Best topology for my network
-
Okay, I'm new to pfs and feel completely in over my head right now.
I keep looking at things from a perspective colored by the personal routers I've always used in the past and I think it's getting in the way of the most practical layout I need for my network.So, I'm going to describe what I want to end up with and take advice rather than asking if a particular layout in my head makes any sense (hint, they usually don't).
-
I have a bunch of smart devices (IE IoT crap) that are all wireless. I want them delegated to their own 2.4G wireless network and isolated from other devices except where home hubs need to get in touch with them. They're all Apple HomeKit compatible.
-
I have multiple iPhones, iPads, and laptops that will be on their own 2 band 5G wireless network.
-
I have multiple desktop computers, Playstation, AppleTVs, and assorted servers that are all wired. I don't have Ethernet in my house so they all run over MoCA 2.5 adapters.
I want 2 and 3 to be able to talk amongst themselves, and talk to 1. I don't want 1 to be able to access the Internet, or anything on 2 or 3 unless they are answering a query.
I have a Nokia ONT with 2.5G AT&T fiber, a Mokerlink 8x 2.5G managed switch, and a mesh network made up of a Synology RT6600ax and an MR2200ac. I may not need both and am fine with ditching the MR2200ac. The 6600 has a single 2.5G port on it.
The new hardware I got to run pfs is a no name Amazon PC with 4x 2.5G NICs on it, specs here:
https://www.amazon.com/dp/B0B81Q3Q42?psc=1&ref=ppx_yo2ov_dt_b_product_detailsThe Synology devices are currently my routers, I want to continue to use them but in AP mode. They are VLAN aware and you can sort of see what I've got running now via these screenshots (ignore the hand drawn paper, that was just me thinking out loud so to speak):
https://www.icloud.com/sharedalbum/#B135M7GFPMGqUs
You can see their AP limitations here:
https://kb.synology.com/en-us/SRM/help/SRM/NetworkCenter/operation_modes?version=1_3So there it is, I hope I can accomplish what I want with what I have.
-
-
T tknospdr referenced this topic on
-
Is there a better subform to put this in?
I thought I might have some feedback by now.
-
@tknospdr said in Best topology for my network:
I thought I might have some feedback by now.
That's because only you can determine the best topology for your network. From what you wrote, it seems that you have a plan that is the right step; so, connect them all and play...you'll learn best getting your hands dirty. Please visit here: https://docs.netgate.com/pfsense/en/latest/index.html to help you craft your plan and if you have any problems come back and the forum will help you resolve them.
-
Alright, I made the leap and deployed the site.
Here's what I ended up doing. It appears to be going well. The only hiccup right now is that I can't access the interface of my AP unless I'm attached to its base wifi network, or wired into one of its ports. I'm not sure if it's just they way it goes or what. I put an ANY/ANY/ANY rule on it's interface but no change.
So what I want to do now is make sure that the wireless network with all the HomeKit devices on it can be accessed from my other subnets, but that it cannot leak back into them or get on the internet.
-
@tknospdr said in Best topology for my network:
I put an ANY/ANY/ANY rule on it's interface but no change.
So what I want to do now is make sure that the wireless network with all the HomeKit devices on it can be accessed from my other subnets, but that it cannot leak back into them or get on the internet.
You'll need firewall rule: pass tcp/udp LANnet Destination ailas - subnet with all Homekit devices or Interface
Then, you'll need rule: block any ailas or subnet with all homekit devices or interface destination: any -
@NollipfSense said in Best topology for my network:
You'll need firewall rule: pass tcp/udp LANnet Destination ailas - subnet with all Homekit devices or Interface
I already have an open 'pass' rule on the LAN, so that should cover that part right?
I mean, I may need an explicit rule in the future if I delete the default rule but for now I'm good here yes?Then, you'll need rule: block any ailas or subnet with all homekit devices or interface destination: any
Cool, that will still allow responding to traffic from other subnets TOO HomeKit devices right?
Also, just poking around but would this work just as good?
If I'm wrong, I'm wrong. I'm just trying to learn...
Rules - ETH3 is my HomeKit adapter from the pfS box. -
@tknospdr In your block rule, the destination should be any...
-
@NollipfSense said in Best topology for my network:
@tknospdr In your block rule, the destination should be any...
My rule says if traffic hits the adapter for ETH3 coming from ETH3 network and it's destined for anything besides ETH3 network, block it.
Doesn't it?If I make that same rule but block ANY destination the devices won't be able to talk among themselves, right?
Or am I reading too much into how rules work.
I really need an easy to understand primer on how the pf FW rules work. I always feel like I've almost got it, but then my rules never seem to work like I expect them to.
-
@tknospdr rules apply on an interface as packets arrive on that interface. They apply in order top down.
https://docs.netgate.com/pfsense/en/latest/firewall/fundamentals.htmlPackets from a LAN device to another LAN device will not go through the firewall.
