Very Basic IPv6 security question.
-
@guardian said in Very Basic IPv6 security question.:
How often do you worry about outgoing traffic?
All the time.... I choke off IoT, most Microsoft traffic including updates (I open updates when I want to update, not when M$ wants to jam them down my throat), as well as ad blocking and known C&C/Malware networks. Once I go into IPv6 I end up with a lot of extra complexity and overhead.
Generally, you'd have IoT on it's own network. You can set up a network with only Unique Local Addresses for them.
OK, maybe I don't understand, but it looks like on this L3 managed switch (SG300), IPv6 must be enabled or set up in some way.
You didn't mention L3 switch before. You deal with them the same way as a router. However, is that actually a L3 switch? The Cisco spec doesn't seem to mention that.
BTW, I have a Cisco SG200 switch and while it has some IPv6 settings, it's not a L3 switch.
-
@JKnott said in Very Basic IPv6 security question.:
@guardian said in Very Basic IPv6 security question.:
How often do you worry about outgoing traffic?
All the time.... I choke off IoT, most Microsoft traffic including updates (I open updates when I want to update, not when M$ wants to jam them down my throat), as well as ad blocking and known C&C/Malware networks. Once I go into IPv6 I end up with a lot of extra complexity and overhead.
Generally, you'd have IoT on it's own network. You can set up a network with only Unique Local Addresses for them.
At the moment I only have cameras (which are only allowed to contact a server that I control for remote storage of motion capture), and an ATA which I restrict to only contacting the provider's servers. Both are old and don't support IPv6 AFAIK.
OK, maybe I don't understand, but it looks like on this L3 managed switch (SG300), IPv6 must be enabled or set up in some way.
You didn't mention L3 switch before. You deal with them the same way as a router. However, is that actually a L3 switch? The Cisco spec doesn't seem to mention that.
BTW, I have a Cisco SG200 switch and while it has some IPv6 settings, it's not a L3 switch.
I don't beleve I was explicit, I just said pfSense -> Managed Switch -> Ethernet of Powerline -> Fresh Tomato Router as Switch and Access Points.
I believe that the 2 in SG200 means Layer 2, and SG300 is Layer 3. Am I misinterpreting the info from the table below or is the SG300 a Layer 3 switch?
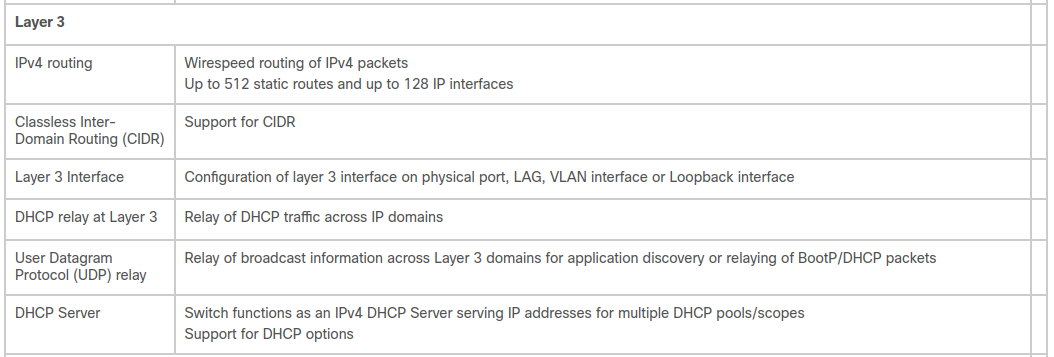
-
@guardian said in Very Basic IPv6 security question.:
is the SG300 a Layer 3 switch?
yes - if you put it layer 3 mode.. It can then be either just layer 2 or 3..
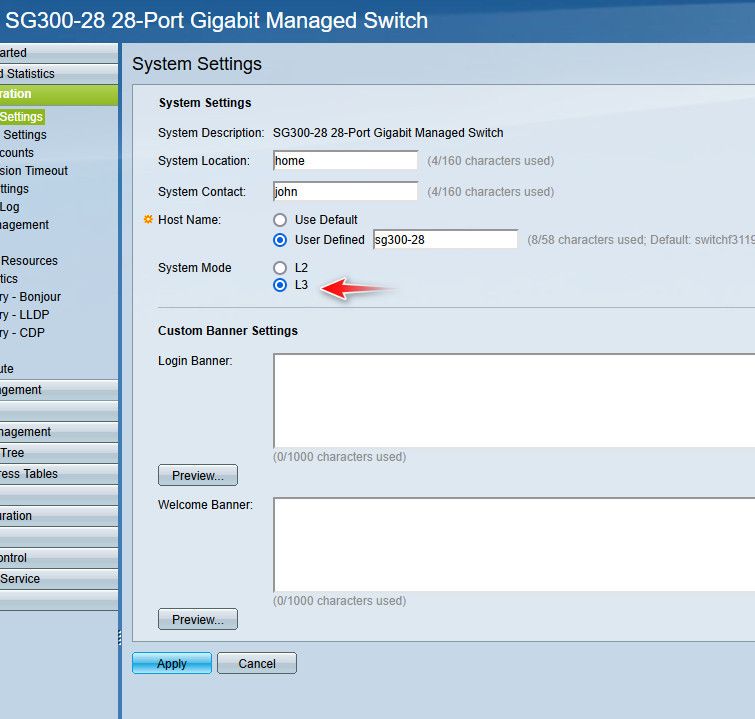
I have mine in 3 mode, but I am currently only doing layer 2 with it..
edit: and yes I gave it a very thoughtful and imaginative host name ;)
You do not need to setup any IPv6 on your switch if you don't want to - its pretty pointless unless you were going to actual route IPv6 with it, or if you wanted to access it for management over IPv6.
