Very Basic IPv6 security question.
-
@SteveITS, @JKnott, @johnpoz Thanks for the replies
@JKnott said in Very Basic IPv6 security question.:
Why are you so negative about IPv6? @guardian is on an ISP that does IPv6 properly. In fact, I got into pfSense because they started offering native IPv6 almost 8 years ago and the Linux firewall I was using wouldn't work with DHCPv6-PD. IPv6 on Rogers just works and works well.
This is correct:
"@johnpoz I think OP only wanted it on one VLAN for the video."The reason for my negativity regarding IPv6 - In a word - ignorance -- It scares the crap out of me because it is so hard to control. I am getting a ton of IPv6 entries that I don't understand (see below) or how to control.
I am running pfBlocker with a ton of ad blocking, and "spyware" blocking which works quite well on IPv4, but it appears that I am getting a bunch of DNS leakage now.
The only way to have any control over Microsoft Windows is to keep it tightly firewalled, and Google (and possibly others) have been responsible for serving Malvertising. So far my efforts to keep this nonsense under control have been successful, but now IPv6 is opening that can of worms back up again.
@JKnott is correct in saying that in bridge mode, "It just works." - simply changing the WAN IPv6 setting to DHCP6 got me a public IP Address.
The DPinger address was set to what I believe is a link local address: fe80:0:0:0:217:---:----:e58f, and it showed 100% packet loss, but when I changed the monitor address to 2607:f8b0:400b:807::2003 (Google.ca), the packet loss dropped to 0% and showed RTT/RTTsd values. So it appears that I have IPv6 connectivity, and the Status / Interfaces tab seems to confirm it. Is there a better monitor target, or a way to make pfSense pick a useful monitor IP automatically?
Status / Interfaces WAN Interface (wan, em0) Status: up DHCP: up MAC Address: 00:28:--:--:--:04 IPv4 Address: 99.--.--.-- Subnet mask IPv4: 255.255.254.0 Gateway IPv4: 99.--.--.1 IPv6 Link Local: fe80::228:----:----:1004%em0 IPv6 Address: 2607:----:----:1dd:fd3d:----:e479:c4c1 Subnet mask IPv6: 128 Gateway IPv6: fe80::217:----:----:e58f DNS servers 2607:f798:18:10:0:640:7125:5204 2607:f798:18:10:0:640:7125:5198 MTU: 1500The Diagnostics / States / States display tab shows a ton of activity: WTF is going on here?
IP # States Protocol # States Source Ports Dest. Ports 2607:f798:804:1dd:fd3d:9735:e479:c4c1 204 udp 203 1 Protocol counts IP # States Protocol # States Source Ports Dest. Ports 2600:9000:5304:2800::1 1 udp 1 1 2600:9000:5305:7800::1 1 udp 1 1 2600:9000:5302:6000::1 2 udp 2 1 2001:4860:4802:32::a 9 udp 9 1 2600:9000:5303:b600::1 3 udp 3 1 2600:9000:5304:bd00::1 1 udp 1 1 2001:502:1ca1::30 2 udp 2 1 2001:4860:4802:32::6b 1 udp 1 1 2600:9000:5301:fa00::1 1 udp 1 1 2600:9000:5307:c200::1 1 udp 1 1 2600:9000:5304:9400::1 1 udp 1 1 fe80::228:1aff:fee0:1004 1 ipv6-icmp 1 1 2600:9000:5306:d600::1 2 udp 2 1 2001:4860:4802:32::6a 1 udp 1 1 2600:9000:5305:bf00::1 1 udp 1 1 2001:4860:4802:38::6a 1 udp 1 1 2607:f8b0:400b:807::2003 1 ipv6-icmp 1 1 2001:500:856e::30 3 udp 3 1 2600:9000:5303:1000::1 1 udp 1 1 2600:9000:5305:4e00::1 1 udp 1 1 2600:9000:5307:8600::1 1 udp 1 1 2600:9000:5307:8e00::1 1 udp 1 1 2001:503:231d::2:30 1 udp 1 1 2600:9000:5302:7700::1 1 udp 1 1 2600:9000:5304:2000::1 1 udp 1 1 2401:fd80:400::1 3 udp 3 1 2600:9000:5302:e700::1 1 udp 1 1 2a01:618:400::1 1 udp 1 1 2600:9000:5307:1700::1 1 udp 1 1 2600:9000:5303:8e00::1 1 udp 1 1 2001:4860:4802:34::6e 1 udp 1 1 2001:500:48::1 3 udp 3 1 2001:501:b1f9::30 4 udp 4 1 2a00:1b98:1:0:20c:29ff:fe83:d782 4 udp 4 1 2001:4860:4802:34::a 16 udp 16 1 2600:9000:5303:1600::1 1 udp 1 1 2600:1401:2::f0 3 udp 3 1 2600:9000:5303:2e00::1 1 udp 1 1 2600:9000:5306:4e00::1 2 udp 2 1 2600:9000:5300:b700::1 1 udp 1 1 2600:9000:5302:d000::1 1 udp 1 1 2001:500:40::1 1 udp 1 1 2001:503:83eb::30 4 udp 4 1 2600:1480:f000::43 1 udp 1 1 2600:9000:5305:4c00::1 1 udp 1 1 2a06:fb00:1::1:96 1 udp 1 1 2001:500:f::1 3 udp 3 1 2001:678:20::41 1 udp 1 1 