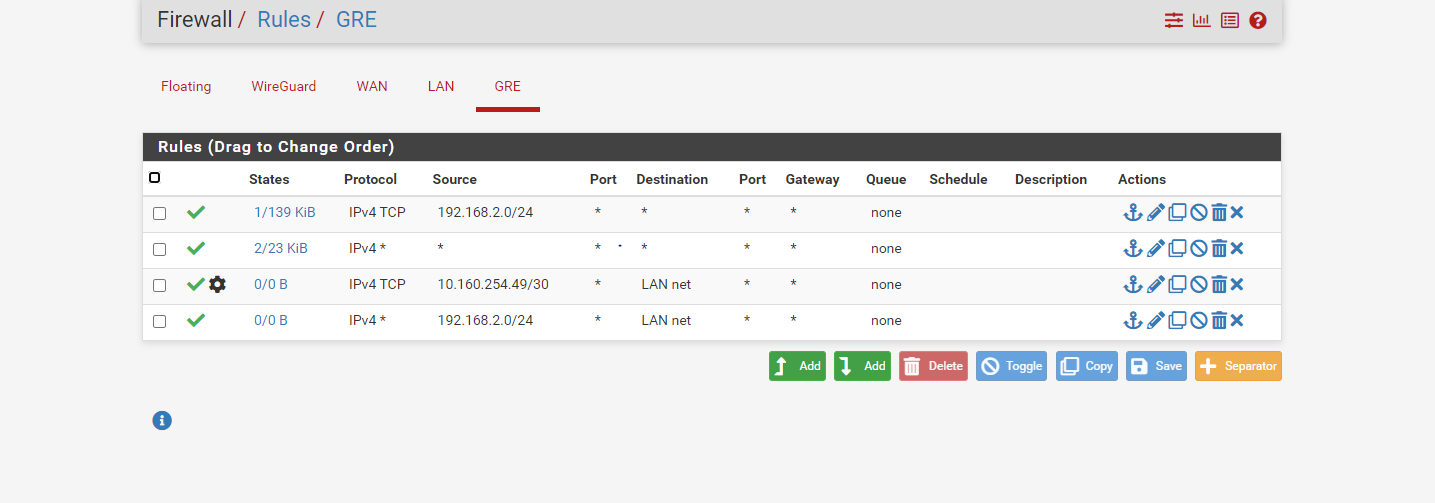
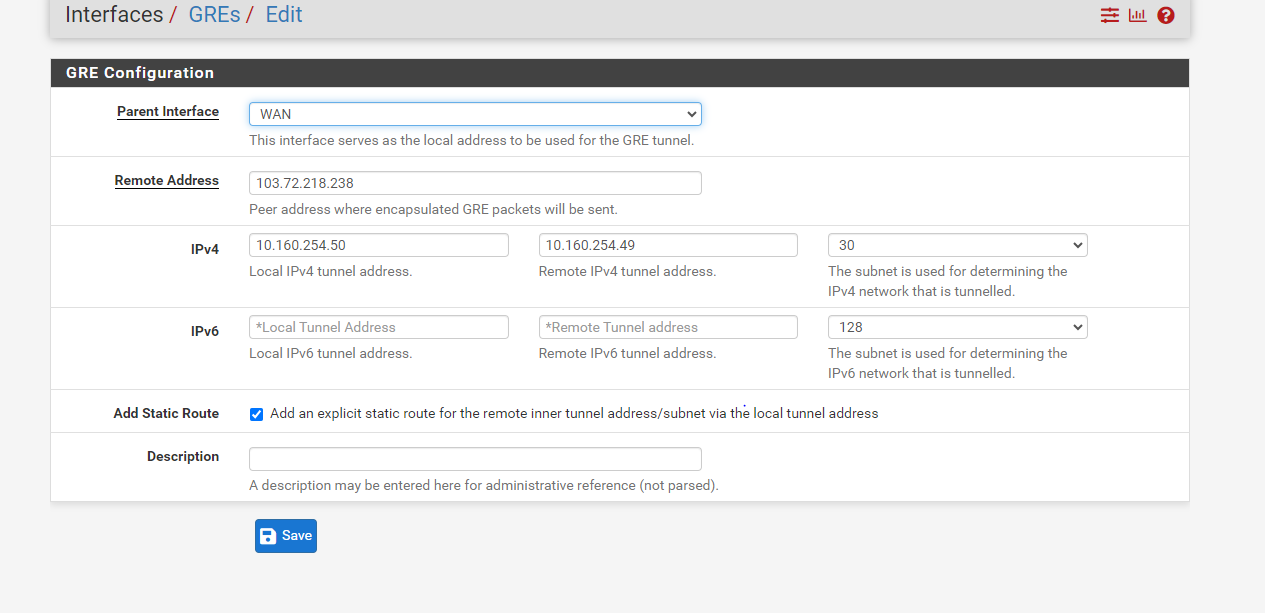
-
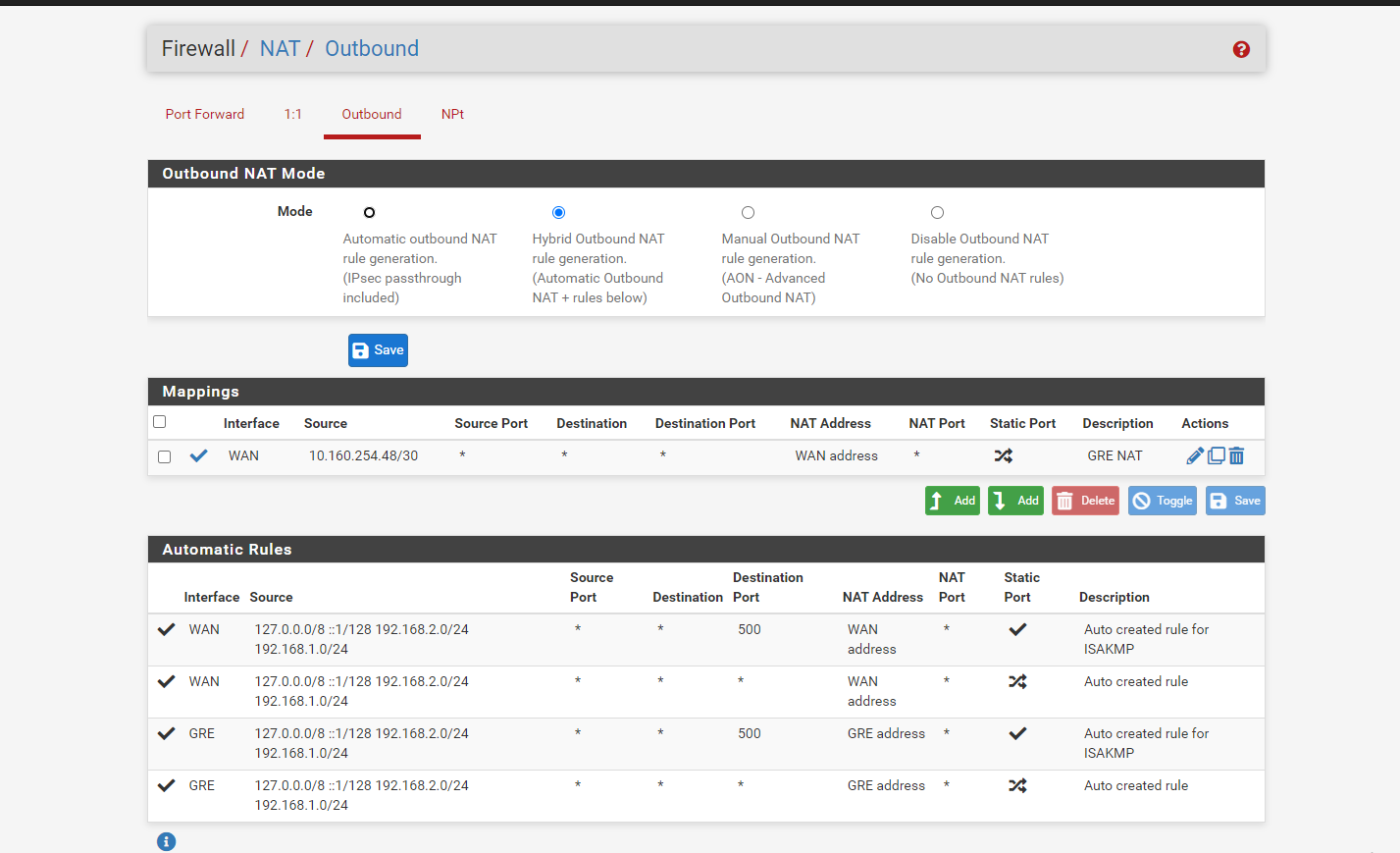
@Rohit-0 Right now you are missing outbound NAT rules intirely. You need to have pfSense NAT both you local pfSense Networks and the Remote Mikrotik client network. I think clicking “Automatic outbound NAT rule generation” should do it as your routing setup should make pfSense include the remote mikrotik network in the NAT for WAN outbound traffic.
But if it does create automatic rules for NAT’ing on the GRE interface as well, you instead need to create a manual NAT rule on Interface WAN stating that all 192.168.1.0/24 and 192.168.2.0/24 (according to your drawing) should be NAT’ed using the IWAN interfaces address.
