FreeRADIUS MAC authentication
-
I am setting up FreeRADIUS for the first time and attempting to use MAC based auth with a switch. My switch is taking the device's MAC and sending it to FreeRADIUS because I see this in the log entries, but what am I missing, why is this failing to authenticate?
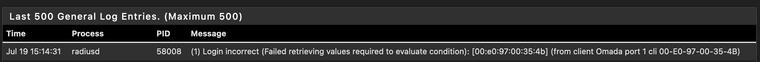
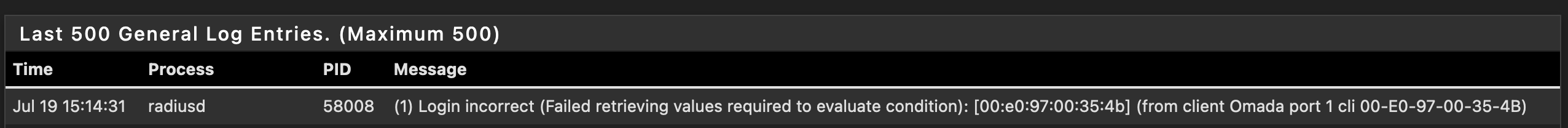
In case you can't see in the image, the error reads:Login incorrect (Failed retrieving values required to evaluate condition): [00:e0:97:00:35:4b] (from client Omada port 1 cli 00-E0-97-00-35-4B)The MAC address is correct and has already been added to FreeRADIUS here so I would expect it to be authenticating. I tried it with both -'s and :'s but get the same result either way.
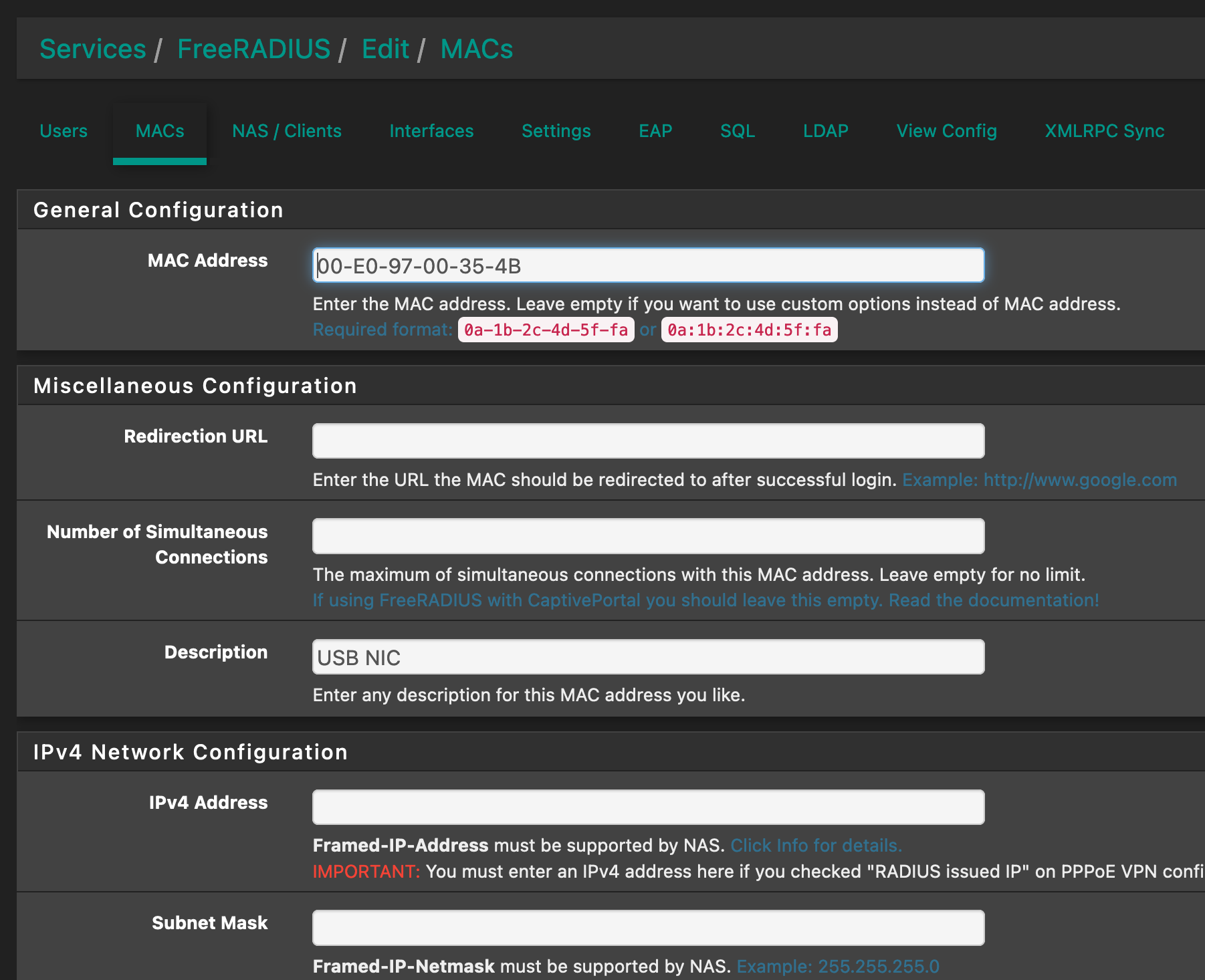
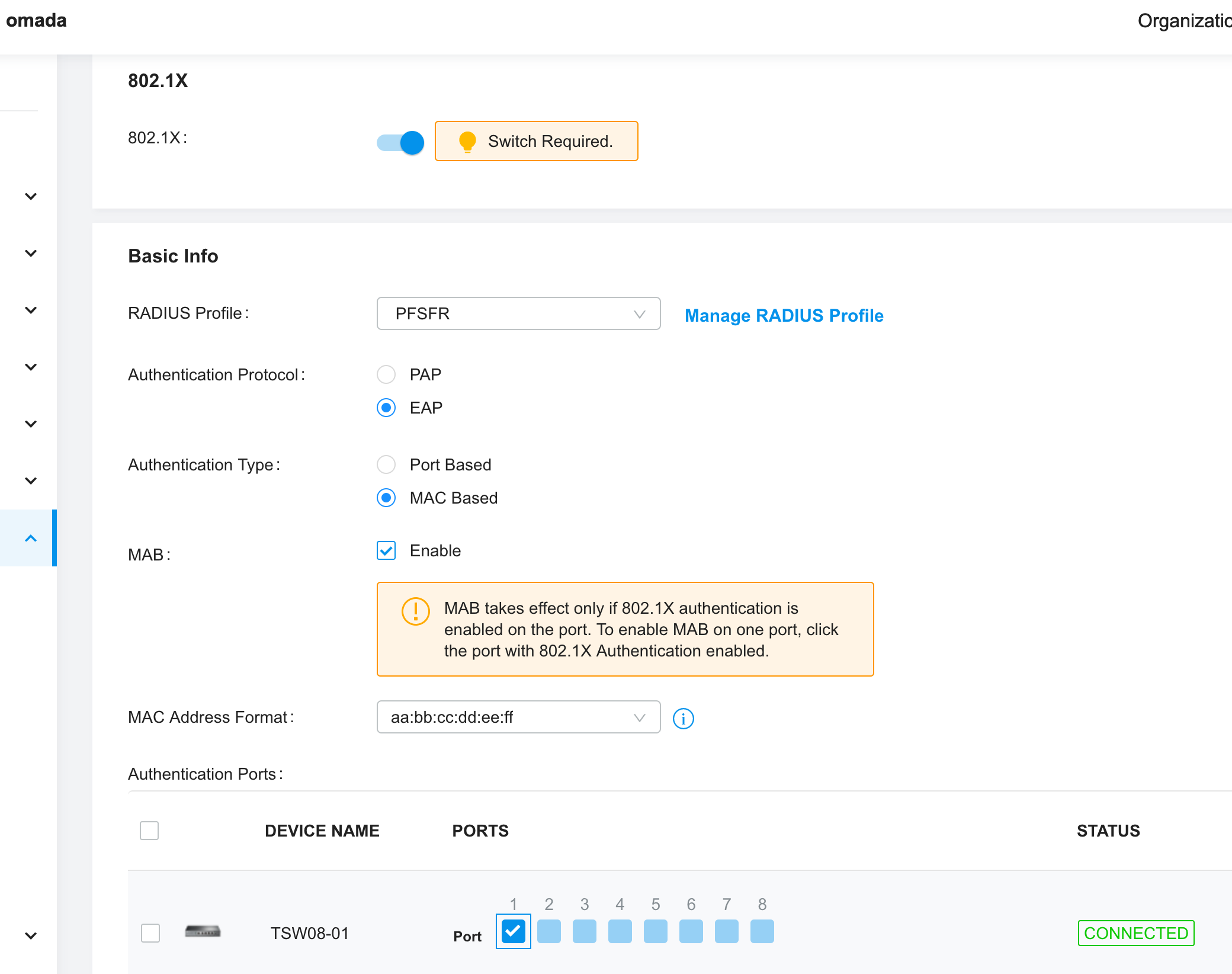