2600:1401:1::43 4 udp 4 1 2001:4860:4802:36::a 21 udp 21 1 2001:502:2eda::3 2 udp 2 1 2001:67c:26b4:7:21e:bff:fec7:87a 4 udp 4 1 2606:4700:50::adf5:3a7e 1 udp 1 1 2600:9000:5303:e00::1 1 udp 1 1 fe80::217:10ff:fe9a:e58f 1 ipv6-icmp 1 0 ::1 2 udp 2 1 2600:9000:5300:3e00::1 1 udp 1 1 2001:503:d2d::30 3 udp 3 1 2001:502:8cc::30 3 udp 3 1 2600:9000:5306:d400::1 1 udp 1 1 2600:9000:5307:3d00::1 1 udp 1 1 2600:9000:5300:1500::1 1 udp 1 1 2600:9000:5307:b500::1 1 udp 1 1 2600:9000:5304:2d00::1 1 udp 1 1 2a01:4f8:c0c:97af:ca62:cd80:657f:18cc 5 udp 5 1 2001:4860:4802:34::6b 1 udp 1 1 2001:dcd:1::10 1 udp 1 1 2600:9000:5302:6600::1 1 udp 1 1 2001:4860:4802:38::a 11 udp 11 1 2600:9000:5302:df00::1 2 udp 2 1 2001:503:39c1::30 3 udp 3 1 2600:9000:5301:7900::1 2 udp 2 1 2001:500:e::1 2 udp 2 1 2600:9000:5301:200::1 2 udp 2 1 2610:a1:1009::3 2 udp 2 1 2001:502:7094::30 4 udp 4 1 2a06:98c1:50::ac40:2154 1 udp 1 1 2600:9000:5304:a000::1 1 udp 1 1 2001:500:d937::30 2 udp 2 1 2600:1480:4800::43 1 udp 1 1 2001:503:a83e::2:30 4 udp 4 1 2600:9000:5302:f900::1 1 udp 1 1 2600:9000:5302:5400::1 1 udp 1 1 2600:9000:5301:7800::1 1 udp 1 1 2001:503:eea3::30 3 udp 3 1 2600:9000:5303:b900::1 1 udp 1 1 2600:9000:5302:c900::1 2 udp 2 1 2600:9000:5302:5600::1 1 udp 1 1 2600:9000:5303:9300::1 1 udp 1 1 2600:9000:5300:b800::1 1 udp 1 1 2a01:618:404::1 1 udp 1 1 2600:9000:5302:6900::1 1 udp 1 1 2600:9000:5301:e500::1 1 udp 1 1 2001:4860:4802:32::6c 1 udp 1 1 2600:9000:5306:fd00::1 1 udp 1 1 2401:fd80:404::1 2 udp 2 1Is this stuff is dangerous? Thoughts/suggestions?
EDIT: I had a pcap running (IPv6 traffic only) while I was doing this investigation, and it seems like I am getting a ton of DNS (Port 53) activity.
I want to shut it down if it is anything more than just resolving stuff for the IPTV box (Which I don't have yet). Why am I getting all this IPv6 traffic when don't have any internal interfaces with IPv6 enabled?
Now I need to figure out if I can get IPv6 through my SG300 switch and Ethernet over powerline adapter. I currently have a 3 VLAN IPv4 trunk that connects to my WiFi Access Point (2 Private SSIDs, and 1 GUEST.
I guess my next step is to create an interface for the IPv6 and send it to an access port on the SG300 to see if I have IPv6 connectivity. If that works, then I move on to the Ethernet over powerline.
-
@guardian said in Very Basic IPv6 security question.:
The reason for my negativity regarding IPv6 - In a word - ignorance -- It scares the crap out of me because it is so hard to control. I am getting a ton of IPv6 entries that I don't understand (see below) or how to control.
I think that's the case with a lot of people, but they forget it was the same when they started with IPv4. The basic principles of IPv6 are the same as IPv4. However, when it was designed, they took IPv4 and kept what worked and dropped what didn't. For example ICMPv6 is used for a lot to manage things. It gets rid of ARP, which existed before IPv4. Other things were done to improve performance, such as a fixed length header, etc..
I've been using IPv6 for over 13 years, initially with a 6in4 tunnel, but for the past 6.5 years with native IPv6 from Rogers.
The DPinger address was set to what I believe is a link local address: fe80:0:0:0:217:---:----:e58f, and it showed 100% packet loss, but when I changed the monitor address to 2607:f8b0:400b:807::2003 (Google.ca), the packet loss dropped to 0% and showed RTT/RTTsd values. So it appears that I have IPv6 connectivity, and the Status / Interfaces tab seems to confirm it. Is there a better monitor target, or a way to make pfSense pick a useful monitor IP automatically?
You have to use a routeable address for that. Link local won't work. I suspect this is a deficiency with pfSense. I ran traceroute to Google and used the first global address I saw.
Now I need to figure out if I can get IPv6 through my SG300 switch and Ethernet over powerline adapter. I currently have a 3 VLAN IPv4 trunk that connects to my WiFi Access Point (2 Private SSIDs, and 1 GUEST.