Please post the revised NAT setup
-
@keyser here is my revised NAT rule and let me check
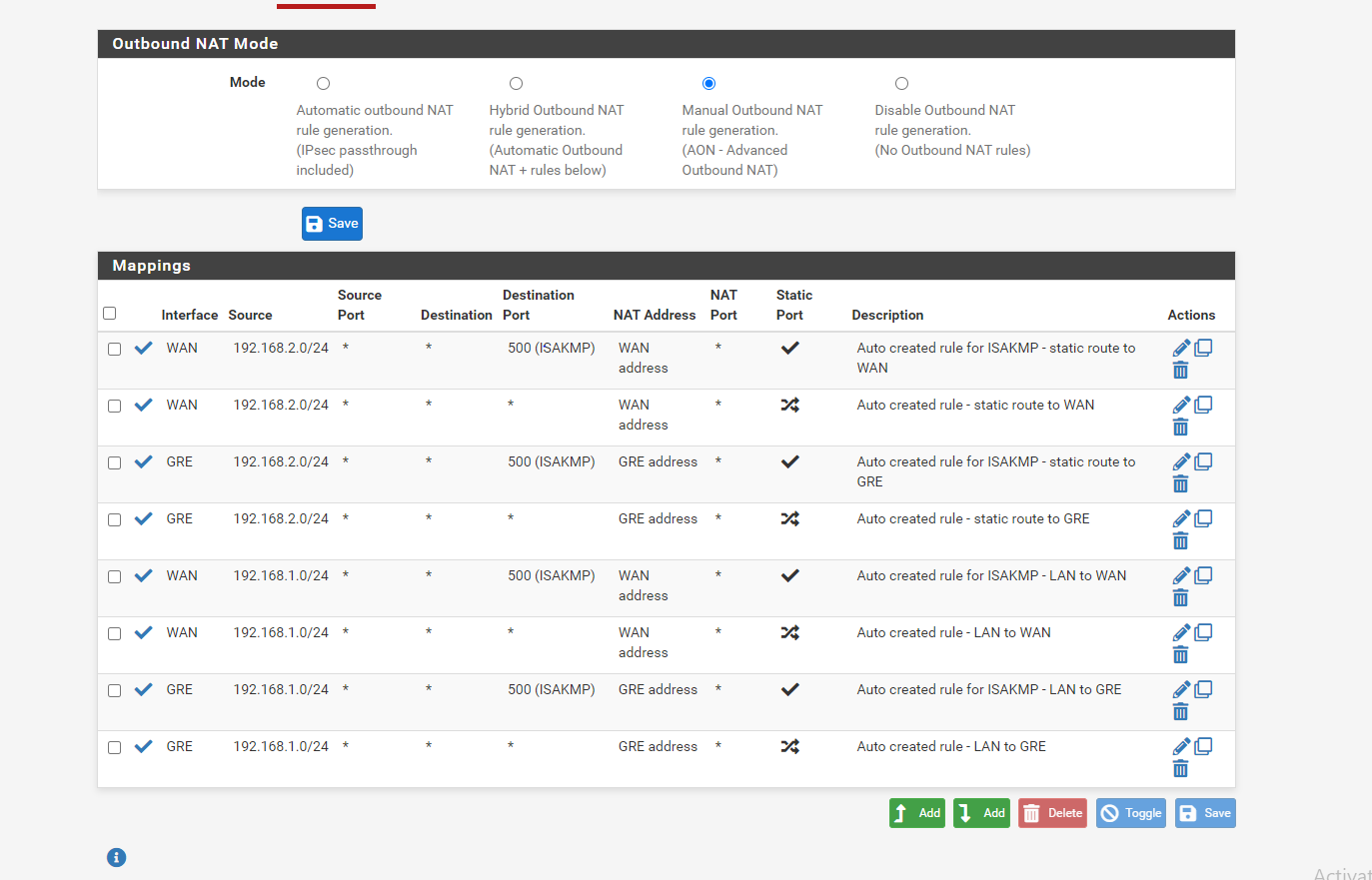
-
@Rohit-0 Still i'm getting blocked for GRE traffic
-
@Rohit-0 Thanks it was my mistake from mikrotik side i should not allow fast path in GRE setting , Thanks again for everything
-
@Rohit-0 My pleasure - but the Outbound NAT rules are still wrong - it will work, but not like you intend (fully routed).
You need to remove the four rules assigned with the GRE interface. They are not needed and will cause all traffic from the mikrotik network to appear as being sent from 10.160.254.50 -
@keyser thanks again