If it matters, this is what the settings look like on the switch:
and here "MAB" means:
(MAC Authentication Bypass) allows clients to be authenticated without any client software installed. MAB is useful for authenticating devices without 802.1X capability like IP phones. When MAB is enabled on a port, the switch will learn the MAC address of the client automatically and send the authentication server a RADIUS access request frame with the client’s MAC address as the username and password. MAB takes effect only when 802.1X authentication is enabled on the port. -
@aaronssh Freeradius (and most other Radius’) are setup to use PAP and CHAP Authentication by default when attempting MAC Auth.
The log entry also seems to suggest that Freeradius cannot complete the auth attempts because of its missing EAP setup - which is understandable if your switch is using EAP.Try using PAP as the protocol on your switch, or otherwise you need to setup your Freeradius with the EAP settings needed to communicate with your switch.
-
@keyser So I tried switching to PAP but am getting the same errors. I have a question though, I am testing this on my Macbook and each time I connect it prompts for 802.1x credentials rather than using the MAC address. I have a hunch that is why we are seeing in FreeRADIUS:
Login incorrect (Failed retrieving values required to evaluate condition): [00-E0-97-00-35-4B] (from client Omada port 1 cli 00-E0-97-00-35-4B)Because when this box comes up, I hit cancel:
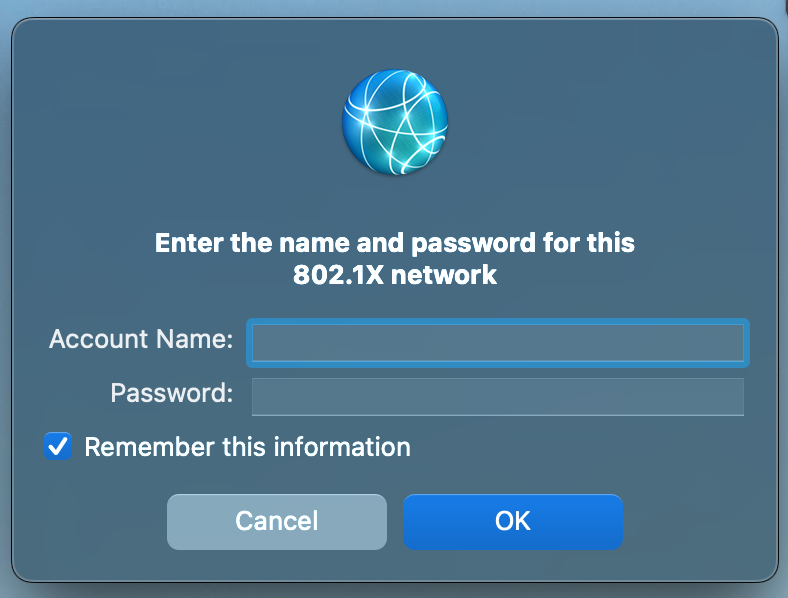
Is there some trick to forcing the MAC address auth and bypassing this 802.1x screen? At this point I can't tell if that is a MacOS quirk, a quirk with my switch, or something with FreeRADIUS.
