IPSEC no ping or access to lan through openvpn
-
Hi,
Using pfsense 2.6.0 created IPSEC between two locations.
Site A LAN : 192.168.99.0
Site B LAN : 192.168.1.0IPSEC between A&B establishing without any problem.
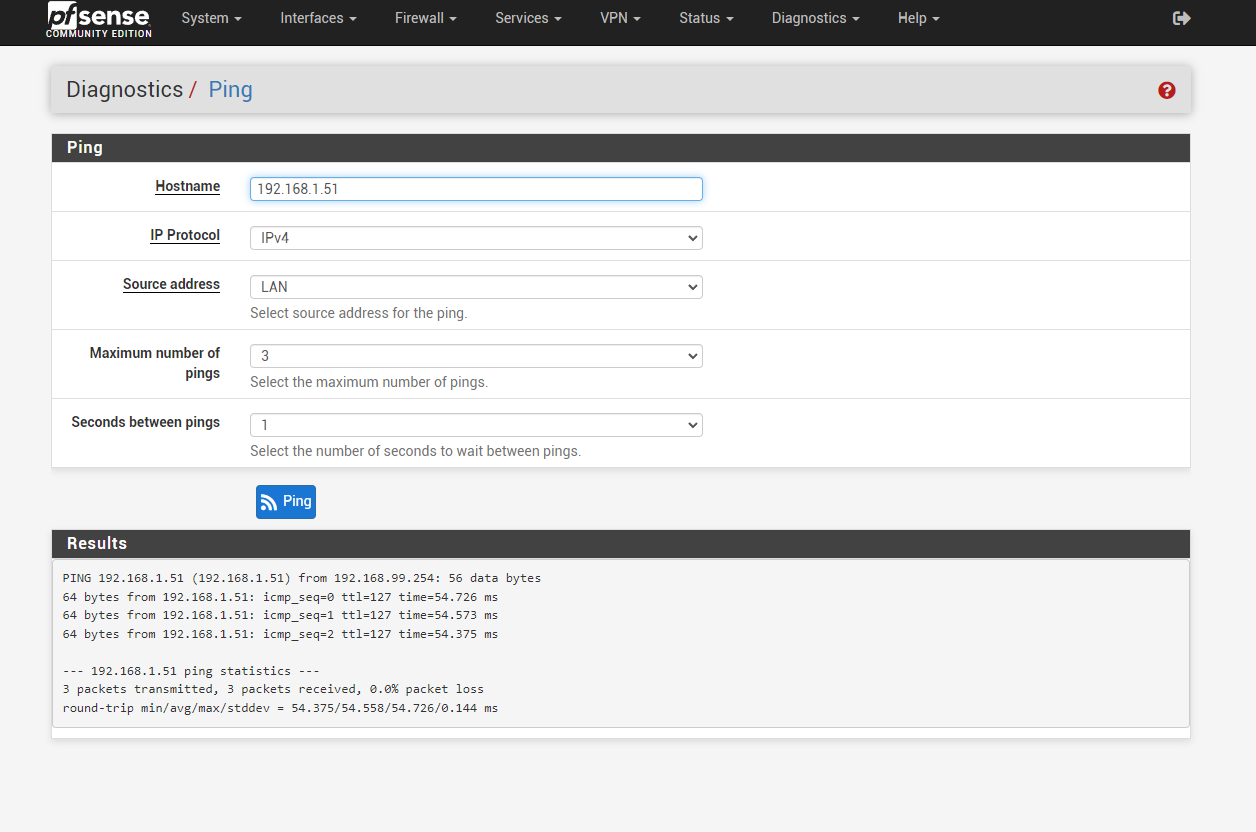
When i ping from site A to Site B through Diagnostic->Ping->Source address Auto->192.168.1.51 no ping.
When i ping from site A to Site B through Diagnostic->Ping->Source address LAN->192.168.1.51 ping passes to 192.168.1.51.
Also openvpn is active on Site A, when users connect to site A through vpn they must be access to site B's LAN through site A's IPSEC but also it's not passing any ping either.
IPSEC firewall rules are any any on both sides.