-
@johnpoz said in Very Basic IPv6 security question.:
@guardian said in Very Basic IPv6 security question.:
but why when I only enabled IPv6 on the WAN, and have it disabled on all other interfaces am I getting so much IPv6 DNS traffic?
because unbound is using IPv6 to query the roots. and authoritative dns..
[Snip]
@johnpoz thanks very much for taking so much time to put together such a detailed answer. As always you are right on!
Look in your dns resolver status. Notice mine only has IPv4 - because I told unbound not to use IPv6. I have IPv6 setup and working, but I don't see any point in having unbound use IPv6 through my HE tunnel. So I tell it not to use the IPv6 for dns.
do-ip6: <yes or no> Enable or disable whether ip6 queries are answered or issued. Default is yes. If disabled, queries are not answered on IPv6, and queries are not sent on IPv6 to the internet nameservers. With this option you can disable the IPv6 transport for sending DNS traffic, it does not impact the contents of the DNS traffic, which may have ip4 and ip6 addresses in it.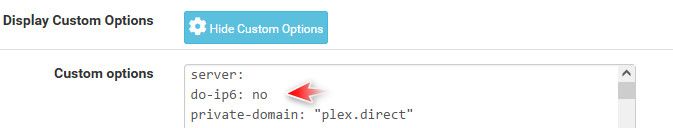
@johnpoz that's the magic spell - thanks so much.... Nasty IPv6 DNS Traffic all gone! :)
@johnpoz said in Very Basic IPv6 security question.:
@guardian said in Very Basic IPv6 security question.:
is the SG300 a Layer 3 switch?
yes - if you put it layer 3 mode.. It can then be either just layer 2 or 3..
[SNIP]
You do not need to setup any IPv6 on your switch if you don't want to - its pretty pointless unless you were going to actual route IPv6 with it, or if you wanted to access it for management over IPv6.
@johnpoz Thanks that helps!
-
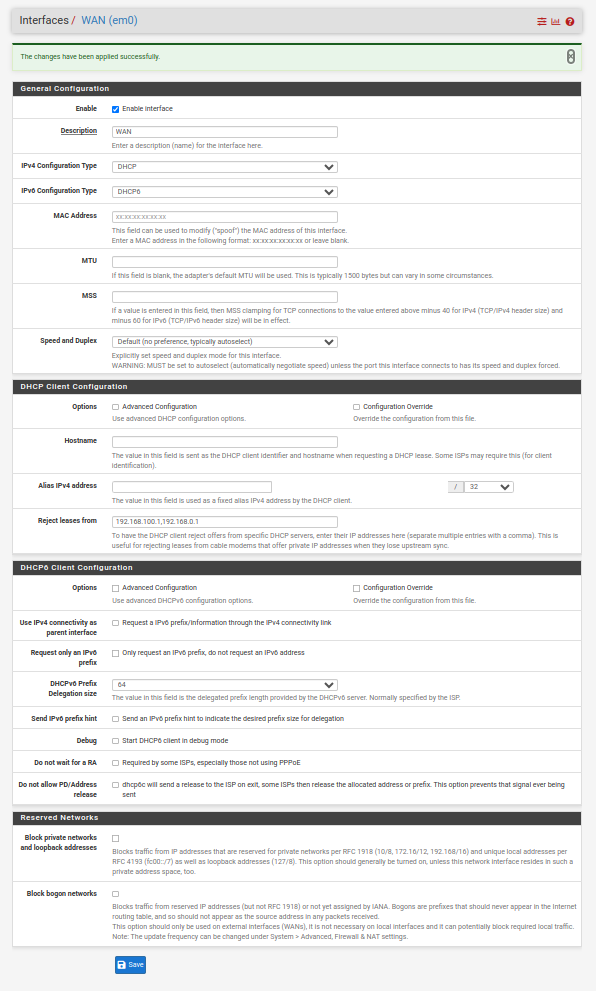
Have I configured pfSense IPv6 Correctly? I am attempting to configure a VLAN6 which I am connecting over a trunk to an SG300 switch, and ultimately to an access port on GE2. The IPv4 is working fine, I get an IP assignment, and a DHCP server, but the IPv6 isn't working. I have a linux laptop connected to GE2 with DHCP configuration for both IPv4/v6. I have no IPv6 connectivity - a ping6 to 2607:f8b0:400b:804::2003 from the laptop results in Destination unreachable: Beyond scope of source address, but is successful if executed from the pfSense WebGUI.
The laptop has an fe80::/64, and the Default Route has an fe80:: address as well. There are no other entries, and if I attempt to run ping6 against the Defaut route, I get invalid argument. For some reason ping6 does not liek fe80 addresses--even when I fully expanded :: with the appropriate number of 0000 to make 8 complete hextets
I need to determine if the problem is with pfSense, the SG300, or the laptop, so any guidance would be much appreciated.
-
@guardian said in Very Basic IPv6 security question.:
The laptop has an fe80::/64, and the Default Route has an fe80:: address as well.