-
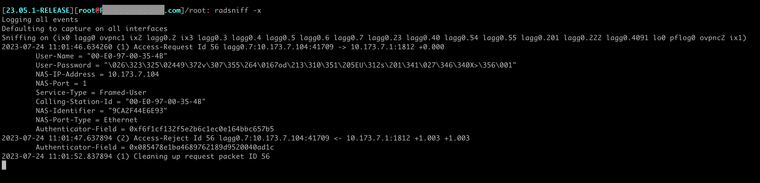
@aaronssh Try running radsniff -x from a ssh session on your pfSense box
-
-
@aaronssh I am not sure how to read that output in the screenshot above other than it looks like FreeRADIUS is rejecting the auth attempt. I don't understand why.
-
radsniff is nice.
I'll add another one :
Shut down FreeRadius in the pfSense GUI.On the pfSense command line (SSH - NOT GUI !!) or console : menu 8 :
radiusd -XEnjoy.
Totally useless, but I say it anyway : if you think FreeRadius doesn't show something, then this means it didn't receive something.
Also, terminology used is rather cryptic. Radius is .... well .... Radius. -
@Gertjan said in FreeRADIUS MAC authentication:
radiusd -X
I do get a lot more info that way, but I don't know how to interpret what I'm seeing here. Can you determine what this means?
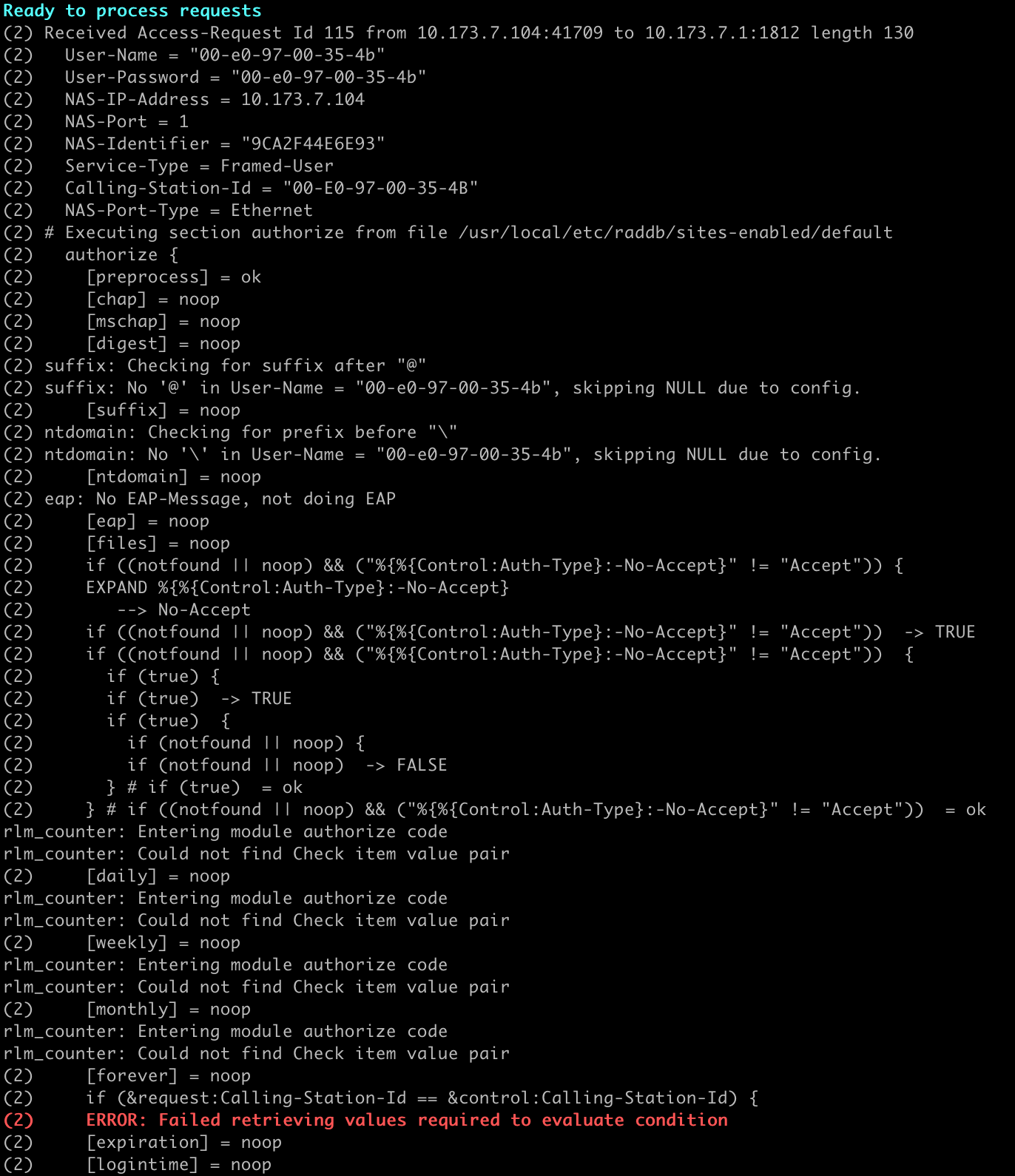
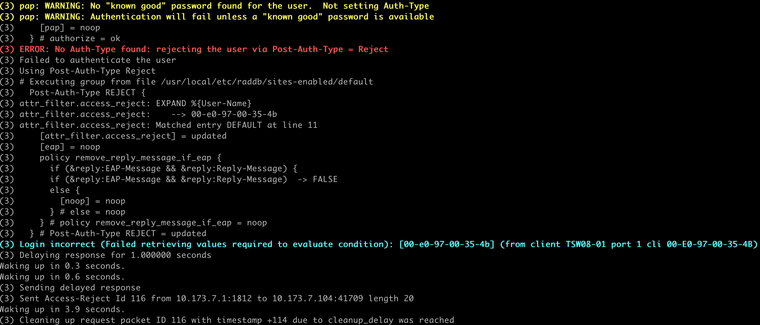
-
Welll ... I never used pfSense Freeradius to do MAC authentication / identification.
I do see the same :
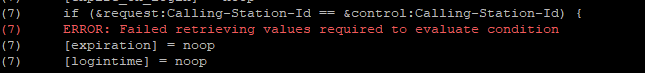 - consider this one harmless.
- consider this one harmless.I don't know who is 10.173.7.104 neither 10.173.7.1 (probably : pfSense but it has a strange LAN IP)
00-e0-97-00-35-4b looks like a MAC. From what device ?