For things like switches, power line adapters, WiFi, etc., it makes no difference whether IPv4 or IPv6 is used. They're both valid Ethernet frames.
-
@guardian said in Very Basic IPv6 security question.:
The DPinger address was set to what I believe is a link local address: fe80:0:0:0:217:---:----:e58f, and it showed 100% packet loss, but when I changed the monitor address to 2607:f8b0:400b:807::2003 (Google.ca), the packet loss dropped to 0% and showed RTT/RTTsd values. So it appears that I have IPv6 connectivity, and the Status / Interfaces tab seems to confirm it. Is there a better monitor target, or a way to make pfSense pick a useful monitor IP automatically?
If you get a dedicated ISP handshake then pfSense will use the first external hop from your gateway (ie to your ISP's connection node) link-local address for IPv6 monitoring. If ICMPv6 is enabled (as it should be but your ISP may be doing something whacky on its first node) Dpinger will get a return ping6 to monitor.
Once you start to learn IPv6 you never look back. It is refreshing how simple it all is but just like IPv4, if you are new to it it does look daunting. Fear not, many of us have been running IPv6 for well over a decade and now find IPv4 restrictive or painful with kludges like NAT being relied upon.
There are many in the networking world, particularly those in the US, who have had IPv4 address space to spare and have simply taken the step of ignoring IPv6 and disabling it rather than learning about it. Meanwhile IPv6 is the backbone of the cell / mobile phone industry and for dedicated protocols such as those used with Thread, Matter, HomeKit, Zigbee and similar low-power home-meshing technology.
If the US had embraced IPv6 from the outset would they ever had to endure horrible things like CGNAT?
So come on in, the IPv6 pool is large, warm and friendly.
 ️
️ -
@RobbieTT said in Very Basic IPv6 security question.:
Meanwhile IPv6 is the backbone of the cell / mobile phone industry
Yep, my phone is IPv6 only and uses 464XLAT to access IPv4 only sites.
-
@guardian IPv6 is independent of the wired or wireless connection. One can run IP, NetBIOS, whatever it was Netware used to use :) or other protocols.
One thing about IPv6 alluded to above, is "they" figured out that if each PC has an IPv6 address then that PC can be tracked by that address. So most browsers and apps ask for a temporary IPv6 address to make connections, and eventually discard it. Windows shows this in ipconfig /all output:
IPv6 Address. . . . . . . . . . . : 2001:470:xxxxxxxxx(Preferred)
Temporary IPv6 Address. . . . . . : 2001:470:xxxxxxxxx(Deprecated)
Temporary IPv6 Address. . . . . . : 2001:470:xxxxxxxxx(Deprecated)
Temporary IPv6 Address. . . . . . : 2001:470:xxxxxxxxx(Deprecated)
Temporary IPv6 Address. . . . . . : 2001:470:xxxxxxxxx(Preferred)
Temporary IPv6 Address. . . . . . : 2001:470:xxxxxxxxx(Deprecated)This is possible because each /64 (each network) gets several quintillion addresses in the /64 block.
IPv6 is not inherently dangerous like IPv4 is not. If there are no firewall rules on WAN allowing unsolicited inbound traffic from the Internet, then there isn't any.
-
-
@JKnott Ah yes. We pretty much just removed it. :)
-
@RobbieTT said in Very Basic IPv6 security question.:
@guardian said in Very Basic IPv6 security question.:
The DPinger address was set to what I believe is a link local address: fe80:0:0:0:217:---:----:e58f, and it showed 100% packet loss, but when I changed the monitor address to 2607:f8b0:400b:807::2003 (Google.ca), the packet loss dropped to 0% and showed RTT/RTTsd values. So it appears that I have IPv6 connectivity, and the Status / Interfaces tab seems to confirm it. Is there a better monitor target, or a way to make pfSense pick a useful monitor IP automatically?
If you get a dedicated ISP handshake then pfSense will use the first external hop from your gateway (ie to your ISP's connection node) link-local address for IPv6 monitoring. If ICMPv6 is enabled (as it should be but your ISP may be doing something whacky on its first node) Dpinger will get a return ping6 to monitor.
Can you please explain how ICMPv6 should be enabled? Are you telling me that I need to add firewall rules to the WAN?

Once you start to learn IPv6 you never look back. It is refreshing how simple it all is but just like IPv4, if you are new to it it does look daunting. Fear not, many of us have been running IPv6 for well over a decade and now find IPv4 restrictive or painful with kludges like NAT being relied upon.
In some ways I agree with you - especially if you are creating "general infrastructure" where you are providing connectivity to customers and it is up to the customers to secure their own stuff. When it comes to privacy / blocking all the garbage that want;s to constantly phone home, it becomes a nightmare due to the sheer number of ip addresses involved.
I don't know if this is more or a pfSense thing than an IPv6 thing, but why when I only enabled IPv6 on the WAN, and have it disabled on all other interfaces am I getting so much IPv6 DNS traffic?
Then there is the size of the tables for AD blocking etc. just the increased sizze of the address alone causes the tables to balloon, and than there is the sheer number of extra addresses.
Do you run an ad blocker or attempt to control the behavior of Applications or IoT devices/
There are many in the networking world, particularly those in the US, who have had IPv4 address space to spare and have simply taken the step of ignoring IPv6 and disabling it rather than learning about it. Meanwhile IPv6 is the backbone of the cell / mobile phone industry and for dedicated protocols such as those used with Thread, Matter, HomeKit, Zigbee and similar low-power home-meshing technology.