That is a link-local address, that is not gua.. So no you wouldn't be able to ping some gua address of 2607:f8b0:400b:804::2003
-
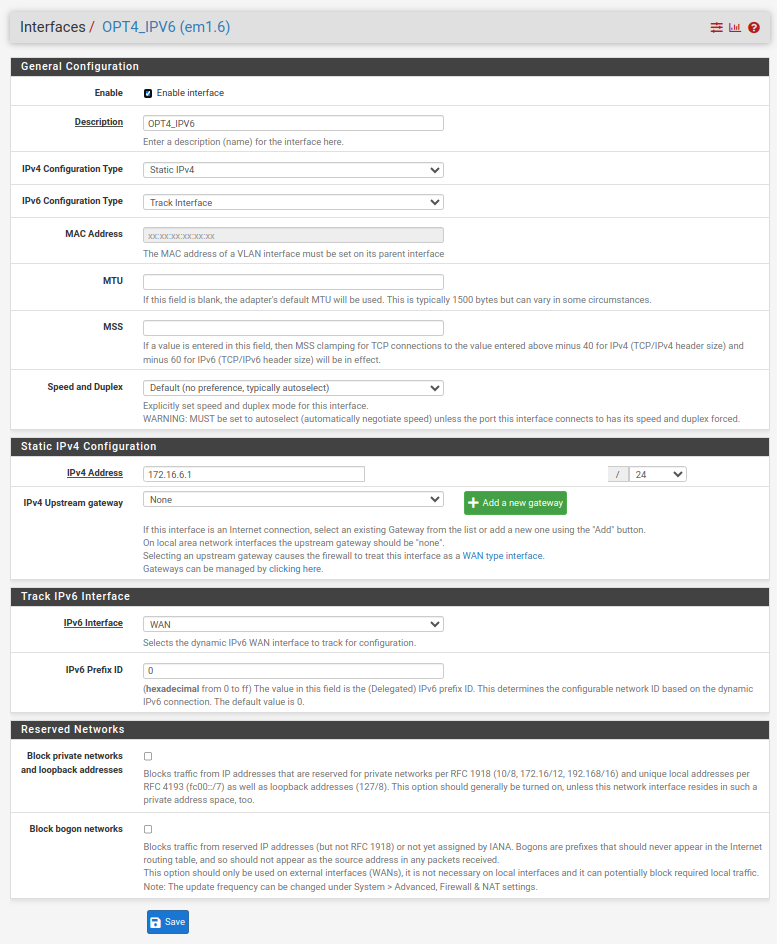
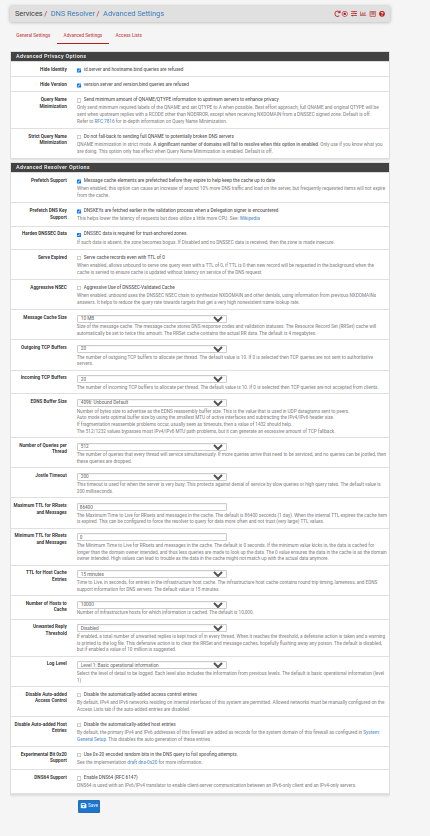
You are not configured for it to work just yet. For the Interfaces / WAN I would start by checking the boxes below and you will also have to determine what the prefix delegation size is from your ISP. A nice fat /48 is typical (as I have on the example below), with some ISPs trimming this down to a /56 (as it is still massive). Hopefully you don't just have a /64 but I understand that there are some ISPs that are that dumb/restrictive (particularly in the US it seems).
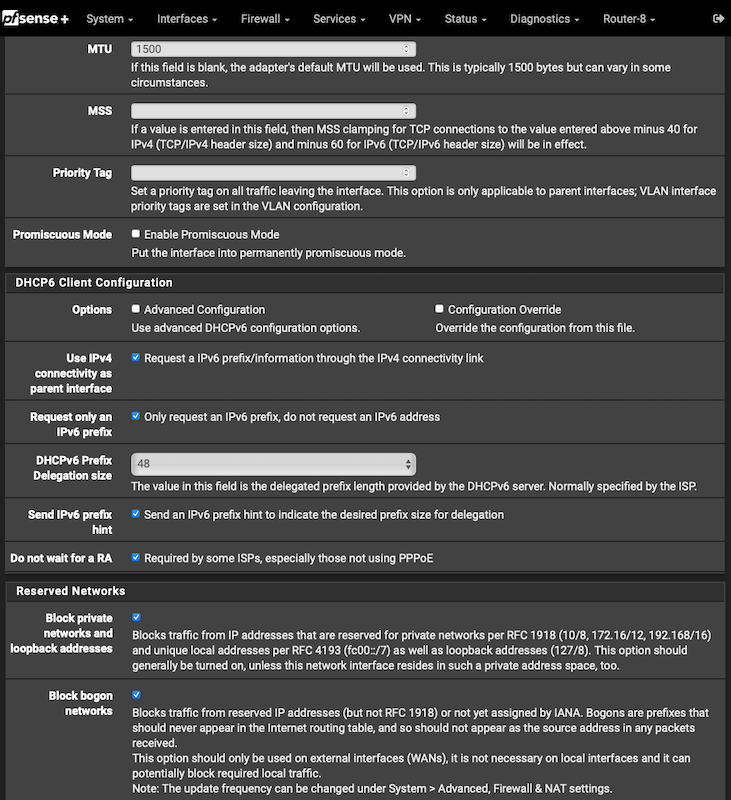
More to do after that on your LAN(s)/VLANs, DHCPv6 Server and Router Advertisements but the above is as good as any starting point. That and reading the section in the pfSense manual.