Packets to a device on another network need to be allowed by that server’s firewall if it has one. Some allow only their own subnet by default.
-
@tknospdr Yes the firewall will not filter traffic destined to the same subnet as it originated from. This is because the traffic will be directed by the switch and never actually go to the firewall.
-
@tknospdr rules apply on an interface as packets arrive on that interface. They apply in order top down.
https://docs.netgate.com/pfsense/en/latest/firewall/fundamentals.htmlThanks for that, reading through it all now, but I think what I need is multiple practical examples. I'll just keep making rules and asking the hive mind if they're right before I turn them on
Packets from a LAN device to another LAN device will not go through the firewall.
Packets to a device on another network need to be allowed by that server’s firewall if it has one. Some allow only their own subnet by default.
@tknospdr Yes the firewall will not filter traffic destined to the same subnet as it originated from. This is because the traffic will be directed by the switch and never actually go to the firewall.
Okay, so that's good info to know.
Now my question is...
Is there a functional difference between a rule denying all traffic on 'ANY' vs denying all traffic !ETH3 net "not matching" originating LAN?
-
@tknospdr The first option will match traffic originated from this lan interface and destined to pfsense or other networks, the second option does not.
-
@Austin-0
So what DOES the 2nd option do? -
@tknospdr It would not match traffic coming from the interface and destined to the firewall or other networks.
-
Okay, here's where I get confused then, because to me saying:
If source is ETH3, but destination is NOT ETH3, drop the packets
Like the bottom rule hereSeems like the most efficient way to express a rule where you want all outbound (from the subnet) packets dropped unless they match an incoming state.
What's the flaw in my thinking?
And seriously, I'm not being argumentative, this is just the best way for me to learn. -
@tknospdr It is a subtle difference but it's possible to have a network behind ETH3 that is routed through ETH3 but is a different subnet. It's not a common setup though so if you're not routing internal traffic then there's not really a difference.
Your example is only blocking "ETH3 Net" but the default block rule would block it.
Your example is also invalid btw...which interface is this ruleset on? If it is on ETH3, the destination can never be ETH3. If it is not on ETH3, then the source for the last rule can never be ETH3 Net.
-
@tknospdr said in Best topology for my network:
What's the flaw in my thinking?
And seriously, I'm not being argumentative, this is just the best way for me to learn.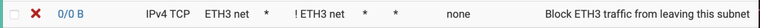
If you say that, then you're. As SteveTS said, you cannot have source and the destination the same...that's not how network works.
Would you go to the airport, say JFK (source or origination) to catch a flight going to JFK destination? You won't find any airline. Or, if you say I want to drop flights going to destination JFK, if the source or origination is JFK...you wouldn't find any flights to drop because no airline flies that route either.Makes sense?
-
@SteveITS said in Best topology for my network:
@tknospdr It is a subtle difference but it's possible to have a network behind ETH3 that is routed through ETH3 but is a different subnet. It's not a common setup though so if you're not routing internal traffic then there's not really a difference.
Are you talking about a VLAN, or something else. Because I do have 2 VLANs traversing ETH3. If those don't count I don't want to learn any other stuff I don't have to deal with right now.
My ears are already smoking with this learning module.Your example is only blocking "ETH3 Net" but the default block rule would block it.
The default block rules that I keep seeing mentioned are implied right? I don't actually see anything in any of the FW rule lists so it's just "zero rules = block everything" right?
Your example is also invalid btw...which interface is this ruleset on?
The ruleset is on ETH3
If it is on ETH3, the destination can never be ETH3.
I don't understand this. You can't make a rule on a subnet regarding traffic on itself?
If it is not on ETH3, then the source for the last rule can never be ETH3 Net.
Similar question... You can't make a rule saying for incoming packets on adapter ETH2, if the source is ETH3 do X?
-
@NollipfSense said in Best topology for my network:
Makes sense?
What you're saying makes sense, but I didn't think that's what I was saying.
I thought the rule I created said:
If I go to JFK, show me a list of flights that !JFK (are not destined for JFK), then ground them so they can't leave the airport. Effectively grounding ALL flights out of JFK.
It seems like I'm misunderstanding the usage of 'Invert match', so what would I use that for?
I thought it meant "everything that is not X", but clearly that's faulty thinking. -
@tknospdr said in Best topology for my network:
If I go to JFK, show me a list of flights that !JFK (are not destined for JFK), then ground them so they can't leave the airport. Effectively grounding ALL flights out of JFK.
But, the thing is there is no such list and will never be such list; so, there will be no flights to ground ever. These two threads should help you understand "invert match:" https://forum.netgate.com/topic/100836/firewall-invert-match-question - https://www.reddit.com/r/PFSENSE/comments/lyxkoj/invert_match/