If the US had embraced IPv6 from the outset would they ever had to endure horrible things like CGNAT?
I will agree with that one for sure!
So come on in, the IPv6 pool is large, warm and friendly.
 ️
️
Maybe so, but I might get Athlete's Foot from the pool deck. (All this #uc3ing DNS leakage???)@SteveITS said in Very Basic IPv6 security question.:
IPv6 is not inherently dangerous like IPv4 is not. If there are no firewall rules on WAN allowing unsolicited inbound traffic from the Internet, then there isn't any.
If the firewall block all uninitiated incoming by default, that solves some of the problem, but with interfaces being able to create their own random accresses with SLAAC, it makes controlling outbound traffic much more difficult.
@JKnott said in Very Basic IPv6 security question.:
For things like switches, power line adapters, WiFi, etc., it makes no difference whether IPv4 or IPv6 is used. They're both valid Ethernet frames.
Thanks for that - I suspected that was the case, but I wasn't sure.
I still need to figure out how to create the necessary IPv6 paths in my managed switch to get the IPv6 into the trunck, and then get it out agian in my new Tomato router.
-
@guardian said in Very Basic IPv6 security question.:
Are you telling me that I need to add firewall rules to the WAN?
The pfSense WAN firewall rule list is perfect as it was the day you installed pfSense.
And not only pfSense. Every router / firewall on planet earth, and probably in this solar system.
It's empty.
So : nothing gets in.@guardian said in Very Basic IPv6 security question.:
Can you please explain how ICMPv6 should be enabled?
Euh ... same way as ICMPv4 is 'enabled'.
Normally, the default LAN firewall rules (Netgate put them there - you saw them when you installed pfSense) will take care of things.
The role of ICMPv6 is more important as what ICMPv4 does.@guardian said in Very Basic IPv6 security question.:
Then there is the size of the tables for AD blocking etc. just the increased sizze of the address alone causes the tables to balloon, and than there is the sheer number of extra addresses.
Do you run an ad blocker or attempt to control the behavior of Applications or IoT devices/
True. In the future, it will be harder to keep a list with IPs or networks with 'known sources'.
Even the number of domain names is growing every day. Every domain name can point to many IPs.
Gradually, we, humans, will have to change.
If you don't want to see all the garbage, don't go looking for it.
That is : do not use tools/stuff/whatever (applications) that pulls in all this stuff.@guardian said in Very Basic IPv6 security question.:
the firewall block all uninitiated incoming by default
That's the principal role of a firewall.
initiated traffic on the trusted network(s) (LAN) passes, and replies for this that come back, is granted.
Traffic initiated on the non trusted network(s) (WAN) is blocked.@guardian said in Very Basic IPv6 security question.:
I still need to figure out how to create the necessary IPv6 paths in my managed switch
A switch is a dumb device that uses MAC addresses, which are a level lower.
A witch doesn't bother with TCP, UDP, ICMP or higher IPX, IPv4, IPv6 or even higher. A switch looks at the packet headers, uses MAC source and destination and doesn't care for the rest - extra packet info and payload.
A smart switch can blur this concept a bit, but in general : VLAN's are packets with a vlan tag ID. These can get grouped or separated out. VLAN exists because some one (the admin of course) was to lazy to pull more wires ( : or, to handle situations where more wires would introduce more weight : example : plains, etc )
: or, to handle situations where more wires would introduce more weight : example : plains, etc ) -
@Gertjan said in Very Basic IPv6 security question.:
@guardian said in Very Basic IPv6 security question.:
Are you telling me that I need to add firewall rules to the WAN?
The pfSense WAN firewall rule list is perfect as it was the day you installed pfSense.
And not only pfSense. Every router / firewall on planet earth, and probably in this solar system.
It's empty.
So : nothing gets in.@guardian said in Very Basic IPv6 security question.:
Can you please explain how ICMPv6 should be enabled?
Euh ... same way as ICMPv4 is 'enabled'.
Normally, the default LAN firewall rules (Netgate put them there - you saw them when you installed pfSense) will take care of things.
The role of ICMPv6 is more important as what ICMPv4 does.It has been so long since I set pfSense up, but I don't remember any ICMP rules. I don't think it adds any new rules because I enabled IPv6. Can someone tell me what rules I should have on the WAN for dual stack IPv4/6. Maybe that is why my pingers don't get set up correctly.
-
How can I control DNS leakage. I had a tightly controlled IPv4 network - no IPv6 on any interface, and all DNS traffic forced through unbound.
All I did was enable IPv6 on the WAN, and Diagnostics / Stages summary shows approximately 200 UDP states, which I have confirmed by PCAP are DNS calls. How can I lock this down?
-
@guardian Any particular port, say 5353 for example?
-
@guardian said in Very Basic IPv6 security question.:
Can someone ...
Default WAN firewall list : No RULES at all.
This stands as long as you do not have devices that you want to reach 'from the Internet'.
Example : If you have an internal web server, or mail server on your LAN, you need to add firewall rules to permit incoming traffic on the WAN interface (IPv4 : a NAT rule - IPv6 : just a firewall rule).