 ️
️ -
This page :
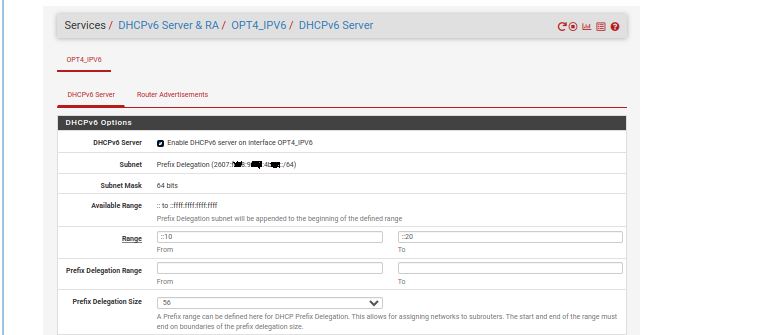
Normally, the /56 should be /64
Your OPT4_IPV6 is uses a prefix (carved out of the /56, so one of the 256 avaible upstream) /64
I advise you to look for more info.
Here : System > Advanced > Networking and check "DHCP6 Debug". Save.
Disconnect the WAN, and reconnect;
Follow what happens here : Status > System Logs > DHCP. Important is, for now, what "dhcp6c" is telling you (the dhcp IPv6 CLIENT - the dhcp process on tha WAN side, doing IPv6 stuff).
You want to see that it obtained a 'prefix' so it can be sued 'somewhere' :: your OPT4_IPV6 interface.You should see a line that says it received a IPv6 network (prefix) like this :
What you can do now, it hard code things. That's what I'm doing myself right now.
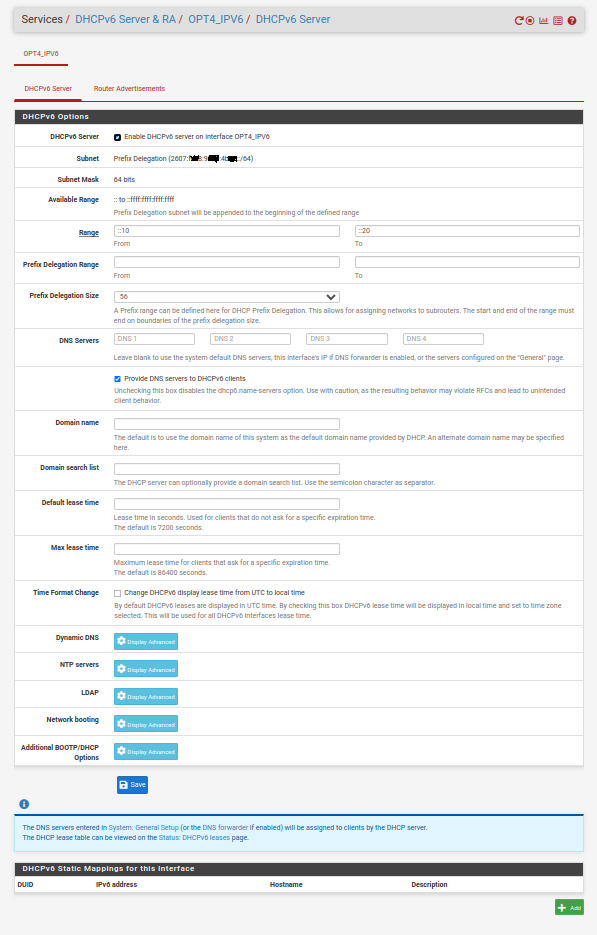
My LAN DHCPv6 server settings :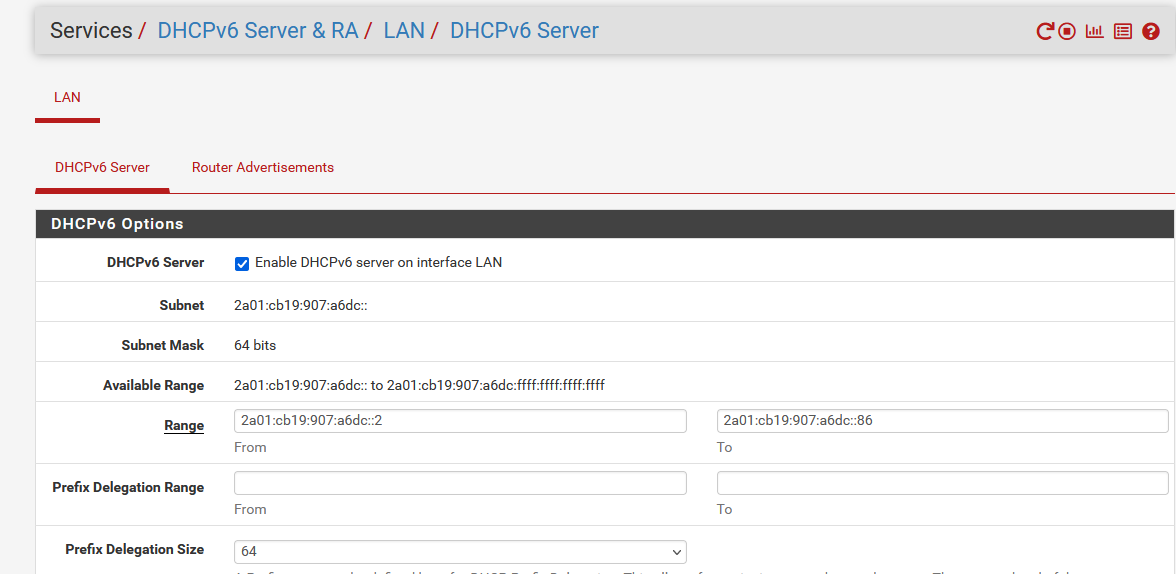
Because I know that I will receive "2a01:cb19:xO7:a6dc" as a prefix, I "hard coded" it.
