How to block random VPN attempts
-
I have an IKEV2 VPN for our iPhones using certificates for a few years now. I have a rule containing an alias for the cell phone company's subnets, otherwise they are blocked and it would not work.
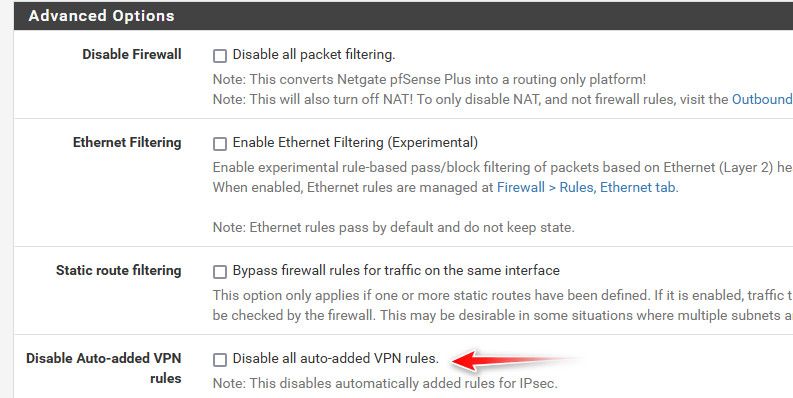
I noticed in the VPN logs there are many VPN attempts on port 500 then failing authentication. None are successful but I would prefer they are blocked before attempting VPN. I am puzzled Pfsense is not automatically blocking these attempts. My question is do I need an "inverse" rule using the phone company alias on the WAN? What am I missing? I thought anything else would be blocked before VPN attempts automatically. I did study https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/firewall-rules.html#ipsec-fw-outer and https://docs.netgate.com/pfsense/en/latest/vpn/firewall-rules.html and wondering about this sentence: "automatically adds hidden firewall rules". I then found that my "Disable all auto-added VPN rules." is not checked. I am a little concerned before I try setting this on to see if anyone here can verify that's the problem. THANKS!
Here is a log entry with IPs changed: 10.9.8.7 is me, 1.2.3.4 is whoever:
charon[72402]: 04[NET] <1567> received packet: from 1.2.3.4[59338] to 10.9.8.7[500] (360 bytes) charon[72402]: 04[ENC] <1567> parsed AGGRESSIVE request 0 [ SA KE No ID ] charon[72402]: 04[CFG] <1567> looking for an IKEv1 config for 10.9.8.7...1.2.3.4 charon[72402]: 04[IKE] <1567> no IKE config found for 10.9.8.7...1.2.3.4, sending NO_PROPOSAL_CHOSEN charon[72402]: 04[ENC] <1567> generating INFORMATIONAL_V1 request 2161089625 [ N(NO_PROP) ] charon[72402]: 04[NET] <1567> sending packet: from 10.9.8.7[500] to 1.2.3.4[59338] (40 bytes) charon[72402]: 04[MGR] <1567> checkin and destroy IKE_SA (unnamed)[1567] charon[72402]: 04[IKE] <1567> IKE_SA (unnamed)[1567] state change: CREATED => DESTROYING charon[72402]: 04[MGR] checkin and destroy of IKE_SA successful -
Ummm... Unless they're connecting, they are being blocked. With a VPN, the key is necessary. No key, no access and they can try all they want.
-
@JKnott But I would prefer they not get that far. Port 500 is responding to them as open and they make the attempts, from around the world. I don't want them to get past the firewall rules, don't want them to know I have VPN. I think that is more secure even though they will never get in, it's still garbage traffic in my router.
-
You can't block them, without blocking yourself. Firewalls can filter on addresses and ports. You're already blocking most addresses and ports.
-
@MarioG I’m not following your logic. You’re puzzled why pfsense isn’t blocking something that you do permit through an alias?
Edit. Also how would pfsense or any firewall know what a legitimate user would look like. Auth is the only way.