Another example : If you have a Openserver running on your pfSense, so you can admin it while on holiday, you need a firewall rule to permit incoming traffic to the OpenVPN server.
Another example : If you have a NAS that you want to make viosible on the Internet so you can share all your movies with your friends, you need a firewall rule (IPv4 : again a NAT rule).These are my WAN rules ;
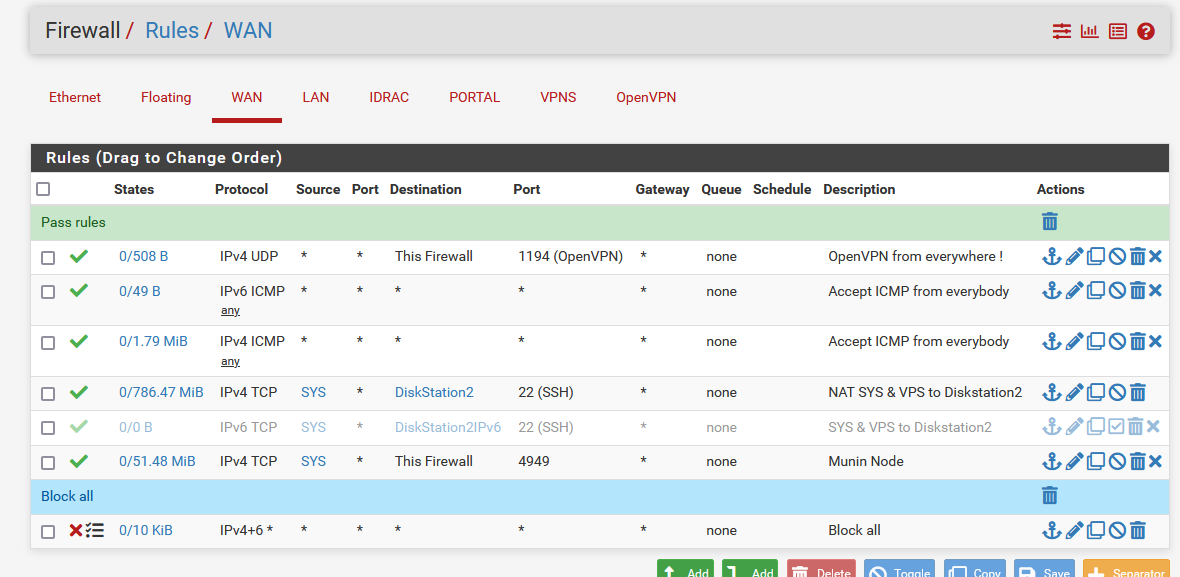
First rule : I like to admin pfSense 24h/24 (don't ask why).
Rule 2 : I accepts all incoming ICMPv6 traffic (don't ask why - this is probably for testing purposes).
Rule 3 : Same thing for ICMPv4.
Rule 4 : I have a group of dedicated bare bone servers somewhere in a data centre in paris. They are grouped up in an alias, and these have access to my Syno NAS for backup purposes.
Rule 5 : de activated. My ISP stills sucks when it comes to Ipv6 : my upstream router doesn't allow me allow incoming IPv6 traffic on it's prefixes, used by pfSense.
Rule 6 : Incoming Munin traffic as I have a Munin** node running on pfSense - which allows me to create this, because I do like reading log lines, but I've nothing against images.
Rule 7 and explicit "Block all" rule.Note : there is a last hidden Rule : implicit : Block all. This means that if you have no rules on an interface, all incoming traffic will be blocked. This is valid for every pfSense interface : WAN LAN whatever.
That's why the default LAN firewall rule list has one pass rule on it for all traffic.@guardian said in Very Basic IPv6 security question.:
Maybe that is why my pingers don't get set up correctly.
pingers == the pfSense dpinger procces ?
dpinger runs 'in' process so it can use any interface to send traffic OUT of any interface.
"OUT" is out of the box, going to any device elsewhere, outside of pfSense.
The pfSense firewall rules are operational on INCOMING == going into the box.There is this concept : use firewall rules here :
My advise : don't do that !!
If you have to, first : read the complete Netgate pfSense user manual.
Then : watch some video where they show examples.
Sign the dis-charger.
Go to a mirror and say out loud : "they told me not to do so - but I'm going to so any way".
Now you're ready to use floating rules. It was nice talking to you. -
@guardian said in Very Basic IPv6 security question.:
but why when I only enabled IPv6 on the WAN, and have it disabled on all other interfaces am I getting so much IPv6 DNS traffic?
because unbound is using IPv6 to query the roots. and authoritative dns..
;1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.8.2.4.0.3.5.0.0.0.9.0.0.6.2.ip6.arpa. IN PTR ;; ANSWER SECTION: 1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.8.2.4.0.3.5.0.0.0.9.0.0.6.2.ip6.arpa. 86400 IN PTR ns-1064.awsdns-05.org.;; QUESTION SECTION: ;1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.8.7.5.0.3.5.0.0.0.9.0.0.6.2.ip6.arpa. IN PTR ;; ANSWER SECTION: 1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.8.7.5.0.3.5.0.0.0.9.0.0.6.2.ip6.arpa. 86400 IN PTR ns-1400.awsdns-47.org.this is gtld server
;; QUESTION SECTION: ;0.3.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.1.a.c.1.2.0.5.0.1.0.0.2.ip6.arpa. IN PTR ;; ANSWER SECTION: 0.3.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.1.a.c.1.2.0.5.0.1.0.0.2.ip6.arpa. 86400 IN PTR e.gtld-servers.net.The other 2 were dns on aws.. etc..