When that part is done, back to the DHCP server - now set up :
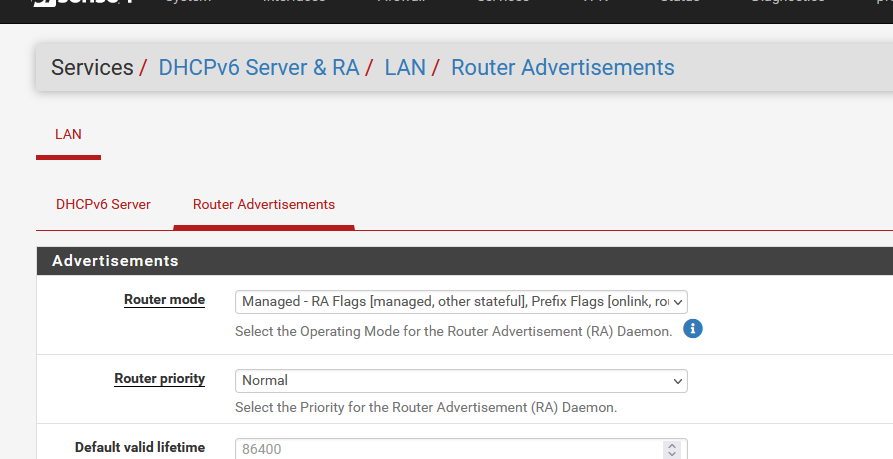
Why : "because it works for me"


Or : This setting make DHCP IPV6 client behave how how IPv4 DHCP behave.Now you should see in the logs :
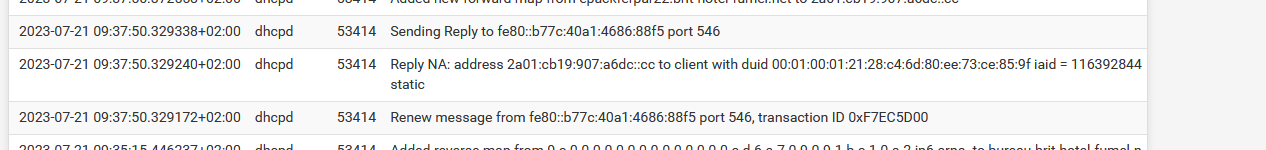
Btw : I also use DHCPv6 Static MAC .. sorry "DUID" mappings so my IPv6 devices always receive the same IPv6 under my control. Exactly like the v4 way.
I know, your - this setting :
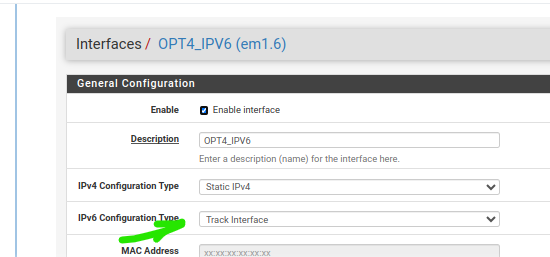
is better as you don't control what the prefix will me tomorrow : your upstream ISP router, or the ISP, can change that prefix. This is why is 'tracking' exists : When the prefix is known (obtained by the DHCPv6 client) it will be used by the DHCPv6 server.
And yes, there can be multiple LANs so multiple FHCPv6 servers, so multiple prefixes. In theory, pfSense could ask for 256 (/56) prefixes, as your ISP has them available for you. -
For simplicity I suggest the following, to keep your IPv6 prefix in line with what your ISP is offering you:
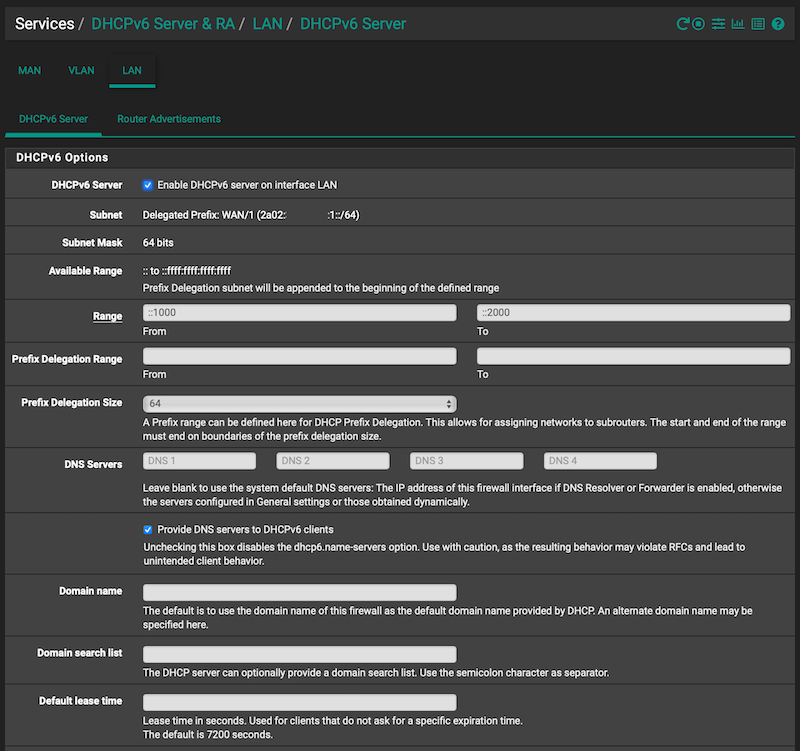
For the Router Advertisements / Router Mode I suggest either Assisted or Stateless (aka SLAAC). I use Assisted as it works better for my clients (especially for some Apple devices) but SLAAC is common too. I would not use the others listed unless you know what you are doing and why:
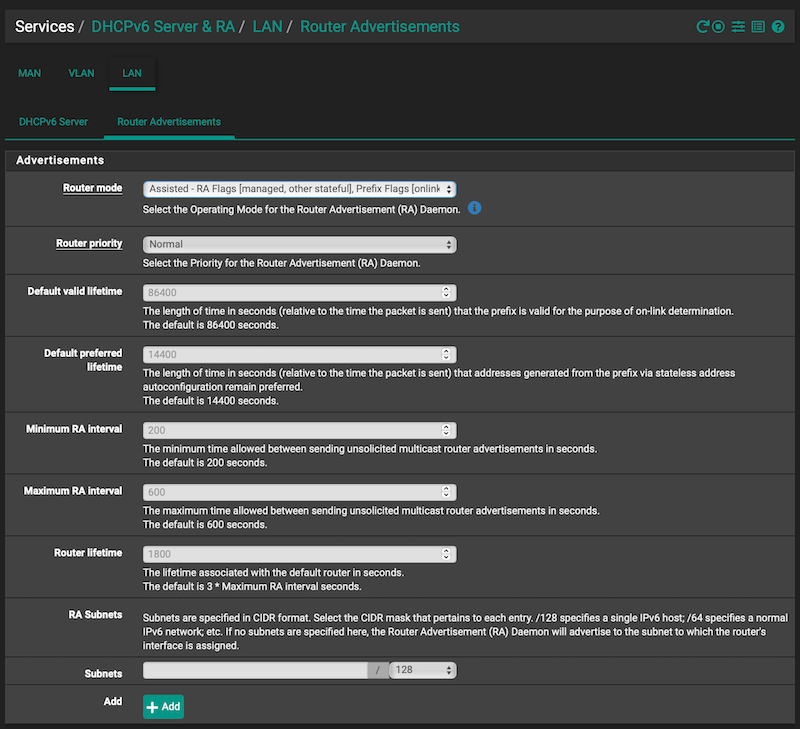
This is all in an effort to keep things simple and clear.
 ️
️ -
@RobbieTT said in Very Basic IPv6 security question.:
... keep things simple and clear.
Yes ... but .... This :
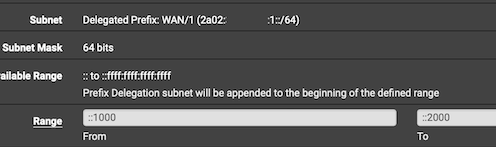
will assign IPv6 GUA's to clients like
2a0
 bsde:cdab:1234:5678:9abcd:[1000->2000]
bsde:cdab:1234:5678:9abcd:[1000->2000]I prefer the 2a0
 bsde:cdab::[1000->2000] ==> simple and clear
bsde:cdab::[1000->2000] ==> simple and clear
Again : I know, treating the prefix as a static value is plain wrong / can bite you back in the future (== break your IPv6 networking).
-
@Gertjan said in Very Basic IPv6 security question.:
will assign IPv6 GUA's to clients like
2a0
 bsde:cdab:1234:5678:9abcd:[1000->2000]