Do you want to prevent someone from knocking on the door but who knows what the person looks like?
Again I’m not following the logic here. -
@MarioG pretty sure when you create the vpn server pfsense creates hidden rules that allows it.
Not sure how to stop that actually off the top of my hidden - not sure if floating rules would come before the hidden rules.
# VPN Rules pass in on $WAN reply-to ( igb1 209.<snipped> ) proto udp from any to (self) port = 500 ridentifier 1000114651 keep state label "IPsec: testipsec - inbound isakmp" pass in on $WAN reply-to ( igb1 209.<snipped> ) proto udp from any to (self) port = 4500 ridentifier 1000114652 keep state label "IPsec: testipsec - inbound nat-t"look in your do a cat /tmp/rules.debug and you can see all the rules. There are hidden rules pfsense creates that are not listed in the gui.
https://docs.netgate.com/pfsense/en/latest/firewall/pf-ruleset.html
Those showed up when I enabled mobile ipsec and created a phase1.. I don't use ipsec on pfsense. That is my wan IP where I snipped out the last 3 octets..
While you might be able to create some floating rules, but normally hidden rules supersede interface rules. So not sure on the inbound to your wan, if could block what you want in floating.
@stephenw10 might know or @Derelict
I hear what you want to do.. I do the same thing on allowing only US IPs to talk to my plex and some other services I run. But I have never setup road warrior ipsec on pfsense.. Openvpn is just so much easier, and or now tailscale, etc.
-
@michmoor Not correct. The alias has networks owned my the cell phone company. Without those that alias rule VPN is blocked. The problem is that IPs NOT in the alias are making the VPN requests that are then failing. I don't want anyone who should not get past rules to get as far as VPN requests.
-
@johnpoz I think I am going to try disabling the hidden auto rules I mentioned above. Will try this week and let you know how it goes. If that doesn't I may try inverse rules to block everyone other than the alias, but as you said it depends on which rules come first. Thanks for the response. If no one answers how to fix for sure, I will try checking the "Disable all auto-added VPN rules" and let everyone know the results.
-
@MarioG hmmm. How is that possible.
Maybe I’m misunderstanding the problem.
You permit let’s say a /24 in the alias.
An IP outside of that /24 is attempting to connect but failing. You are seeing the auth attempts but you believe the firewall should block before the auth attempts. If that’s the case then you are correct. The only other way I can see that happening is that there’s rule order issue in your WAN rules maybe. -
@MarioG said in How to block random VPN attempts:
"Disable all auto-added VPN rules"
That should do it!!! and then create your own rules on wan to allow only who you want..
I do that for my openvpn connection, which doesn't create hidden rules. I only allow US Ips via a geoip alias from pfblocker to only allow US IPs to even start a conversation with openvpn.
-
@MarioG said in How to block random VPN attempts:
I noticed in the VPN logs there are many VPN attempts on port 500 then failing authentication.
@MarioG said in How to block random VPN attempts:
I would prefer they not get that far. Port 500 is responding to them as open and they make the attempts, from around the world.
@johnpoz said in How to block random VPN attempts:
allow US Ips via a geoip alias from pfblocker to only allow US IPs to even start a conversation with openvpn
I agree with @johnpoz approach. Use pfblocker to both block risky IP addresses and only allow the minimum subset consistent with your requirement.
I use a series of rules to black list (risk address, not my country) then white list known good addresses then telco company.
-
How to block random VPN attempts
Easy !