See the e.gtld - that is a NS for the .com tld
;; QUESTION SECTION: ;com. IN NS ;; ANSWER SECTION: com. 86400 IN NS h.gtld-servers.net. com. 86400 IN NS j.gtld-servers.net. com. 86400 IN NS e.gtld-servers.net. com. 86400 IN NS g.gtld-servers.net. com. 86400 IN NS k.gtld-servers.net. com. 86400 IN NS i.gtld-servers.net. com. 86400 IN NS c.gtld-servers.net. com. 86400 IN NS b.gtld-servers.net. com. 86400 IN NS m.gtld-servers.net. com. 86400 IN NS d.gtld-servers.net. com. 86400 IN NS l.gtld-servers.net. com. 86400 IN NS f.gtld-servers.net. com. 86400 IN NS a.gtld-servers.net.;; QUESTION SECTION: ;e.gtld-servers.net. IN AAAA ;; ANSWER SECTION: e.gtld-servers.net. 86400 IN AAAA 2001:502:1ca1::30You could check them all.. to see what they are..
Look in your dns resolver status
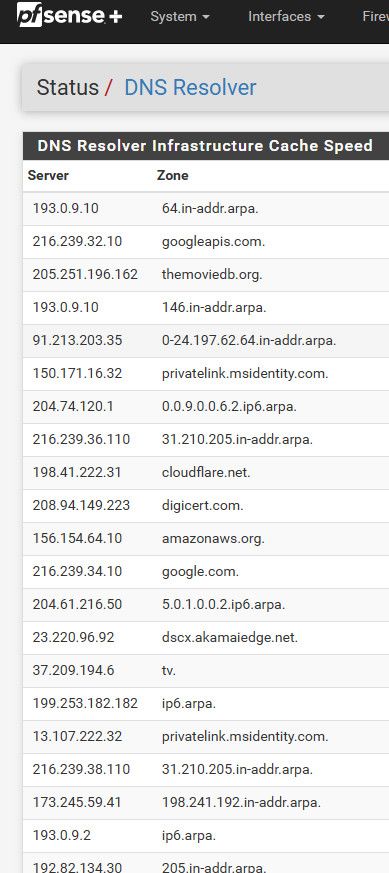
Notice mine only has IPv4 - because I told unbound not to use IPv6. I have IPv6 setup and working, but I don't see any point in having unbound use IPv6 through my HE tunnel. So I tell it not to use the IPv6 for dns.
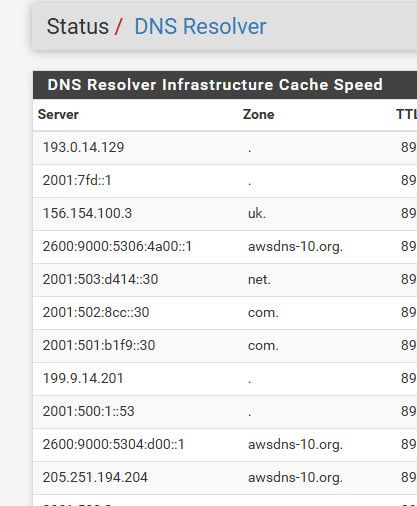
do-ip6: <yes or no> Enable or disable whether ip6 queries are answered or issued. Default is yes. If disabled, queries are not answered on IPv6, and queries are not sent on IPv6 to the internet nameservers. With this option you can disable the IPv6 transport for sending DNS traffic, it does not impact the contents of the DNS traffic, which may have ip4 and ip6 addresses in it.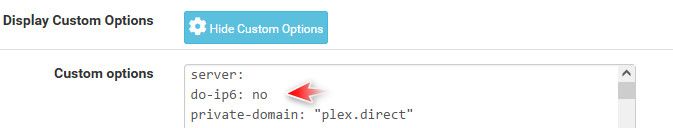
If I turn that off - look at that making queries to IPv6.
-
@guardian said in Very Basic IPv6 security question.:
If the firewall block all uninitiated incoming by default, that solves some of the problem, but with interfaces being able to create their own random accresses with SLAAC, it makes controlling outbound traffic much more difficult.
How often do you worry about outgoing traffic?
@guardian said in Very Basic IPv6 security question.:
I still need to figure out how to create the necessary IPv6 paths in my managed switch to get the IPv6 into the trunck, and then get it out agian in my new Tomato router.
http://groklawstatic.ibiblio.org/staticpages/index.php%3fpage=2005010107100653
Switches have nothing to do with IPv4 vs IPv6. They're for Ethernet frames. If you have a path for IPv4, you'll have one for IPv6 too.
-
@Gertjan said in Very Basic IPv6 security question.:
VLAN exists because some one (the admin of course) was to lazy to pull more wires ( : or, to handle situations where more wires would introduce more weight : example : plains, etc )
Or for things like VoIP phones, where the phone and a computer share a switch port. Same with access points with more than one SSID.