Etc.I'm the more basic "user + password" guy.
The pfSense documentation hasn't a doc / example for you ?
-
@Gertjan
10.173.7.104 is the switch
10.173.7.1 is pfSense
00-e0-97-00-35-4b is the MAC address on my MacbookSo all of that looks right to me, and I don't understand why it is rejecting.
-
@aaronssh Perhaps you forgot to enable MAC bypass in Freeradius since your client is 802.1x challenged?
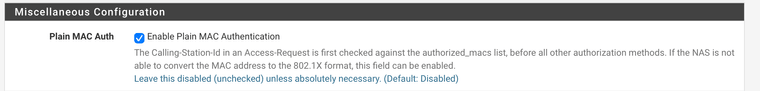
-
@keyser I noticed that and tried it both ways, but it does not change the result or the error messages.
-
So I noticed in the logs that both the USER and PASS that are being passed to FreeRADIUS are the MAC address. I have that MAC address entered in the MACs section of FreeRADIUS so to me it seems like it SHOULD at that point authenticate ok. It obviously doesn't.
So I thought, what the hell, let's trying setting up a user under USERS in FreeRADIUS and enter the MAC address as both the user and pass. Bam, that works! So seems very counterintuitive but that's good enough for me. Thank you everyone for your help!
-
@aaronssh Well, I’m using mac-auth and my clients are entered on the MAC addresses sheet, so it does work in the right configuration.
But if you are not going to use 802.1x you can just create the MAc addresses as users. -
This post is deleted!