Instead of using the 'default' WAN firewall rule like :
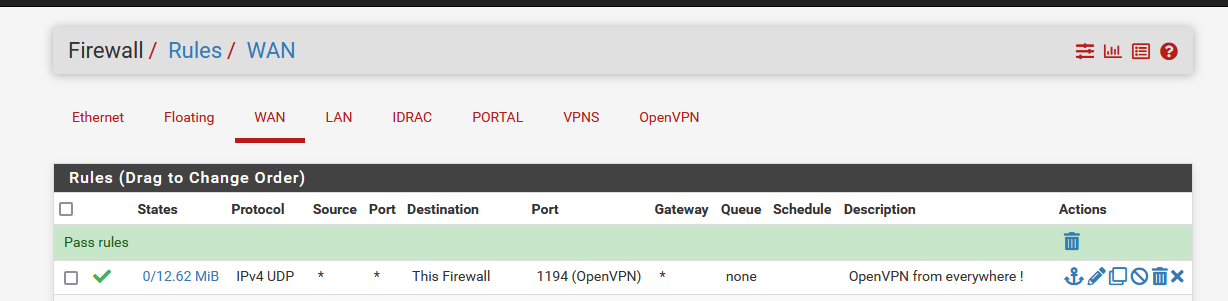
Make this :
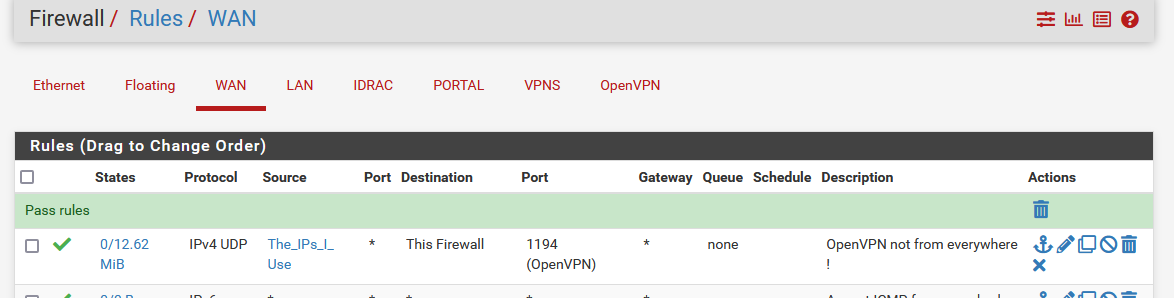
Don't relax yet, there is still something to do.
You saw the source alias called "The_IPs_I_Use" ? You have to add all the IPs that you allow. These are the one you use when you connect to pfSense OpenVPN.
It won't take long before you discover that this isn't the perfect solution yet ;)Situation : you live in the USA.
You could use the pfSense package pfBlockerng, and place a firewall above the OpenVPN firewall I've shown above, where you block all IPs that do not come from "USA" with GEOIP blocking (still not perfect, but it would help).Btw : OpenVPN is secure. Normally, you can leave the OpenVPN visible = exposed on the Internet. If 'they' don't have the key, they can't enter. Like your house front door or phone number, if you don't want them to 'knock' or call you, remove the front door (or put a guy or 'thing' in front of it that 'filters' who approaches your house), or stop / quit using the phone.
You are using, and are part of a public network. If you don't want the public coming over : stop the OpenVPN service. They will still keep trying to connect to your VPN, even if you didn't have it activated. That's how Internet is these days. -
Yes, when you create an IPSec instance on WAN it automatically adds rules to allow traffic from the configured remote side. If that's a remote access instance it allows connections from any IP.
So disable those automatic rules and add your own pass rules to limit that.
-
An idea ?? Maybe move the server instance from Wan to Localhost. Then create port-forwards for the IKE VPN, restricted to only your mobile provider subnet. That way the FW rules should block the rest of the world even starting the VPN process on port 500 ?
-
@pwood999 said in How to block random VPN attempts:
Wan to Localhost
That solution, needs one step more : the NAT rule coupled with the firewall rule.
Have the VPN service/process listen on the WAN interface, that's where the traffic comes in.
This needs a firewall PASS rule (not a firewall+NAT rule) that can be set up with to match :
Protocol used
Destination Port
Source AddressesThe destination would be "This firewall" as it includes the WAN IP.