bsde:cdab:1234:5678:9abcd:[1000->2000]No, you are mistaken. When configured as stated the DHCPv6 leases look like:
2axx:xxx:xxxx:1::16be
With the ':1::' above being this particular LAN network prefix and the remaining 4 digits identifying the host.
You also get the full GUA, privacy addresses et al.
Example pfSense IPv6 leases, when configured as stated:
cat /var/dhcpd/var/db/dhcpd6.leases # The format of this file is documented in the dhcpd.leases(5) manual page. # This lease file was written by isc-dhcp-4.4.3-P1 # authoring-byte-order entry is generated, DO NOT DELETE authoring-byte-order little-endian; server-duid "\000\001\000\001+\240\234\326\220\redacted\251"; ia-na "\000\000\000\000\000\001\000\001*G\035m\redacted\303X" { cltt 5 2023/07/21 09:25:26; iaaddr 2a02:reda:cted:1::10d9 { binding state active; preferred-life 4500; max-life 7200; ends 5 2023/07/21 11:25:26; } } ia-na "f\263\3222\000\003\000\001\000\redacted\263f" { cltt 4 2023/07/20 03:01:42; } ia-na "\000\000\000\000\000\001\000\001)\232\244\230\330\276\redacted\254<" { cltt 5 2023/07/21 09:31:17; iaaddr 2a02:reda:cted:1::15de { binding state active; preferred-life 4500; max-life 7200; ends 5 2023/07/21 11:30:20; } } ia-na "\000\000\000\000\000\001\000\001)\232\242\017\304\221\014\redacted3\341" { cltt 5 2023/07/21 09:24:41; iaaddr 2a02:reda:cted:1::12b9 { binding state active; preferred-life 4500; max-life 7200; ends 5 2023/07/21 11:24:41; } } [snip…] ️
️ -
@RobbieTT said in Very Basic IPv6 security question.:
No, you are mistaken. When configured as stated the DHCPv6 leases look like:
2axx:xxx:xxxx:1::16be
With the ':1::' above being this particular LAN network prefix and the remaining 4 digits identifying the host.
You also get the full GUA, privacy addresses et al.
You know : I know I'm doing something wrong, and I'm trying to understand what I'm doing wrong for long time now.
So, Let try again :
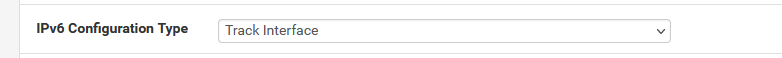
with :
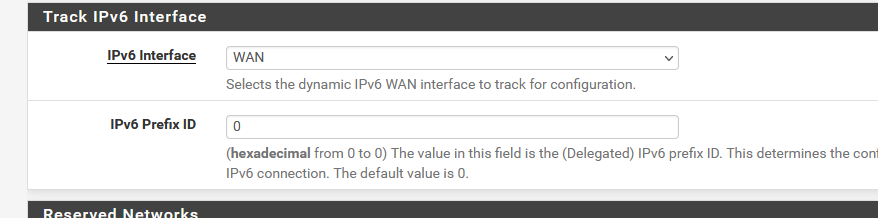
( My ISP router announces in it's own GUI that it has a /56 available, but pfSense (dhcp6c) doesnt show a "256" - it shows 0 to 0 ? So I chose zero ... )
dhcp6c manages to obtain the prefix "2a01:cb19:907:a6dc" - and only this prefix.