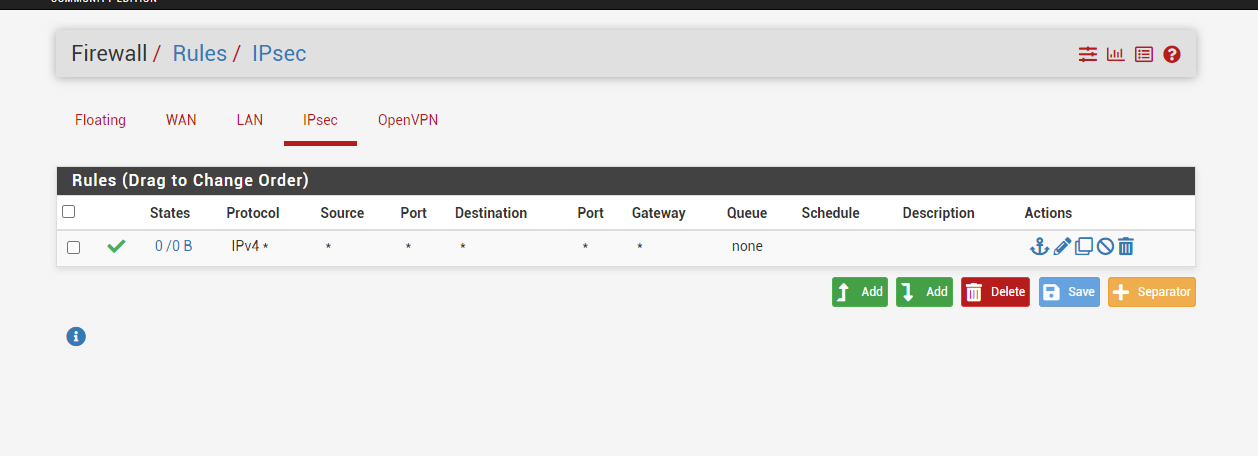
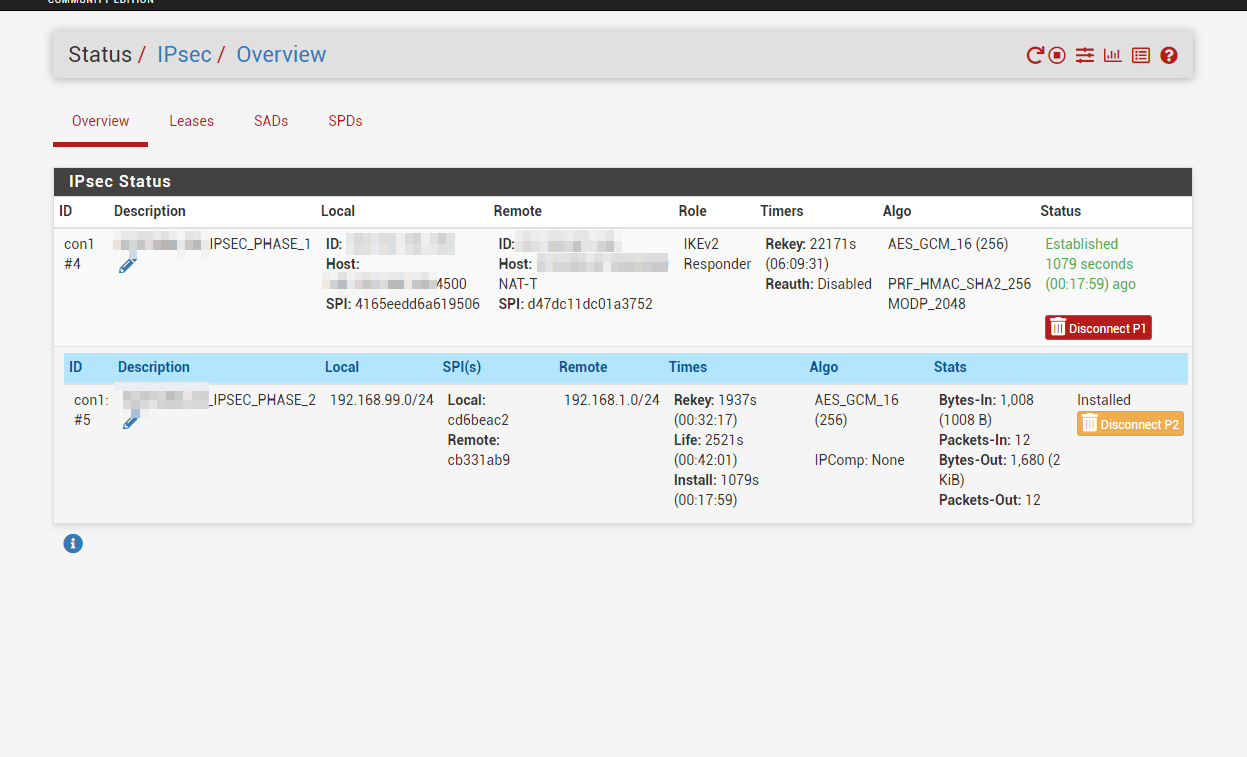
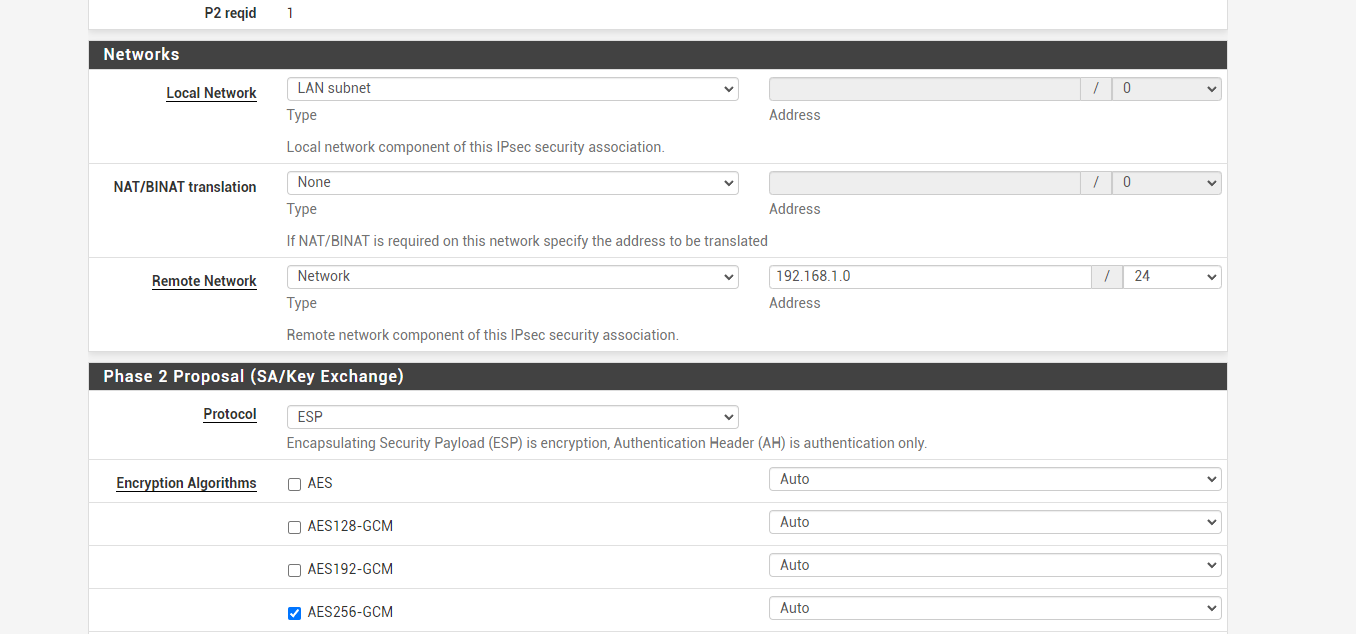