-
@Gertjan said in How to block random VPN attempts:
That solution, needs one step more : the NAT rule coupled with the firewall rule.
Have the VPN service/process listen on the WAN interface, that's where the traffic comes in.
This needs a firewall PASS rule (not a firewall+NAT rule) that can be set up with to match :
Protocol used
Destination Port
Source AddressesThe problem here is the OP is using a road warrior where the source address is unknown.
I had been thinking to use schedule so things are not left open all the time...that's what attracted me to pfSense.
-
@NollipfSense said in How to block random VPN attempts:
The problem here is the OP is using a road warrior where the source address is unknown.
True.. But you can take an educated guess for example that it would be some IP from the US only.. Or some other country where your users reside.. Etc..
I have no idea what IP my plex users might come from.. But pretty sure it won't be from Russia or China, etc.. Or any other IP other than some US ip.. Same goes for users connecting to my openvpn, etc.
So I created this list of IPs that are allowed.
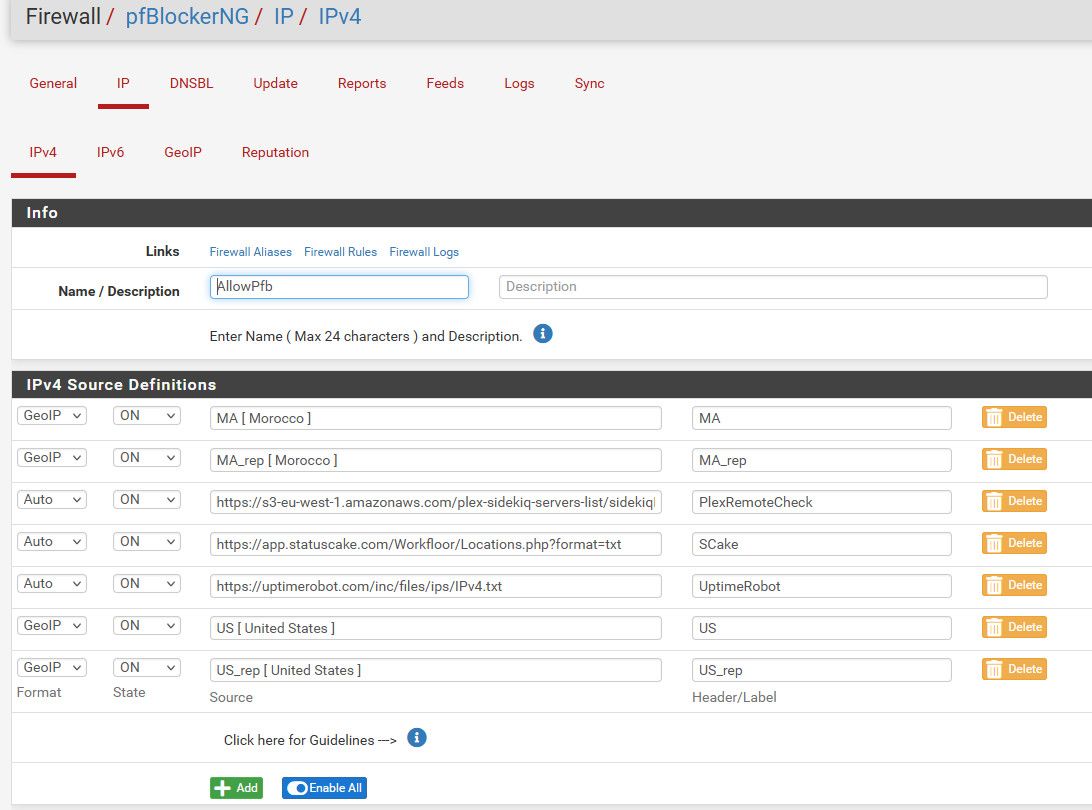
Now I use those in my forwards/Rules - so only included in that allowPfb list are allowed to talk to those ports and services that are forwarded.