-
@JKnott said in Very Basic IPv6 security question.:
@guardian said in Very Basic IPv6 security question.:
If the firewall block all uninitiated incoming by default, that solves some of the problem, but with interfaces being able to create their own random accresses with SLAAC, it makes controlling outbound traffic much more difficult.
How often do you worry about outgoing traffic?
All the time.... I choke off IoT, most Microsoft traffic including updates (I open updates when I want to update, not when M$ wants to jam them down my throat), as well as ad blocking and known C&C/Malware networks. Once I go into IPv6 I end up with a lot of extra complexity and overhead.
@guardian said in Very Basic IPv6 security question.:
I still need to figure out how to create the necessary IPv6 paths in my managed switch to get the IPv6 into the trunck, and then get it out agian in my new Tomato router.
http://groklawstatic.ibiblio.org/staticpages/index.php%3fpage=2005010107100653
Switches have nothing to do with IPv4 vs IPv6. They're for Ethernet frames. If you have a path for IPv4, you'll have one for IPv6 too.
OK, maybe I don't understand, but it looks like on this L3 managed switch (SG300), IPv6 must be enabled or set up in some way.
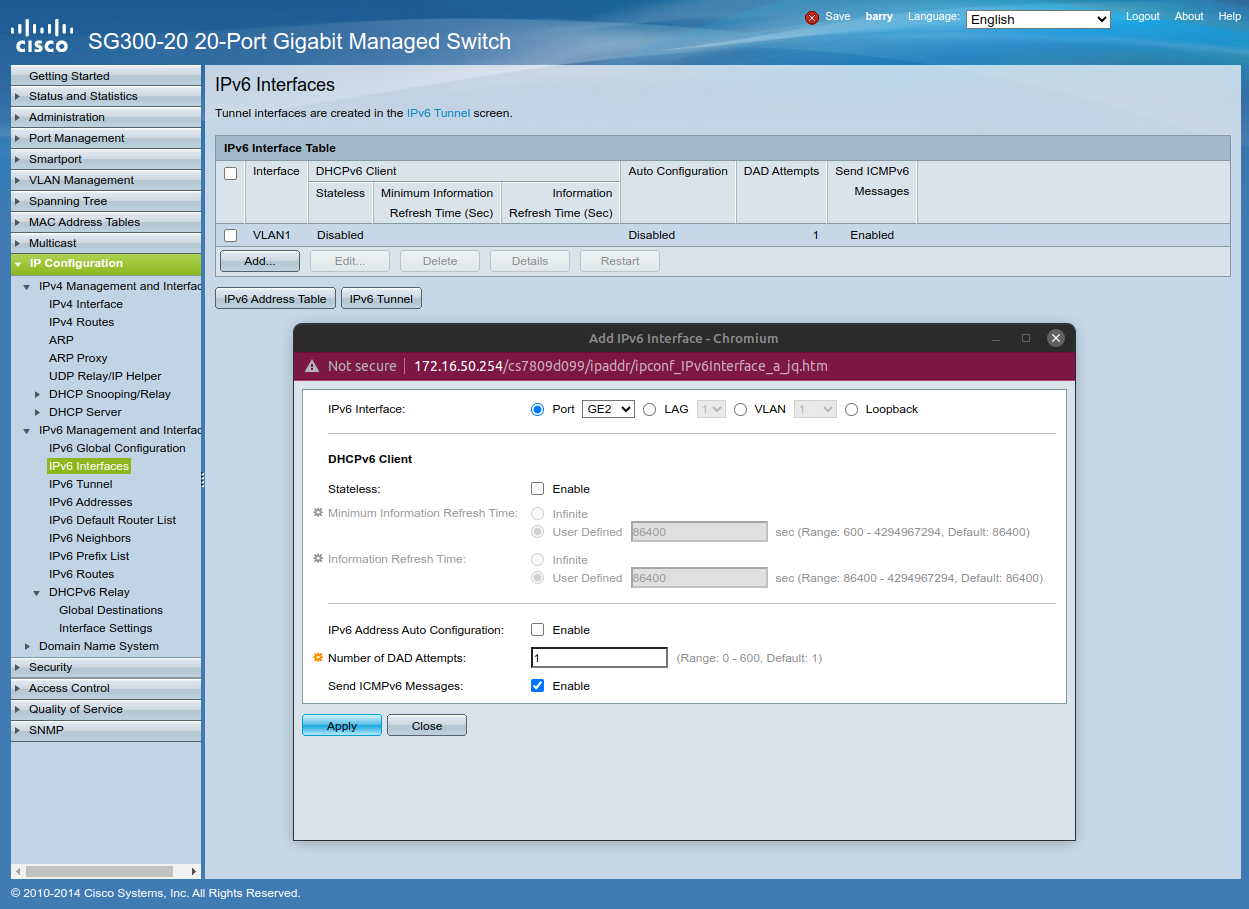
It has been so long and infrequently that I have had to interact with the switch once I set it up (beyond using the monitor tap function)
-
@guardian said in Very Basic IPv6 security question.:
How often do you worry about outgoing traffic?
All the time.... I choke off IoT, most Microsoft traffic including updates (I open updates when I want to update, not when M$ wants to jam them down my throat), as well as ad blocking and known C&C/Malware networks. Once I go into IPv6 I end up with a lot of extra complexity and overhead.
Generally, you'd have IoT on it's own network. You can set up a network with only Unique Local Addresses for them.