Anyway, I set my LAN V6 to tracking (the WAN interface), re assign the DHCP server v6 to :
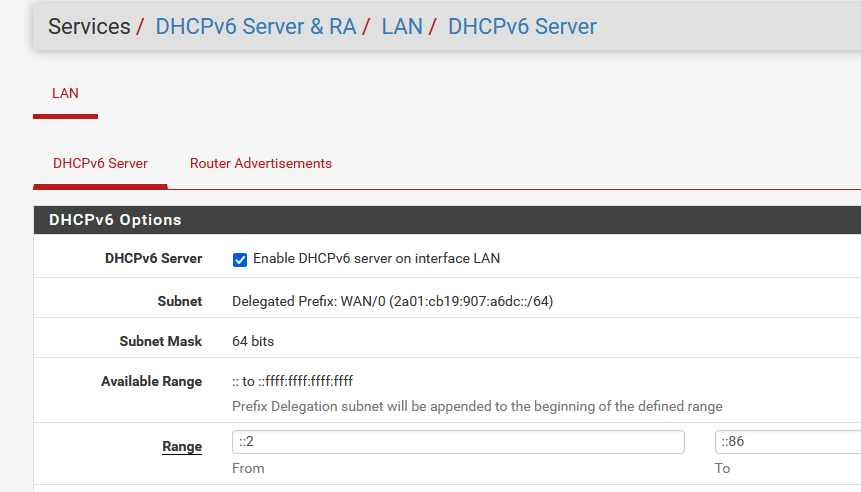
and reboot.
When done reboot : the GUI shows :
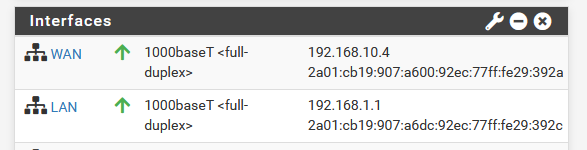
That's not a nice xxxxxxxx::1 as you mentioned.
How do I force a ::1 force LAN pfSense ? What did I forget ?Now : my PC :
I "ipconfig /renew" :
Carte Ethernet Ethernet :
Suffixe DNS propre à la connexion. . . : bhf.net Description. . . . . . . . . . . . . . : Intel(R) Ethernet Connection (11) I219-LM Adresse physique . . . . . . . . . . . : A4-BB-6D-BA-16-A1 DHCP activé. . . . . . . . . . . . . . : Oui Configuration automatique activée. . . : Oui Adresse IPv6. . . . . . . . . . . . . .: 2a01:cb19:907:a6dc::c7(préféré) <======= champagne !! Adresse IPv6 de liaison locale. . . . .: fe80::daa9:bcf8:99cd:717e%11(préféré) Adresse IPv4. . . . . . . . . . . . . .: 192.168.1.6(préféré) Masque de sous-réseau. . . . . . . . . : 255.255.255.0 Bail obtenu. . . . . . . . . . . . . . : vendredi 21 juillet 2023 13:04:59 Bail expirant. . . . . . . . . . . . . : samedi 22 juillet 2023 13:11:59 Passerelle par défaut. . . . . . . . . : fe80::92ec:77ff:fe29:392c%11 192.168.1.1 Serveur DHCP . . . . . . . . . . . . . : 192.168.1.1 IAID DHCPv6 . . . . . . . . . . . : 346340205 DUID de client DHCPv6. . . . . . . . : 00-01-00-01-26-59-DF-8D-A4-BB-6D-BA-16-A1 Serveurs DNS. . . . . . . . . . . . . : 192.168.1.1 NetBIOS sur Tcpip. . . . . . . . . . . : Activé Liste de recherche de suffixes DNS propres à la connexion : bhf.netSo, ok, thanks you for re forcing me to use tracking mode.
How can I get my short (simple) LAN IPv6 back, the one ending with a ::1 instead of this very long :
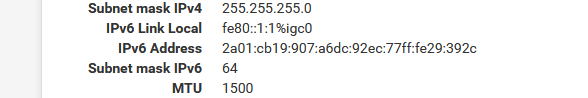
is there a way ?
-
My guess is that as you only have 1 subnet / LAN defined, so no need for a choice of prefix ID (I have 3 local networks defined).