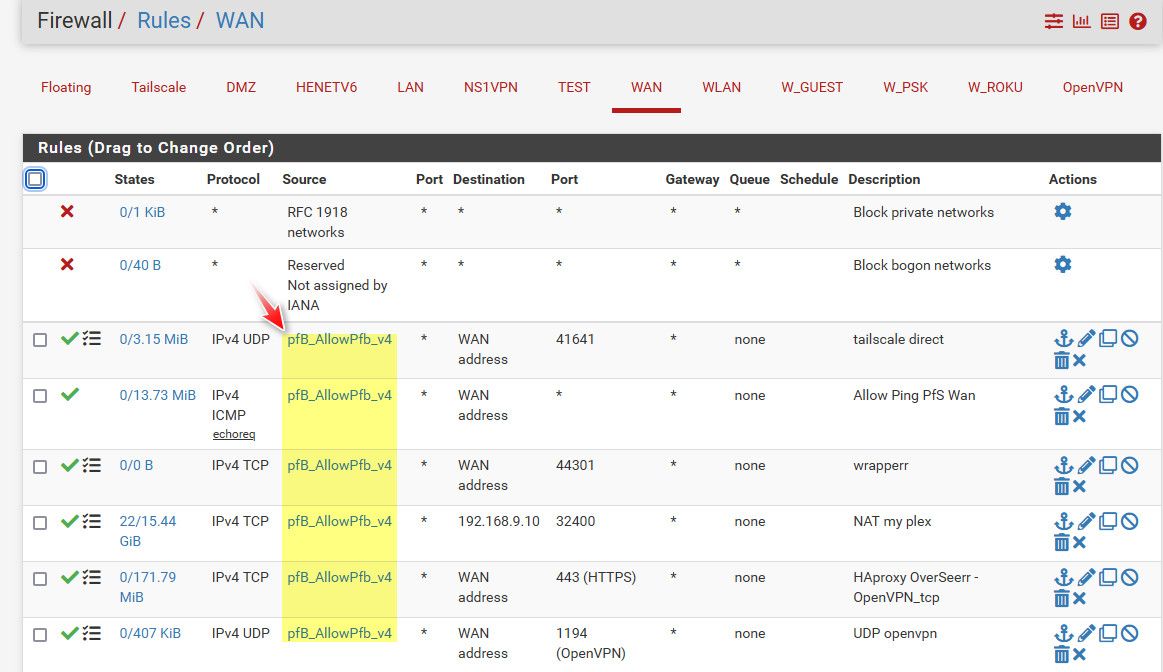
I have a family member currently living in Morocco is why those are included.. And I allow IPs from status cake and uptime robot - since they might be from outside the US, they change now and then. And then the service from plex to check if your plex is available remotely - which also can be from international IPs..
Now allowing any IP from US is pretty open, but is far less open than the whole planet ;)
-
@johnpoz To me, schedule is the best solution as only I know the schedule...I cannot see any situation where schedule wouldn't work for a road warrior setup...the best thing about pfSense firewall to me.
-
@NollipfSense you can for sure use schedules as well.. But if you don't limit what IPs can talk.. Which is what the OP was asking about, during your scheduled allowed time, he would be seeing the same random connection attempts - which he doesn't want to see.
-
@NollipfSense said in How to block random VPN attempts:
wouldn't work for a road warrior setup...
Yes he wants to allow road warrior access but what is known about valid road warrior users?
- is it only the time of day access starts?
- are all countries valid?
- is access required from all telcos?
- is access required from known bad internet addresses
- is access required from external vpn suppliers
For my use case the answer to all the above is no. I also use a white list of specific IP4 & URL addresses I know are OK and which pfblocker does not log for me.
Unfortunately before I can use IP6 I would need pfsense to support an alias with masking the least significant portion of addresses to turn device addresses back to site addresses.