OK, maybe I don't understand, but it looks like on this L3 managed switch (SG300), IPv6 must be enabled or set up in some way.
You didn't mention L3 switch before. You deal with them the same way as a router. However, is that actually a L3 switch? The Cisco spec doesn't seem to mention that.
BTW, I have a Cisco SG200 switch and while it has some IPv6 settings, it's not a L3 switch.
-
@JKnott said in Very Basic IPv6 security question.:
@guardian said in Very Basic IPv6 security question.:
How often do you worry about outgoing traffic?
All the time.... I choke off IoT, most Microsoft traffic including updates (I open updates when I want to update, not when M$ wants to jam them down my throat), as well as ad blocking and known C&C/Malware networks. Once I go into IPv6 I end up with a lot of extra complexity and overhead.
Generally, you'd have IoT on it's own network. You can set up a network with only Unique Local Addresses for them.
At the moment I only have cameras (which are only allowed to contact a server that I control for remote storage of motion capture), and an ATA which I restrict to only contacting the provider's servers. Both are old and don't support IPv6 AFAIK.
OK, maybe I don't understand, but it looks like on this L3 managed switch (SG300), IPv6 must be enabled or set up in some way.
You didn't mention L3 switch before. You deal with them the same way as a router. However, is that actually a L3 switch? The Cisco spec doesn't seem to mention that.
BTW, I have a Cisco SG200 switch and while it has some IPv6 settings, it's not a L3 switch.
I don't beleve I was explicit, I just said pfSense -> Managed Switch -> Ethernet of Powerline -> Fresh Tomato Router as Switch and Access Points.
I believe that the 2 in SG200 means Layer 2, and SG300 is Layer 3. Am I misinterpreting the info from the table below or is the SG300 a Layer 3 switch?
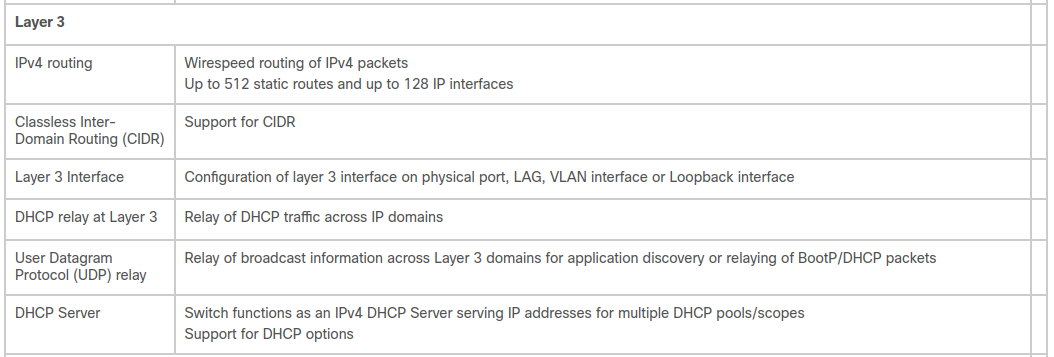
-
@guardian said in Very Basic IPv6 security question.:
is the SG300 a Layer 3 switch?
yes - if you put it layer 3 mode.. It can then be either just layer 2 or 3..
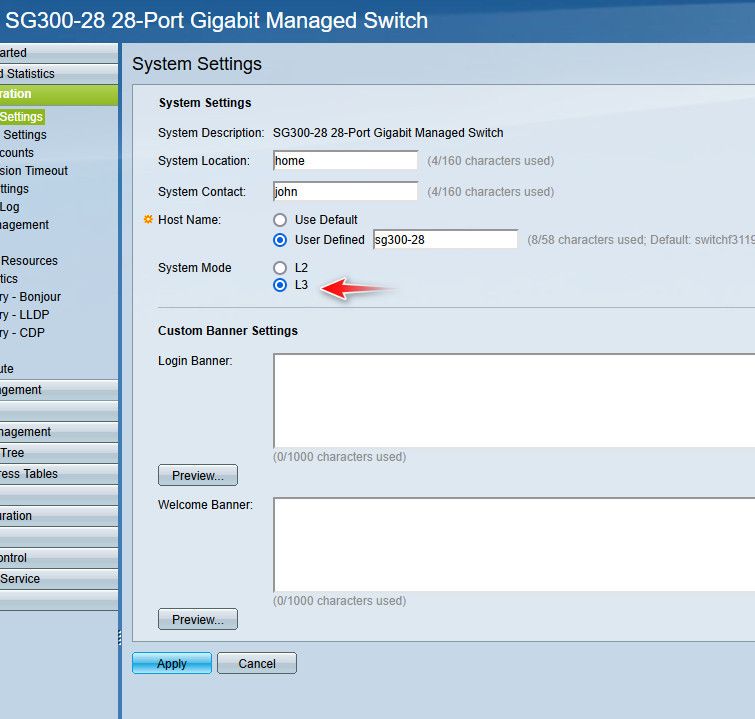
I have mine in 3 mode, but I am currently only doing layer 2 with it..
edit: and yes I gave it a very thoughtful and imaginative host name ;)
You do not need to setup any IPv6 on your switch if you don't want to - its pretty pointless unless you were going to actual route IPv6 with it, or if you wanted to access it for management over IPv6.