Any leases showing here:
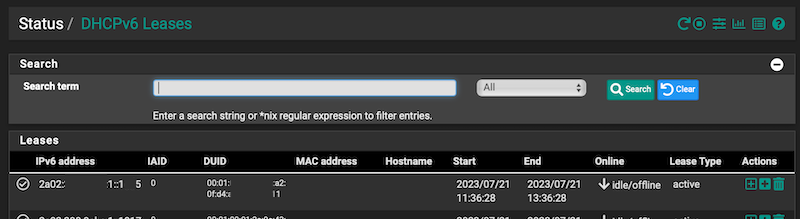
An example client shows the following addresses:
en0: flags=8863<UP,BROADCAST,SMART,RUNNING,SIMPLEX,MULTICAST> mtu 1500 options=6463<RXCSUM,TXCSUM,TSO4,TSO6,CHANNEL_IO,PARTIAL_CSUM,ZEROINVERT_CSUM> ether f8:4d:xx:xx:26:88 inet6 fe80::xx:80c4:xxxx:7eef%en0 prefixlen 64 secured scopeid 0xf inet6 2a02:xxxx:xxxx:1:1808:6752:xxxx:a287 prefixlen 64 autoconf secured inet6 2a02:xxxx:xxxx:1:7c15:c736:xxxx:7732 prefixlen 64 deprecated autoconf temporary inet 10.0.1.10 netmask 0xffffff00 broadcast 10.0.1.255 inet6 2a02:xxxx:xxxx:1::1b06 prefixlen 64 dynamic inet6 fd83:xxxx:239c:4fb4:8cd:5e06:xxxx:def8 prefixlen 64 autoconf secured inet6 fd8d:xxxx:3a57:4f07:142f:f915:xxxx:4cef prefixlen 64 deprecated autoconf secured inet6 2a02:xxxx:xxxx:1:b5b2:5b0a:xxxx:6e82 prefixlen 64 deprecated autoconf temporary inet6 2a02:xxxx:xxxx:1:f186:b1b0:xxxx:3a5b prefixlen 64 autoconf temporary nd6 options=201<PERFORMNUD,DAD> media: autoselect status: activeYou would probably benefit from your own thread as we are distracting from this one. Apologies to @guardian.
 ️
️ -
@guardian said in Very Basic IPv6 security question.:
Have I configured pfSense IPv6 Correctly? I am attempting to configure a VLAN6 which I am connecting over a trunk to an SG300 switch, and ultimately to an access port on GE2. The IPv4 is working fine, I get an IP assignment, and a DHCP server, but the IPv6 isn't working. I have a linux laptop connected to GE2 with DHCP configuration for both IPv4/v6. I have no IPv6 connectivity - a ping6 to 2607:f8b0:400b:804::2003 from the laptop results in Destination unreachable: Beyond scope of source address, but is successful if executed from the pfSense WebGUI.
The laptop has an fe80::/64, and the Default Route has an fe80:: address as well. There are no other entries, and if I attempt to run ping6 against the Defaut route, I get invalid argument. For some reason ping6 does not liek fe80 addresses--even when I fully expanded :: with the appropriate number of 0000 to make 8 complete hextets
I need to determine if the problem is with pfSense, the SG300, or the laptop, so any guidance would be much appreciated.
You have to configure the VLAN on every device that uses it or it passes through. For example, my guest WiFi is on VLAN3. I configured VLAN3 on the same interface as my main LAN, on the access point for the 2nd SSID and also both ports on my switch that it had to pass through.
Link local addresses are often used for routing. On Rogers, your default route will be a link local address and you will also have a global address on your WAN interface, but it's not used for routing.
BTW, I see you have a prefix delegation size of 64. That will get you only a single /64 prefix. You want to use 56, which will get you 256 /64s.
Also, why are you using DHCPv6 on your LAN? Unless you have a specific need for it, I'd recommend you stick with SLAAC. Also, thanks to some genius at Google, Android devices don't support DHCPv6.
I'd recommend you start simple and then work out what else you want, after you get pfSense working. For example, configure your VLAN after the main LAN is working.
-
@Gertjan said in Very Basic IPv6 security question.:
Because I know that I will receive "2a01:cb19:xO7:a6dc" as a prefix, I "hard coded" it.
Is that address from Rogers? If not, you shouldn't be using it. My addresses from Rogers start with 2607.
-
@Gertjan said in Very Basic IPv6 security question.:
Again : I know, treating the prefix as a static value is plain wrong / can bite you back in the future (== break your IPv6 networking).
This is one area where Rogers is really good. I've had the same prefix for a few years. Even my IPv4 address is virtually static and my IPv4 host name changes only when I change hardware.
-
@JKnott said in Very Basic IPv6 security question.:
Also, why are you using DHCPv6 on your LAN? Unless you have a specific need for it, I'd recommend you stick with SLAAC. Also, thanks to some genius at Google, Android devices don't support DHCPv6.
Just so we are all on the same page with the applicable pfSense options:
-
Managed
The firewall will send out RA packets and addresses will only be assigned to clients using DHCPv6. -
Assisted
The firewall will send out RA packets and addresses can be assigned to clients by DHCPv6 or SLAAC. -
Stateless DHCP
The firewall will send out RA packets and addresses can be assigned to clients by SLAAC while providing additional information such as DNS and NTP from DHCPv6.
Coming from different router environment I originally selected "Stateless DHCP," given that I used SLAAC previously on a different OS. A Netgate developer suggested "Assisted" instead and it solved a brace of annoying issues and is friendly enough for 'droid clients too.
 ️
️ -
-
@RobbieTT said in Very Basic IPv6 security question.:
Coming from different router environment I originally selected "Stateless DHCP," given that I used SLAAC previously on a different OS. A Netgate developer suggested "Assisted" instead and it solved a brace of annoying issues and is friendly enough for 'droid clients too.
I use unmanaged. Between SLAAC and RDNSS, you generally have all you need.
As has been mentioned, start simple and go from there, as you get things working.
-
@JKnott said in Very Basic IPv6 security question.:
As has been mentioned, start simple and go from there, as you get things working.
Cannot argue with that.

 ️
️ -
@JKnott said in Very Basic IPv6 security question.:
Because I know that I will receive "2a01:cb19:xO7:a6dc" as a prefix, I "hard coded" it.Is that address from Rogers?
No. I'm living in the original, old world, not the recent one ;)
To be exact : 2a01:cb19:907:a6dc
ISP Orange, France.@RobbieTT said in Very Basic IPv6 security question.:
Just so we are all on the same page
Managed, for myself.
I'm doing my best to give Android devices a hard time on my networks.
I'm joking of course, I don't have any Android devices so I'm not in the need of the SLAAC thing.
( or am I saying the same thing differently ? )