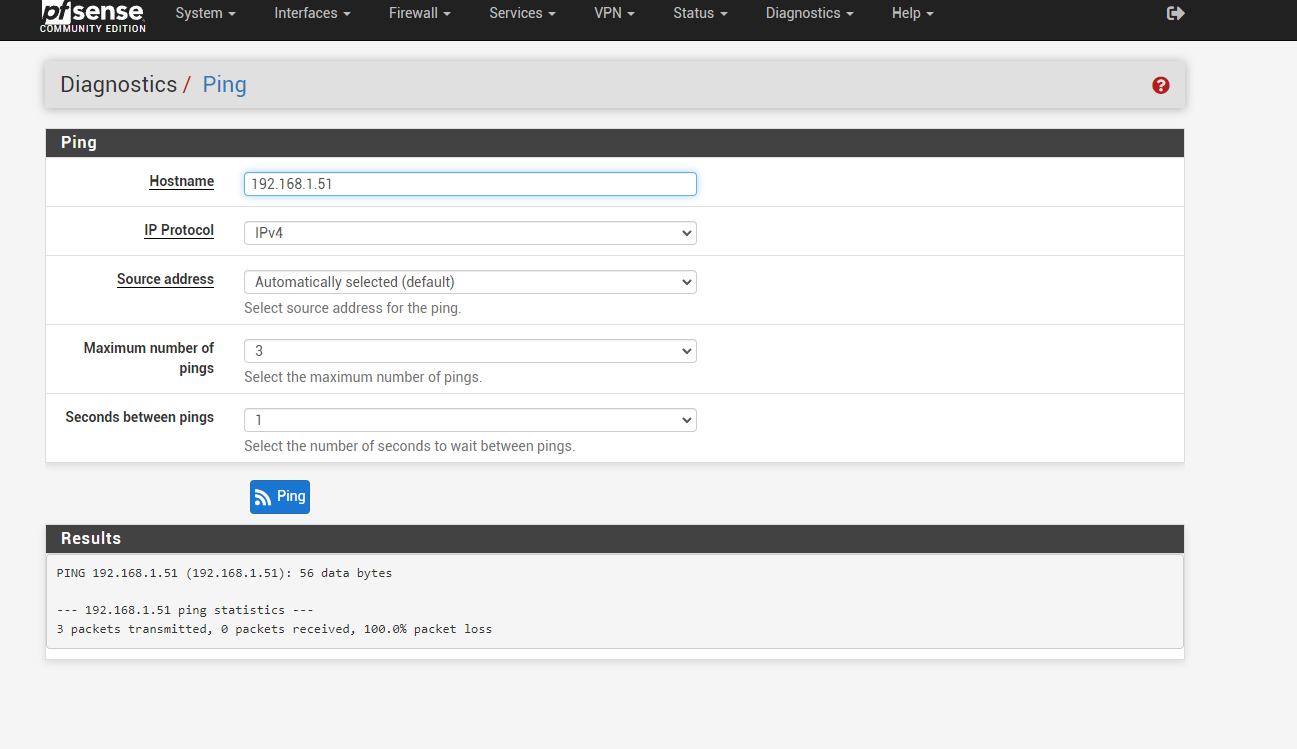
i'm most probably missing something very obvious but couldn't find it.Any ideas what am i doing wrong?
-
@yeahmagnets
So add a phase 2 in IPSec for the OpenVPN tunnel network.And in case you've not "redirect gateway" enabled, add the remote LAN to the "Local Networks" in the OpenVPN server settings.
-
@viragomann Thanks man, adding vpn ip block to phase2 solved the ping and access problem.
The only problem left is if vpn user's subnet is the same with remote site's subnet then user can not ping or reach to server,i mean let's assume user's home subnet is 192.168.1.0/24 and the remote site's subnet is 192.168.1.0/24 then user can not ping or rdp to servers.
I think i need to search subnet overlap words to find articles and guides right?
-
@yeahmagnets said in IPSEC no ping or access to lan through openvpn:
The only problem left is if vpn user's subnet is the same with remote site's subnet then user can not ping or reach to server,
Do you mean, the clients local network or the tunnel network?
The clients local network is irrelevant and isn't seen by the OpenVPN server (pfSense) at all. The client gets a virtual IP out of the tunnel network, when he connect, so you only have to set the VPN tunnel network to something unusual in the OpenVPN settings. E.g. 10.227.134.0/24. With that, as long as the user has not set a 10/8 LAN, an address conflict would be very unlikely. -
@viragomann let me put it this way, one of my clients working from home and his modem providing 192.168.1.0/24 network, my company lan is also 192.168.1.0.24 and my server is 192.168.1.128, usually he can ping or access to server through vpn without any problem, but somehow by any chance if any device at his home gets 192.168.1.128 from his home modem then he is not able to reach to server or ping., because his computer start searching 192.168.1.128 on his home network, somehow (sorry newbie on pfsense here) i need to say to pfsense do not search any 192.168.1.x ip on local network or when you get request for 192.168.1.128 don't search this specific ip on local network when vpn is up, just don't know how to :)
i'm looking for a solution for this problem.
-
@yeahmagnets
Yes, that's an issue naturally. In this case the client is not able to route the remote site.Even though you can nat the traffic to something else at A, but I'd suggest to rather change the local subnets. Networks which should be accessible via user VPNs should not use as common network ranges.
-
@viragomann said in IPSEC no ping or access to lan through openvpn:
but I'd suggest to rather change the local subnets. Networks which should be accessible via user VPNs should not use as common network ranges.
you are absolutely right but this installation hapened way before i start to work here and i can't change any time soon :( in the future i'll change and correct this madness (litteraly) but now i need to find a temporary solution for this.
@viragomann said in IPSEC no ping or access to lan through openvpn:
Even though you can nat the traffic to something else at A
any advice on this? what should i search to learn how to do it?
-
@yeahmagnets said in IPSEC no ping or access to lan through openvpn:
what should i search to learn how to do it?
It's on you to undergo that effort.
Note, nat means that the user has to use a different IP range to access the remote site. There is no other way around.
I'll use 10.222.231.0/24 in this example.If you're running multiple OpenVPN instances, either servers or clients, you should assign an interface the the respective server instance and just enable it. Interfaces > Assignments. Then use this for the further settings as "OpenVPN interface".
Then go to Firewall > NAT > NAT 1:1 and add a rule to the OpenVPN interface:
Interface: OpenVPN interface
External subnet IP: 10.222.231.0
Internal IP: network > 192.168.1.0/24
Destination: not configured (you can specify the OpenVPN tunnel network, but not needed, since there are not other networks on this interface)
Description: enter something for your referenceIn the OpenVPN server settings add 10.222.231.0/24 to the "Local Networks".
Now if the connected user intend to access 192.168.1.128 he has to use 10.222.231.128 instead.
-
@viragomann thank you, that did the trick